Luna ransomware encrypts Windows, Linux and ESXi systems
Ransomware is making headlines daily. New samples are introducing new techniques, more sophistication and anti-detection techniques to hide their detection from the cybersecurity radar.
One of the most recent examples is the Luna ransomware, shortly documented by Kaspersky. The ransomware was discovered in June 2022 on underground forums, and it seems that it is in development by Russian actors. "The advertisement states that Luna only works with Russian-speaking affiliates. Also, the ransom note hardcoded inside the binary contains spelling mistakes," says the Kaspersky research team.

Become a certified reverse engineer!
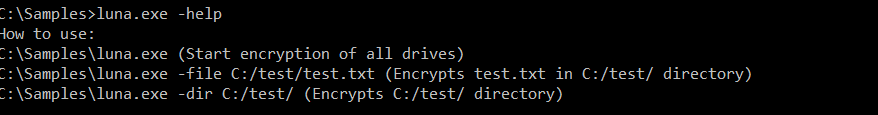
The ransomware has a command-line interface with simple features implemented, as observed below.
Figure 1: Luna (the Russian word for moon) command line interface.
Luna is developed in the Rust language, such as other notable ransomware families: Hive and BlackCat. Using the Rust language, criminals obtained a set of advantages from the detection point of view. As announced on the Rust website, it provides:
- A language empowering everyone to build reliable and efficient software
- High performance because Rust is fast and memory efficient
- It provides great documentation, a friendly compiler with useful error messages and top-notch tooling
- It is cross-platform
A clear motivation from the criminals' point of view is the cross-platform feature, as it allows the development of a ransomware piece that can be used in different operating systems, such as Windows, Linux and ESXi systems. Rust is also memory efficient, and the ransomware code does not remain static, making its detection hard, another advantage of Rust within the malware landscape.
Encryption process
Luna ransomware is using a not common encryption combination, taking advantage of the fast and secure X25519 elliptic curve Diffie-Hellman key exchange using Curve25519 with the Advanced Encryption Standard (AES) symmetric encryption algorithm, as mentioned by Kaspersky.
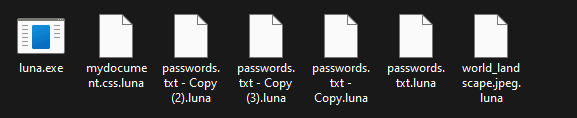
The extension .luna is appended to all encrypted files during the encryption process, but the ransomware capabilities are still under development.
Figure 2: Luna sample and damaged files with the .luna extension appended to the file name.
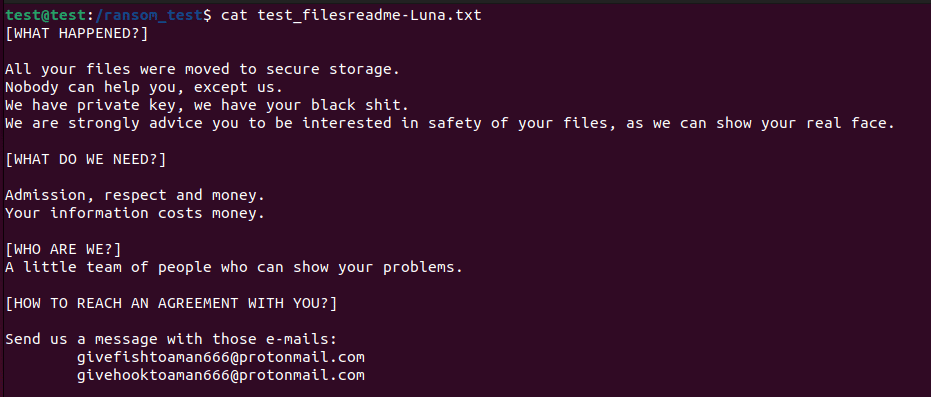
An interesting detail observed during this analysis is that Luna's source code seems to be adapted to the Russian language, probably indicating the group’s targets are not part of the former USSR (Union of Soviet Socialist Republics). Within this context and to corroborate the previous thought, the ransomware note is written in American English, with some grammatical errors probably indicating an automatic translation from another language.
Figure 3: Luna ransomware note.
Regarding the Linux and ESXi samples, the same source code is used to compile both versions, with minor changes performed during the build process.
Understanding Luna ransomware
Using exotic languages like Rust demonstrates a significant trend in the ransomware landscape. Luna is the perfect example, with the criminals’ groups developing cross-platform ransomware families to cause the highest damage during the encryption process and target different operating systems. Rust and Goland are criminals' most popular programming languages to develop new threats.
In this sense, monitoring must be in place to reduce the potential damage of a ransomware incident, as well as to spotlight the threat on the cyber security radar and thus allow a fast and efficient containment of the threat.
Sources:
- Luna ransomware, Kaspersky