Analysis of Nokoyawa ransomware
Ransomware is an ongoing threat. New variants are constantly detected, and existing threats keep adding new features and techniques for performing malicious operations. A notable example is Nokoyawa ransomware, a new variant possibly related to Hive and Babuk.

Become a certified reverse engineer!
Digging into the details of Nokoyawa
At first glance, the Nokoyawa binary is not packed and protected by ransomware authors. As seen below, we can observe plain-text strings indicating some of the features of this ransomware.
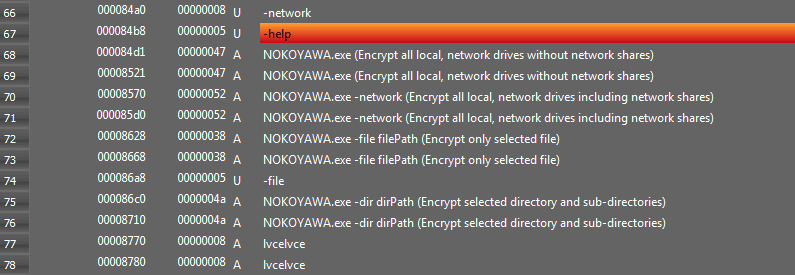
Figure 1: Strings of Nokoyawa ransomware not obfuscated.
Nokoyawa command line options
Nokoyawa has hardcoded several command line possibilities for customized executions, as shown in Figure 1, namely:
- -help: Print the list of available commands
- -network: Encrypt all local, network drives including network shares
- -file filePath: Encrypt a single file
- -dir dirPath: Encrypt selected folder and sub-folders
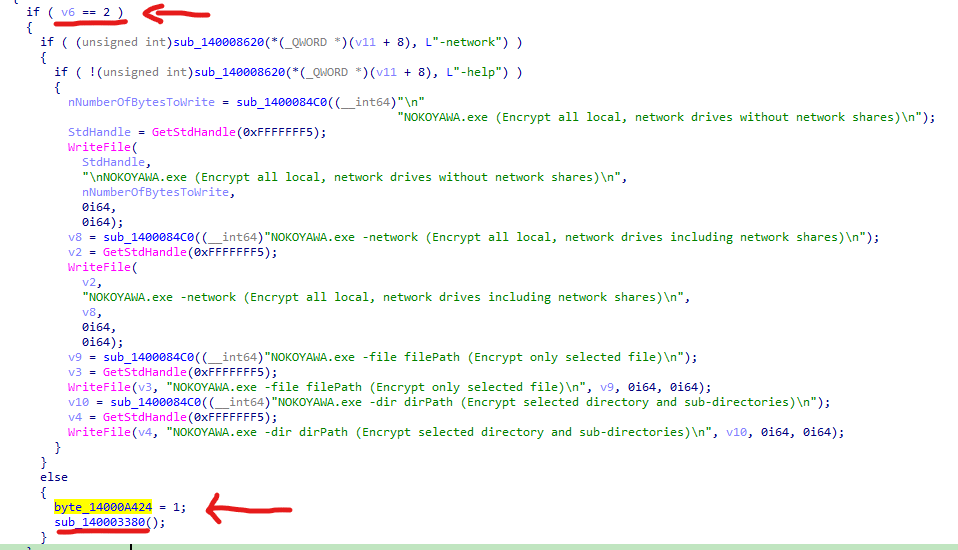
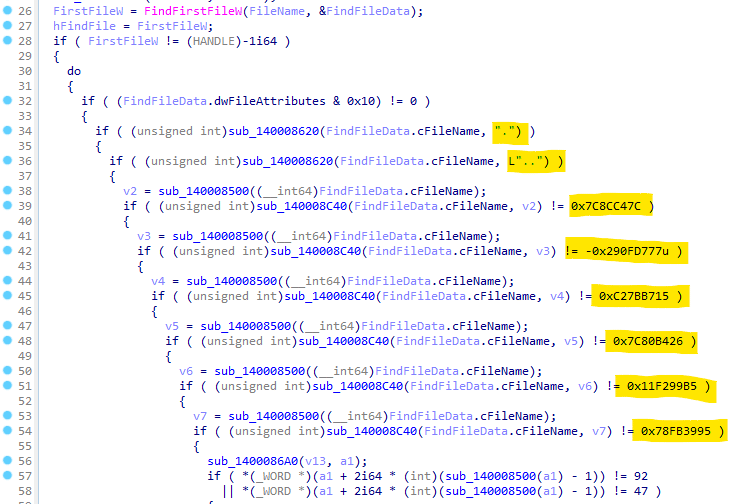
If no argument is provided on the terminal execution, Nokoyawa encrypts all local drives and volumes by default. As highlighted below, if the variable “v6” — the number of arguments from the command line — is not equal to 2, the ransomware passes the execution to the “sub_140003380()” function and starts the encryption process on all the available volumes.
Figure 2: Nokoyawa encrypts all the volumes and drives by default if no argument is passed on the command line.
Skipped files during the encryption process
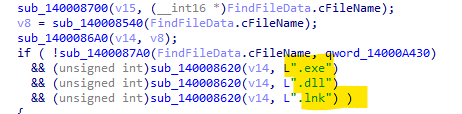
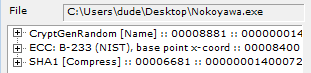
This ransomware takes advantage of multi-threading to encrypt files efficiently and quickly. Some files and extensions are skipped during the malware runtime. The folders are hashed (see list below), but the ignored file extensions are in clean-text: dll, exe and lnk.
Also, files with NOKOYAWA in their names are excluded during the process.
0x11f299b5 program files0x78fb3995 program files (x86)
0x7c80b426 appdata
0x7c8cc47c windows
0xc27bb715 programdata
0xd6f02889 $recycle.bin
Figure 3: Folders skipped during Nokoyawa execution.
Figure 4: File extensions ignore in runtime.
Encryption process
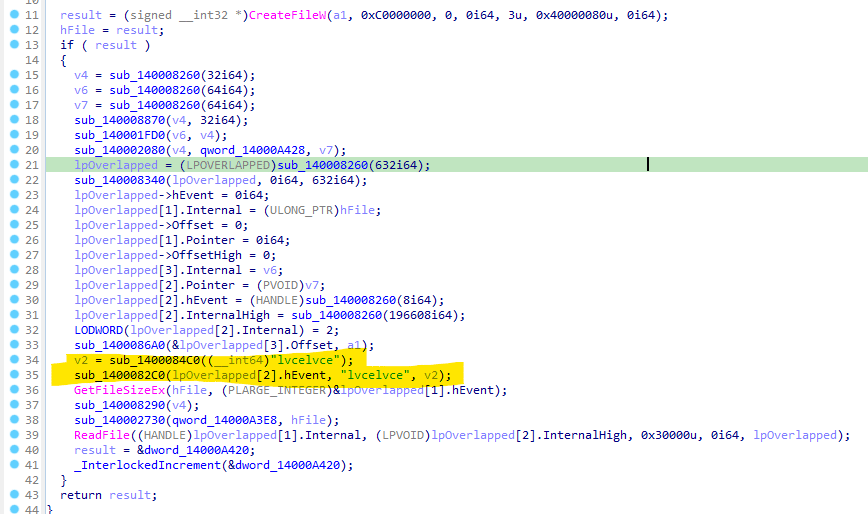
Nokoyawa uses the BCryptGenRandom() call from bcrypt.dll to generate 0x20 random bytes (seed), creating a fresh key-pair of elliptic-curve cryptography (ECC) - public and private keys. After that, the public key inside the malware and the pair generated in the previous step are used to generate a shared and symmetric SALSA20 key, which will be used to encrypt the target files. As shown below, the nonce used in SALSA20 is hardcoded: “lvcelvce.”
Figure 5: Beginning of the encryption process and the hardcoded nonce used in the SALSA20.
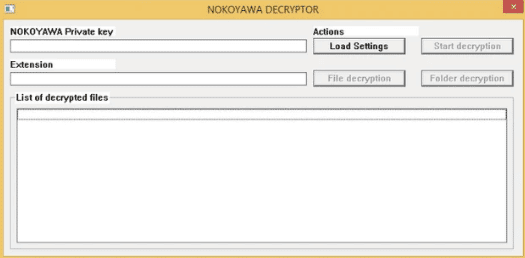
The SHA1 hash of the generated key is appended to the end of each damaged file, along with the public key and the string NOKOYAWA. In addition, the public key in the encrypted file and the private key owned by the Nokoyama operators are necessary to generate the SALSA20 symmetric key for decrypting each damaged file. Below is a picture of the Nokoyawa decryptor.
Figure 6: Nokoyawa decryptor.
Ransomware note
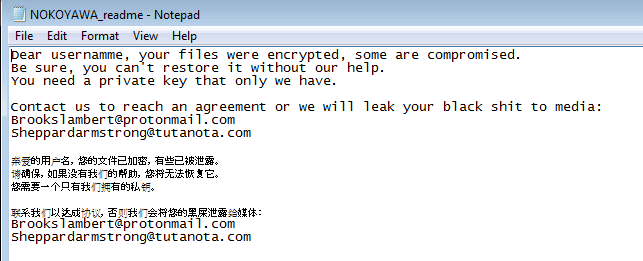
Each encrypted file has appended the .NOKOYAWA extension. The ransomware note called “NOKOYAWA_readme.txt” is also dropped into each folder with an English and Chinese version in the same file.
Figure 7: Nokoyawa ransomware note.

Become a certified reverse engineer!
Ransomware prevention measures
Ransomware is one of the most dangerous pieces of malware because it can compromise and leak sensitive data. It is costly and badly impacts the reputation of the affected brands. Because of this, a cybersecurity strategy to fight this threat is necessary.
Although there is no perfect formula for stopping ransomware incidents, implementing monitoring procedures, using host-based security solutions such as antivirus and EDR and increasing the use of canary files are elementary instruments that could help you avoid damage from these threats in the wild.
Sources:
- Ransomware related to Hive, TrendMicro
- New Nokoyawa Variant, Fortinet
- Nokoyawa Ransomware, SentinelOne
- Canary files, Infosec Institute