Vigilante Malware: Do We Need a Cyber Vigilante? [Updated 2019]
The Mystery Behind the Linux.Wifatch Malware
Thousands of IoT devices across the world have been infected with a new strain of malware, but this hacking campaign appears quite unusual.
Security experts at Symantec have detected a new malicious code, identified as Linux.Wifatch, which has infected tens of thousands of IoT devices across the world, but the strange thing is that the threat actor behind the botnet hasn't used them for any illegal activities.
The Linux.Wifatch malware is able to compromise routers and other Internet of Things devices, but unlike other malicious code, it acts to improve the security of infected devices.
The backdoors set up by Wifatch would allow a potential attacker to use bots for different activities, including DNS poisoning, traffic redirection and distributed denial-of-service (DDoS) attacks. However, the authors of the Linux.Wifatch seem to have a different motivation. The malware acts as a sort of cyber vigilante: It scans the web search for compromised IoT devices and it analyzes devices using a signature-based detection approach. If it discovers the presence of a malware on the device, it tries to hack it, then it disables the Telnet service to keep other threats out.
This mechanism is not new; other types of malware lock out other malicious code from the infected systems, but Wifatch operates simply to block the infection.
Wifatch has been dubbed by the experts the "Internet of Things (IoT) vigilante" due to its method of operation.
"The further we dug into Wifatch's code the more we had the feeling that there was something unusual about this threat. For all intents and purposes, it appeared like the author was trying to secure infected devices instead of using them for malicious activities," states the blog post published by Symantec.
"Wifatch's code does not ship any payloads used for malicious activities, such as carrying out DDoS attacks, in fact all the hardcoded routines seem to have been implemented in order to harden compromised devices. We've been monitoring Wifatch's peer-to-peer network for a number of months and have yet to observe any malicious actions being carried out through it. In addition, there are some other things that seem to hint that the threat's intentions may differ from traditional malware. Wifatch not only tries to prevent further access by killing the legitimate Telnet daemon, it also leaves a message in its place telling device owners to change passwords and update the firmware."
It is interesting to note that when the vigilant malware gains control of an IoT device, it informs users trying to connect over Telnet that the service has been disabled for security reason and even provides recommendations for preventing attacks.
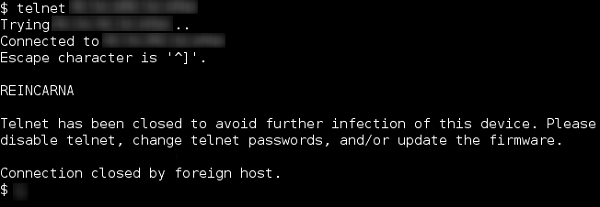
Figure 1 - Malware displayed by the Vigilante Malware
The researcher discovered a specific module in the vigilante malware that has been developed to sanitize the infected IoT devices.
"Some of the threats it tries to remove are well-known families of malware targeting embedded devices. The threat author left a comment in the source code that references an email signature used by software freedom activist Richard Stallman".
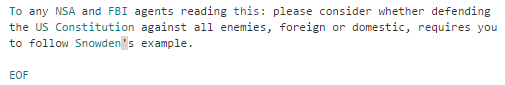
Figure 2 - Comment in the source code of the Vigilante malware
Symantec has identified tens of thousands of devices infected with the vigilante malware across the world; most of them are routers and IP cameras.
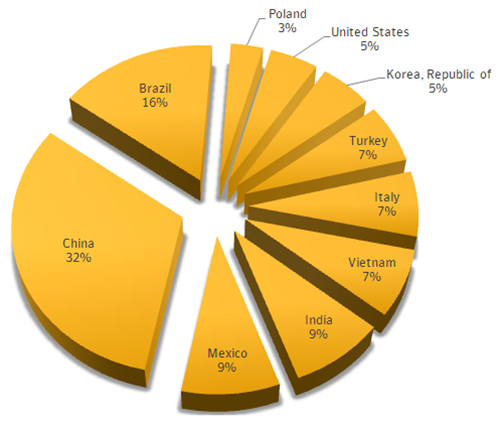
The majority of the infections were observed in China, followed by Brazil (16%), Mexico (9%), India (9%), Vietnam (7%), Italy (7%), Turkey (7%), South Korea (5%), and the United States (5%).
Figure 3 - Wifatch Infections by Countries (Symantec Report)
The analysis of the source code confirmed that the Wifatch is designed to target the principal IoT architectures: The list of compromised systems includes devices based on ARM (83%), followed by MIPS (10%), and SH4 (7%).
The vigilante malware was spotted for the first time in November 2014, thanks to an independent researcher who noticed some suspicious processes on his home router.
"During some exploration of my own home router, I discovered some processes for which I couldn't locate the executable, at least not at the place it was mentioned it should be.
"The process informations were pointing to /sbin/ifwatch-if but actually loaded executable sat in /dev/netslink/ .
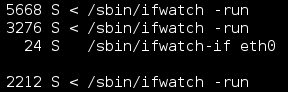
Figure 4 - Analysis made in November 2014 by an independent researcher.
"That path was also present in my mount info, what was another proof of compromise to me," as explained in a blog post by the independent researcher who first detected the vigilante malware.
The experts at Symantec have been monitoring the malware since March 2015.
The researchers speculate that the "Internet of Things (IoT) vigilante" malware is the result of the effort of someone who apparently monitors routers and other IoT devices searching for indicators of compromise; anyway the expert behind the Wifatch did not obfuscate the source code, although it would have been easy for the author to do it.
The malware is developed in Perl and the researchers noticed that each instance of the vigilante malware uses its own Perl interpreter. The botnet uses a peer-to-peer (P2P) model that makes it very efficient.
The vigilante malware infects the IoT device over Telnet; it exploits systems likely IoT components that are poorly configured and are protected by weak credentials. Once the vigilante malware infects a device, it allows botmaster to control it by using commands signed with a private elliptic curve digital signature algorithm (ECDSA) key.
"Wifatch's code is not obfuscated; it just uses compression and contains minified versions of the source code. It would have been easy for the author to obfuscate the Perl code but they chose not to. The threat also contains a number of debug messages that enable easier analysis. It looks like the author wasn't particularly worried about others being able to inspect the code," state Symantec in its analysis. "The threat has a module (dahua.pm) that seems to be an exploit for Dahua DVR CCTV systems. The module allows Wifatch to set the configuration of the device to automatically reboot every week. One could speculate that because Wifatch may not be able to properly defend this type of device, instead, its strategy may be to reboot it periodically, which would kill running malware and set the device back to a clean state."
Who Is Behind the Vigilante Malware?
The experts at Symantec speculate that the author of the Vigilant malware is a single expert with a deep knowledge of cryptography. He implemented security mechanisms that made its botnet resistant to cyber-attacks and take-over operations conducted by law enforcement. The experts at Symantec confirmed the use of the Tor anonymity network for hiding the control infrastructure and making hard the identification of the control servers.
Poorly Configure Routers in the Wild
Why might a white hacker be interested in developing a vigilante malware to fix flaws in compromised routers?
Unfortunately, a large number of IoT devices, including home routers, are daily compromised due to poor security settings. Default credentials and hard-coded credentials are among the most common errors exploited by any category of attackers. Cybercriminals and state-sponsored hackers usually target home routers to carry out a wide range of attacks.
Early in 2014, the Polish Computer Emergency Response Team (CERT) has documented a series of cyber-attacks observed in Poland carried out by cybercriminals hacking into home routers and changing their DNS settings. In this way the attackers were able to conduct MITM attacks on online banking connections. The techniques could be used to target also users from other countries and to exploit several vulnerabilities in home routers; with this method the attackers configured routers to use a DNS server under their control to respond with rogue IP addresses to DNS queries for the domain names they have targeted.
"The attack is possible due to several vulnerabilities in home routers that make DNS configuration susceptible to unauthorized remote modifications. In the resulting man-in-the-middle attack content of several e-banking websites was altered to include JavaScript injects that tricked users into giving up their usernames, passwords and TANs [transaction authentication numbers]. Effectively, money is stolen from users' bank accounts," reported the Polish CERT in a blog post.
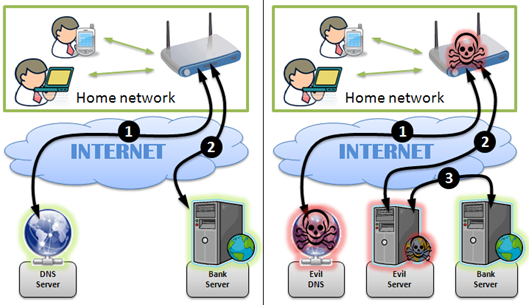
Figure 5 - Attack scenarios reported by CERT in Poland
In December 2104, over the holidays, the Lizard Squad team knocked out the networks of Sony PSN and Microsoft Xbox live service, using a tool they have designed to run DDoS attacks. The tool is dubbed Lizard Stresser and, according to the security expert Brian Krebs, its firepower is composed by thousands of hacked home Internet routers.
The Lizard Squad proposed Lizard Stresser as attack-as-a-service platform, allowing anyone to run powerful DDoS attacks.
Figure 6 - Lizard Stresser Tool
The Lizard Stresser tool is a powerful DDoS tool that draws on Internet bandwidth from hacked home Internet routers worldwide.
In May 2015, researchers at the ESET security firm released a study about a new malware known as the Moose worm that was compromising devices with weak or default credentials. The principal targets of the Moose worm were Linux-based routers, in particular the SOHO devices, including home routers, running on MIPS and ARM architectures.
Experts at ESET reported that Moose can eavesdrop, which means it can spy on communications from devices connected to the infected router.
In June 2015, security researchers at the Fujitsu Security Operations Center in Warrington (UK) spotted a strain of the Upatre malware being served from hundreds of compromised home routers. The experts noticed that the cybercriminals mainly exploited MikroTik and Ubiquiti's AirOS routers.
"We have seen literally hundreds of wireless access points, and routers connected in relation to this botnet, usually AirOS," said Bryan Campbell, lead threat intelligence analyst at Fujitsu. "The consistency in which the botnet is communicating with compromised routers in relation to both distribution and communication leads us to believe known vulnerabilities are being exploited in the firmware which allows this to occur."
Also, in this case the experts speculate that attackers have compromised so many routers by exploiting devices with default credentials (e.g., "ubnt" for both username and password on most Ubiquiti AirOS routers). The researchers noticed also that a large number of devices used to spread the Dyre malware had the Telnet port wide open.
The problems with home routers are a never-ending history: On August 2015, experts from the Carnegie-Mellon CERT discovered that a number of home routers from various vendors come with hard-coded credentials that could be used to hijack the devices.
DSL home routers from a number of vendors contain hard-coded credentials that could allow a hacker to hijack the network devices via Telnet services.
A bunch of home gateway vendors, presumably sourcing their firmware from the same place, can be hijacked using depressingly common hard-coded logins.
The CERT at the Software Engineering Institute at Carnegie Mellon University issued an advisory confirming the serious security issued in the home routers and invited organizations to write firewall rules that block Telnet or SNMP on the device as a temporary measure to mitigate the threat.
"A remote attacker may utilize these credentials to gain administrator access to the device," states the CERT advisory.
The list of vendors includes ASUS and ZTE in Asia, and Digicom, Observa Telecom, and carrier Philippine Long Distance Telephone (PLDT). All the devices analyzed by the researchers have the "XXXXairocon" as default Telnet password, where the "XXXX" is the MAC address of the home router. All the home routers except the PLDT devices have admin as default username, while the PLDT username is adminpldt.
The above cases are just a few examples of vulnerable devices that have been abused by attackers for illegal activities representing a threat for end users. It is likely that the hacker behind the vigilante malware is frustrated by such poor security and decided to act independently to improve the security of the vulnerable routers and IoT devices.
Risks of Cyber Vigilantes
First of all, let's remark that the use of malware to compromise a computer system without explicit authorization of the owner is a crime, even if the intent is to sanitize it.
This means that the author of the vigilant malware is responsible for a crime, exactly like any other crook that compromises the IoT malware for profit, although with the necessary attenuation of the case.
Despite the alleged noble intent of the author of the vigilante malware, we cannot ignore that this kind of initiative represents a threat for end users.
The cyber vigilante hacks routers and IoT devices, gaining control over them by establishing a backdoor. What happen if a third actor, a criminal ring or an intelligence agency, is able to take over the cyber vigilante? The potential impact for end users could be dramatic.
As reported by Forbes, the IoT security expert Ted Harrington, of Independent Security Evaluators, said people should be wary of such code.
"My hypothesis would be that the author of this malware may have become frustrated with how often basic security flaws persist across devices, especially in connected devices. Well- known, easily addressed, readily understood security flaws are constantly being introduced to connected devices," he told FORBES.
"However, violating systems as a path to remediation is not the right way to go. To make a physical comparison, this would be analogous to breaking into someone's home in order to leave them a note that says their alarm system isn't effective. Maybe that's helpful, but it's still a violation of your home."
A Few Suggestions to Improve Security of Home Routers
Let's close this post with a list of suggestions to improve the security of your home devices and avoid nasty surprises:
- Change the default credentials on the router by choosing a strong password.
- Never leave your access point open or unsecured. Enable wireless encryption on your router. It is suggested to enable WPA2, which is actually the strongest encryption technology available.
- Use a complex WPA2 key (click here to read more about this, as well as other tips and tricks for securing your wifi network)
- Be aware of "Wi-Fi Protected Setup" (WPS) technology implemented by many routers to facilitate device configuration. Unfortunately, this technology could open the door to hackers even if you are using a WPA connection. I suggest that you disable WPS; you can do it by accessing the router's administration page.
- Keep the firmware of your router updated.
References
http://www.symantec.com/connect/blogs/there-internet-things-vigilante-out-there
http://securityaffairs.co/wordpress/40629/hacking/iot-vigilante-malware.html
http://www.theverge.com/2015/10/1/9434521/router-virus-fights-off-malware-security
https://lootmyself.wordpress.com/2014/11/09/ifwatch-malware-part-1/
http://www.forbes.com/sites/thomasbrewster/2015/10/01/vigilante-malware-makes-you-safer/
http://securityaffairs.co/wordpress/37245/hacking/linux-moose-worm-hit-soho.html
http://securityaffairs.co/wordpress/38183/cyber-crime/hacked-routers-serve-dyre.html
http://securityaffairs.co/wordpress/32022/cyber-crime/lizard-stresser-hacking-tool.html
http://securityaffairs.co/wordpress/39631/hacking/cert-home-routers-issues.html