Android malware BrazKing returns
Banking trojans put internet end-users at risk due to their sophistication and obfuscation techniques. They are often capable of evading antivirus and EDR systems, as observed on the relatively new MAXTRILHA trojan banker from Brazil.
BrazKing is one of the most predominant banking trojans these days, impacting mobile users worldwide. This malware has existed since 2018 November. It was developed by Brazilian gangues and targets mainly Brazilian mobile users. This new release brings many new features and seems more capable and agile than before.

Become a certified reverse engineer!
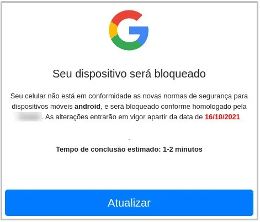
As observed on other malware this line, it avoided the Google Play Store protections and was disseminated legitimately on the official store, increasing the number of infections. In short, when the users are navigating a specific website, often disseminated via social engineering campaigns, they are asked to install a new app to fit the new updates. Figure 1 below shows a print of the malicious window in the Portuguese language.
Figure 1: BrazKing initiates its infection chain with a social engineering message (source).
After clicking on the button, the application is downloaded using the mobile web browser and installed on the device by the package manager. Because of this, the option “ download of apps from unknown sources” should be disabled to prevent scenarios of this nature and protect, thus, the users’ devices.
Modus operandi of BrazKing trojan
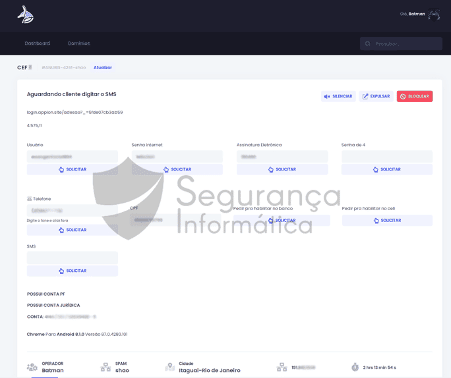
As explained by IBM researchers, the trojan communicates in real-time with the C2 server, and the criminals send specific information to request or execute single operations. This operation mode was documented and observed last year on phishing campaigns from Brazil that targeted different banking organizations in Brazil, Spain, Mexico, the UK, and Portugal.
Figure 2: C2 server from Anubis Network threat detected and documented in December 2020 (source).
BrazKing periodically sends a screenshot of the device to the C2 server and can perform automatic actions if the criminals do not specify actions. For example, the trojan can exhibit overlay windows over when specific apps are running — a common behavior also documented on desktop trojan variants.
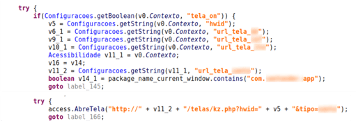
Figure 3: BrazKing has a matching overlay displayed on over legitimate apps.
A sophistication point observed by IBM experts is related to the way on how the trojan displays the overlay windows in this new release: “We noted that while BrazKing now works without the SYSTEM_ALERT_WINDOW permission, which allows BrazKing to be more elusive and arouse less suspicion, it remains in its manifest.”
In detail, the trojan loads the overlay screen URL from the C2 server and renders it into an Android web-view component. The users can navigate through banking overlay windows introduce their credentials without exiting the malicious application. For this, the Brazking uses the “TYPE ACCESSIBILITY OVERLAY” feature as the type of the windows.
The trojan communicates with its C2 server during the infection operation based on commands observed on other Brazilian trojans. The complete list of commands is presented below.
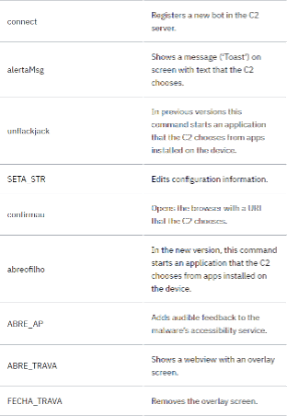
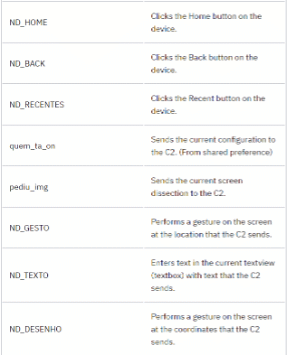
Understanding the BrazKing capabilities
BrazKing takes advantage of a set of capabilities that put it on the cybersecurity radar. In general, this piece of malware is capable of performing:
- Input injection: communication with the running applications is possible.
- Screen grabber: collect information about the device screen.
- Keylogger: obtain stored credentials.
- Create overlay windows: launch fake windows and deceive users into sharing their secrets.
- Uninstall protection: block users when they try to uninstall the trojan.
- Prevent factory reset: the malware tries to block users when they try to reset the device.
- RAT capabilities: BrazKing utilizes the most advanced schemas, and TTPs observed on Brazilian banking trojans.
- Read SMS and contacts: The trojan can read SMS and contacts without explicit android permissions.

Become a certified reverse engineer!
Understanding Android malware BrazKing
Criminals are changing their malicious methods both in sophistication and agility. Users should be cautious and understand that emergent threats constantly introduce new techniques to take advantage of human fails.
For instance, if someone cannot uninstall a specific app or even factory reset the smartphone, that should trigger an alert. There are no magic steps to prevent malware in general, but we can enumerate some points that can protect our devices against threats of this line.
- Never disable the “allow downloads from unknown sources” option.
- Think two times before accessing a suspicious link.
- Be wary of windows that prompt you to install applications.
- Promote and join phishing and malware training to be aware of these constant challenges.
And last but not least, download and install antivirus software from legitimate sources or paid applications based on their reputation.
Sources:
- BrazKing malware dissection, IBM
- Brazilian trojan - BrazKing, thesecmaster
- The new MAXTRILHA trojan, Segurança Informática
- Anubis network, Segurança Informática