LockBit 3.0 ransomware analysis
LockBit has been one of the most popular and dangerous ransomware pieces since 2019. The group behind the threat typically attacks critical infrastructures such as health systems, including hospitals.
LockBit 2.0 overview
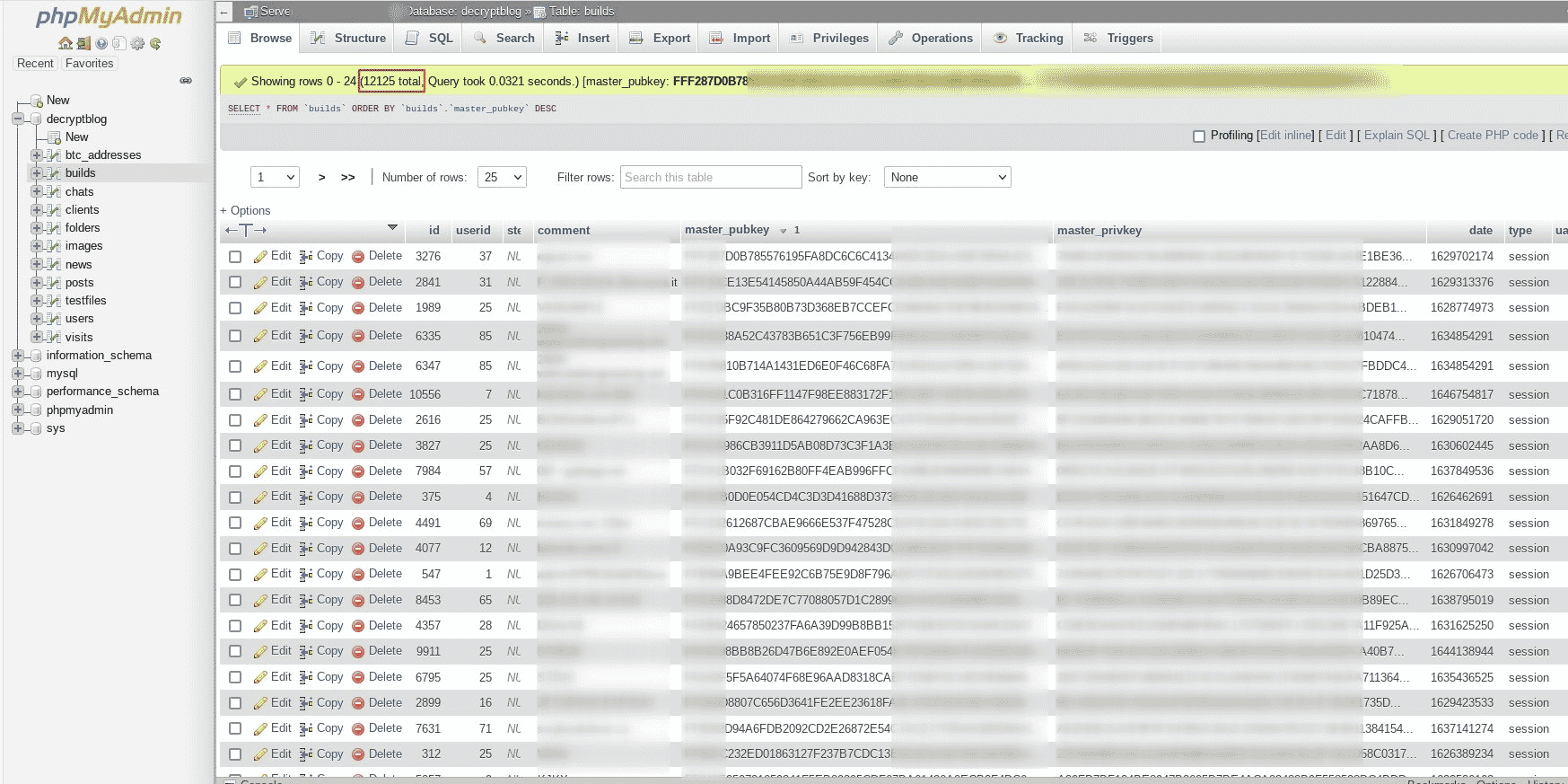
Looking at the LockBit 2.0 website, more than 850 victims were affected in 2022 by this ransomware, a clear sign of the damage and impact caused by the LockBit operators during their wild campaigns. Criminals claim that they damaged at least 12,125 companies during the LockBit 2.0 version, seen below.
Figure1: Total of compromised companies by LockBit 2.0 version.
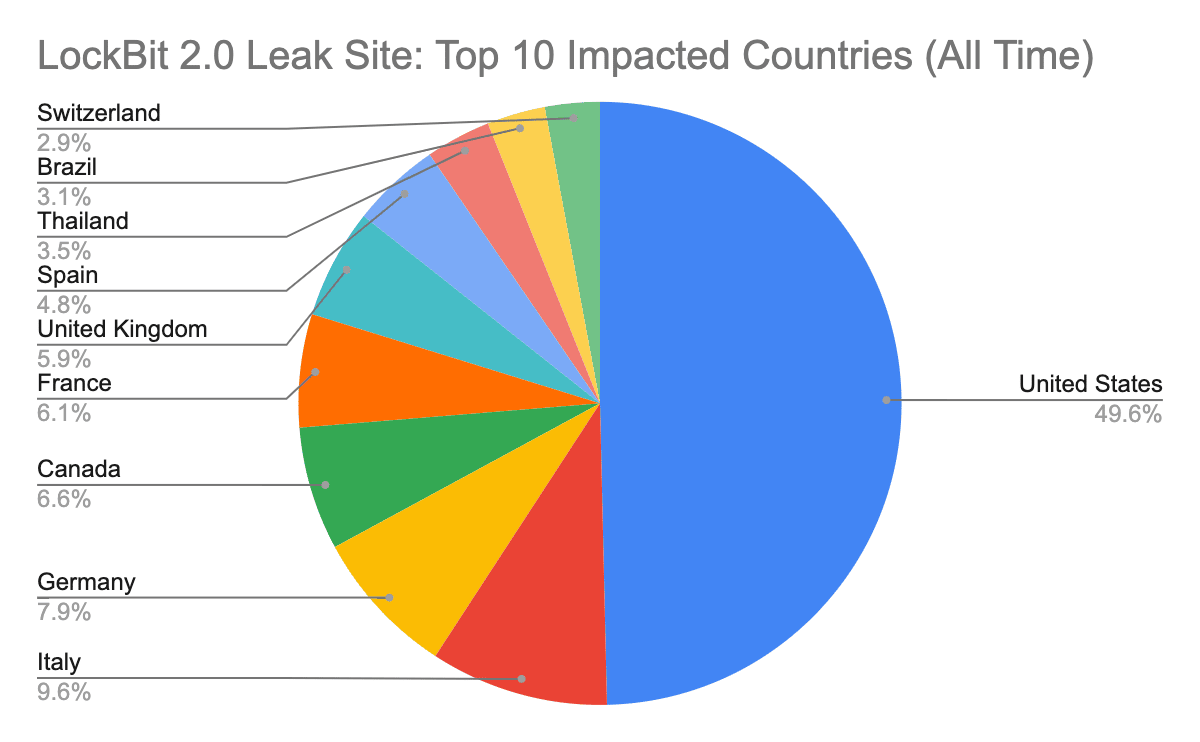
According to the PaloAlto publication, the USA, Italy, Germany, Canada and France are the top five most affected countries by LockBit 2.0 campaigns, with criminals causing a huge global impact.
Figure 2: Top 10 impacted countries by LockBit 2.0 (source).
LockBit 3.0 release
With the introduction of the new release of LockBit ransomware (version 3.0), significant capabilities were implemented, including a bug bounty program and Zcash payments.
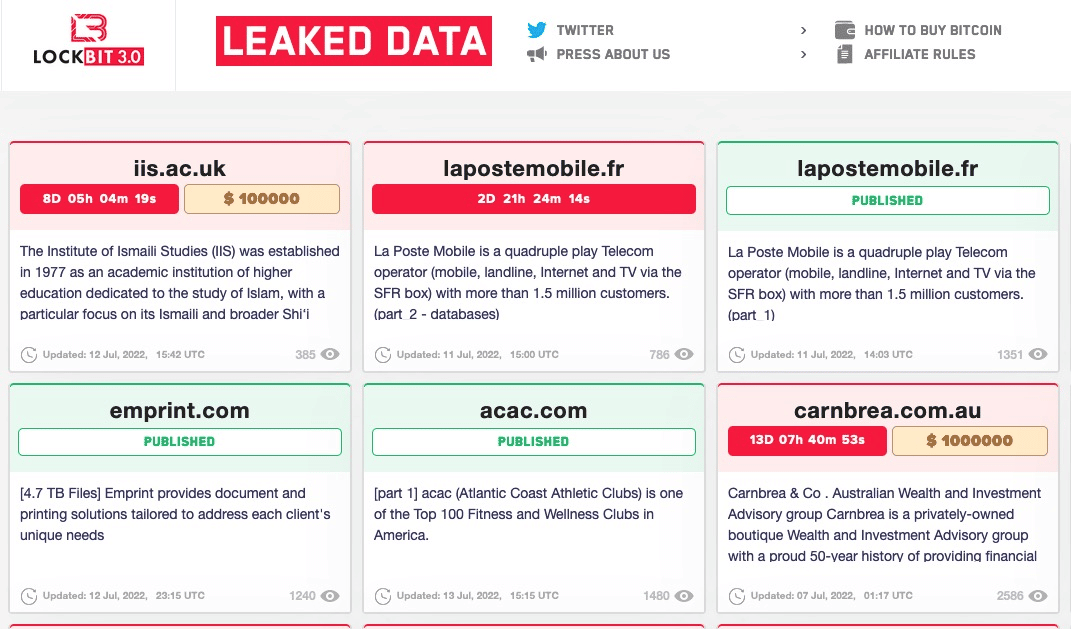
Although there are no official numbers about incidents related to this new version, criminals decided to change in June to the LockBit 3.0, and some victims can be found on the group website.
Figure 3: LockBit 3.0 victims.
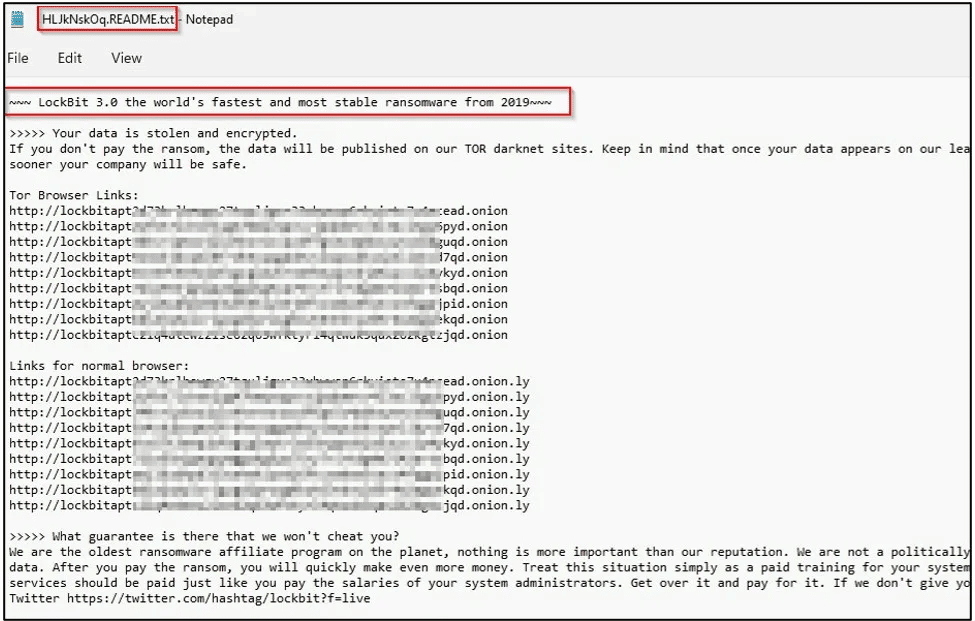
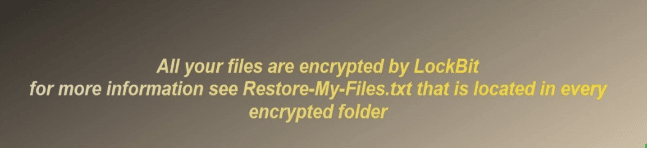
The ransomware notes are no longer named “Restore-My-Files.txt” but were moved to a new format: [id].README.txt, as presented below.
Figure 4: Ransomware note of LockBit 3.0 version.
Also, a new desktop wallpaper is introduced by criminals in this fresh release, as shown in Figure 5.
LockBit 2.0 desktop wallpaper (source)
LockBit 3.0 desktop wallpaper
Figure 5: Differences between LockBit 2.0 and 3.0 desktop wallpaper.
Notable capabilities introduced in version 3.0
LockBit 3.0 operators introduced a lot of fresh capabilities in this 3.0 version, including:
- Anti-detection mechanisms to evade AV and EDR systems
- LockBit 3.0 relies on an “access token” to be supplied as a parameter upon execution
- A command line option with possible parameters was also introduced
- The new version is more evasive and faster than the older versions, according to malware experts
- A fresh anti-debug feature added
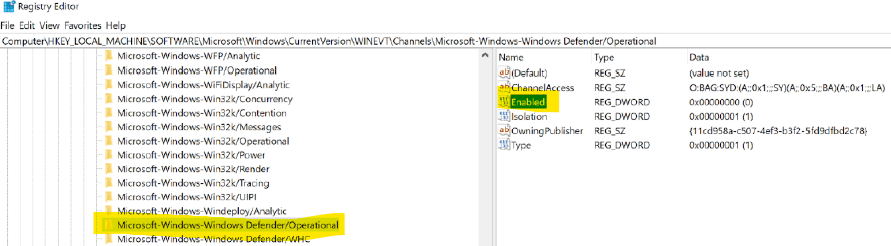
- A mechanism for disabling the Windows Defender and tempering the Windows Event Logs is also present.
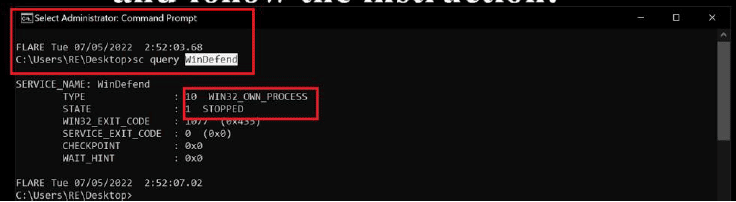
After executing, LockBit 3.0 tries to disable the Windows Defender to prevent its detection, as mentioned above.
Figure 6: LockBit 3.0 disables Windows Defender during its execution.
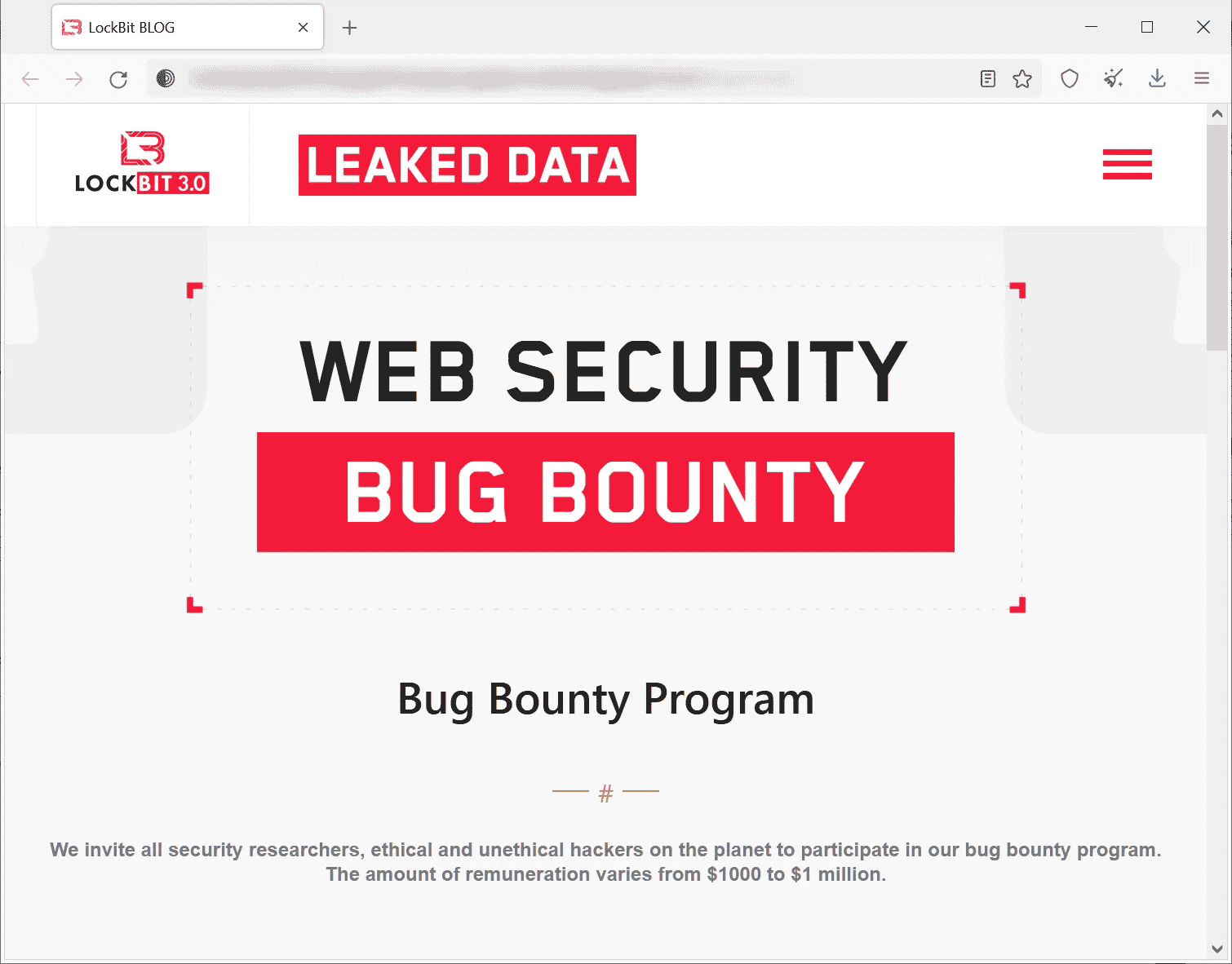
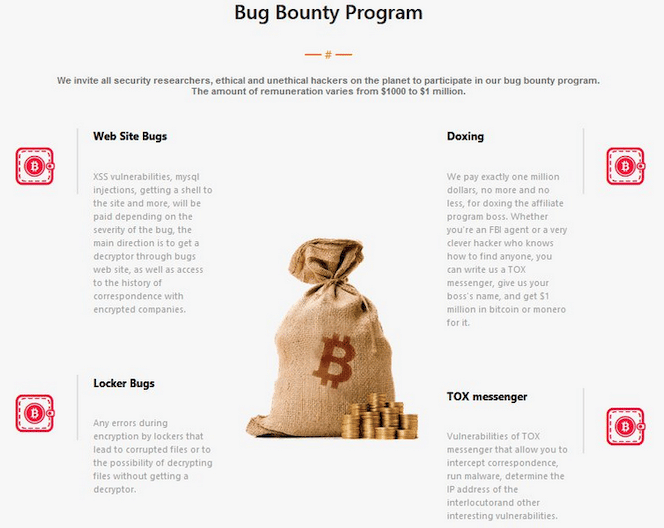
Within some features observed, criminals also introduced a bounty program bug. This is the first bug bounty program released by a ransomware group that encourages researchers to submit security reports for rewards ranging between $1,000 and $1 million.
"We invite all security researchers and ethical and unethical hackers on the planet to participate in our bug bounty program. The amount of remuneration varies from $1,000 to $1 million.”
Figure 7: Bug bounty program offered by LockBit operators.
The ransomware gang will also reward “brilliant ideas” to improve its operations. As expected, this bug bounty program differs from traditional and legitimate programs. The available categories are presented below.
- Website bugs: XSS vulnerabilities, MySQL injections, getting a shell to the site and more will be paid depending on the bug's severity. The main direction is to get a decryptor through the bug’s website and access the history of correspondence with encrypted companies.
- Locker bugs: Any errors during encryption by lockers that lead to corrupted files or the possibility of decrypting files without a decryptor.
- Brilliant ideas: We pay for ideas; please write us about how to improve our site and software; the best ideas will be paid for. What is so interesting about our competitors that we don't have?
- Doxing: We pay exactly $1 million, no more and no less, for doxing the affiliate program boss. Whether you're an FBI agent or a very clever hacker who knows how to find anyone, you can write us a TOX messenger, give us your boss's name, and get $1 million in bitcoin or monero.
- TOX messenger: Vulnerabilities of TOX messenger that allow you to intercept correspondence, run malware, determine the IP address of the interlocutor and other interesting vulnerabilities.
- Tor network: Any vulnerabilities which help to get the IP address of the server where the site is installed on the onion domain, as well as getting root access to our servers, followed by a database dump and onion domains.
Figure 8: Bug bounty categories present on the LockBit 3.0 website.
The addition of Zcash as a payment option is another of the new features present in this new release. In detail, Zcash is a privacy coin, making it harder to trace and the perfect payment method for illegal purposes.
Prevention measures
Although there is no magic formula to stop ransomware in general, we can deliver a set of steps to reduce the risk of an incident of this nature.
- Create offline backups and frequently maintain backup and restoration. Test the procedure periodically.
- Create a zero-trust architecture with VLAN segregation to isolate DMZ from valuable assets and make lateral movement hard.
- Implement multi-factor authentication mechanisms on-premises and online/cloud
- Enforce the password policy to a strong and complex model (e.g., more than 10 chars at least).
- Use endpoint services such as EDR and AV.
- Remove unnecessary access to administrative shares on the internal network.
- Be careful with RDP exposed to the internet.
- Use canary files/tokens to detect ransomware early.
Finally, be proactive and perform cybersecurity assessments to find and mitigate weaknesses to prevent attacks in the wild, both from the external and internal perspectives.
Sources:
- LockBit 2.0, PaloAlto
- LockBit 3.0, BleepingComputer
- LockBit malware analysis, Segurança-Informática