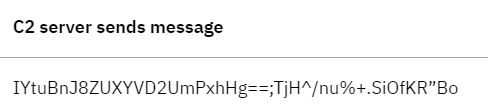Vizom malware: What it is, how it works and how to prevent it | Malware spotlight
The Vizom Trojan is an active piece of malware targeting online banking users in Brazil that takes advantage of the window overlay technique to steal user’s details. In this article, we will take a deep dive into techniques, tactics and procedures (TTP), how it infects the victims’ devices and how this threat can be prevented in general.
Introduction
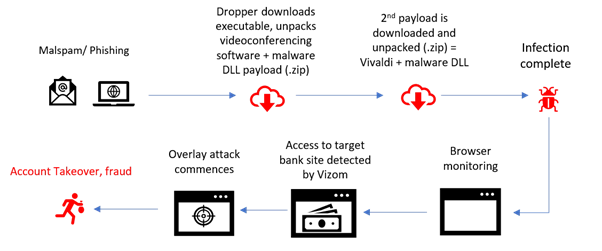
The Vizom Trojan spreads via phishing campaigns and impersonates popular videoconferencing software to reach a large number of victims. These target tools used by Vizom to spread in the wild are crucial these days to businesses and social events, due to the COVID-19 pandemic situation. Many people are using videoconferencing software to communicate online or to meet online during remote work. Figure 1 presents a high-level diagram of Vizom malware.
Figure 1: Vizom’s infection chain and fraud method (source)
The malware starts its infection process when the victim downloads and installs the target file — the initial dropper. After executing the dropper, a ZIP file with malicious DLLs inside is moved onto the APPDATA %temp% folder.
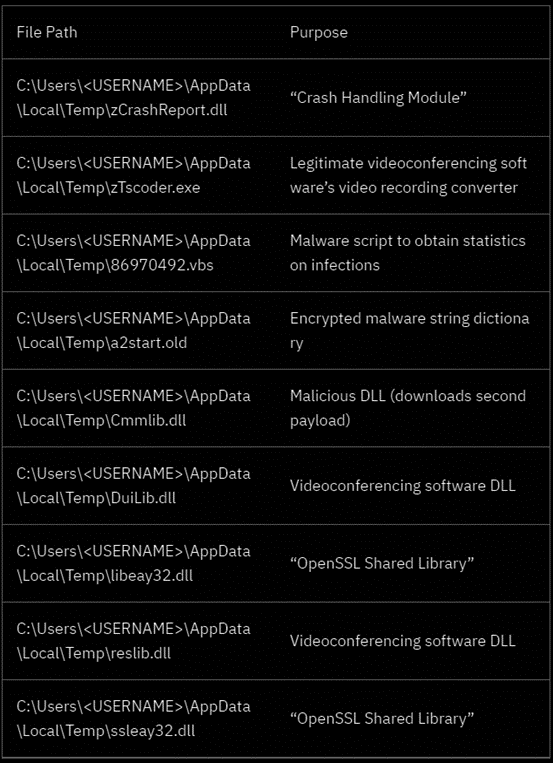
The following list shows what Vizom’s dropper unpacks after it initially reaches a new victim device.
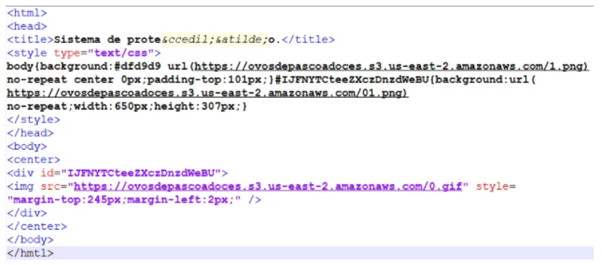
Figure 2: Mix of legitimate and malicious resources from Vizom malware installed during the infection chain
DLL injection to execute the threat
After dropping the malicious DLLs on disk, the malware abuses a legitimate videoconferencing software to load into the memory the malicious DLLs — a technique also known as DLL injection. By doing that, Vizom malware takes advantage of running the malicious DLL as the child process of a benign videoconferencing file. In fact, this is a common trick used by criminals to bypass AV detection and make its analysis difficult.
Because the Windows operating system loads DLLs following a certain structure, when an executable is started, it looks for dependent DLLs in the same directory from which it is executed. This is the main trick used by criminals at this point.
In detail, a Windows operating system have some ways of loading dependent DLLs, namely:
- It searches the directory from which that application was called and/or loaded
- It searches in C:\Windows\System32
- Searches in C:\Windows\System
- Goes up and searches in C:\Windows
- Searches the current working directory
- Searches directories in the entire system’s PATH environment variable
- Finally, it searches directories in that user’s PATH environment variable
As described in this case, Vizom’s malicious DLLs are saved in the same directory of the executable file that loads them into the memory during its execution. In this case, the malicious DLL’s name was taken from a popular videoconferencing software: “Cmmlib.dll”.
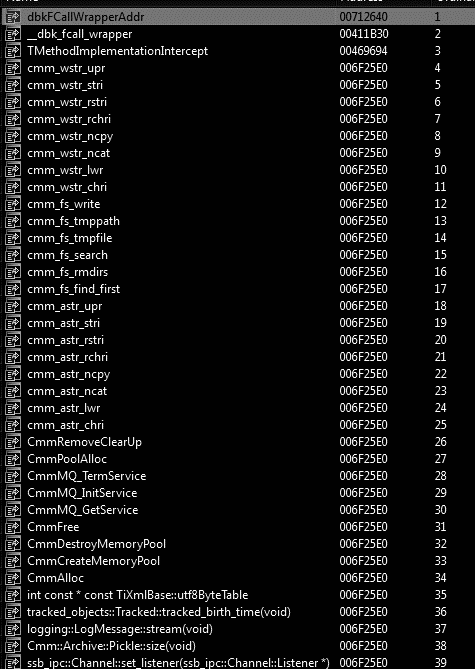
An interesting detail is that the malware’s author copied the real export list of that legitimate DLL but all the functions have the same address as observed below — in fact, the malicious code’s address space.
Figure 3: Cmmlib.dll export list showing the same address for all functions
Downloading the next stage
The next task is to execute an HTTP request and download the next stage from an AWS S3 bucket online. The binary “zTscoder.exe” installed initially in the %temp% folder is then used to perform this activity. At this point, Vizom downloads another ZIP file from a remote server.
--
hxxps://galinhaborabora[.]s3[.]amazonaws.com/felicidadeviver[.]zipIn detail, this file contains inside a legitimate browser application called Vivaldi, a browser program based on Chromium.
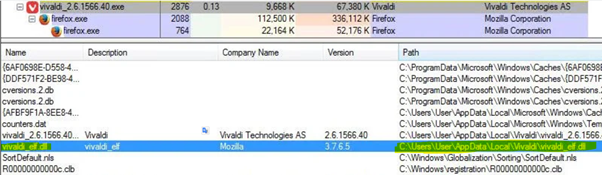
Vivaldi is dropped into the target system along with the malware’s malicious DLLs. Once again, the target DLLs are loaded into the memory using the Vivaldi application in order to avoid detection. The DLL injection technique previously decribed is used again by Vizom.
Figure 4: Final DLLs are loaded into memory
Vizom persistence technique
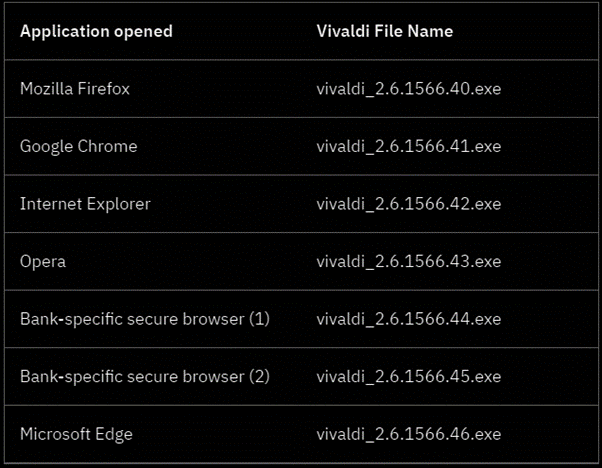
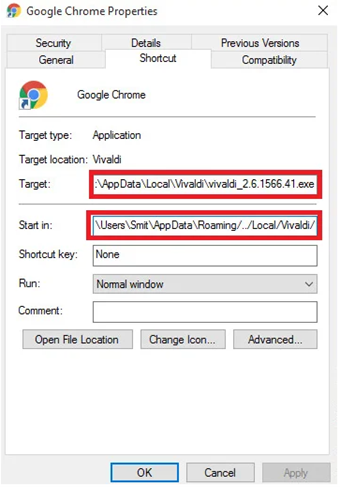
To ensure that the malware is executed every time the user’s device is started, Vizom modifies the browser’s shortcuts and adds the malicious path where the Vivaldi software is installed. When executed, the browser is launched as a child of Vivaldi’s process (see Figure 4 above). The browser’s shortcuts are modified according to the next table.
Figure 5: Vizom persistence technique (changing shortcut path)
Trojan capabilities
Vizom has some malicious capabilities that allow it to operate the infection chain after it is installed on the victim’s device. Those components include:
- Browser monitoring
- Communication with the attackers’ (C2) server in real time
- Remote access Trojan
- Malicious overlay screens module
Like other active Trojans in the wild, such as Grandoreiro, Lampion and URSA, Vizom uses overlay windows to lure the victims when they are accessing the legitimate banking portals.
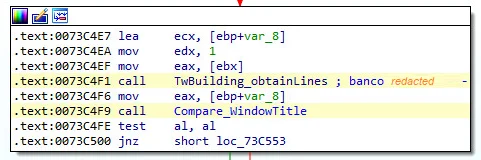
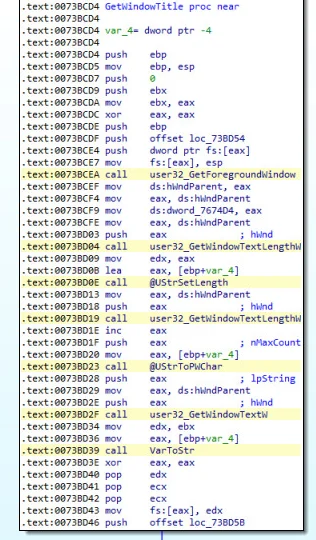
The malware is monitoring the browser’s activity and obtains the title of the browser window comparing it with the malicious strings hardcoded inside the binary. If the obtained string is one of the target banking portals hardcoded, the overlay process starts. This comparison happens continually in a loop.
Figure 6: Vizom window tab monitoring and string comparison
Figure 7: Vizom overlay window (source code)
Vizom malware uses TCP sockets to communicate with the C2 server. In detail, the communication with the C2 server is based on a reverse shell where the infected machine communicates back to the attacking server and a listener port receives the connection. Also, Vizom’s communication with the C2 server is encrypted with AES256 using Delphi’s TCryptographicLibrary.
The messages sent between the infected device and the C2 server are encrypted and using a particular format. The encrypted data and the key are separated by a semi-colon (;), as seen below.
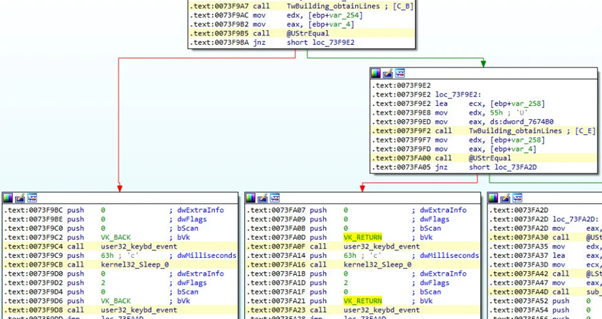
Like other Brazilian Trojans, all the victim’s activity is monitored, including the mouse clicks and keyboard keystrokes.
Figure 8: Keyboard keystrokes accessed via keybd_event API
At this point, criminals can monitor all the victim’s activity, using a remote backoffice portal with all the exfiltrated information and sensitive details.

Become a certified reverse engineer!
Prevention measures
These days, Latin American malware have abused overlays to performs its malicious activity and at the same time lure the victims when they are accessing legitimate banking portals. This approach has been observed in several Brazilian Trojans and seen as an effective way of breaking barriers and, thus, to evade AV and EDR detection.
Although there is no solution to avoid malware infections, there are several good practices we would like to recommend to improve the resilience of a system and its protection:
- Never open links or download attachments from emails from unknown sources
- Check email senders and if it was potentially spoofed
- Inspect the email for grammatical errors or misspelled words
- If you don’t trust the email, contact the companies that supposedly sent the email to check that the messages came from them
- Use updated systems, including operating systems, installed software, and antivirus
- Get into phishing training as it can be an excellent tool to prevent you from have being infected via social engineering schemas
Sources
This new malware uses remote overlay attacks to hijack your bank account, ZDNet
New Vizom Malware Discovered Targets Brazilian Bank Customers with Remote Overlay Attacks, SecurityIntelligence