SambaCry: Hundreds of thousands of Linux systems exposed to a campaign that delivers cryptocurrency miner
CVE-2017-7494 - A Samba seven-year-old remote code execution vulnerability
At the end of May, security experts discovered a seven-year-old remote code execution vulnerability affecting all versions of the Samba software since 3.5.0. The flaw has been promptly fixed by the maintainers of the project. The vulnerability, tracked as CVE-2017-7494, can be exploited by an attacker to upload a shared library to a writable share and then cause the server to load and execute it.
The Samba CVE-2017-7494 vulnerability is easily exploitable; researchers highlighted that just a line of code could be used for the trigger the flaw under specific conditions:
- Make file- and printer-sharing port 445 reachable on the Internet,
- Configure shared files to have write privileges.
- Use known or guessable server paths for those files.
When the above conditions are satisfied, remote attackers can upload any code of their choosing and cause the server to execute it, possibly with unfettered root privileges, depending on the vulnerable platform.
"All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it." reads the security advisory issued by Samba.
Maintainers of the Samba published the patch at the following URL
http://www.samba.org/samba/security/
Sysadmins must fix their installs as soon as possible, and if it is not possible for any reason a workaround can be implemented by the adding the line
nt pipe support = no
to their Samba configuration file and restarting the network's SMB daemon. The change will limit clients from accessing some network computers.
"Additionally, Samba 4.6.4, 4.5.10 and 4.4.14 have been issued as security releases to correct the defect. Patches against older Samba versions are available at http://samba.org/samba/patches/. Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible."
SambaCry, a network wormable issue
According to the researchers, the Samba bug appears to be a network wormable issue; this means that an attacker can use a malicious code that can self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
Samba is an open source network application that provides the same functionality as Microsoft Server Message Block (SMB). The SMB protocol was recently targeted in the WannaCry attack by the EternalBlue exploit, by similitude the Samba issue was named SambaCry.
HD Moore, vice president of research and development at Atredis Partners, just after the public disclosure of the vulnerability posted the following images showing successful exploits against Samba on a computer running Ubuntu and NAS device made by Synology.
The Metasploit PR code for the exploitation of the CVE-2017-7494 flaw was quickly published on GitHub.
Just after disclosure of the SambaCry issue, experts at F5 executed the following query on Sshodan.io
"port:445 !os:windows"
looking for systems having tcp/445 open to the Internet. The query shows approximately one million non-Windows hosts that have tcp/445 open to the Internet, most of them in the United Arab Emirates (36%).
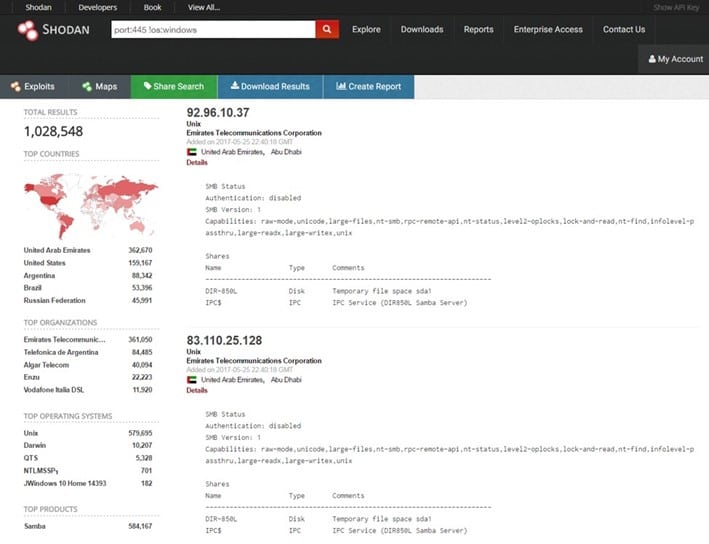
Figure 1 - Shodan search revealed devices with port 445 open to the Internet
"While many of these may be running patched versions, have SELinux protections, or otherwise don't match the necessary criteria for running the exploit, the possible attack surface for this vulnerability is large," stated the report published by F5.
The experts expressed concerns about the availability of an exploit code and predicted that malware and ransomware toolkits could trigger the SambaCry in a short future.
"There is also the possibility that this will be used in a worm-like fashion, such as we saw with WannaCry just two weeks ago," continued F5.
The SambaCry campaign
According to the researchers at Kaspersky, when the SambaCry vulnerability was discovered, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet. Also, in this case, malware researchers speculated the possibility to observe a rapid increase in the number of cyber-attacks leveraging the flaw issue, just like WannaCry attacks.
Experts at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The security researchers have spotted a malware campaign that is exploiting the SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
"On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!" reported Kaspersky.
The independent security researcher Omri Ben Bassat also observed the same campaign that he dubbed "EternalMiner." The expert confirmed threat actors started exploiting the SambaCry flaw just a week after its discovery to hijack Linux PCs and to install an upgraded version of "CPUminer," a Monero miner.

Figure 2 - Omri Ben Bassat Tweet about SambaCry campaign
According to Kaspersky, the attackers first check that an unauthorized user has permissions to write to the network drive, the attackers do it trying to write a text file consisting of 8 random symbols.
If the attempt is successful, the attackers delete the file.
Figure 3 - SambaCry attack (Writing and deleting the text file from Kaspersky honeypot)
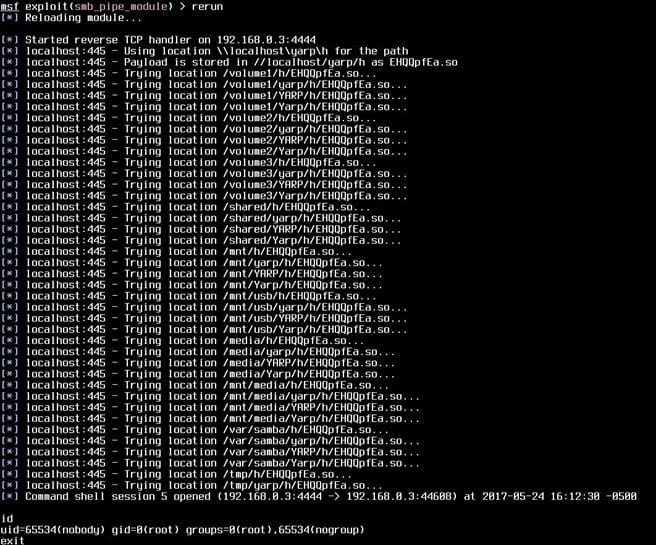
If the test is successful, the attackers upload the exploit's payload that is assembled as a Samba plugin. After successful exploitation of the SambaCry, the payload could run with super-user privileges; the attacker just needs to guess the full path to the dropped file with their payload, starting from the root directory of the drive.
"We can see such attempts in the traffic captured on our honeypot. They are just brute-forcing the most obvious paths (specified in different manuals, etc.), where files can be stored on the drive," states Kaspersky
Figure 4 - Bruteforcing the path to the payload from Kaspersky Honeypot
Once the attackers have found the path to the file, they will load and execute it in the context of the Samba server process, triggering the SambaCry vulnerability. Afterward, the file is deleted from the server to hide the traces.
Kaspersky experts observed attackers execute two different payloads on the targeted systems:
- INAebsGB.so — A simple reverse shell that allows a remote attacker to access the target system.
- cblRWuoCc.so — A backdoor that includes cryptocurrency mining utilities – CPUminer.
"The attacked machine turns into a workhorse on a large farm, mining cryptocurrency for the attackers. In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim's computer with other types of malware," Kaspersky researchers say.
According to Kaspersky, threat actors behind this campaign have already earned 98 XMR, which worth USD 5,380 today. The experts believe that crooks could earn much more with the increase in the number of compromised Linux systems.
"The mining utility is downloaded from the domain registered on April 29th, 2017. According to the log of the transactions, the attackers received their first crypto-coins on the very next day, on April 30th. During the first day, they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week, they gained about 5 XMR per day. This means that the botnet of devices working for the profit of the attackers is growing," the researchers say.
At the time I was writing, there is no information about the scale of the SambaCry campaign, anyway it is important for system administrators and Linux users to install security updates to their Samba installs to prevent such kind of attacks.
References
https://www.samba.org/samba/security/CVE-2017-7494.html
https://securelist.com/78674/sambacry-is-coming/
http://securityaffairs.co/wordpress/59930/hacking/sambacry-miner-campaign.html

Become a certified reverse engineer!











