Sunnyday ransomware analysis
Sunnyday, one of the most recent pieces of ransomware, has impacted users worldwide. According to the publication Segurança-Informatica, “some similarities between other ransomware samples such as Ever101, Medusa Locker, Curator, and Payment45 were found. Although it has very similar features to the mentioned ransomware samples, we are not able to make any attribution to its threat group.”
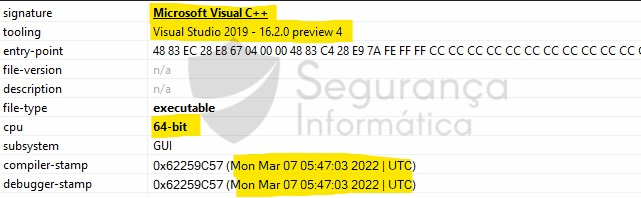
In detail, the Sunnyday binary is being disseminated as a 64-bit Windows file that was released on 07 March 2022 and was compiled and linked by criminals via Microsoft Visual Studio 2019.
Figure 1: SunnyDay release date, signature, and tooling details (source).
Digging into the details of Sunnyday ransomware
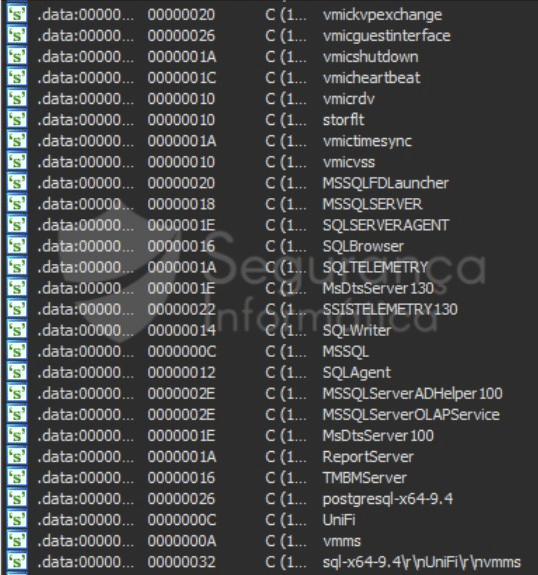
Sunnyday ransomware iterates over all the system services and tries to stop target services via the “ControlService()” call with the argument “SERVICE_STOP.” Services related to databases and backup services are shown in the full list below.
Figure 2: Hardcoded services found inside the SunnyDay ransomware sample (source).
On the other hand, the SunnyDay ransomware also uses a list of hardcoded processes in runtime to terminate specific programs. It gets the double-linked list of processes via the “CreateToolhel32Snapshot()” Win call and navigates among them by using the “Process32NextW()” call, a well-known technique largely observed in other malware families.
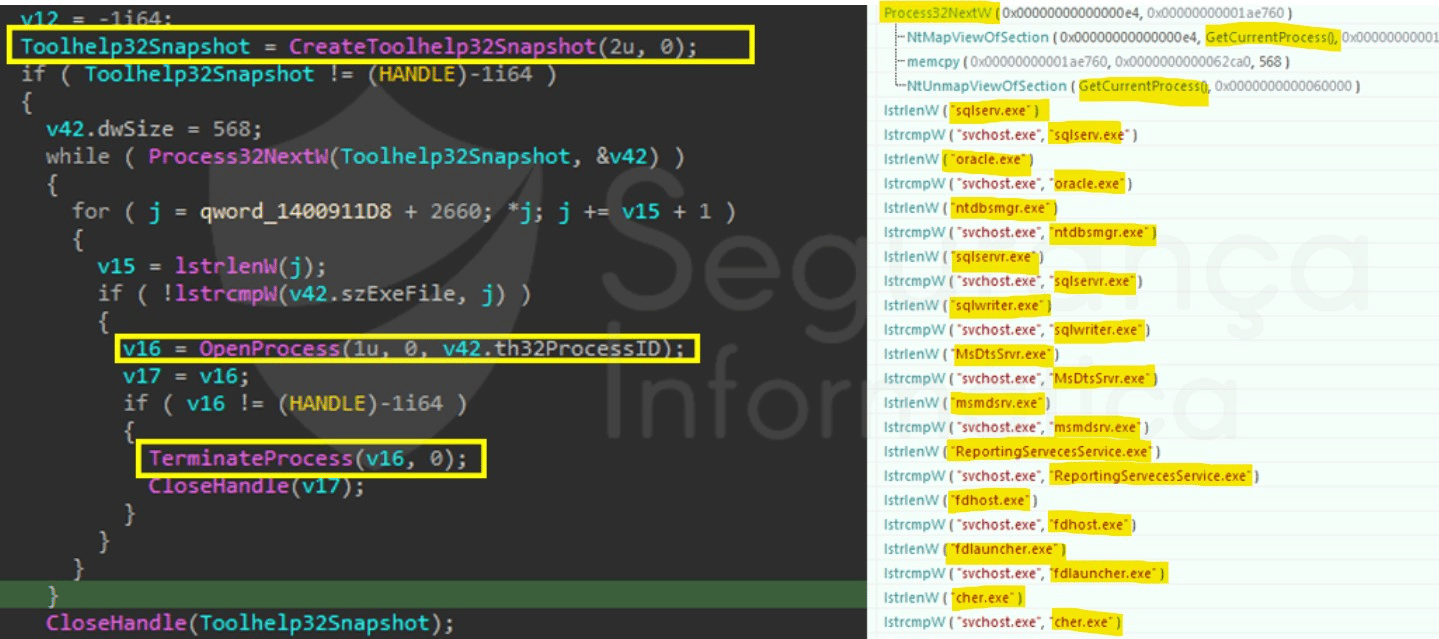
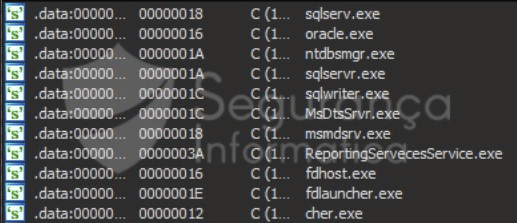
Figure 3: Sunnyday ransomware list of hardcoded processes (source).
Salsa20 speeds up the encryption process
SALSA20 stream cipher is an algorithm increasingly used by ransomware because it can encrypt content at high speed. This algorithm has been observed in other ransomware samples, such as Ever101 and Medusa Locker. The element “speed-rate” is one of the important parameters from the criminals' point of view because the encryption process must be as fast as possible to damage the largest number of files in a short period, thus reducing the victim's available reaction time. “It offers speeds of around 4–14 cycles per byte in software on modern x86 processors and reasonable hardware performance,” says Segurança-Informática.
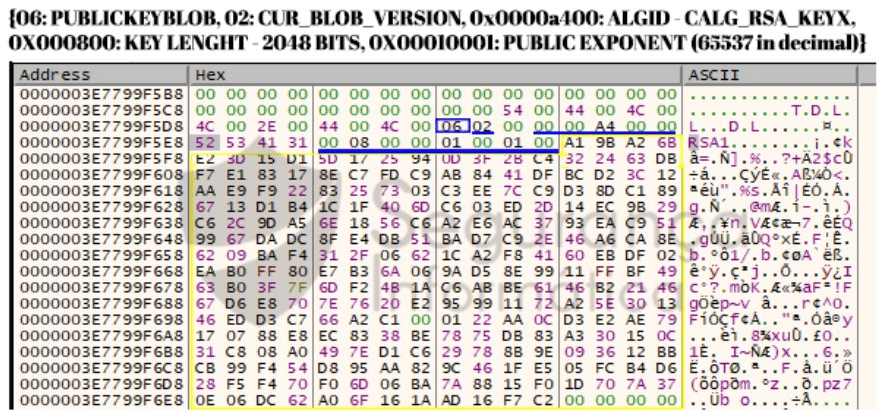
The ransomware sample comes with an RSA public key in a blob format and the malware takes advantage of Windows APIs (CryptoAPI) to carry out the encryption process. The blob is composed of the AlgID “CALG_RSA_KEYX,” which is a 2048-bit key with the Public Exponent: 65537 in decimal.
Figure 4: Sunnyday ransomware public key blob available in the analyzed binary (source).
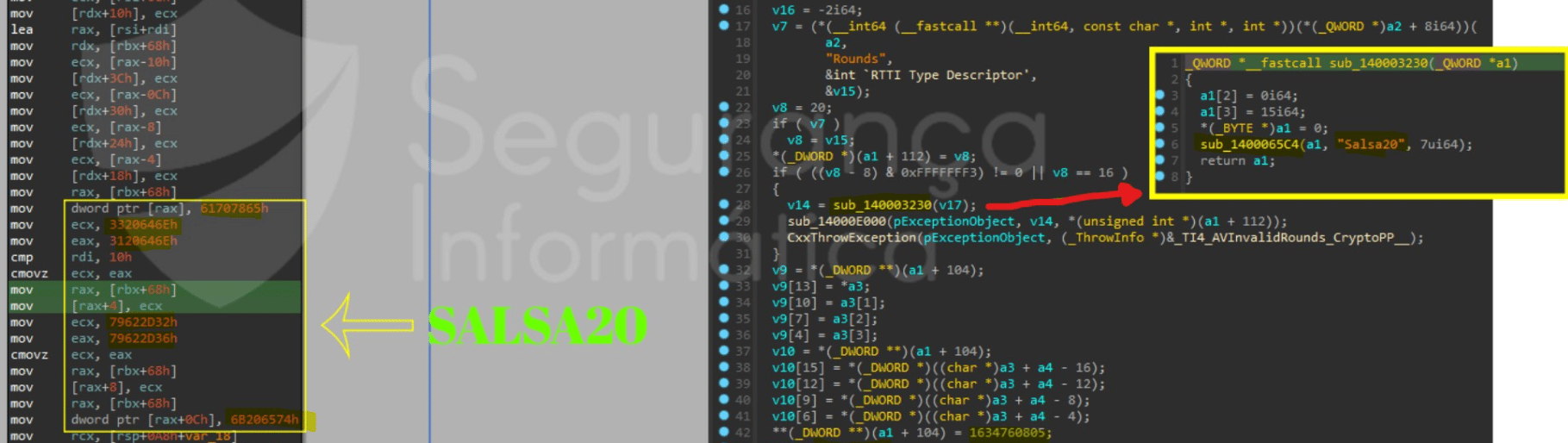
After getting the blob from the binary, the ransomware calls the SALSA20 stream cipher from the CryptoPP library.
Figure 5: Symmetric SALSA20 stream cipher detection (source).
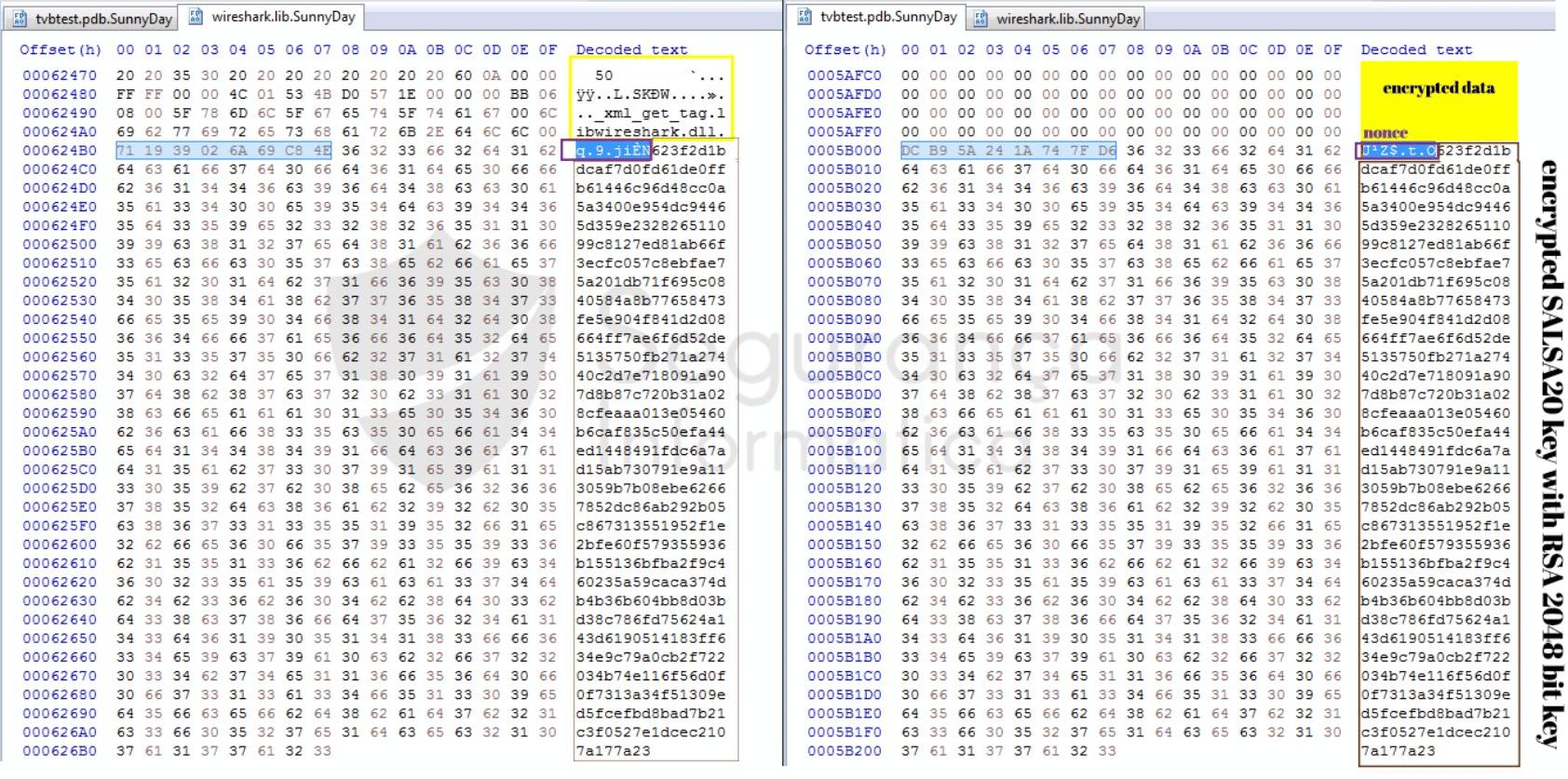
In detail, the ransomware uses a single SALSA20 key to encrypt the system files. The encryption key is created via CryptoGenRandom() and next encrypted with the RSA 2048-bit key that is on the ransomware binary (see Figure 4 above).
After encrypting a single file, the ransomware appends the SALSA20 key with 512 bytes at the end of the file. This key can be used to decrypt the files later, after the payment of the ransom and further contact with the criminals.
Figure 6: Encrypted files with the added nonce and SALSA20 key (512 bytes) encrypted with the RSA 2048-bit key (source).
When the encryption process terminates, a ransom note is dropped on the machine's desktop folder. Also, the Windows shadow copies are deleted to make it difficult to recover the files via forensics exercises.
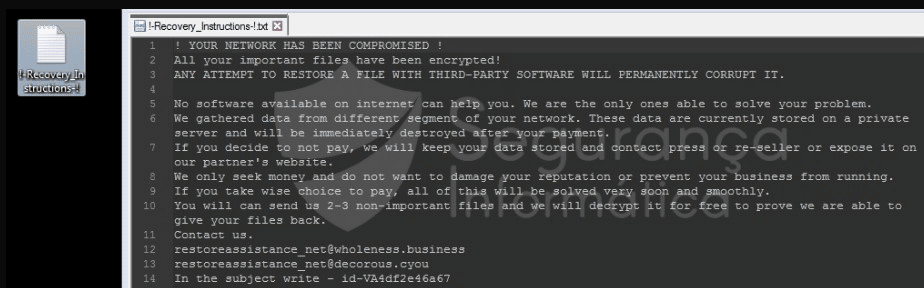
Figure 7: Ransom note of Sunnyday ransomware (source).

Become a certified reverse engineer!
Final thoughts on Sunnyday ransomware
Sunnyday ransomware is on the rise, and it is taking advantage of the SALSA20 stream cipher to speed up the encryption process. As experts have noticed, this ransomware is being spread in attacks on small and medium-sized companies, impacting their businesses and demanding a ransom depending on the size of the organization and damaged data.
According to the Segurança-Informatica analysis, Sunnyday can either be a new variant or a development of the following ransomware samples, based on its code analysis and ransomware note structure:
- Ever101
- MedusaLocker
- Curator
- Payment45; and
- Keversen
Although there is no perfect formula for stopping ransomware infections, the introduction of monitoring strategies, the usage of endpoint security solutions such as antivirus and EDR, and the increasing use of canary files can be seen as mandatory mechanisms that could prevent the damage of these threats in the wild.
Sources:
Analysis of the SunnyDay ransomware, Segurança-Informática
Ransomware deletion methods, and the canary in the coal mine, Infosec Institute