Android malware worm auto-spreads via WhatsApp messages
Fraudulent mobile applications are on the rise. One recent example is malware hidden on the Google Play marketplace in a fake application and capable of spreading itself via Whatsapp instant messages. If the victim grants the correct permissions, the malware automatically retrieves a crafted payload from its C2 servers and disseminates it on WhatsApp messages.
This article covers how this kind of malware works, the techniques used by malicious actors and how to prevent it.

Become a certified reverse engineer!
WhatsApp malware worm overview
In general, mobile devices are not as secure as computers. The standard security protections used for workstations and servers are not in place for most mobile devices, so mobile devices may not be protected by firewalls, encryption, antivirus or endpoint detection and response.
However, these devices are often connected to cloud services, business emails and other applications that put companies at risk.
Within this context, the CheckPoint Research team discovered malware on the Google Play marketplace with the capability of spreading itself by using the victim's WhatsApp messages. When submitted into the official marketplace, the malicious application was not flagged as malware and may have been downloaded and installed by approximately 500 users.
Figure 1: Malicious application available on the official Google Play marketplace (source).
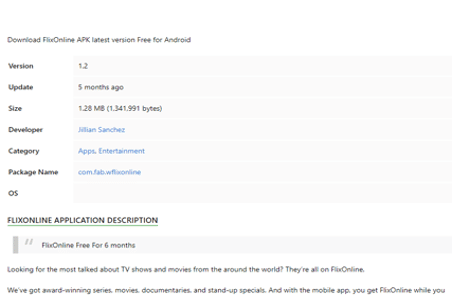
As observed in figure 2 below, this malicious application impersonates the legitimate application NetFlix, and it provides online media content such as movies and series for free. The application was allegedly developed by Jillian Sanchez, according to the name associated with the APK submission on Google Play.
Figure 2: Details about the malicious application "com.fab.wflixonline".
Digging into the FlixOnline malware details
This piece of malware automatically replies to messages that come from WhatsApp and then sends a payload received from its C2 server online.
"The application is actually designed to monitor the user's WhatsApp notifications, and to send automatic replies to the user's incoming messages using content that it receives from a remote C&C server," CheckPoint researchers said.
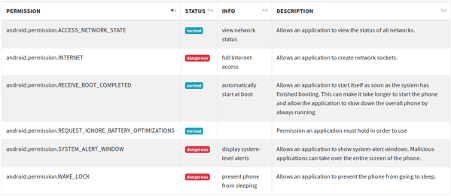
Some additional mandatory permissions are prompted when the victim downloads and installs the application. The permission "android.permission.INTERNET" is necessary to create online sockets with its C2 server to retrieve and send information from the infected device. The "RECEIVE_BOOT_COMPLETED" feature is enabled by default to start the app at boot, allow total control of the device and achieve persistence. Additionally, the "WAKE_LOCK" permission is essential to prevent the phone from sleeping. The full details extracted can be observed below.
Figure 3: Permissions requested by the malicious application during its execution.
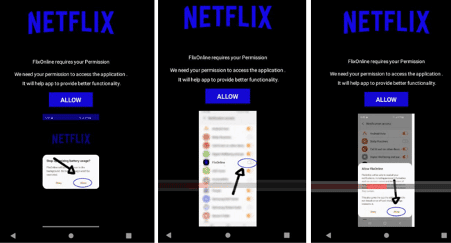
Another interesting permission is "SYSTEM_ALERT_WINDOWS." It's responsible for creating overlay windows over other applications to steal information or bait users to click or execute something malicious. Some of the overlay windows are retrieved from a hosting service, as observed below.
Figure 4: Overlay windows presented by the malware in run-time.
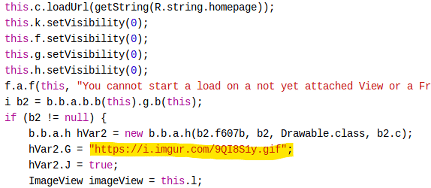
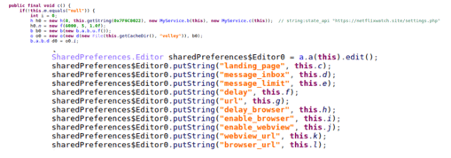
After the permissions are set, the malware receives an initial payload from its C2 server that hides its icon to help prevent the deletion of the application. This routine is performed periodically by a function that retrieves information from the C2 server online.
Figure 5: Parser of the C2 server payload.
Interacting with the WhatsApp notifications
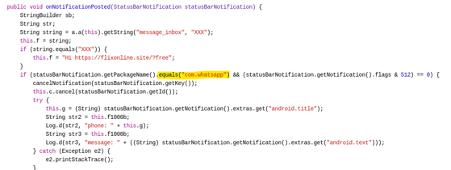
After this point, the malware is ready to distribute the payload via WhatsApp. During its execution, the callback OnNotificationPosted checks for the package name of the source app, and if the application name is WhatsApp, the "new" notification is processed.
Figure 6: The malware is finding WhatsApp notifications.
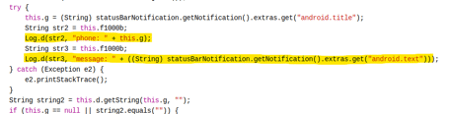
Then, the malware closes the notification to deceive the victim. The notification is hidden, and its details are obtained as presented in figure 7 (the title and content).
Figure 7: Route responsible for processing the notification.
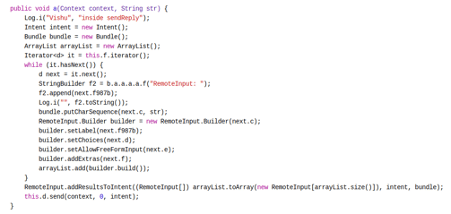
In the next stage, the malware invokes the component responsible for inline replies and sends the message reply with the malicious payload obtained from its C2 server.
Figure 8: Block of code responsible for sending the reply on WhatsApp.
Final thoughts on WhatsApp worm malware
Mobile wormable malware has been distributed in the wild with innovative and dangerous techniques for spreading and manipulating data or stealing users' secrets. These malicious pieces also take advantage of trusted applications, such as WhatsApp, installed on the target mobile devices to reach other users.
By using this modus operandi, threat actors can perform a range of malicious activities, including:
- Disseminate further malware via malicious URLs
- Steal data from user's legitimate applications (such as WhatsApp)
- Create fake or malicious messages and send them via legitimate applications
- Extort users by threatening to send sensitive data or malicious links to all their contacts or WhatsApp groups (the best target from the malicious perspective).
The best recommendations to keep your mobile devices protected are never installing or downloading suspicious or strange applications from unofficial marketplaces. Even though this specific app has been downloaded and installed from Google Play without detection from the Google side, it's always important to check the requested permissions and learn about them.
Sometimes the permissions are not aligned with the nature of the target application, and this detail should be taken into account every time. Let's take mobile threats seriously and protect our devices against threats of this line.
Sources
- Android malware worms via WhatsApp, CheckPoint Research Team
- Wormable Android app, TheHackerNews