SUNBURST backdoor malware: What it is, how it works, and how to prevent it | Malware spotlight
SUNBURST is a supply chain attack that takes advantage of a backdoor implanted in a supplier to target and compromise organizations indirectly around the globe. Orion, the SolarWinds software that was compromised by criminals, was used by about 33,000 public and private customers. Many of them were Fortune 500 companies and federal government agencies. The attack was discovered in December 2020, eight months after the original breach. It impacted U.S. government agencies, technology companies and countries including Canada, Belgium, Britain and Israel.
SUNBURST: The big picture
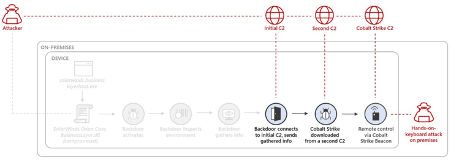
The SUNBURST supply chain attack uses the following workflow grouped into six main steps, also described by Cynet in its website.
1. Dribbling security appliances
This piece of malware was delivered in the form of a Windows DLL file (SolarWinds.Orion.Core.BusinessLayer.dll), implanted on the SolarWinds update package. The backdoored package was delivered to SolarWinds customers. As the package was digitally signed by SolarWinds, it is seen as trusted software and deployed in their internal networks, bypassing EDR systems and antivirus by default. The problem starts at this point, and criminals, knowing the typical modus operandi of antivirus software, are using this approach to disseminate malware in the wild.
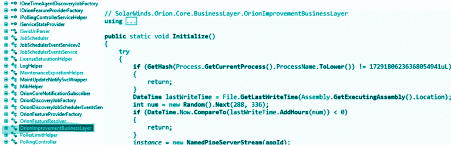
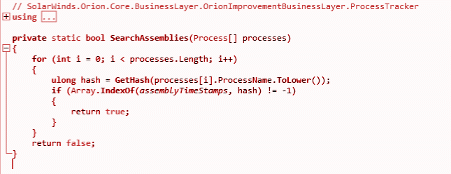
Criminals were able to modify the software and add a malicious backdoor inside the SolarWinds Orion plugin DLL called “SolarWinds.Orion.Core.BusinessLayer.dll” as observed in Figure 1 below.
Figure 1: DLL call modified by criminals to introduce the malicious code (backdoor).
As observed, the backdoor waits 12-14 days before sending its first ping to the C2 server, a technique utilized to evade detection on the network layer. With this behavior in place, detecting and relating it with malicious purposes is harder from the security point of view.
2. The first connection with the C2 server
After the update and the first communication with the C2 server, some basic information is sent, including the computer username, IP address and OS version in order to determine if the machine is able to be explored, and also to prevent a second infection.
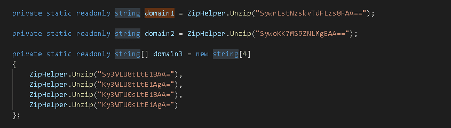
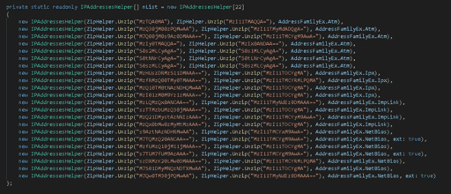
SUNBURST uses a custom domain generation algorithm (DGA) to determine the IP address of its C2 server. After establishing the communication it the C2 server, the backdoor tries to mimic the legitimate SolarWinds OIP (Orion Improvement Program) communication to masquerade its activity and, thus, bypassing and evading security appliance and monitoring systems. Figure 2 below presents part of the code with the malicious implementation of the DGA algorithm.
Figure 2: Process used by SUNBURST backdoor to generate the C2 address (source).
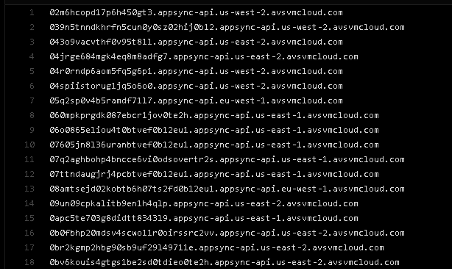
Some examples of FQDNs queried by SUNBURST can be observed below and are also available on GitHub:
Figure 3: FQDNs queried by SUNBURST during its execution.
3. Evading endpoint detection
This “step” is something always in the mind of criminals: how to evade detection. In the first place, when installed on the target machine,
the backdoor waits 12-14 days before sending its first ping to the C2 server, a clear sign the main goal of criminals is putting the backdoor away from the eyes of the threat detection platforms and endpoint agents such as antivirus.
To accomplish this task, the malicious code checks, in a loop, the existence of specific drivers and processes on the target machines during the backdoor execution. If any hardcoded process is detected, the malware execution is terminated.
Figure 4: Block of code responsible for detecting target process names during the SUNBURST execution.
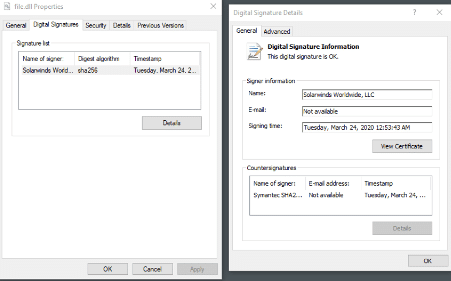
In addition, the backdoor tries to disable security processes by changing its registry keys, evading specific endpoint security measures and also impersonating trusted network entities. A clear signal about this is that criminals stole the certificate’s private key of SolarWinds, they signed the malicious DLL and replaced it in the official repository.
Figure 5: Malicious DLL digitally signed by SolarWinds Worldwide, LLC.
4. Command & control (C2) activity
The backdoor does not communicate with its C2 server after its deployment. Instead, it waits some days, and after that, the first ping is then sent. The malicious DLL takes advantage of the SolarWinds application layer protocol to masquerade the malicious traffic, and in this way, C2 activity will not trigger any security alerts.
In order to avoid detection, SUNBURST executes DNS requests using a random delay. In some cases, the delay time between requests is more than 120 minutes for each victim and domain.
SUNBURST also sends HTTP requests to the C2 domain using a pseudo-random, benign-looking URI to invoke commands, passing, thus, the payload within the HTTP body in JSON format (/swip/upd/Orion[.]Wireless[.]xml), as stated by Varonis in its publication.
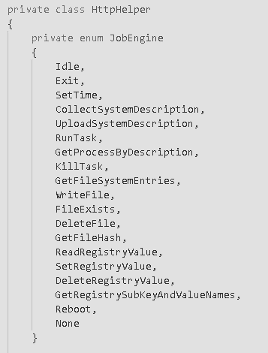
The operations performed are reading and writing files into the target machine, restarting the machine, and so on. The complete list of operations can be found in Figure 6 below.
Figure 6: SUNBURST backdoor operations and commands (source).
5. Moving laterally
The main goal of this kind of malicious incident is access to the internal secrets of organizations. In this sense, SUNBURST creators used malware capabilities, in particular, PowerShell scripts to gain access to additional systems in the targets’ internal networks.
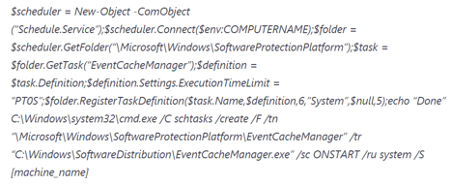
As detailed by FireEye and Volexity, lateral movement activity was observed via PowerShell remote task creation:
Figure 7: Lateral movement activity observed during the backdoor execution.
In addition, the backdoor is also capable of delivering second-stage payloads, which are part of the CobaltStrike software suite.
Figure 8: SUNBURST lateral movement using CobaltStrike (source).
6. Secret’s exfiltration
This is the most important step when criminals are compromising a network. They gain internal access to a target system, and they exfiltrate sensitive data using Powershell email commands or even transmitting compressed files using HTTP requests; when this scenario is possible. In specific situations, criminals can take advantage of other internet protocols such as ICMP and DNS to exfiltrate information from internal networks jumping, thus, the internal barriers like firewalls, IDSs, and so on.
Figure 9 below shows the structure of an HTTP POST request used to send information to the C2 server.
Figure 9: Structure of the POST request used by SUNBURST backdoor to communicate with its C2 and exfiltrate data (source).
In other scenarios like this, criminals end the infection chain with the deployment of ransomware demanding payment for the stolen data. In this case, the strategy was different, because one of the main objectives of the criminals was not to arouse any suspicion and alarm of their presence.

Become a certified reverse engineer!
The woes of SUNBURST backdoor
SUNBURST backdoor poses as one of the most dangerous supply chain attacks seen in the last decade. Identifying and blocking potential points of exposure is a really hard task depending always on the dimension of the environments, organizations and so on. However, some steps should be taken into account to improve the security posture, namely:
- Monitorization and logging: you need to look at log data and analyze past activities. That information can be useful to investigate past breaches, popular vulnerabilities and detecting incidents in real-time. A short-time reaction is a key to prevention.
- Host-based agents: as obvious, security logs are not enough to detect and protect environments against SUNBURST attacks. In this sense, the usage of host-based agents like EDR agents installed on all network devices is a mandatory measure to mitigate the risk of infection and detect malicious activity early.
- Visibility and management: an initial best practice starts by identifying all the devices on the network creating a panoramic vision about everything. With this in place, updating and managing all the vulnerabilities and problems in your network will help you to mitigate and measure the risks of an incident of this nature.
- Threat hunting: a good starting point to identify SUNBURST activity is searching for the IoCs provided by FireEye in DNS logs. Threat hunting is always a hands-zone measure to detect anomalous activity or artifacts when they are not detected by the security software, as threats of this nature are always designed to bypass the most advanced security mechanisms.
Sources
- Attack Flow, C2 Protocol, and Prevention, Cynet
- SolarWinds SUNBURST backdoor assessment, HornetSecurity
- Why the Sunburst Malware Was So Unique, Deepinstinct
- Inside the Stealthy APT Campaign, Varonis
- Analyzing Solorigate, Microsoft
- Deep dive into the Solorigate, Microsoft
- How Sunburst Sends Data Back to the Attackers, Symantec