Deadbolt ransomware: The real weapon against IoT devices
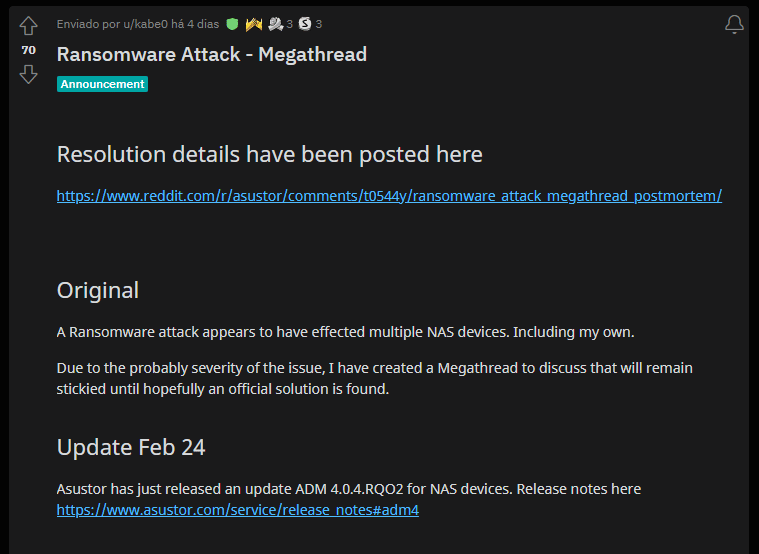
Deadbolt ransomware is on the rise. More recently, this malware has impacted QNAP NAS appliances and ASUSTOR network-attached storage (NAS) devices. One of the most popular threads about these attacks can be found on Reddit, where a ransomware victim explains how to identify damaged devices and defeat this ransomware.
Figure 1: Deadbolt thread on Reddit (source).

Become a certified reverse engineer!
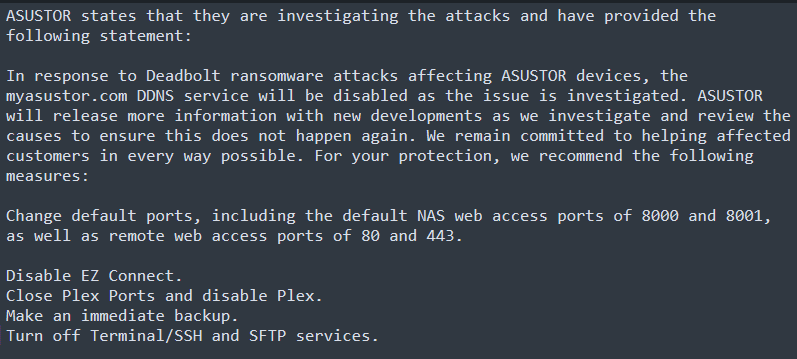
The QNAP NAS and ASUSTOR device's files have been damaged and encrypted by Deadbolt ransomware. According to the ransomware operators, the malicious piece takes advantage of a zero-day vulnerability. Although there are few details about the root causes, ASUSTOR explained that the NAS devices had been encrypted via a flaw in the PLEX media server os EZ Connect that allows access to the devices.
Figure 2: Advisory by ASUSTOR in response to the Deadbolt attacks.
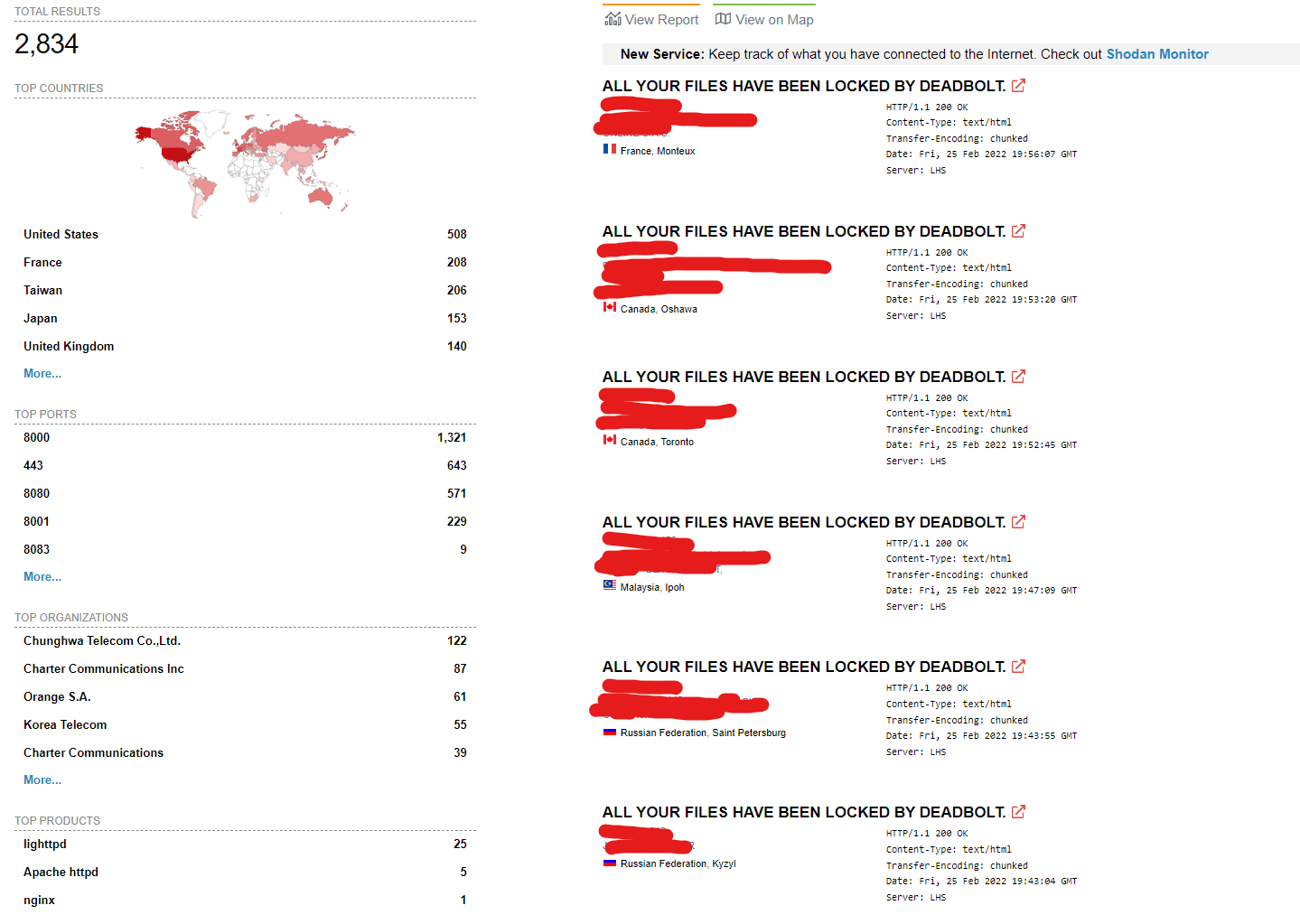
By using Shodan dork, we can observe that a large number of devices (2834) were hit with this ransomware and are still damaged.
Figure 3: 2834 devices still damaged by Deadbolt ransomware at the moment of analysis.
In detail, we can observe around 500 devices geolocated in the U.S., followed by France, Taiwan and Japan as the most impacted countries.
Deadbolt ransomware details
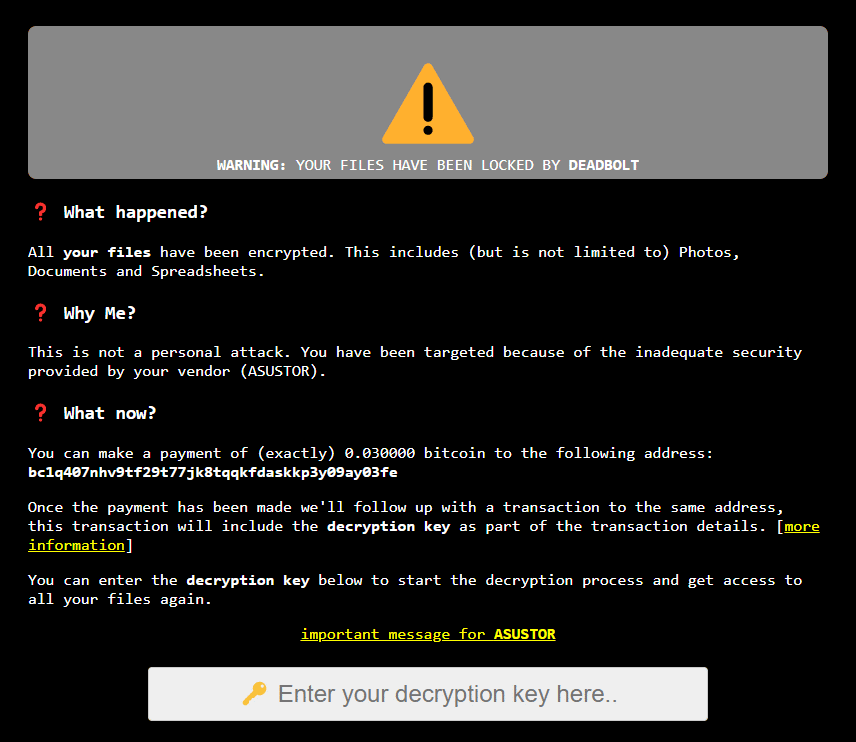
The ransomware damages all the files available on the devices, adding the .deadbolt extension to each file during encryption. The ransom note highlights that victims need to pay a ransom of 0.03 bitcoins ($1.100) to a unique Bitcoin address in exchange for a decryption key.
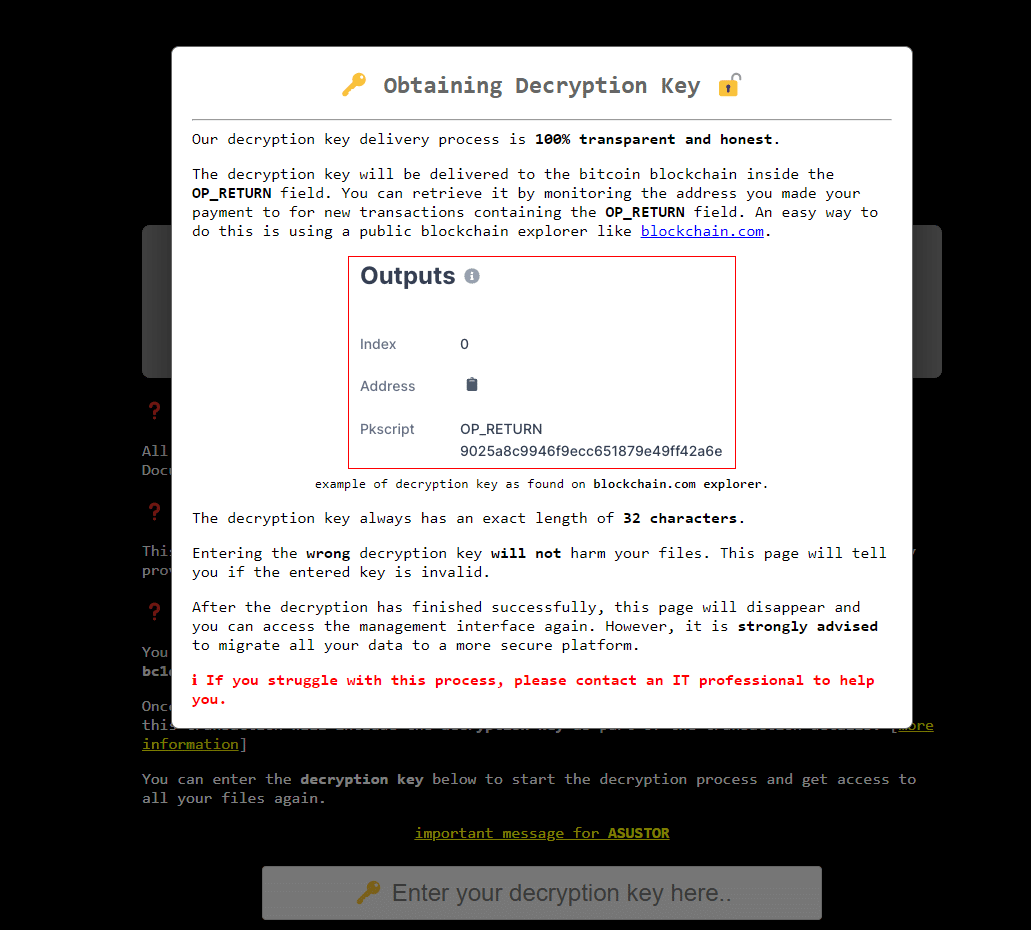
During its execution, the ransomware drops the ransom note on the “login page” of the devices announcing the following steps to recover the files.
Figure 4: Ransomware note dropped on the login page of the damaged devices.
According to the ransomware operators, a follow-up transaction will be added to the same address after the payment that includes the decryption key.
Figure 5: Details about file decryption - Deadbolt ransomware.
Regarding the NAS devices, there is a trick that can allow to access the login page of the device bypassing the ransomware note. In this sense, the admin page can be accessed by using the following URLs:
http://IP:8080/cgi-bin/index.cgi
or
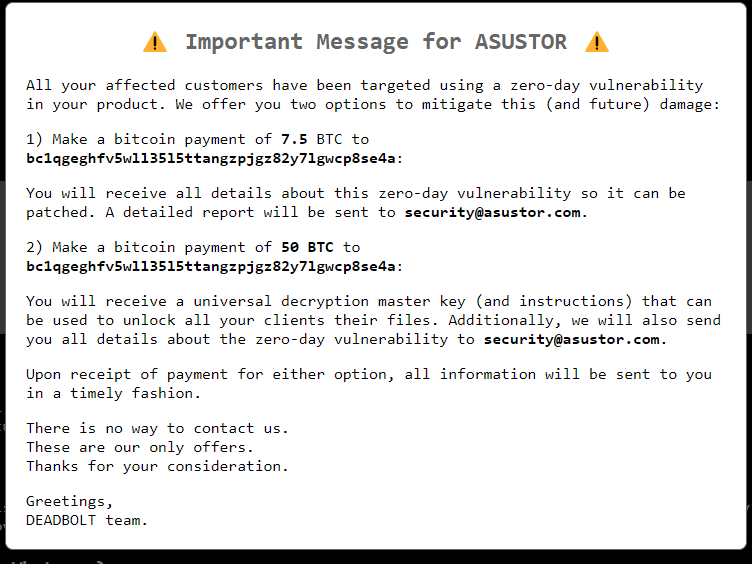
https://IP/cgi-bin/index.cgi It can still be visible in the ransomware note as a message, especially for the different vendors. In the case of ASUSTOR, the ransomware operators can disclose details about the zero-day vulnerability if ASUSTOR pays them 7.5 BTC worth $290.827. On the other hand, if payment of 50 BTC ($1.85 million) was received, a global private key would be sent, and all the damaged devices around the globe could be decrypted.
Figure 6: Import message for Asustor.
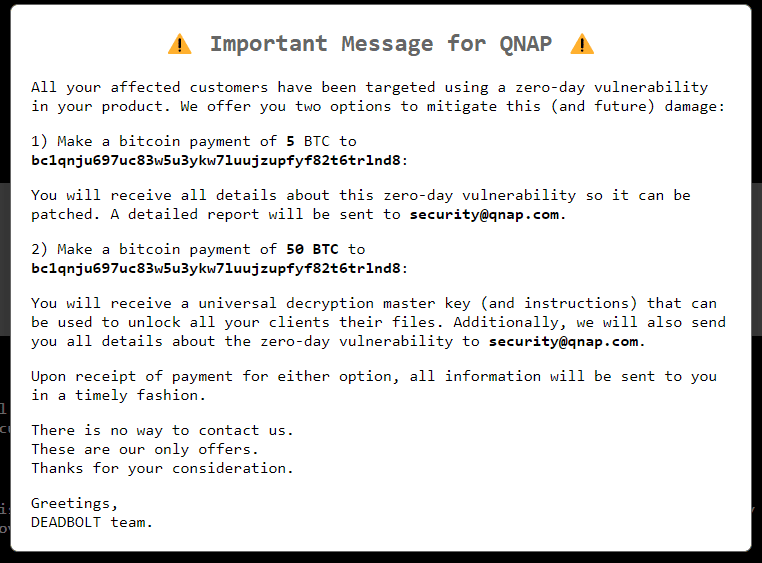
A similar message to QNAP can also be observed below.
Figure 7: Import message to QNAP.
While digging into the Deadbolt details, we find that the ransomware operates by first installing a binary file in the /mnt/HDA_ROOT/ folder. Then, the ransomware executable is launched using a config file containing a lot of information, including the encryption key.
The /share folder on QNAP devices is then encrypted — this location is the place that stores the users’ files and folders.
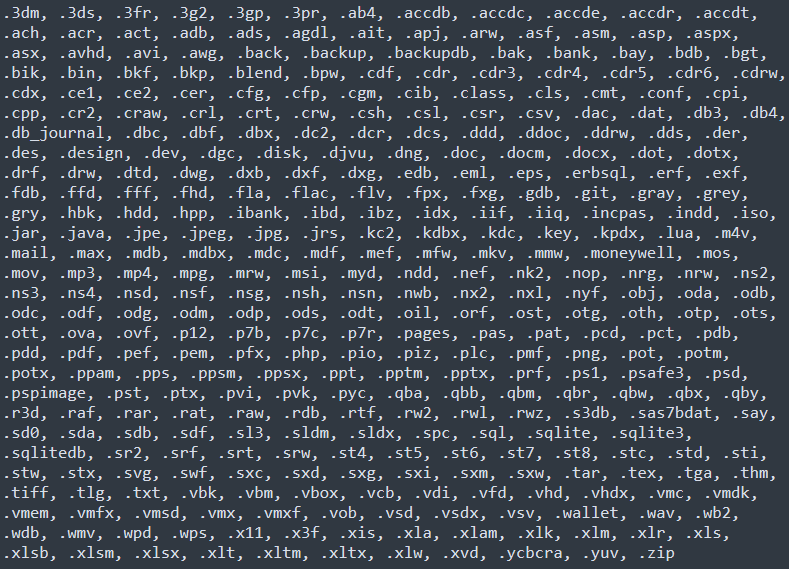
During its execution, Deadbolt encrypts files within specific file extensions. Figure 8 below details all the targeted extensions.
Figure 8: Targeted file extension - Deadbolt ransomware.
The files are encrypted with the AES128 algorithm, and the .deadbolt extension is appended to the file names. For instance, the "a.png" file will be renamed "a.png.deadbolt."
How to fix damaged devices
At first glance, when the decryption key is entered on the ransom page, it will be converted into a SHA256 hash and compared with the hash of the victim's decryption key and the hash of the master decryption key.
The SHA256 hash for the master decryption key is the following: 93f21756aeeb5a9547cc62dea8d58581b0da4f23286f14d10559e6f89b078052.
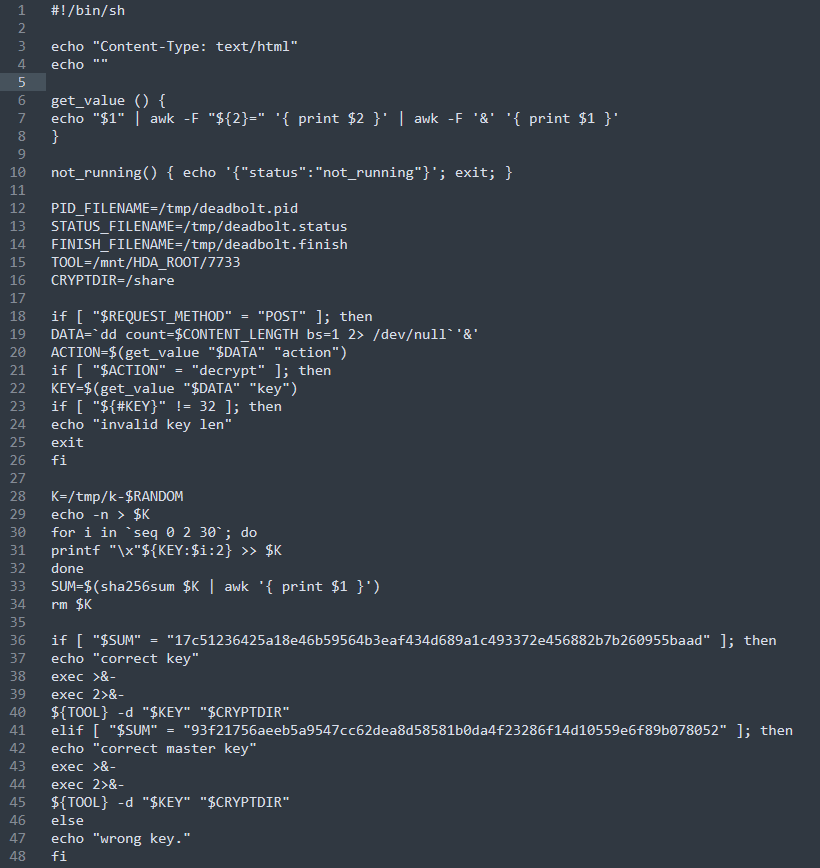
In detail, the next script can be used to decrypt damaged devices with the master decryption key:
Figure 9: Decryption script of Deadbolt ransomware (source).
Nonetheless, in the case of the QNAP devices, during the firmware updates, the executable files for decryption and the index.html page with the ransomware note are deleted — a scenario that prevents the decryption of the file system.
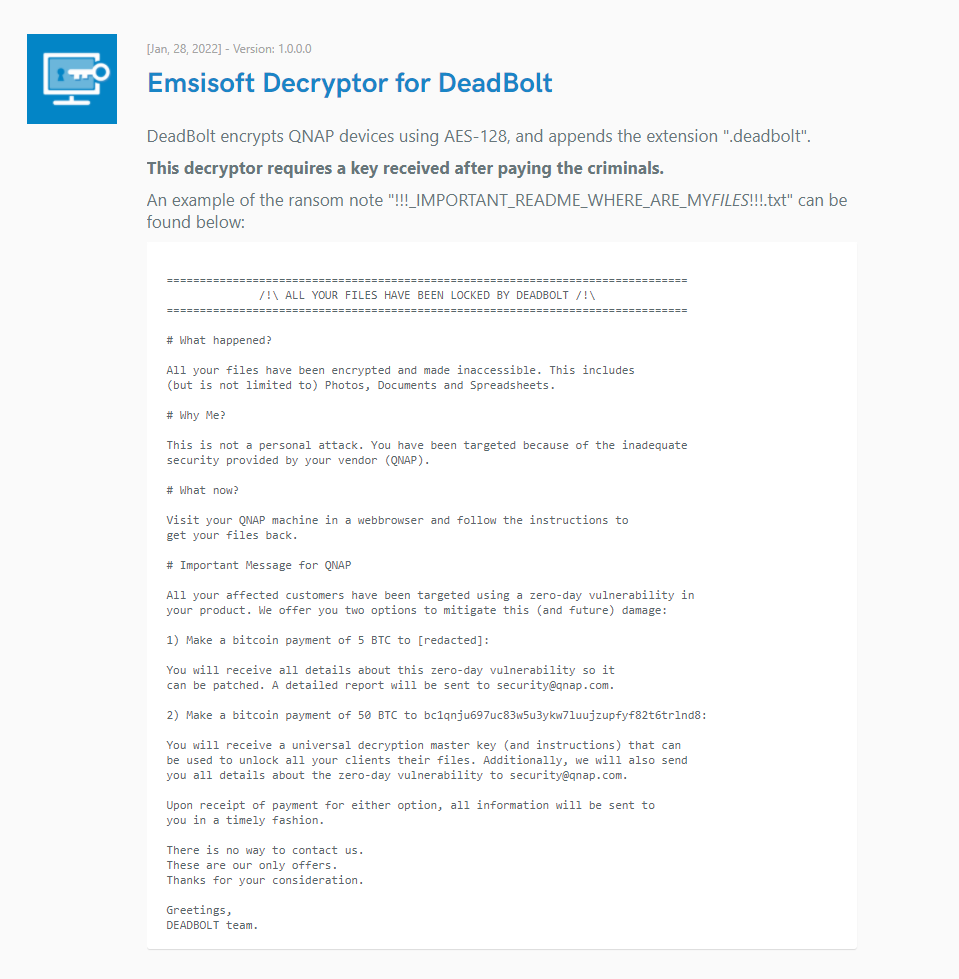
In this sense, a security expert developed a free Windows decryption that can be downloaded from Emsisoft. With this executable, the files can be recovered without paying the ransom.
Figure 10: Deadbolt decryptor by Emsisoft.
More details about the decryption process are here.
Sources:
- Deadbolt script, Informaticacoslada
- Ransomware attack megathread, Reddit
- Deadbolt attacks QNAP devices, BleepingComputer
- Deadbolt details, TheHackerNews