Ransomware deletion methods and the canary in the coal mine
Introduction
Ransomware is an emergent threat. Every week, there is a new and notable outbreak of this class of data encryption malware. From Ragnar Locker to Netwalker, the threats are increasing, and they are crippling and extorting an ever-widening group of organizations.
This piece of malware is not new. Early on, ransomware encrypts everything as fast as possible, trying to do damage before any response/reactions could initiate from the victim's side. The point-of-infection is easy to detect — usually an unfixed or out-of-date device. The problem here is that the threat is only detected when the encryption process is terminated, making applications stop working and resulting in a large volume of data encrypted.
In this article, we will discuss some deletion methods used by recent ransomware threats and how canaries can help to fight and detect early ransomware activity.
Deletion methods used by ransomware
To be an effective incident, a ransomware incident begins by discovering how to delete shadow copies on the target device. In addition to the backup file recovery mechanism, the Windows operating system has another complementary way to recover data. Shadow copies have been present since Windows XP. In a nutshell, this tool allows one to create backup copies of files, making it possible to go back to the previous point or perform a system restore.
Despite this functionality of Windows operating systems, the story does not always have a happy ending. Recent pieces of ransomware look for this feature during the infection chain and eliminate all copies of the device, making it impossible to restore the system to an earlier point.
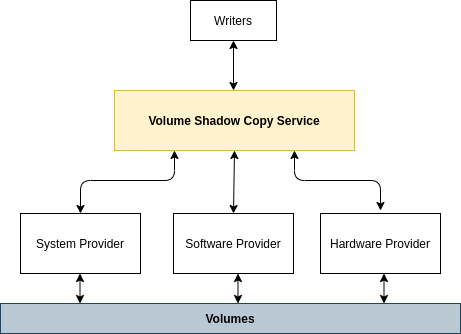
This mechanism works on the Volume Shadow Copies Service (VSS) and is supported by other important components named VSS Writers and VSS Providers. VSS Writers are responsible for supplying a steady pipeline of data to be backed up by the service, and the VSS Providers for maintaining the actual shadow copies objects available. Figure 1 below presents a high-level diagram of the shadow copies mechanism.
Figure 1: High-level diagram of Windows shadow copies mechanism
Criminals use different deletion methods, such as command-line utilities, or programmatically via system calls. There is a panoply of command-line entries and utilities found in several ransomware samples. Some examples are described below.
vssadmin delete shadows /all /quiet
This command-line is used for several malwares, such as Ryuk, WannaCry, Dharma, RobinHood, Hermes, Phobos and Locky.
wmic shadowcopy delete /nointeractive
This method is very popular and observed on GandCrab, Robinhood, Phobos, LockBit, Rapid and JCry.
More recent ransomware samples show that malware authors have a preference for invoking deletion methods directly from their code. In fact, invoking deletion methods directly from malware has the advantage of bypassing several security detection mechanisms and other solutions along this line.
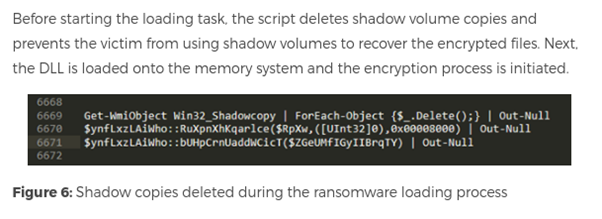
This is achieved with WMI’s Win32_ShadowCopy class and the helpful PowerShell cmdlets to access WMI objects, as observed on the Netwalker ransomware analysis article.
Get-WmiObject Win32_ShadowCopy | % { $_.Delete() }
Get-WmiObject Win32_ShadowCopy | Remove-WmiObject
Figure 2: Deletion method of Netwalker ransomware (article here).
There are other less common methods, such as invoking COM objects using WMI calls instead of command-line utilities or taking advantage of IOCTL via the Direct Device Access approach.
With this methodology in place, the damage of a ransomware incident can be more critical and severe, thus forcing the victim to pay the ransom to get and recover their files.
How to detect incidents with canary files
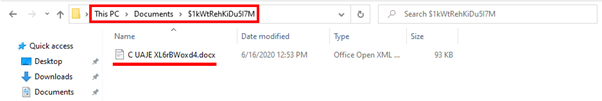
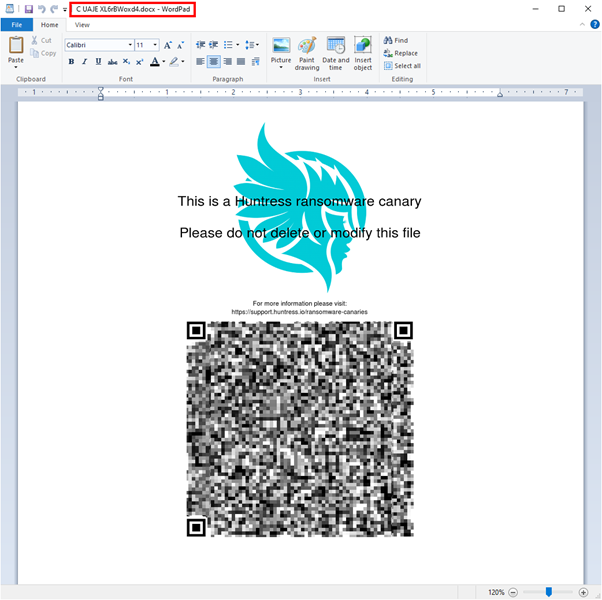
The canaries are an analogy to the canaries of the old miners. This was a test, lowering a canary into a mineshaft to discover a potential hazard: if the canary dies, it indicates a toxic amount of carbon monoxide gas in the air within the mineshaft. Canary files are files on devices or shared folders that are desirable for ransomware to infect but are not valuable to the company. These files only exist to trigger a quick indication of a ransomware infection.
Instead of monitoring the entire operating system and all the files in the operating system — a time-consuming and slow process — only specific files are monitored in the infrastructure. The same could happen, for example, with honey accounts in an Active Directory network. When an honey account is accessed, an alert is triggered on a portal managed by a SOC team that can react quickly to contain and block the incident.
Huntress, for instance, is a service in the market based on canary files and designed to detect malicious ransomware activity on a network endpoint: “When the Huntress Agent detects that a canary file has been altered, renamed, or deleted (such as when it gets encrypted by ransomware), it will alert our Threat Operations Team. Our team will review the conditions causing the alert and notify the Huntress partner of the incident details.”
Figure 3: Canary files used to prevent ransomware attacks — Huntress
Ransomware prevention
Some ransomware prevention tips are presented in this section.
- Backup: Create several versions of files on a daily basis, allowing you to create any restoring point
- Off-site backup: Maintain at least a backup off-site. This measure prevents the possibility that all information can be accessed and destroyed by criminals during an incident
- Disconnect: Disconnecting the infected device from the internet and any other devices is necessary to the safety of the network
- Updates: Operating system and endpoint security solutions (antivirus) updated
- VSSaexe: Think of disabling VSSaexe service — a tool to administer Volume Shadow Copy Service and used for restoring previous versions. With this service in place, criminals can use it to perform malicious attempts to delete shadow copies in an easy way (LOLBINS)
- Firewall: Keep the Windows firewall turned on and properly configured
- File sharing: Disable file sharing on the network if not necessary. This kind of methodology should be applied by default, thus preventing the threat of dissemination and the possibility that the infection can delete shadow copies. In addition, if a host is infected, it will stay isolated
- Remote service: Consider disabling remote services
- Software restriction policies: Define software restriction policies that keep executable files from running when they are in specific locations in the system
Conclusion
Endpoint monitoring is the key to prevent shadow copies attacks. The smallest allocation of privilege possible, the necessary services running and customized hardening (such as maintaining only a few native OS tools and blocking PowerShell execution via group policy) can be the best practices to prevent LOLBIN attacks and mitigate early ransomware incidents.
Sources
- Stomping Shadow Copies - A Second Look Into Deletion Methods, Fortinet
- Ransomware Canaries Technical Details, Huntress