Duqu 2.0: The most sophisticated malware ever seen [Updated 2019]
Disconcerting news is shocking the IT security industry. The virus protection giant Kaspersky has been compromised by a sophisticated cyber-threat.
A new, powerful strain of the notorious Duqu malware appeared in the wild after going dark in 2012. The so-called Duqu 2.0 was the malicious agent used against the security firm and many other targets worldwide.
Duqu 2.0 was described by security researchers as highly sophisticated malware that exploited a number of zero-days vulnerabilities, which are listed below:
-
CVE-2015-2360;
Malware researchers at Kaspersky that first detected it revealed that among its targets there were entities linked to the negotiations about Iran's nuclear deal and IT security firms. Duqu 2.0 targeted a number of Western organizations and entities operating Asia and in the Middle East.
"Duqu 2.0, the cyberespionage tool that was used to compromise security firm Kaspersky Lab, has also been used in a number of other attack campaigns against a range of targets, including several telecoms firms. Analysis by Symantec concurs with Kaspersky's assessment today that Duqu 2.0 (detected by Symantec as W32.Duqu.B) is an evolution of the older Duqu worm, which was used in a number of intelligence-gathering attacks against a range of industrial targets before it was exposed in 2011. Although their functionalities were different, the original Duqu worm had many similarities with the Stuxnet worm used to sabotage the Iranian nuclear development program," explained malware researchers at Symantec that analyzed the malware.
The experts at Kaspersky Lab highlighted that the majority of infections observed in the 2014-2015 period is linked to the negotiations engaged by the P5+1 (the United States, United Kingdom, Germany, France, Russia, and China, facilitated by the European Union) with Iran. The purpose of the P5+1 events was the achievement of a verifiable diplomatic resolution that would prevent Iran from obtaining a nuclear weapon.
"Most notably, some of the new 2014-2015 infections are linked to the P5+1 events and venues related to the negotiations with Iran about a nuclear deal. The threat actor behind Duqu appears to have launched attacks at the venues for some of these high level talks. In addition to the P5+1 events, the Duqu 2.0 group has launched a similar attack in relation to the 70th anniversary event of the liberation of Auschwitz-Birkenau." states a report published by Kaspersky Lab.
The attack against the Kaspersky Lab
Duqu 2.0 was discovered by experts at Kaspersky Lab in an attempt of intrusion against its internal network. The discovery of the intrusion was casual; the researchers discovered the sophisticated strain of malware while testing a new technology designed to detect advanced persistent threats.
The attack against the Kaspersky firm likely began with a spear phishing attack against an employee in a small office in the APAC region, but at time of this writing, there is no news regarding the infection vector. Spear phishing is a phishing method that uses personal information about an individual, group of individuals, or an organization, to make a phishing e-mail more believable and personalized. It is a specialized, sophisticated way of attacking a specific individual in order to compromise their network/accounts. (For more info on spear phishing, click here.)
The experts suspect that it all started with a classic spear phishing attempt because one the "victims zero" they identified had its mailbox and web browser history wiped to avoid detection. The compromised machines were fully patched; a circumstance that led the experts to believe the attackers relied on a zero-day exploit.
Experts at Kaspersky confirmed that the infection stage was similar to the one implemented by Duqu that relied on malicious Word Documents containing an exploit for a zero-day vulnerability (CVE-2011-3402).
Duqu relied on an exploit that allowed the attackers to jump directly into Kernel mode from a Word Document, a technique considered by researchers very powerful and extremely rare.
Something of similar was noticed in June 2014, despite the fact the malware wasn't Duqu 2.0, the experts at Kaspersky suspect it was a parallel project from the Duqu group.
"A similar technique and zero-day exploit (CVE-2014-4148) appeared again in June 2014, as part of an attack against a prominent international organization. The C&C server used in this 2014 attack as well as other factors have certain similarities with Duqu, however, the malware is different from both Duqu and Duqu 2.0. It is possible that this is a parallel project from the Duqu group and the same zero-day (CVE-2014-4148) might have been used to install Duqu 2.0. Once the attackers successfully infected one machine, they moved on to the next stage," states the report issued by Kaspersky.
Once the attackers gained access to the target network, they exploited another zero-day, (CVE-2014-6324) which was patched in November 2014, for lateral movement. The exploit allows an unprivileged domain user to elevate credentials to a domain administrator account.
"Once the attackers gained domain administrator privileges, they can use these permissions to infect other computers in the domain. To infect other computers in the domain, the attackers use few different strategies. In most of the attacks we monitored, they prepare Microsoft Windows Installer Packages (MSI) and then deploy them remotely to other machines," states Kaspersky. "In addition to creating services to infect other computers in the LAN, attackers can also use the Task Scheduler to start "msiexec.exe" remotely. The usage of Task Scheduler during Duqu infections for lateral movement was also observed with the 2011 version and was described by 6Symantec in their technical analysis."
Once they discovered the intrusion, the researchers at Kaspersky started an internal audit that is still ongoing. The company confirmed the high level of sophistication of Duqu 2.0, which they indicated as the most advanced ever seen. We have read something similar when Kaspersky published a report on the malware in the arsenal of the Equation Group, an APT that is linked to the NSA.
Key findings on Duqu 2.0
Duqu 2.0 implements sophisticated evasion techniques. It resides in memory, making its detection difficult. The new version of Duqu no writes files on the victim's disk. Experts at Symantec explained that Duqu 2.0 comes in two variants, a first one that is a backdoor that appears to be used to gain persistence in the targeted entity by infecting multiple computers. A second variant that represents its evolution, and implements more sophisticated features.
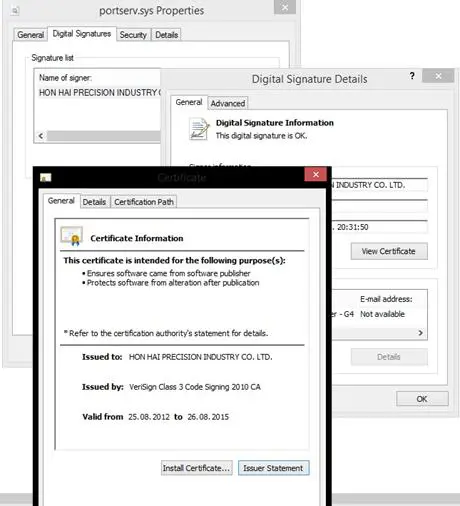
Authors of Duqu 2.0 used a stolen certificate from the Foxconn company to implement a persistence mechanism and remain under the radar.
The investigation conducted by the experts at Kaspersky revealed that the threat actors behind Duqu 2.0 used valid certificate from Hon Hai Precision Industry Co. LTD (aka Foxconn Technology Group) to digitally sign the malicious code. Foxconn provides electronic components for a wide number of companies, including Apple and BlackBerry.
The digital certificate was issued by VeriSign and used the authors of Duqu 2.0 to digitally sign the source code of a driver designed to mask command-and-control traffic.
"The attackers created an unusual persistence module which they deploy on compromised networks. It serves a double function – it also supports a hidden C&C communication scheme. This organization-level persistence is achieved by a driver that is installed as a normal system service. On 64-bit systems, this implies a strict requirement for an Authenticode digital signature. We have seen two such persistence drivers deployed in the course of attacks," states a blog post published by the Kaspersky Lab's Global Research & Analysis Team (GReAT).
The researchers discovered that the threat actors installed malicious digitally signed drivers for network devices to interfere with traffic routing.
Figura 1 - Duqu 2.0 Digital Certificate used to sign source code of the drivers
"During their operations the Duqu threat actors install these malicious drivers on firewalls, gateways or any other servers that have direct Internet access on one side and corporate network access on the other side. By using them, they can achieve several goals at a time: access internal infrastructure from the Internet, avoid log records in corporate proxy servers and maintain a form of persistence after all," continues the post.
"In essence, the drivers are redirecting network streams to and from the gateway machine that runs it," the researchers explained. "To forward connections, the attacker first has to pass a network-based "knocking" mechanism by using a secret keyword. We have seen two different secret keywords in the samples we collected so far: "romanian.antihacker" and "ugly.gorilla"."
The used of digitally signed code seeming to be a prerogative of threat actor behind Duqu, the attackers haven't used the same digital signature more than once.
"Another interesting observation is that besides these Duqu drivers we haven't uncovered any other malware signed with the same certificates," the researchers continued. "That rules out the possibility that the certificates have been leaked and are being used by multiple groups. It also seems to indicate the Duqu attackers are the only ones who have access to these certificates, which strengthens the theory they hacked the hardware manufacturers in order to get these certificates."
Duqu and Duqu 2.0 share several features including the use of a cookie header with a hardcoded string and a random string when sending messages to a C&C server.
Below a sample of cookie headers used by the two strains of malware.
- Duqu: Cookie: PHPSESSID=<random_str_0x1A_size>
- Duqu 2.0: Cookie: COUNTRY=<random_str_0x1A_size>
Another shared feature in the network communications code of the two Duqu variants is to connect to a number of Microsoft URLs to retrieve a proxy address.
"It also doesn't directly connect to a command-and-control server to receive instructions," explained Kurt Baumgartner, principal security researcher at Kaspersky Lab. "Instead, the attackers infect network gateways and firewalls by installing malicious drivers that proxy all traffic from internal network to the attackers' [command and control servers]. Combined, this made discovery very difficult."
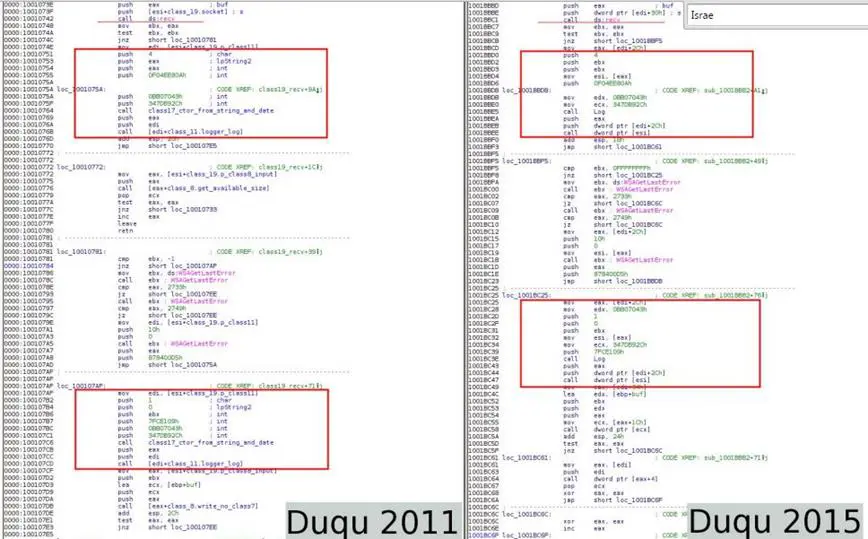
The new strain of Duqu has many similarities with the original variant spotted in 2011. Threat actors behind the Duqu 2.0 campaign didn't appear to work at all on Saturdays and compilation timestamps provided useful information to profile them.
Figure 2 - Source Code comparison Duqu vs Duqu 2.0
"During our analysis in 2011, we noticed that the logs collected from some of the proxies indicated the attackers appear to work less on Fridays and didn't appear to work at all on Saturdays, with their regular work week starting on Sunday," explained Baumgartner. "They also compiled binaries on January 1st, indicating it was probably a normal workday for them. The compilation timestamps in the binaries seemed to suggest a time zone of GMT+2 or GMT+3. Finally, their attacks would normally occur on Wednesdays, which was the reason we originally referred to them as the "Wednesday Gang"."
The experts at Kaspersky highlighted the complexity of the command-and-control mechanism implemented by Duqu 2.0 that improve the one designed for the original 2011 version. The C&C mechanism relies on the usage of network pipes and mailslots, raw filtering of network traffic and masking C&C traffic inside image files.
The experts explained that once Duqu 2.0 infects client in a targeted LAN, newly infected clients might not have a C&C hardcoded in their installation MSI packages. The attacker can activate them over SMB network pipes with a special TCP/IP packet that contains the magic string "tttttttttttttttt."
"To connect the C&C servers, both 2011 and 2014/2015 versions of Duqu can hide the traffic as encrypted data appended to a harmless image file. The 2011 version used a JPEG file for this; the new version can use either a GIF file or a JPEG file. Here's how these image files look like: Another modification to the 2014/2015 variants is the addition of multiple user agent strings for the HTTP communication." states Kaspersky.
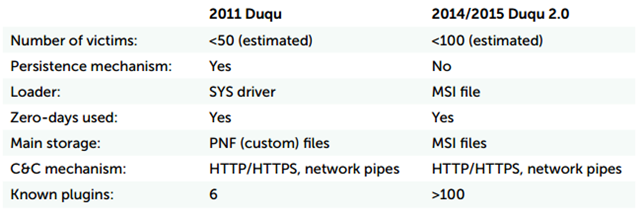
Figure 3 - Similarities between Duqu and Duqu 2.0
Experts at Laboratory of Cryptography and System Security (CrySyS) that received a sample of the Duqu 2.0 malware by Kaspersky, highlighted that the group behind the new variant reused part of the original code introducing significant improvements.
"They reused code and ideas from Duqu in the new Duqu 2.0 malware, but at the same time, they also made modifications in order to render Duqu 2.0 undetectable by the old detection methods," states the report from CrySyS.
Below the list of similarities that the experts discovered between Duqu and Duqu 2.0:
-
Similar string decryption routines related to Anti-Virus product strings
-
Similar methods, magic number, bug and file format related to files encrypted with AES by both threats
-
Same non-standard CBC mode AES encryption used by both threats
-
Extremely similar logging module with exactly the same magic numbers
-
Similar C++-like coding and compiling style
Who developed Duqu 2.0?
The problem of attribution is not easy when experts face with so complex APT, the incident occurred at Kaspersky is worrying and the boldness of the Duqu 2.0 authors is surprising the CEO of the company Eugene Kaspersky.
"Spying on cybersecurity companies is a very dangerous tendency," said Kaspersky. "Security software is the last frontier of protection for businesses and customers in the modern world"
Eugene Kaspersky, CEO of the security firm, defined the Duqu 2.0 campaign high sophisticated and "almost invisible."
Kaspersky described Duqu 2.0 as a "mix of Alien, Terminator and Predator, in terms of Hollywood".
"They wanted to prove themselves that they're cool, so they're able to affect a leading security IT company," Kaspersky said. "That was a mistake. I'm afraid that the costs of this project, cyber attack, could be ten million dollars, maybe more."
Why attack the Kaspersky firm?
There are a number of good reasons to target one of the most important security firm, first of all the attackers could be interested in stealing secrets about Kaspersky technologies. By stealing information on Kaspersky, the attacker can design new malware that could be able to avoid detection of the state-of-the art defensive solutions. Another good reason could be the interest in investigations conducted by the company on the principal Advanced Persistent Threat groups in the wild.
Experts at CrySySLab who analyzed the strain of Duqu 2.0 that infected systems at Kaspersky Lab in May 2015 speculated that the group is still active.
"After analyzing the samples that we received, we think that the attackers behind the Duqu malware are back and active," states the analysis from CrySySLab.
Tod Beardsley, an engineering manager at Rapid7, highlighted the incident at Kaspersky is an alert for the entire security industry.
"Kaspersky has a reputation for being one of the most capable detection and defence organisations in the world, and the fact that they were compromised is a sobering reminder that the gap between offense and defence is, today, massively lopsided in favour of the attacker." said Beardsley.
Who is behind Duqu 2.0?
The problem of attribution for a cyber-attack is hard to solve. An attacker could introduce false flags in order to deceive the investigators. A similar tactic was adopted by the authors of Duqu 2.0 according to Mikko Hypponen. They added one of the drivers that contain the string "ugly.gorilla" used by the Chinese APT known as Comment Crew.
The various teams involved in the analysis of the Duqu malware speculate the involvement of a state actor. Duqu was the product of a joint effort of the NSA Tao and the Israeli Unit 8200; it's obvious that both intelligence agencies are suspected also for the development of Duqu 2.0. The analysis published by Kaspersky revealed that Duqu 2.0 was not designed by the Equation Group, this means that Israel remains the prime suspect for the campaign. The same opinion is shared by Richard Bejtlich of FireEye.
Based only on multiple elements of the @KimZetter story of @kaspersky intrusion, it seems that "Duqu 2.0″ might be an Israeli campaign.
— Richard Bejtlich (@taosecurity) 10 Giugno 2015
Conclusion
Based on the analysis of various security firms, the experts believe that Duqu 2.0 is a government-malware that represents an evolution of the original strain of Duqu. The experts believe that Duqu and Duqu 2.0 were developed by the same pool of developers. Duqu 2.0 is a powerful spyware that was designed to remain under the radars for long term.
The authors of Duqu 2.0 have likely used the malware as one of their main tools in multiple cyber espionage campaigns.
"Given that activity surrounding the original version of Duqu dropped off following its discovery, it is likely that the group may now retreat before re-emerging with new malware. " states the experts at CrySyS Lab.
Let me close suggesting you the reading of the Indicators of Compromise (IOCs) provided by Kaspersky, which include MD5s and IPs from the command and control servers.
Sources
- Duqu 2.0 hit kaspersky
- Duqu 2.0 reemergence
- Duqu 2.0 stolen certificate
- Duqu 2.0 developed by Israel
- The mystery of Duqu 2.0
- Duqu 2.0
- Duqu 2.0 - Crysys