xHelper malware: What it is, how it works and how to prevent it | Malware spotlight
Research shows malware spreading and directed specifically at mobile users. Check Point’s 2019 Mid-Year Trends Report shows that cyberattacks targeting smartphones and other mobile devices were reported as up by 50% compared to 2018. Many users are now relying on mobile anti-malware solutions, with mixed results; some malware has been designed in ways that allows it to effectively bypass defenses and continue to work against the users, according to their scope. One such pervasive malware is xHelper.
xHelper was first seen in March 2019 and immediately showed itself as difficult to identify and delete. As a result, it’s been added to the overall top 10 malware list at #8 and was featured in Check Point’s Global Threat Index for November as being one of the most prevalent mobile malware. By summer 2019, Malwarebytes added this multi-purpose Android Trojan on its top 10 list of most-detected mobile malware.

Become a certified reverse engineer!
What is xHelper?
xHelper is among the family of trojan droppers that delivers malware on mobile devices. It quickly infected over 45,000 devices during a six months period in 2019. That number since then has continued to rise by the hundreds daily, with this malware still showing up strong in 2020.
One of the peculiarities of xHelper is its resistance to any form of detection and deletion. Users can even perform factory resets, and the malware soon shows again and continues to thrive on their mobile devices. “The malware sits silently on the device and waits for commands from the attackers.” It also “modifies a system library (libc.so) intending to prevent infected users from re-mounting system partition in the write mode.”
Also annoying are the intrusive pop-ups or notification spam, redirects showing advertisements or promotions of other sites and services that generate pay-per-click revenue. These are all examples of the semi-stealthy xHelper version, which, upon installation, creates an icon in notifications that is titled “xhelper.”
There is also another version, a stealthier variant of the malware. This is considered more dangerous, as it can not only infect Android devices with more malicious threats but compromise the settings of the infected device. It is a stealth version because on install, no icons are created in notifications; the only evidence of its presence is a simple xHelper listing in the app info section.
Working in the background, xHelper is also able to hide almost all traces of its existence. This malware, in fact, is designed to stay hidden by not appearing on the system’s launcher.
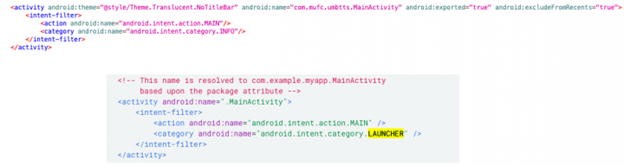
Figure 1. The xHelper code used to remove app from application launcher (top) and list app in launcher (bottom) — Symantec Enterprise Blogs Threat Intelligence
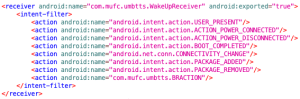
According to May Ying Tee and Tommy Dong, Software Engineers of Symantec’s Security Technology and Response team, xHelper’s application component not only has puzzled researchers by being able to hide and not appear on the system’s launcher, but also, “the malicious app is launched by external events, such as when the compromised device is connected to or disconnected from a power supply, the device is rebooted, or an app is installed or uninstalled.”
They also mention that xHelper code is not a static malware. It has, in fact, changed over time, and its functionality also expanded dramatically most recently. Therefore, there are still a lot of unknowns with the xHelper variants.
Figure 2. xHelper’s manifest code showing the events that will trigger the malware — Symantec Enterprise Blogs Threat Intelligence
How does xHelper work?
Kaspersky's Igor Golovin describes the malware as a matryoshka-style scheme, a “Russian nesting doll” using a multi-stage infection process, which "disguises itself as a popular cleaner and speed-up app" on Android smartphones. It has been affecting mostly users in Russia (80.56%), India (3.43%) and Algeria (2.43%) and annoying users by downloading and installing adware from third-party apps and showing irritating ads and popups. Users have also reported that xHelper is so resilient that it survives factory resets.
An example is the so-called Android/Trojan.Dropper.xHelper that is linked to a puzzle called New2048HD with the package name com.mufc.fireuvw, which no longer appears in the Google Play app store but shows up in third-party markets. Those infected by xHelper have been, in the past, victims affected primarily from inexpensive, Chinese-made smartphones running Android 6 Marshmallow or Android 7 Nougat, and that get their apps from sources other than the official Google Play store.
Figure 3. The puzzle called New2048HD
Security experts and malware analysts found that the popular 2048 math game after installation could launch its own payload to retrieve consumer data and upload it to either a specific URL or to the malware's creators’ phone number via SMS. In addition, it was possibly responsible for further infection of the device by installing malicious files directly into the system partition.
The xHelper malware is not a standard .apk file format stored in the Assets Directory. Instead, it is a machine-readable .dex file with a .jar extension (with the filename of xhelperdata.jar or firehelper.jar) that downloads and installs (or "drops") adware on devices. Using a set of exploits, it can then install malicious files directly in the system partition.
No one so far has a clear idea of how xHelper remains installed, but Emma Davis, author at How To Fix Guide, believes the malware survives using special directories that it creates on the device and where it hides its APK. As users find out, the app remains installed in /system/. They are advised to go to the app permission settings and block/disable notifications for xHelper to completely erase all traces of the malware, as well as get rid of annoying popups and ads.
How to prevent xHelper
It is always recommended to install an antivirus program for Android that can detect malware before being deployed on the system. If you suspect malware, download a legitimate anti-malware program that protects against the Trojan.Dropper.xHelper at least to a certain degree.
There are some useful security apps for users to download found at Google Play. For example, Sophos Intercept X for Mobile scans for malware, checks storage media for malicious or inappropriate content, blocks malevolent websites and more. This app protects an Android device, for free. Otherwise, one can optimize a phone with Trend Micro Mobile Security for Android that offers protection from malware and web threats, plus unwanted access to the device. It can also restore the smartphone's normal settings. However, this product is not free.
If, regardless of the defenses put in place, xHelper has infected your mobile device, then one of the ways that could possibly help stopping it from re-infecting over and over again using a hidden directory containing an APK is to disable Google PLAY temporarily to stop reinfection while performing clean ups and resets.
- Go to Settings > Apps > Google Play Store
- Press Disable button
To re-enable Google Play:
- Go to Settings > Apps > Google Play Store
- Press Enable button
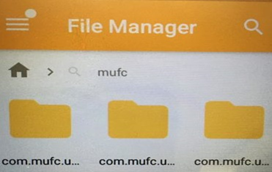
Also in File Manager, go ahead and delete anything starting with com.mufc. This is the advice of Nathan Collier, Senior Malware Intelligence Analyst, in Malwarebytes’ commentary on how to remove xHelper re-infections.
Figure 4. Using an Android file manager to delete the mufc folders and all their contents
Catalin Cimpanu, a security reporter at ZDNet, suggests the following: “The only way to remove xHelper [may be] to perform a full device reflash by reinstalling the entire Android operating system, a solution that was not possible for all infected users, many of whom didn't have access to the correct Android OS firmware images to perform a reflash.”
Finally, be sure to submit a report if you find an app that you believe is in violation of Google Play Content Policies.
Conclusion
xHelper is a mobile Trojan that is almost immortal with the ability to reinstall itself; in fact, users cannot delete it even after doing a full reset on their phone. xHelper is a great example of why users need to be very careful with anything they download even from official stores like Google Play and more, from third-party sources.
At the end of the day, security awareness enhancement is key for malware resistance and is always the first line of defense whenever the user is involved.

Become a certified reverse engineer!
Sources
- Mobile malware attacks are booming in 2019: These are the most common threats, ZDNet
- How to get rid of xHelper Virus, Sangam
- Unkillable xHelper and a Trojan matryoshka, AO Kaspersky Lab
- Remove xhelper (Free Guide) - Removal Instructions, 2-spyware
- Xhelper: Persistent Android Dropper, Symantec Enterprise Blogs | Threat Intelligence
- xHelper: The Russian Nesting Doll of Android Malware, Threatpost
- Mobile Menace Monday: Android Trojan raises xHelper, Malwarebytes Labs
- Mobile Threat Monday: '2048' Android Fans, Beware, PCMag
- Nasty Android malware reinfects its targets, and no one knows how, Ars Technica
- Android devices are infected by new unremovable Xhelper malware, Arridae Infosec
- 'Unremovable' Malware Infects 45,000 Android Phones: What You Need to Know, Tom's Guide
- Experts figured out why the xHelper Trojan is considered “unkillable”, HowToFix.Guide
- 'Unkillable' Android malware can take over your phone: What to do, Tom's Guide
- How to Report Suspicious Apps in the Android Market, Android Authority
- 15 best antivirus apps and best anti-malware apps for Android!, Android Authority
- This is why the vicious xHelper malware resists factory wipes and reboots, ZDNet
- There's finally a way to remove xHelper, the unremovable Android malware, ZDNet
- Unveiled: How xHelper Android Malware Re-Installs Even After Factory Reset, The Hacker News
- Android Trojan xHelper uses persistent re-infection tactics: here’s how to remove, Malwarebytes Labs
- November 2019’s Most Wanted Malware: Researchers Warn of Fast-growing Mobile Threat While Emotet’s Impact Declines, Check Point Software Technologies Ltd.