The VPNFilter: A Powerful Botnet of More Than 500k Devices Ready to Attack
VPNFilter botnet - The discovery
Security researchers at Talos group, along with colleagues from other cybersecurity firms and law enforcement agencies, have discovered a huge botnet composed of more than 500,000 compromised routers and network-attached storage (NAS) devices.
The experts believe the botnet, tracked as VPNFilter, was the product of the Russian Government and was operated by one of the APT groups linked to the Kremlin.
The malware associated with VPNFilter botnet appears very sophisticated, at the time of its discovery it has compromised more than 500,000 devices across 54 countries.
“For several months, Talos has been working with public- and private-sector threat intelligence partners and law enforcement in researching an advanced, likely state-sponsored or state-affiliated actor’s widespread use of a sophisticated modular malware system we call ‘VPNFilter,'” reads the blog post published by Talos.
“We have not completed our research, but recent events have convinced us that the correct way forward is to now share our findings so that affected parties can take the appropriate action to defend themselves.”
The investigation is still ongoing, even if the botnet was attributed to Russia-linked APT groups, it is not clear how the attackers planned to use it, anyway security experts and law enforcement decided to take actions by publishing a report on the threat and seized a domain of its infrastructure due to an imminent massive attack powered by VPNFilter.
Technical analysis of the code revealed many similarities with another nation-state malware, the BlackEnergy malware that was specifically designed to target ISC-SCADA systems and attributed to Russian threat actors.
Another similarity is the geographic distribution of the infections, both BlackEnergy and VPNFilter infected a large number of devices in Ukraine.
According to the experts, many infected devices have been discovered in Ukraine, and their number in the country continues to increase. On May 8, Talos researchers observed a spike in VPNFilter infection activity, most infections in Ukraine and the majority of compromised devices contacted a separate stage 2 C2 infrastructure at the IP 46.151.209[.]33.
The experts discovered the VPNFilter malware had infected devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link.
VPNFilter is a multi-stage, modular strain of malware that has a wide range of capabilities for both cyber espionage and sabotage purpose.
“As of this writing, we are aware of two plugin modules: a packet sniffer for collecting traffic that passes through the device, including theft of website credentials and monitoring of Modbus SCADA protocols, and a communications module that allows stage 2 to communicate over Tor.” continues the report.
“We assess with high confidence that several other plugin modules exist, but we have yet to discover them.”
Malware analysis revealed that the second stage of malware, the one that implements malicious capabilities, can be removed from an infected device by rebooting it. Unfortunately, the first stage of malware implements a persistence mechanism.
At the time of writing, the experts haven’t yet identified the attack vector; they are particularly concerned by the destructive capabilities of the malware that could allow attackers to burn users’ devices to cover up their tracks.
Part of the cybersecurity community believes that the botnet could be used to launch a massive attack during the Ukrainian celebration of the Constitution Day, last year the NotPetya wiper attack was launched on the same period.
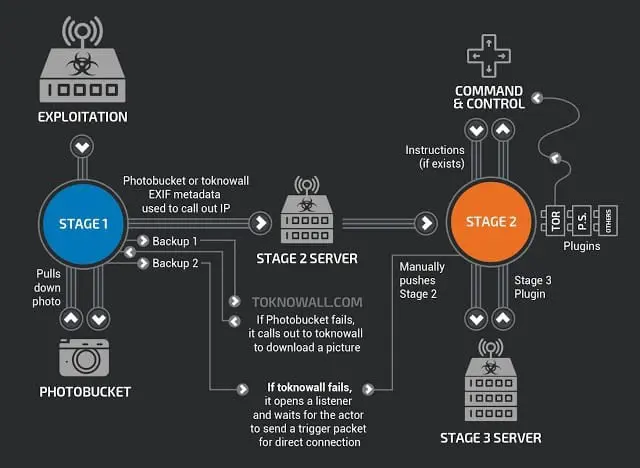
Figure 1 - VPNFilter
“VPNFilter is an expansive, robust, highly capable, and dangerous threat that targets devices that are challenging to defend. Its highly modular framework allows for rapid changes to the actor’s operational infrastructure, serving their goals of misattribution, intelligence collection, and finding a platform to conduct attacks,” Talos concluded.
SCADA/ ICS, the VPNFilter target
The VPNFilter malware targets SCADA/ICS environments by monitoring MODBUS SCADA protocols and exfiltrating website credentials.
The malware implements a destructive capability that can render a compromised device unusable, but the most scaring aspect is that the malicious code could be activated on a large scale to conduct a massive attack. This latter feature has the potential of cutting off internet access for hundreds of thousands of systems at the same time.
According to the experts at Fortinet that analyzed the malware, VPNFilter operates in the following three stages:
- Stage 1 implements a persistence mechanism and redundancy; it allows the malware to survive a reboot.
- Stage 2 includes data exfiltration, command execution, file collection, and device management. Only in some versions it is present a self-destruct module.
- Stage 3 includes multiple modules that perform different tasks. At the time researchers identified only three modules:
- A packet sniffer for traffic analysis and potential data exfiltration.
- The monitoring of MODBUS SCADA protocols.
- Communication with obfuscated addresses via TOR
The main concerns are for a self-destruct mode that could cause severe damages across all infected devices simultaneously, a feature that could potentially result in widespread Internet outage over a targeted geographic region.
The Response of Law Enforcement Agencies
On Wednesday, the Justice Department announced an effort to disrupt the VPNFilter botnet of hundreds of thousands of infected home and office (SOHO) routers and other connected devices under the control of a Russia-linked APT group.
The US Justice Department had seized a domain used as part of the command and control infrastructure, its press release explicitly refers the Russian APT groups (APT28, Pawn Storm, Sandworm, Fancy Bear and the Sofacy Group) as the operators behind the huge botnet,
“The Justice Department today announced an effort to disrupt a global botnet of hundreds of thousands of infected home and office (SOHO) routers and other networked devices under the control of a group of actors known as the “Sofacy Group” (also known as “apt28,” “sandworm,” “x-agent,” “pawn storm,” “fancy bear” and “sednit”),” reads the press release published by the DoJ.
“Today’s announcement highlights the FBI’s ability to take swift action in the fight against cybercrime and our commitment to protecting the American people and their devices,” said Assistant Director Scott Smith. “By seizing a domain used by malicious cyber actors in their botnet campaign, the FBI has taken a critical step in minimizing the impact of the malware attack. While this is an important first step, the FBI’s work is not done. The FBI, along with our domestic and international partners, will continue our efforts to identify and expose those responsible for this wave of malware.”
The Justice Department had obtained a warrant authorizing the FBI to seize the domain that belongs to the command and control infrastructure of the VPNFilter botnet.
Technically the operation conducted by the US authorities is called “sink holing,” the seizure of the domain allows law enforcement and security experts to analyze the malicious traffic associated with the botnet to gather further information on the threat and temporarily neutralize it.
Traffic analysis allows researchers to establish the extent of the botnet, its geographic distribution, and other technical details about the ways it operates (i.e., communications protocols, evasion mechanisms, mechanisms to make the botnet resilient to takeover operations).
“To identify infected devices and facilitate their remediation, the U.S. Attorney’s Office for the Western District of Pennsylvania applied for and obtained court orders, authorizing the FBI to seize a domain that is part of the malware’s command-and-control infrastructure.” continues the DoJ.
“This will redirect attempts by stage one of the malware to re-infect the device to an FBI-controlled server, which will capture the Internet Protocol (IP) address of infected devices, pursuant to legal process. A non-profit partner organization, The Shadowserver Foundation, will disseminate the IP addresses to those who can assist with remediating the VPNFilter botnet, including foreign CERTs and internet service providers (ISPs).”
The owners of the compromised SOHO and NAS devices should reboot their devices as soon as possible, the operation will temporarily remove the second stage malware and will cause the first stage malware to connect the C&C domain for instructions.
“Although devices will remain vulnerable to reinfection with the second stage malware while connected to the Internet, these efforts maximize opportunities to identify and remediate the infection worldwide in the time available before Sofacy actors learn of the vulnerability in their command-and-control infrastructure.” continues the DoJ.
The vulnerability will remain, Justice said, but the move will allow them more time to identify and intervene in other parts of the network.
References
https://blog.talosintelligence.com/2018/05/VPNFilter.html
https://securityaffairs.co/wordpress/72829/malware/vpnfilter-botnet.html
https://www.cyberthreatalliance.org/cta-actions-around-vpnfilter/
https://www.fortinet.com/blog/threat-research/defending-against-the-new-vpnfilter-botnet.html
https://securityaffairs.co/wordpress/72851/apt/vpnfilter-botnet-doj.html
https://www.fortinet.com/blog/threat-research/defending-against-the-new-vpnfilter-botnet.html
https://nakedsecurity.sophos.com/2018/05/23/vpnfilter-is-a-malware-timebomb-lurking-on-your-router/
https://www.symantec.com/blogs/threat-intelligence/vpnfilter-iot-malware









