Pingback malware: How it works and how to prevent it
A new malware called pingback that uses ICMP for communicating with its C2 server was discovered by researchers recently. In this article, we will understand how this malware can bypass its detection taking advantage of the ICMP, learn about its modus operandi, and also provide some measures to detect threats of this nature.
As mentioned by the research team, the malicious file — a Windows DLL — called oci.dll is dropped into the Windows system folder via other malicious vectors explored early by criminals or even by another malicious process running on the target machine. In this case, the DLL is not loaded into the memory using the rundll32.exe utility but using DLL sideloading / DLL hijacking technique. This technique is very popular in the malware landscape, and several types of malware, such as Javali trojan, are using it to perform its operations.
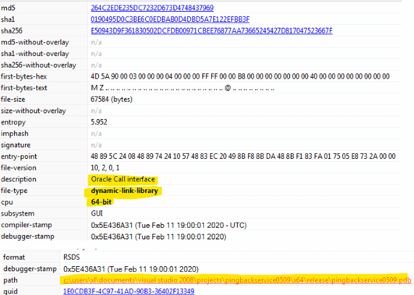
Figure 1: Details of the malicious oci.dll file (pingback malware).
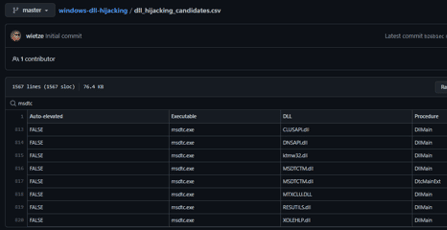
Interestingly, the origin of the malware's name is associated with the path present in the PDB “pingbackservice0509.pdb”. In detail, this DLL mimics a legitimate DLL that is loaded into the memory, taking advantage of binary files present on this list of over 300 Windows executables that are perfect candidates for DLL hijacking.
Pingback malware uses the Microsoft Distributed Transaction Control (msdtc) service to load the oci.dll file as presented below.
Figure 2: List of possible candidates many times used for DLL hijacking.
Modus Operandi of Pingback malware
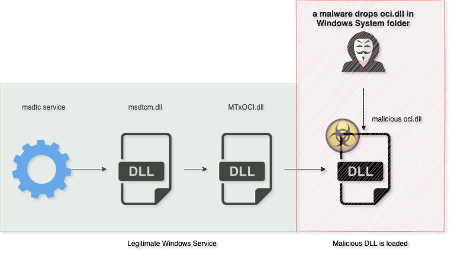
The first trigger happens when the msdtc service starts by the initial stage or uses another attack vector. The legitimate service searches for 3 Oracle ODBC DLLs to load: oci.dll, SqlLib80.dll, and xa80.dll files.
Figure 3: Malicious oci.dll is indirectly loaded by msdtc service (source).
The legitimate oci.dll is an Oracle Call Interface library responsible for communicating with oracle databases. Nonetheless, that DLL is not part of the Windows DLLs (typically available on system32). The attacker must copy it into the system folder manually or use an initial stage, attack vector, or even malware dropper.
"So, in theory, an attacker with system privileges can drop a malicious DLL and save it using one of the DLL filenames that MTxOCI loads," explain the researchers.
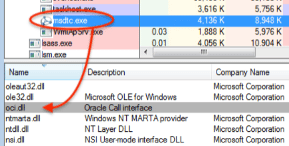
If the oci.dll malware exists, then the legitimate service can load the malicious DLL using the DLL export table maintained by the criminals.
Figure 4: Malicious DLL loaded into the memory by the msdtc.exe legitimate binary using the DLL hijacking technique (source).
ICMP tunneling for communication with the C2 server
Every time the legitimate executable executes the malicious DLL, it takes advantage of the ICMP protocol for communicating with the C2 server.
The reason criminals use this protocol is because there are no ports, and it doesn’t run over TCP and UDP — traffic often inspected by security appliances to flag malware activities.
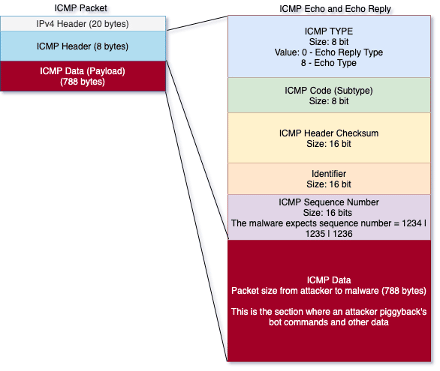
"The ICMP data section is where an attacker can piggyback an arbitrary data to be sent to a remote host. The remote host replies in the same manner, by [piggybacking] an answer into another ICMP packet and sending it back," said Macrohon and Mendrez.
Figure 5: ICMP packet. The size of the ICMP data sent by the attacker is always 788 bytes (source).
In detail, pingback malware listens for any inbound ICMP packets and parses the packets based on sequence numbers: 1234, 1235, 1236. An incoming ICMP packet with sequence 1234 indicates that the request contains a payload or commands to be executed. In contrast, 1235 and 1236 are just pingbacks, a way of keeping track and understand if a specific request has been received.
This malware can perform some operations, including (i) execute a shell, (ii) download and upload files using TCP/ICMP protocols to bypass internal defenses, and (iii), execute arbitrary commands on the infected machine.
The essence of these commands is to transmit data between the C2 server and the infected machines and enable a remote attacker to execute additional payloads on the target machine.

Become a certified reverse engineer!
Understanding ICMP threats
Threats leveraging ICMP tunnels to avoid detection are not new. This protocol is used many times by criminals to masquerade their activity, transfer sensitive information between the infected machines and C2 server, receive commands, payloads and so on. Because ICMP protocol is usually used for diagnostic purposes, it can be discarded for some security appliances in particular situations.
From the security point of view, a simple rule could be implemented to validate if an ICMP packet is malign, searching for a block of data with a size of 788 bytes or greater and with sequence numbers: 1234, 1235, and 1236. In addition, commands such as download, upload, shell, and exec present in an ICMP data packet should be considered an object of analysis and flagged as suspicious early.
Last but not least, be proactive and start taking malware protection seriously!
Sources
- Pingback analysis, Trustwave
- Pingback using ICMP protocol, BleepingComputer