Bahamut Android malware and its new features
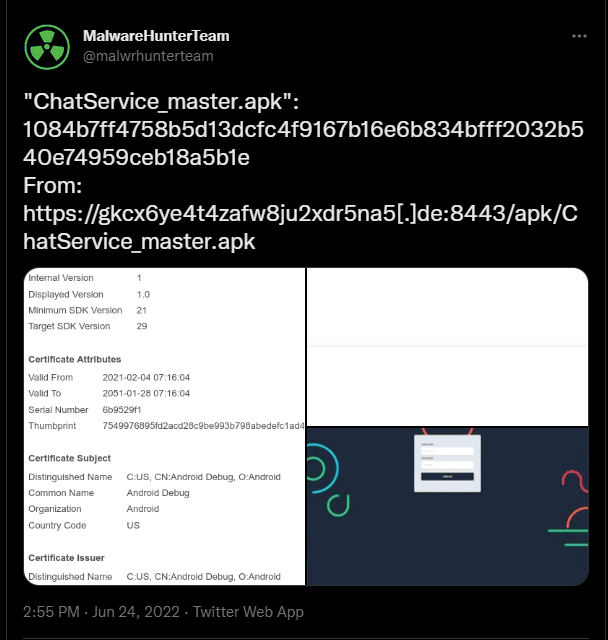
Bahamut is an APT group active since 2017 and is attacking mobile user’s after a year of silence. The first alert of this new campaign was seen on Twitter, with the MalwareHunterTeam publishing new indicators of comprising (IoCs) about a new malware piece. Details on the malicious APK are shown below.
Figure 1: Malicious APK from the newest campaign of the Bahamut APT group.
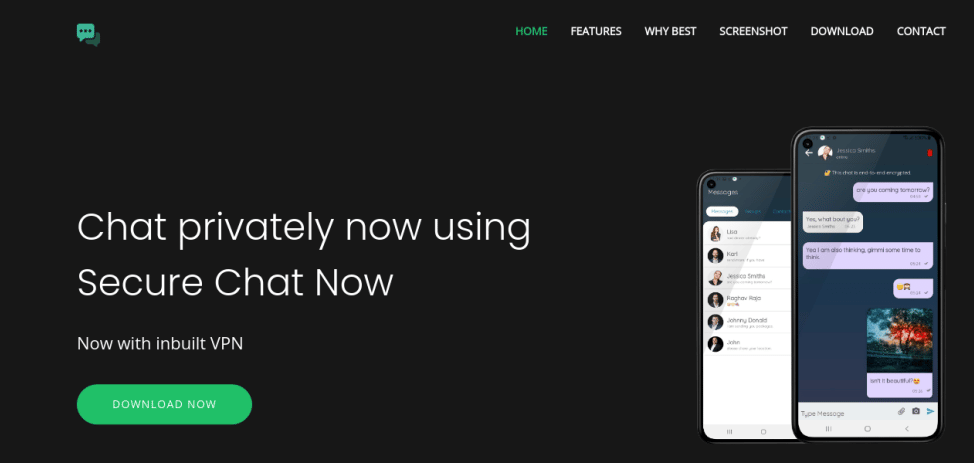
The new campaign has been ongoing since April 2022, and the operators behind the threat developed a website to download a potential legitimate app to lure victims. As mentioned by some security experts, “the phishing sites were masked as genuine websites for downloading a messaging application that provides secure communication.”

Become a certified reverse engineer!
In addition, the malicious application has also been distributed via obscene websites in the wild by criminals.
Figure 2: Malicious website pretending to be a genuine mobile platform for secure messaging (source).
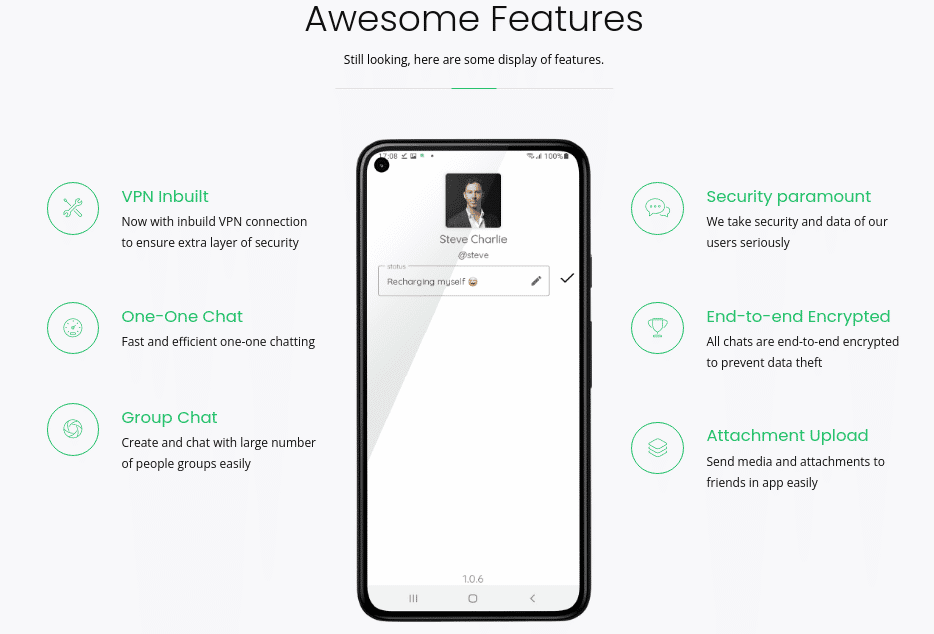
As mentioned in a publication by Cyble, the phishing website looks professional, and the criminals are presenting the application features on the Features menu and the Contact Us and Subscribe page, as observed in Figure 3 below. With these details in place, victims are convinced to download the malicious APK and install it on their devices.
Figure 3: Features of the malicious APK from the Bahamut ongoing campaign.
As can be seen, criminals are offering a lot of features, including:
- VPN inbuilt: Now with an inbuild VPN connection to ensure an extra layer of security.
- One-one chat: Fast and efficient one-one chatting.
- Group chat: Create and chat with many people groups easily.
- Security paramount: We take the security and data of our users seriously.
- End-to-end encrypted: All chats are end-to-end encrypted to prevent data theft.
- Attachment upload: Send media and attachments to friends in-app easily.
Digging into the APK details
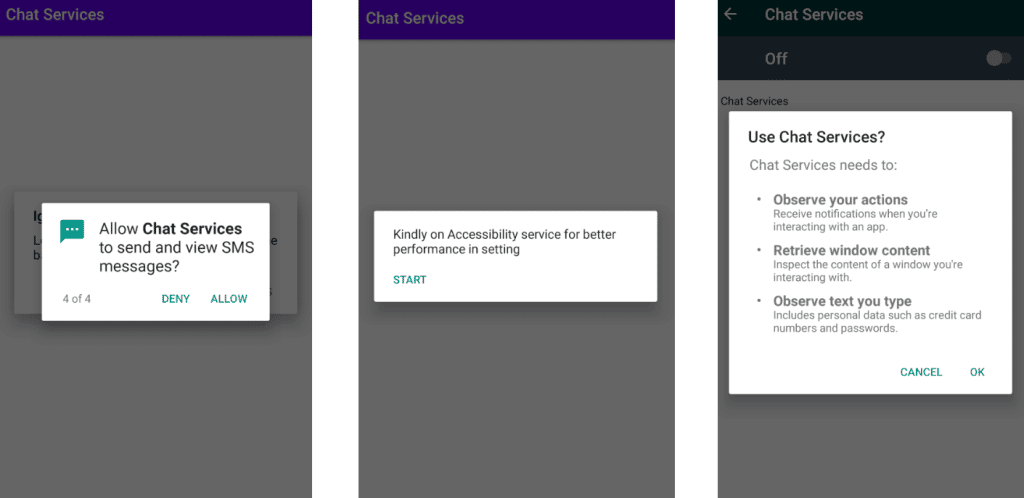
The malicious Android package file abuses certain permissions requested during the installation process. Some of them are READ_SMS, READ_CONTACTS, READ_CALL_LOG and RECEIVE_SMS.
Figure 4: Part of app permissions requested during the installation process (source).
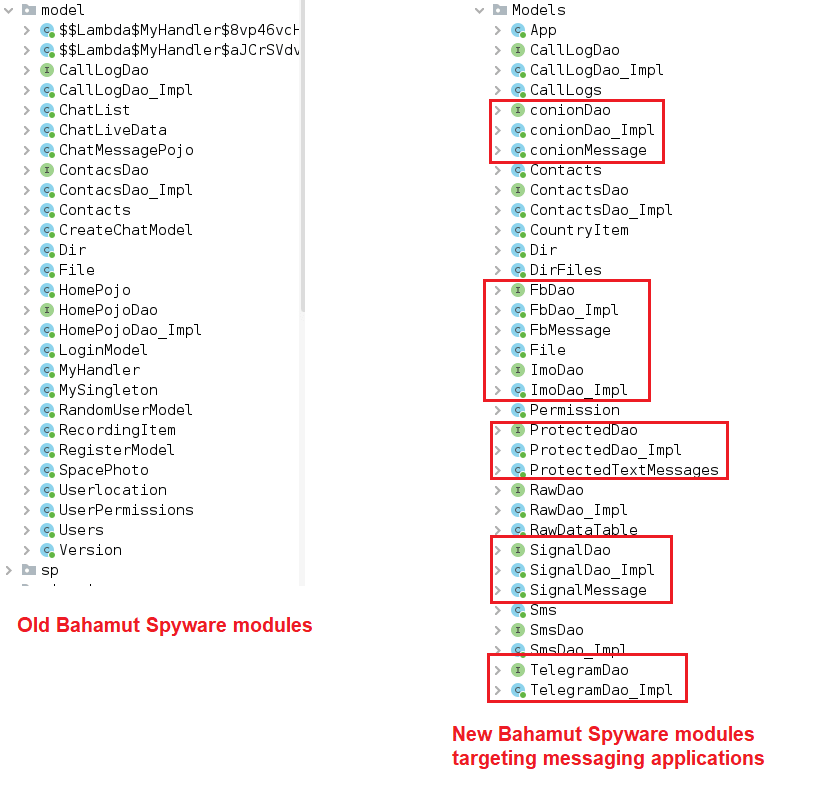
Looking at the app permissions is expected the abusage of chatting applications due to the nature and past campaigns in which Bahamut groups had been involved. By comparing the similarities between this malicious APK and old samples of Bahamut Android Spyware, the Cyble team observed that some extra modules were added. These modules are related to messaging applications, including Viber, Imo, Signal and Telegram.
Figure 5: Similarities between the Bahamut Android Spyware sample modules and the new Android package file distributed in 2022 (source).
In detail, the target applications are the following:
- com.viber.voip
- com.protectedtext.android
- com.facebook.orca
- com.imo.android.imoim
- org.telegram.messenger
- com.whatsapp
- com.secapp.tor.conion
- org.thoughtcrime.securesms
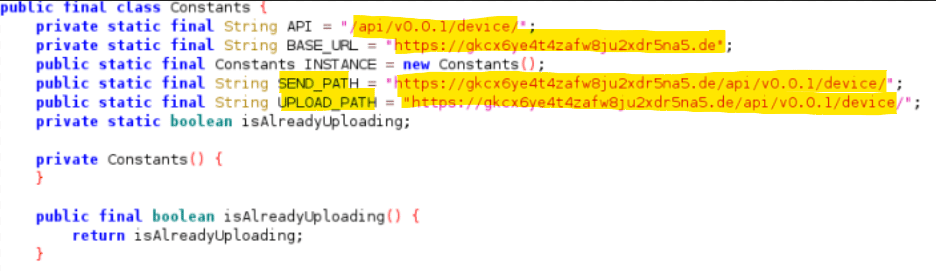
The application executes in the background, captures the victims’ chats and secrets, and sends all the information to the malicious C2 server. Also, details from internal storage, such as documents and photos, are obtained and stolen by criminals.
Figure 6: Command and Control (C&C) server used in the Bahamut campaign in 2022.

Become a certified reverse engineer!
Preventive measures against the Bahamut malware
Mobile malware has been distributed with new and dangerous techniques for spreading and manipulating data or stealing users’ secrets.
These malicious pieces use social engineering schemas to lure victims into downloading malicious applications and executing them on their devices. After that, and taking advantage of legitimate applications such as Telegram, Signal and WhatsApp, criminals can perform a lot of malicious activities, including:
- Disseminating malware via messages
- Stealing the users’ secrets from legitimate applications or the internal storage
- Creating fake messages and sending them via legitimate applications
- Extort users by threatening to send sensitive data or malicious links to all user’s contacts or WhatsApp groups (the best target from the malicious perspective).
In this sense, prevention is crucial to stop these kinds of threats. Before downloading and installing a new app, check if the source is trusted and if app permissions align with its purpose.
Sources:
- Bahamut Android malware, Cyble
- Android Trojan bankers, Segurança-Informática