DreamBus Botnet: An analysis
A new variant of the SystemdMiner threat dubbed DreamBus is impacting Linux servers around the globe to mine cryptocurrency.
Linux servers serve an important role in cloud-based infrastructures. This operating system is broadly used to make websites and platforms available online, as the costs to maintain these kinds of servers and licenses are less compared to Microsoft operating systems.
Recently, a new variant of the SystemdMiner threat with fresh improvements and features was released by cybercriminals. The DreamBus modules are poorly detected by security products and target enterprise-level applications running on Linux systems, including PostgreSQL, Redis, Hadoop, YARN, Apache Spark, HashiCorp Consul, SalStack and the SSH service.
Packer modification to evade analysis
DreamBus starts its operation from an ELF binary (Unix executable) responsible for setting up the environment, infecting the systems of copies of itself (worm capability), downloading new modules for spreading and deploying XMRig to mine Monero cryptocurrency.
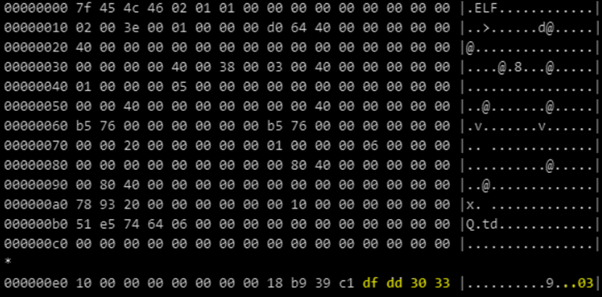
The packer UPX is used to protect this malware, evade its analysis and reduce its size. The UPX header — UPX! (0x21585055) — is modified and replaced with the value 0x3330dddf to make hard the packer identification.
Figure 1: UPX header modified - DreamBus.
How DreamBus works
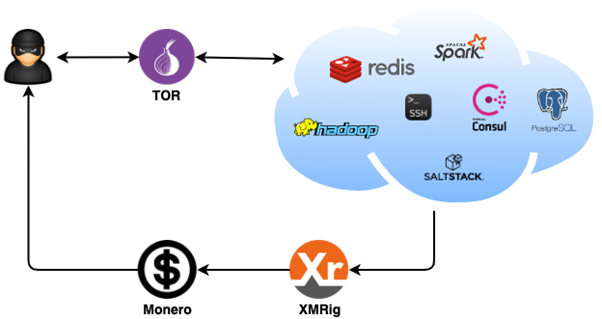
DreamBus is malware composed of several modules and a self-update feature. Part of the C2 commands and components are hosted using the TOR network or an anonymous file-sharing hosting service. To take advantage of the target systems, the malware exploits several applications including SSH, PostgreSQL, Redis, Hadoop YARN, Apache Spark, HashiCorp Consul and SaltStack.
According to the Zscaler ThreatLabZ analysis, many DreamBus plugins share code, for example, to create a lock file named 22 in the directory /tmp/.X11-unix/, and most set the name of the calling thread to tracepath. This is intended to disguise the DreamBus modules and make them appear to be legitimate (since many modules are downloaded with pseudo-randomly generated filenames).
Figure 2: High-level diagram of the DreamBus botnet architecture.
In addition, a proxy service such as tor2web to translate requests between TOR and the internet is installed if the compromised systems do not have TOR installed.
DreamBus modules
Once installed on a target machine, the bot tries to spread to as many systems as possible. DreamBus scans vulnerable systems on a local intranet in ranges 172.16.0.0/12, 192.168.0.0/16 and 10.0.0.0/8.
The modules are download in run-time and exploit the services presented below.
Some of these apps are targeted with brute-force attacks against their default administrator usernames, others with malicious commands sent to exposed API endpoints or via exploits for older vulnerabilities.
The final stage of this malware is to download and install an open-source application that mines the Monero (XMR) cryptocurrency to generate profits for the criminals.
Furthermore, each of the infected servers is also used as a bot in the DreamBus operation to launch further brute-force attacks against other possible targets.
Stopping DreamBus attacks
DreamBus is a modular Unix-based botnet impacting systems around the world with worm-like behavior. The malware can spread internally by scanning private RFC 1918 subnet ranges for vulnerable systems, using common and default passwords via brute force or application-specific exploits.
Threat actors behind DreamBus are geolocated in or near Russia based on the time when new commands are pushed out during the malware operation.
Stopping cryptojacking activity with monitoring agents is the key to preventing this type of malware: looking for signs such as reduction of computer processing speed and performance, increased electricity use, devices overheating and increased demands of the CPU. Also, host-level monitorization should be taken into account as the first step of security.
Sources:
DreamBus Botnet - Technical Analysis, Zscaler (hyperlink article name here: https://www.zscaler.com/blogs/security-research/dreambus-botnet-technical-analysis)
The Ultimate Packer for eXecutables, UPX (https://upx.github.io/)