Purple Fox rootkit and how it has been disseminated in the wild
The Purple Fox rootkit has been a malicious and powerful weapon active since March 2018 and covered as an exploit kit. This piece of malware acts as a wormable binary. It also evades defenses by impersonating legitimate software and can be stealthy for a long time due to its rootkit capabilities.
Purple Fox malware uses social engineering techniques, such as phishing and spearphishing, to target its victims and enlarge its scope using the newly implemented wormable capability. Although not many changes were detected from the known variants of this malware, this time, it is also impersonating and dropping legitimate software as a way of evading its detection. This practice is not new, and popular banking trojans like Javali and URSA have used this technique to circumvent the security perimeter.
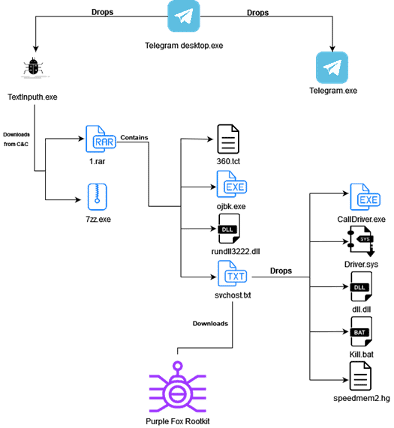
The typical distribution vehicles of the 1st stage are phishing campaigns, spam messages on forums, social media posts, comments (Youtube and Facebook), and untrustworthy software download websites. Some of the observed campaigns involved the WhatsApp and Telegram brands. The high-level diagram of Purple Fox new waves is depicted below.
Figure 1: High-level diagram of the Purple Fox rootkit - January 2022 (source).
Digging into the details
As illustrated above, Purple Fox is posing as legitimate software, in this object of analysis an AutoIT binary impersonating the Telegram installer. This kind of approach has been used by cyber gangs last years, including in the URSA trojan TTPs. The Purple Fox 1st stage — the binary file — drops into a new folder two additional binaries: (i) a legitimate file from Telegram software and (ii) a malicious downloader named TextInputh.exe. In detail, the Telegram binary is never used, just used to confuse its analysis. However, the TextInputh.exe binary is the downloader to the next stage.
During the execution, a new folder is created, and two new files are downloaded from the Command and Control (C&C) server online:
- "1.rar": a compressed file with other files inside.
- "7zz.exe": a legitimate file used to unrar the "1.rar" file.
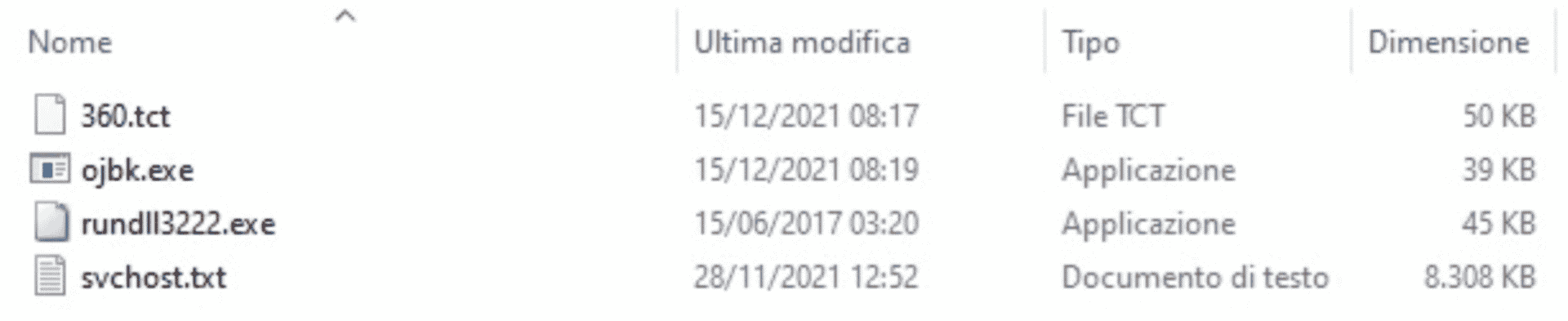
Figure 2: Files inside the "1.rar" file.
After executing the previous process, the "TextInputh.exe" file performs the following tasks:
- The "360.tct" (a DLL) file is renamed to "360.dll" and moved into the ProgramData folder along with the rundll3222.exe and svchost.txt files.
- After that, the ojbk.exe is executed with the "-a" argument.
- The files "1.rar" and "7zz.exe" files are deleted.
As described by Minerva's research, when executed with the "-a" parameter, the DLL is loaded using the reflective way. After its execution, additional files which work together are also dropped, namely:
- calldriver.exe: a binary capable of terminating the execution of 360 AV.
- driver.sys: a file responsible for creating a new driver called "Driver" on the infected machine.
- dll.dll: a DLL executed after the UAC bypass. In this case, the CMSTPLUA COM interface well-known technique is used. "This technique is commonly used by the LockBit and BlackMatter ransomware authors", said Minerva researchers.
- speedmem2.hg: an SQLite file.
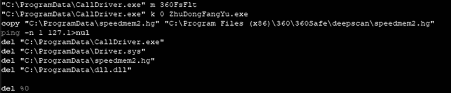
- kill.bat: house cleaning files executed at the end of the process.
Figure 3: Content of the kill.bat file executed at the end of the malicious process.
At first glance, these files are executed together to block the 360 AV detection and allow the stealthy execution of the Purple Fox rootkit.
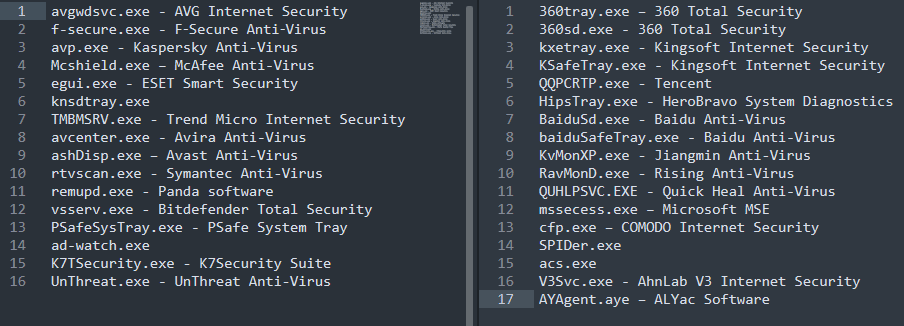
After executing the last stage, the Purple Fox rootkit, some AV processes are terminated. For this purpose, the following processes are matched at the start:
Figure 4: Antivirus processes terminated during the Purple Fox rootkit execution.
As expected, the criminals are notified during the malware execution, and all the gathered information is sent to the C2 server.
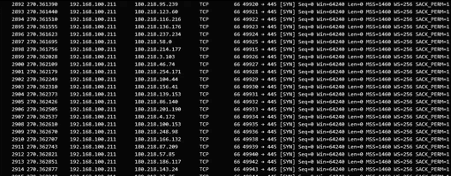
When hosted with success on the victim-side, Purple Fox rootkit can explore SMB vulnerabilities and adjacent access machines by attempting weak passwords and port scanning other networks — a well-known process discovered in 2018 when it was detected the first time.
Figure 5: Purple Fox rootkit SMB auth attempts.
The rootkit is equipped with a wormable feature capable of using the victims' email applications and disseminating the threat in the wild to propagate itself.

Become a certified reverse engineer!
Understanding Purple Fox
Purple Fox rootkit is on the rise and equipped with the most advanced TTP to remain stealthy on the victims' machines, thus evading cybersecurity defense. With the wormable capability in place, this threat can disseminate itself in the wild, targeting more users without additional effort from the malware operators.
Although there is no perfect formula to stop malware in general, some measures can be taken to prevent malware infection, namely:
- Do not execute files provided from unknown sources.
- Keep software updated, including AV and EDR systems.
- Share the "bad feeling" with the security teams when something strange happens. For example, if you execute a single binary file and the computer reboots.
- Make malware and phishing training a mandatory rule in your life because everyone uses the Internet and online services every day.
Let's take malware protection seriously and be proactive.
Sources:
- Purple Fox propagate as a worm, Exclusive Networks
- PF rootkit, Guardicore
- PurpleFox rootkit analysis, Minerva Labs