MyloBot 2022: A botnet that only sends extortion emails
A new version of the MyloBot botnet has been used to deploy malicious payloads to send extortion emails, demanding victims pay $2,732 in bitcoins.
MyloBot is a malware active since 2018 and capable of deploying malicious payloads on the target and sending extortion emails to "threaten" the victims to pay a considerable value of $2,732 in bitcoins.
According to the Minerva Labs research team who analyzed this threat, this botnet is more sophisticated and evolved than samples seen in the past. Some of the known anti-debugging and VM techniques observed in the past disappeared. In contrast, a set of new injection techniques such as Process Hollowing and APC Injection were introduced by criminals.

Become a certified reverse engineer!
Anti-debug and VM techniques
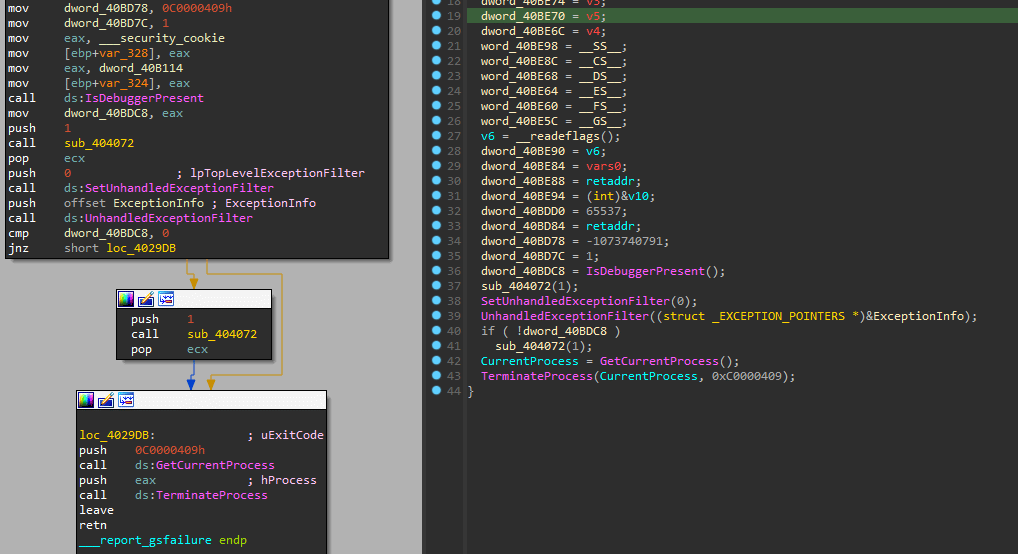
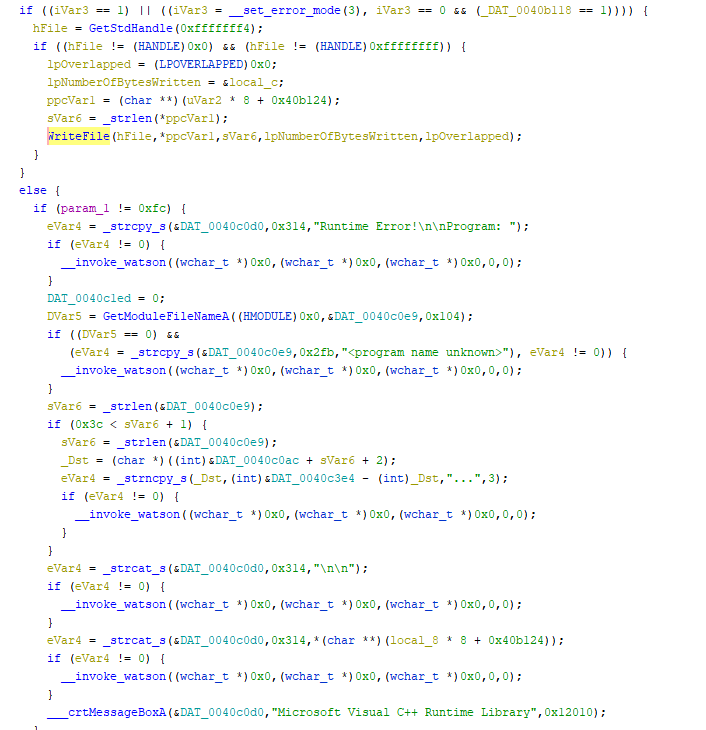
One of the anti-debug tricks found in this sample is using the "SetUnhandledExceptionFilter" exception filter. If an exception is triggered during the malware execution and no handler is called, the "kernel32!UnhandledExceptionFilter()" API call is invoked. [CLICK IMAGES TO ENLARGE]
Figure 1: Anti-debug technique used by MyloBot 2022.
With this technique in place, the malware can register its real payload in a custom exception filter and make its analysis hard.
How to bypass this protection
Place a breakpoint at the address passed as the single parameter to "SetUnhandledExceptionFilter" and ignored the exception.
Another technique utilized by MylotBot is a call to the "CreateTimerQueueTimer" function that creates a timer that will expire after a specific period. The usage of this approach makes detection harder since the payload will not run in the remote thread context. Metamorfo, better known as Casbaneiro, is one of the most popular banking trojans that use this technique to bypass detection.
After the initial checks and ensuring the malware is not debugging in a sandbox environment, an additional PE File (2nd stage) available on the MMZ: 442 section resources is executed into the memory. As observed, the resource is obfuscated to avoid potential detections.
Figure 2: MyloBot 2022 2nd stage available on the MMZ: 442 resources.
The new payload is then decoded and executed into a new suspended process using the Process Hollowing technique.
MyloBot 2nd stage
The new process created via process hollowing is composed of three important actions, namely:
- Executing anti-VM checks and looking for: VMWARE, VBOX, VIRTUAL HD and QEMU strings. If it matches, the malware terminates its execution.
- As observed in the past samples, also this one tries to find other malware in specific registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\RunHKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run
HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- Creates persistence under a new folder in C:\ProgramData path and drops a new EXE file (the 1st stage again).
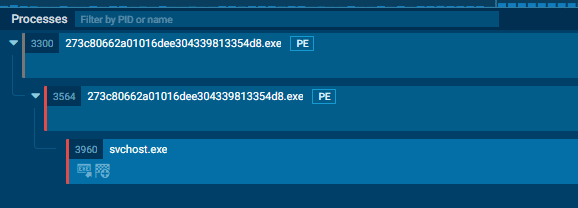
After that, a new process called "svchost.exe" is initiated in a suspended state, and the parent process is injected into the new one using the APC Injection technique.
Figure 3: APC Injection technique used during the MyloBot 2022 execution.
3rd stage - svchost.exe
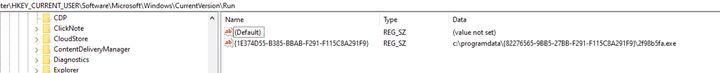
As documented by Minerva Labs research, this 3rd stage is responsible for creating persistency under HKCU\Software\Microsoft\Windows\CurrentVersion\Run with the path to the written file as a value:
Figure 4: MyloBot persistence via Windows registry key on \CurrentVersion\Run.
After that, the written file is injected into a new remote thread by using the "CreateRemoteThread" approach. 3rd stage runs over the Windows processes tree and tries to inject the written file into a 64 bytes process. If it fails, the file under the "C:\ProgramData" path will execute the notepad.exe process and injects it into that.
Next, the C2 server is notified, and a new payload is downloaded — a PE file and, in some cases, a text file named: update.txt.
MyLoBot 2020 final stage
According to Minerva's research, the same anti-VM and debugging techniques are executed when this final stage is executed. Also, this stage has a resource with an additional EXE obfuscated. Once again, the Process Hollowing technique is used to execute into the memory the target payload. After that," it runs a 64bit cleanmgr.exe process and injects the whole payload into it using a CreateRemoteThread technique", says Minerva Team.
Figure 5: Injection into suspended cleanmgr.exe (source).
The whole infection chain is a carousel with many stages, validations and injections — a typical modus operandi observed since 2018. In this sense, the "cleanmgr.exe" is equipped with a Timing anti-debugging technique that checks for huge delays between instructions.
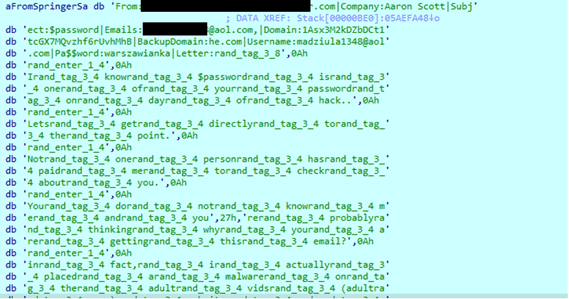
After that, a "\Sessions\2\BaseNamedObjects\Santiv18" mutex is created, and if the "update.txt" file is not found, MylotBot uses the victim's endpoint to send extortion emails.
Figure 6: Extorsion message and email senders used to disseminate the scam in the wild (source).
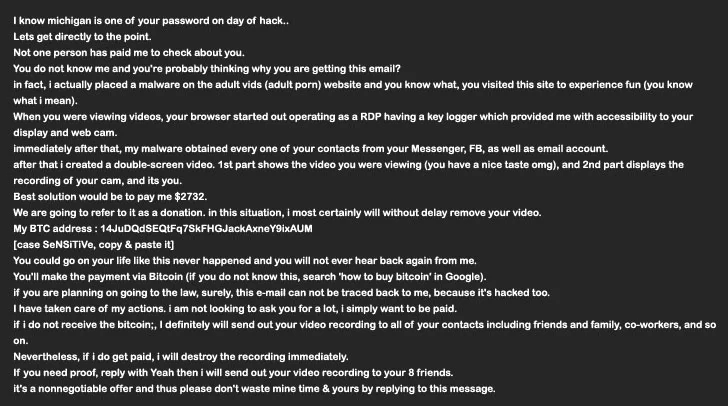
The email body sent to the victims is the following:
Figure 7: Extortion email sent by MyloBot 2022.
Given the complexity of this malware, Minerva states that it could not understand whether this would be the last stage of the infection chain and if other payloads could be executed later.

Become a certified reverse engineer!
The MyloBot threat
MyloBot 2022 is a sophisticated and complex threat, with several TTP present and capable of preventing a full analysis of this malware. Although it was not possible to conclude the last stage of infection of this malicious piece, there are clear indicators that the threat has been disseminated in some specific countries, such as Iraq, Iran, Argentina, Russia, Vietnam, China, India, Saudi Arabia, Chile, and Egypt (TOP 10 of affected countries).
According to an analysis by Minerva Labs, the malware reveals that it can also download additional files, suggesting that the author of the threat also leaves a door open to carry out other attacks by extracting additional files. In this way, botnets like this are dangerous because they could drop and execute other kinds of threats, such as ransomware, spyware, worms or other files on all the infected machines.
Thus, the usage of updated endpoint security solutions is seen as the first step in fighting cyber threats of this nature. Also, backup copies are recommended to prevent disruptions attacks, such as data encryption malware or other threats.
Sources:
- MyloBot 2022, Minerva Labs
- TOP 10 affected countries, ETEK