Trojan URSA malware: How it works and how to prevent it
Different pieces of malware have emerged in the wild with distinct approaches and ways of operating. In 2020, a new piece of malware called URSA, also known as Mispadu malware by ESET, was documented and analyzed. This is a trojan malware that steals credentials from the victim’s computers and executes a banking overlay in order to collect banking data by simulating the pages of the legitimate banking portal. The modus operandi and tactics techniques and procedures (TTPs) of the URSA trojan will be analyzed and we will share some preventative measures to counter potential infections of this nature.

Become a certified reverse engineer!
URSA's modus operandi
Since June 2020, malspam campaigns related to the URSA Trojan have affected users in several countries including Bolivia, Chile, Mexico, Argentina, Ecuador, Peru, Colombia, Paraguay, Costa Rica, Brazil, Spain, Italy and Portugal.
URSA is a relatively recent malware and aims to steal banking credentials through browsers when the victim visits their banking portals. This piece of malware is characterized by obtaining credentials from infected devices, mainly web-browsers, email clients such as Outlook, Thunderbird and even FTP clients. For this, the malware uses embedded legitimate tools (LOLbins) that allow bypass endpoint detection and response (EDR) and traditional antivirus software.
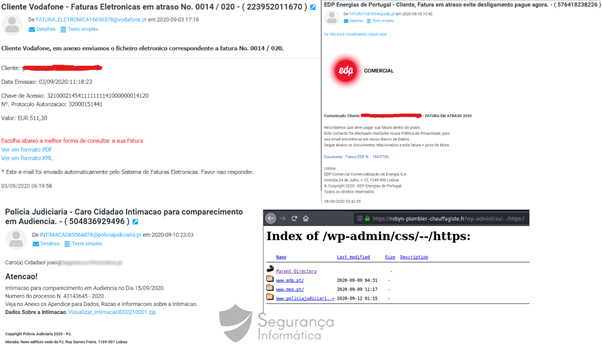
The threat is disseminated globally through social engineering campaigns that impersonate different types of companies from several sectors. As observed in Figure 1, the messages disseminated are related to invoices and often are sent at the end of the month to simulate a real scenario related to payment of bills, rent and so on. [CLICK IMAGES TO ENLARGE]
Figure 1: Phishing templates used in trojan URSA campaigns.
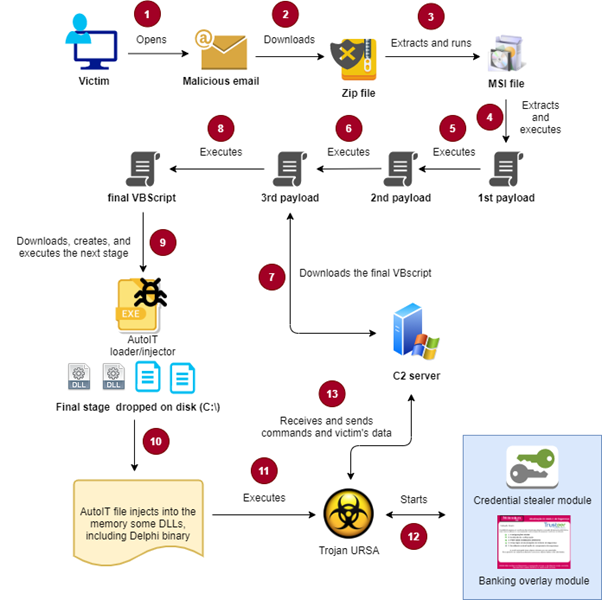
The malicious file (.zip) is often downloaded when the victim visits the link available on the email body. The infection chain is composed of several rabbit holes, and after executing several steps of deobfuscation, the loader/downloader begins the process of getting the next stage from the C2 server available on the internet (step 9, highlighted in Figure 2).
Figure 2: High-level diagram of Trojan URSA malware.
Several validations are performed before infecting the target device, including:
- Virtual environment detection (VirtualBox, VMWare and Hyper-V)
- Validate system language settings
- Check the computer name
Through this approach, criminals validate whether the victim is able to be infected. Only devices with the language settings presented below are infected by this threat.
According to the seguranca-informatica.pt blog, “If the victim’s computer is executing in a language ID different from the hardcoded, or the computer name is equal to “JOHN-PC," the infection process stops. Change the computer name to “JOHN-PC” is a potential killswitch to avoid URSA infections.”
The final malicious stage of URSA
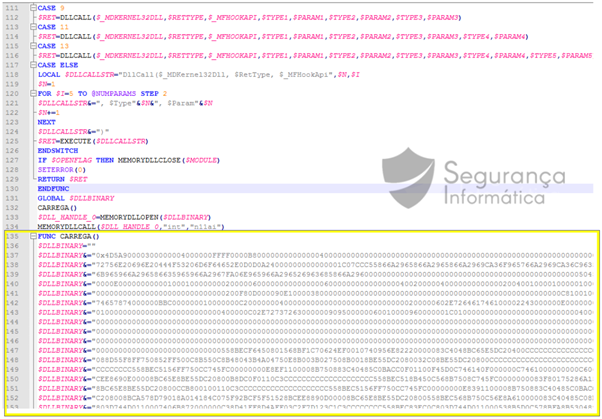
After some rounds of deobfuscation and anti-debug and VM techniques, an AutoIT executable is used to inject the last stage of the URSA malware into the memory. This script is a modified version of the AutoIT compiler and used by criminals to bypass antivirus behavior analysis during the infection process. Although this is not a new TTP, the usage of this approach is bypasses EDR and antivirus detection.
Figure 3: URSA process injection via an AutoIt binary file.
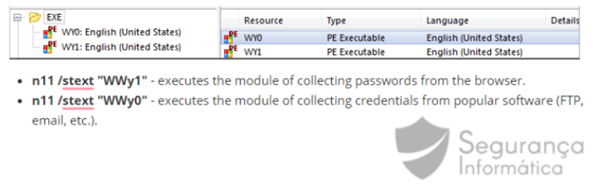
Another interesting trick employed by this malware are the embedded executables used to perform the credential’s harvesting process. In detail, legitimate tools are available inside the binary and launched dynamically during its execution.
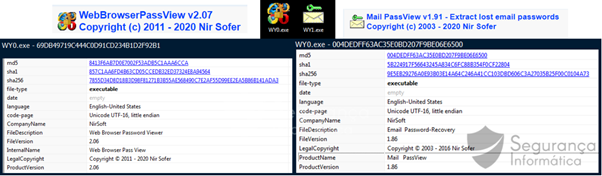
Figure 4: Legitimate tools available inside the malware binary.
As observed in figure 5, these tools are part of the toolset from Nir Sofer and classified as trusted by some antivirus solutions. By using them, criminals obtain a fully undetectable scenario. The binaries NirSoft’s WebBrowserPassView and Mail PassView will collect the user’s data and send the data to the C2.
Figure 5: LOLbins used by trojan URSA to bypass its detection and collect credentials from different sources.
From URSA harvesting to the exfiltration process
During the harvesting process, credentials from different locations are obtained, including:
- Credentials stored in web browsers
- Data from email clients such as Outlook emails and passwords
- FTP credentials from Filezilla
- Data typed by the victim during the banking impersonation process via overlay windows
Figure 6 below shows data exfiltrated by this malware and sent to the C2 controlled by criminals.
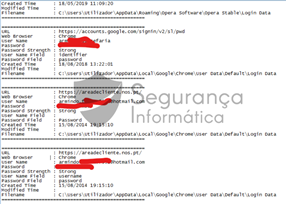
Figure 6: Exfiltrated data during the malware execution.
According to seguranca-informatica.pt analysis, several banking organizations are impacted by this threat around the globe. The full list is depicted below.
.text:039E67EC 0000001C unicode BANCOUNION_BO
.text:039E6814 0000000E unicode BNB_BO
.text:039E6830 00000010 unicode BISA_BO
.text:039E684C 0000000E unicode BCP_BO
.text:039E6868 00000014 unicode FASSIL_BO
.text:039E6888 00000018 unicode BANCOFIE_BO
.text:039E68AC 00000018 unicode BANCOSOL_BO
.text:039E68D0 0000000C unicode BG_BO
.text:039E68E8 00000014 unicode BANECO_BO
.text:039E6908 0000001A unicode CORPBANCA_CH
.text:039E6930 00000010 unicode BBCA_CH
.text:039E694C 00000024 unicode BANCOFALABELLA_CH
.text:039E697C 00000020 unicode BANCOEDWARDS_CH
.text:039E69A8 0000001E unicode BANCORIPLEY_CH
.text:039E69D4 00000018 unicode TBANCWLS_CH
.text:039E69F8 00000014 unicode BANEFE_CH
.text:039E6A18 0000001C unicode SCOTIABANK_CH
.text:039E6A40 00000010 unicode BICE_CH
.text:039E6A5C 0000001C unicode BANCOINTER_CH
.text:039E6A84 00000024 unicode BANCOCONSORCIO_CH
.text:039E6AB4 00000010 unicode BITCOIN
.text:039E6AD0 0000000E unicode PAYPAL
.text:039E6AEC 00000014 unicode BANKIA_ES
.text:039E6B0C 00000018 unicode SABADELL_ES
.text:039E6B30 0000001A unicode BANKINTER_ES
.text:039E6B58 00000018 unicode IBERCAJA_ES
.text:039E6B7C 0000001A unicode LIBERBANK_ES
.text:039E6BA4 00000014 unicode ABANCA_ES
.text:039E6BC4 0000001C unicode KUTXABANCA_ES
.text:039E6BEC 00000016 unicode UNICAJA_ES
.text:039E6C10 00000012 unicode GERAL_PT
.text:039E6C30 0000000E unicode BPI_PT
.text:039E6C4C 0000001A unicode NOVOBANCO_PT
.text:039E6C74 0000000E unicode BCP_PT
.text:039E6C90 0000000E unicode CGD_PT
.text:039E6CAC 00000014 unicode ACTIVO_PT
.text:039E6CCC 00000018 unicode MONTEPIO_PT
.text:039E6CF0 0000001C unicode CREDITOAGR_PT
.text:039E6D18 0000000E unicode BPM_IT
.text:039E6D34 00000010 unicode BPER_IT
.text:039E6D50 00000016 unicode UNICRED_IT
.text:039E6D74 00000018 unicode SAMPAOLO_IT
.text:039E6D98 0000000E unicode BNL_IT
.text:039E6DB4 00000018 unicode BANCAMPS_IT
.text:039E6DD8 0000001A unicode SANTANDER_CH
.text:039E6E00 0000001A unicode SANTANDER_ES
.text:039E6E28 00000010 unicode BBVA_ES
.text:039E6E44 0000001A unicode CAIXABANK_ES
.text:039E6E6C 0000001A unicode SANTANDER_PT
.text:039E6E94 00000010 unicode BBVA_MX
.text:039E6EB0 00000014 unicode AZTECA_MX
.text:039E6ED0 00000016 unicode BANAMEX_MX
.text:039E6EF4 00000016 unicode BANORTE_MX
.text:039E6F18 00000012 unicode SANTA_MX
.text:039E6F38 00000010 unicode HSBC_MX
.text:039E6F54 00000014 unicode SCOTIA_MX
.text:039EA11C 0000000A unicode bbva
.text:039EA134 0000000A unicode xico
.text:039EA184 0000000A unicode BBVA
.text:039EA1AC 0000000C unicode banco
.text:039EA1E0 0000001A unicode Banco Azteca
.text:039EA208 0000001C unicode banconacional
.text:039EA230 00000010 unicode agrcola
.text:039EA24C 00000032 unicode Banco Nacional de México
.text:039EA28C 00000010 unicode banorte
.text:039EA2A8 00000010 unicode Banorte
.text:039EA2C4 00000014 unicode santander
.text:039EA2E4 0000001E unicode bancadeempresa
.text:039EA310 0000000C unicode mxico
.text:039EA328 00000012 unicode gobierno
.text:039EA348 0000000A unicode pyme
.text:039EA360 00000020 unicode Banco Santander
.text:039EA38C 00000014 unicode caixabank
.text:039EA3AC 00000008 unicode bpi
.text:039EA3C0 00000014 unicode CaixaBank
.text:039EA3E0 00000016 unicode scotiabank
.text:039EA404 0000000E unicode Scotia
.text:039EA420 0000000A unicode hsbc
.text:039EA438 0000000A unicode HSBC
.text:039EA450 0000000A unicode solu
.text:039EA468 00000010 unicode advance
.text:039EA484 00000012 unicode investor
.text:039EA4A4 00000012 unicode Santader
.text:039EA4C4 00000016 unicode blockchain
.text:039EA4E8 00000010 unicode bitcoin
.text:039EA504 00000010 unicode binance
.text:039EA520 00000012 unicode coinbase
.text:039EA540 0000000E unicode kraken
.text:039EA55C 0000000E unicode crypto
.text:039EA578 00000012 unicode primebit
.text:039EA598 0000000C unicode bitso
.text:039EA5B0 0000000E unicode paypal
.text:039EA5CC 0000000E unicode bankia
.text:039EA5E8 0000001C unicode bancosabadell
.text:039EA610 00000014 unicode bankinter
.text:039EA630 00000012 unicode ibercaja
.text:039EA650 00000014 unicode liberbank
.text:039EA670 0000000E unicode abanca
.text:039EA68C 00000014 unicode kutxabank
.text:039EA6AC 0000001A unicode unicajabanco
.text:039EA6D4 00000012 unicode bancobpi
.text:039EA6F4 00000014 unicode novobanco
.text:039EA714 0000001C unicode millenniumbcp
.text:039EA73C 0000001A unicode caixadirecta
.text:039EA764 00000016 unicode activobank
.text:039EA788 00000012 unicode montepio
.text:039EA7A8 00000014 unicode crditoagr
.text:039EA7C8 0000002C unicode bancapopolaredemilano
.text:039EA800 00000012 unicode bancobpm
.text:039EA820 0000000A unicode bper
.text:039EA838 00000014 unicode unicredit
.text:039EA858 00000010 unicode banking
.text:039EA874 00000028 unicode bancaintesasanpaolo
.text:039EA8A8 00000008 unicode bnl
.text:039EA8BC 0000000C unicode banca
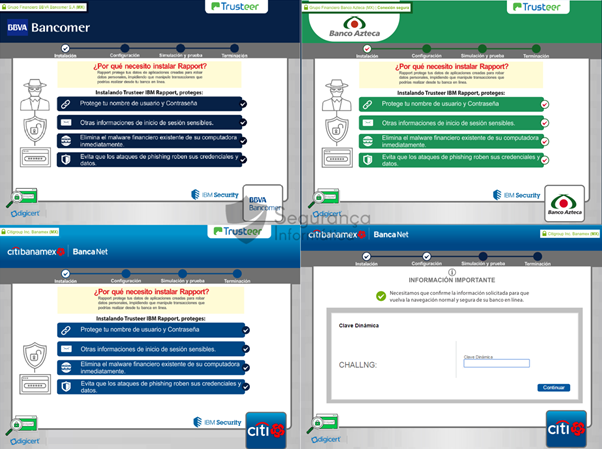
.text:039EA8D4 00000012 unicode bancampsWhen the victims access the target banking organizations, the overlay windows are triggered and the malicious windows are presented according to a well-defined sequence. In detail, criminals can steal the authentication data used to access the legitimate banking portal, bypassing additional protection mechanisms such as multi-factor authentication layers, and even performing wire transfers with the user’s consent. Some overlay windows extracted from that process are shown below.
Figure 7: Banking overlay windows used by URSA trojan to steal sensitive data during the infection process.
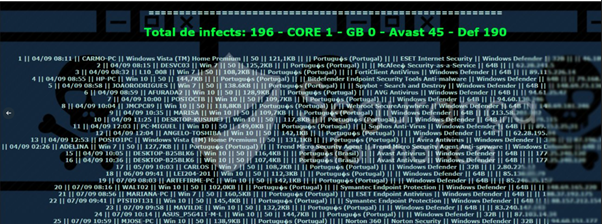
Finally, all the collected data is sent to the C2 server available on the internet. URSA servers are often geolocated in Brazil, as documented in the original research.
Figure 8: Details from victims infected by URSA trojan. Data collected from the C2 server online.
URSA prevention measures
Although there is no perfect formula to fight malware in general, there are several good practices that aim to improve the resilience of a system and its protection:
- Never open links or download attachments from emails from unknown sources
- Check email senders
- Inspect the email for grammatical errors or misspelled words
- If you don’t trust the email, contact the companies that supposedly sent the email to check that the messages came from them
- Use updated systems, including operating systems, installed software and antivirus
- Get into phishing training as it can be an excellent tool to prevent you from have being infected via social engineering schemes
Sources:
Full analysis and report, Segurança Informática
Mispadu Banking Trojan Resurfaces, TrendMicro