The Hunt for Memory Malware
Memory forensic is a skill to find out all the artifacts in the memory that is present in the running computer. It is an interesting method to find out what are the running process, open network connections, registry handles, kernel modules etc. It looks rosy when you hear all the features of memory forensics but strong knowledge on windows is a prerequisite to this technology.
Memory forensics is very useful to a security analyst to carry out investigation whenever there is any computer security incident. It is also used by Malware researchers to find out the properties of malware behaviour. To start first with analysing the memory we need to obtain Computer memory dump from the machine. There are a set of tools to achieve this staring from the free ones to the paid.
Common tool list
Memory acquisition tools
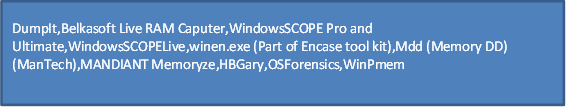
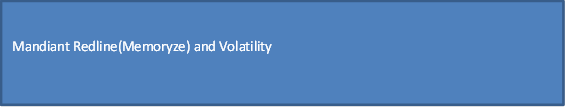
Memory Analyser
I would like to showcase how we can do memory forensics, here I am running a malware that I got from kernelinfo.com (free malware samples are available for download in kernel info after user registration)
Out of these tools I recommend using tool Volatility and Memoryze (Mandiant) for analysing the dump which is collected.
Volatility and Memoryze
Volatility is an open source memory forensic tool that is written in Python. Unlike other tool that only runs on windows and requires .NET installations Volatility is free to run on windows, Linux and mac to carry out analysis. Volatility also gives power to go beyond the normal functionality by building customized web interface. Volatility has the efficient algorithm to analyse RAW dumps from large system where normal tools will lead to system crash. It also helps in analysing different file format like crash dumps, hibernation files, VMware saved state and suspended state(.vmss/.vmsn) and many more. You can download volatility from (https://code.google.com/p/volatility/downloads/list)
Even though Memoryze don't support Linux it is one of the tools that is commonly used by malware researchers as it supports all the flavours of windows. The preferred way to launch Memoryze is to use the user interfaces built for Memoryze called Redline.
My first duty here is to take the memory dump of the machine
It is recommended to use third part tools to take memory dumps of the whole system. Windows has features to take memory dumps of a process however If you need a memory dump of a whole system, it's better to rely on third party tools.
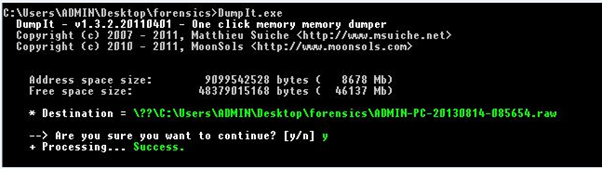
Taking memory dump
Here I am using Dumpit to take memory dump.
Usually it takes time to generate the dump file.
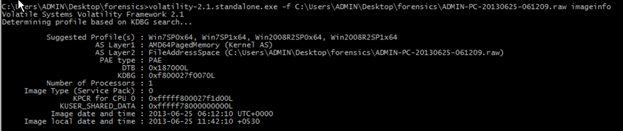
Imageinfo>Before we go ahead, Volatility needs to know what type of system your memory dump came from, so it knows which data structures, algorithms, and symbols to use.
Note-image info plugin will not work on hibernation files
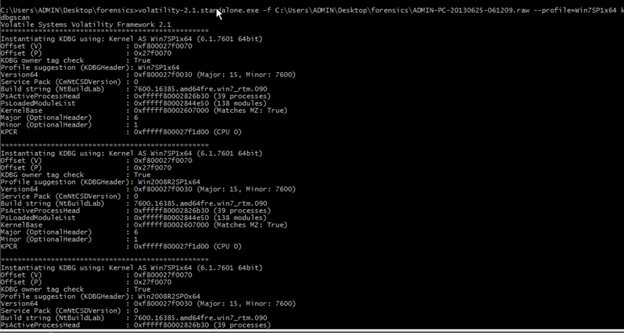
kdbgscan >is designed to positively identify the correct profile and the correct KDBG address. so if you already know the correct profile (or if you have a profile suggestion from image info), then make sure you use it.
Command:
volatility-2.1.standalone.exe -f C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 kdbgscan
You can get more information on KDGG at
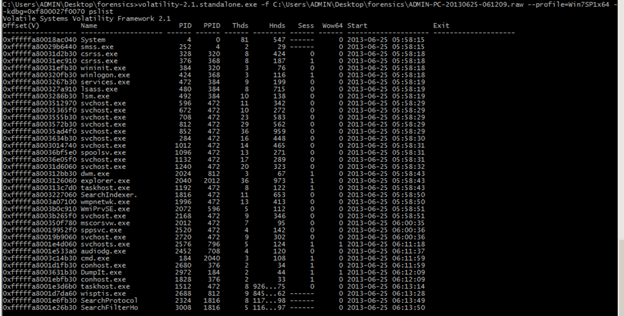
Pslist to display the process
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 -
-kdbg=0xf800027f0070 pslist
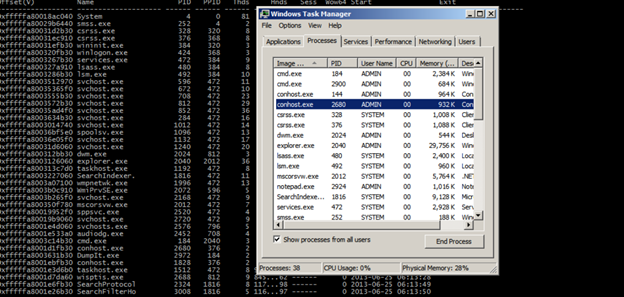
Once I have run the pslist command I have taken the Windows task manager to see whether both PIDS of CMD.exe are 184.Y
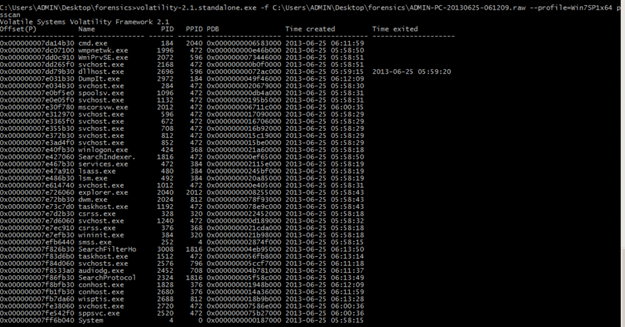
To see the processes that are inactive or processes that have been hidden or unlinked by a rootkit run psscan command.
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 psscan
To see the what all dll's that an exe calls use dlllist command
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 dlllist
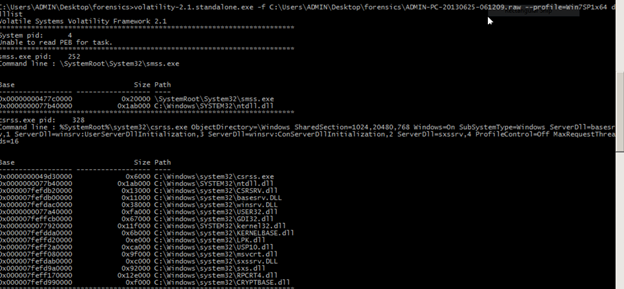
To flush all the dll that is loaded in the memory to a folder
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 dlldump -D dlls
Dll is the directory that we have dumped all dll files
In the result pane you can see how successful the extraction of these dll dump in dll folder is. There are also chances that the extraction is a failure, due to paging. Now you can find the md5 value of each dll and classify whether it is malicious or not. Other way is to upload it in virustotal.com to check its malicious behaviour presence.
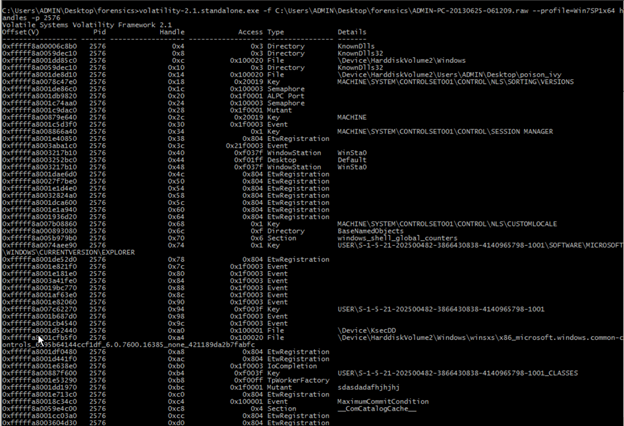
Viewing handles
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 handles -p 2576
Shows the handles for the particular process 2576.
To find the threads
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 threads -F AttachedProcess
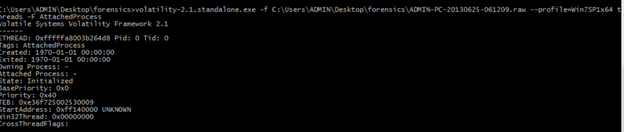
It shows no attached process exits.
If you want to see the environmental variables
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 threads -L
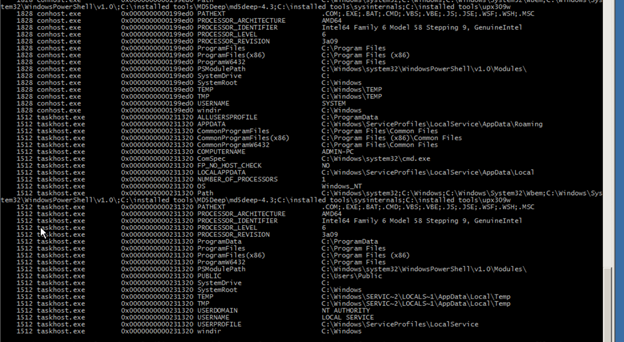
We can dump all the exe from the image to a folder by giving procmemdump command
Command:
Type— C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 procmemdump -D
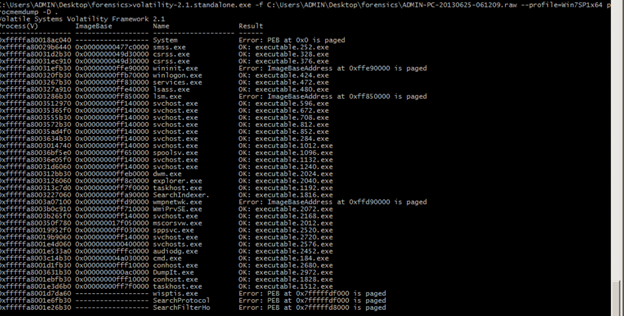
Now we can see the svhosts.exe process as executable.2576 in the target folder.
Commands like connections, connscan,sockets, sockscan are also useful for viewing network connections but it only applies to windows XP and windows server 2003 server.
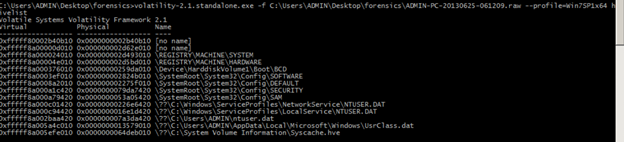
Hivelist-to locate the virtual address of registry hives
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 hivelist
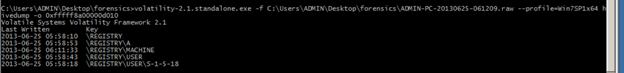
To list all subkeys in a hive we can use hivedump
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 hivedump -o 0xfffff8a00000d010
Userassist- to see commonly used programs
Command:
C:UsersADMINDesktopforensicsADMIN-PC-20130625-061209.raw --profile=Win7SP1x64 userassist
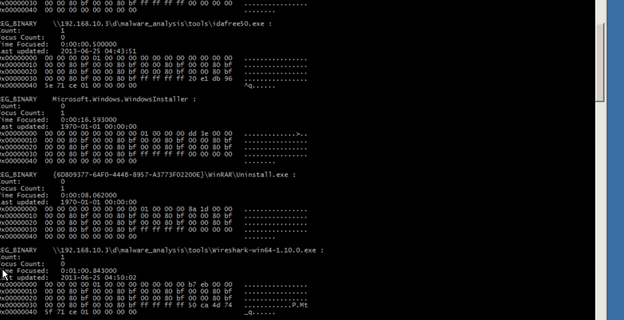
Malfind is used to find the hidden dlls.In the below,I have given pslist to see all the process.For each process I am checking any presence of hidden dlls by issuing the malfind command.
Command:
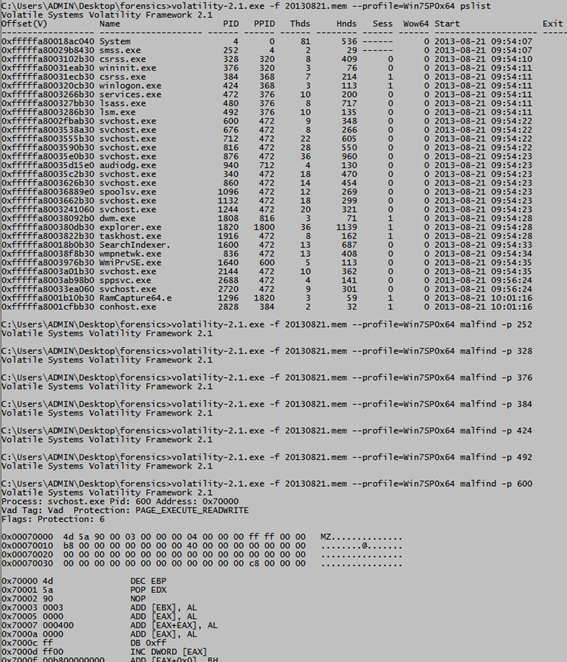
C:UsersADMINDesktopforensics>volatility-2.1.exe -f 20130821.mem --profile=Win7SP0x64 malfind -p 600
You can see the windows services in the RAM by issuing svsscan.In my scenerio I don't have any suspicious running out here.
Command: volatility-2.1.exe -f 20130821.mem --profile=Win7SP0x64 svcscan
Cracking passwords.
Now lets see how we can crack the password using the memory forensic tool Volatility.I don't think volatility can be used to crack passwords of windows 7 operating system.But for Windows XP we can.
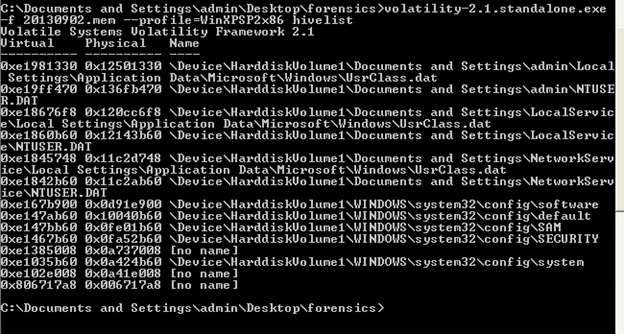
Hivelist: Is used to find the virtual address of registry hives in the memory.To crack password we need to bother about the virtual address of SAM and SYSTEM hive.
Command: C:Documents and SettingsadminDesktopforensics>volatility-2.1.standalone.exe
-f 20130902.mem --profile WinXPS2x86 hivelist
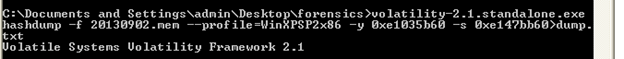
Once we have located the virtual address of the registry hives, we need to dump the hashes to a text file for further analysis.
Command: C:Documents and SettingsadminDesktopforensics>volatility-2.1.standalone.exe
-f 20130902.mem --profile=WinXPSP2x86 -y 0xe1035b60 -s 0xe147bb60 hashdump>dump.txt
Here -y0xe1035b60 and -s 0xe147bb60 are the virtual address of SECURITY and SAM hives.
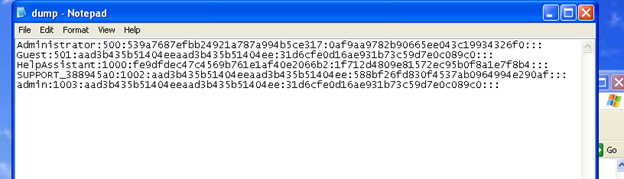
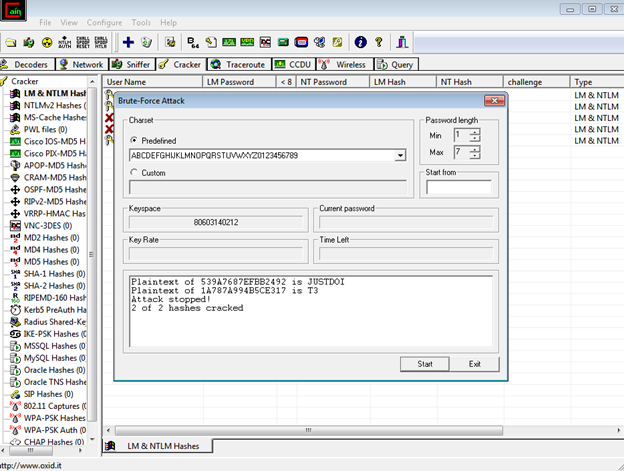
Once the Dump is created, we can use other third party tools like Cain and Abel, Rainbow tables to bruteforce the dump file. It may take days to months' time depending upon the complexity and length of the password.
References:
http://code.google.com/p/volatility/wiki/CommandReference#
http://cyberarms.wordpress.com/2011/11/04/memory-forensics-how-to-pull-passwords-from-a-memory-dump/

Become a certified reverse engineer!
www.youtube.com/watch?v=8HsZLge0wWc









