Networking Basics for Reverse Engineers
Introduction
This article will define network reverse engineering, list tools used by reverse engineers for reverse engineering and then highlight the network basics required by such engineers. The article will illustrate, through the lens of an attacker, how to expose the vulnerability of a network protocol and exploit the vulnerability, and then discuss how to mitigate attack on the identified vulnerability.
This article is ideal for students and professionals with an interest in security, penetration testing and reverse engineering.

Become a certified reverse engineer!
Network reverse engineering
Put simply, network reverse engineering is the art of extracting network/application-level protocols utilized by either an application or a client server. For the purpose of explaining the network basics required for reverse engineering, this article will focus on how the Wireshark application can be used to extract protocols and reconstruct them.
Required network basics
To successfully perform reverse engineering, engineers need a basic understanding of Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) as they relate to networks, as well as how these protocols can be sniffed or eavesdropped and reconstructed. Specifically, we’ll set up a lab to analyze and extract Real-time Transport Protocol (RTP) data from a Voice over IP (VoIP) network and then reconstruct the original message using the extracted information.
TCP and UDP protocols
One key characteristic of TCP is that it’s a connection-oriented protocol. A connection-oriented protocol is one that requires prior communication to be set up between endpoints (receiving and transmitting devices) before transmission of data. It delivers data in the same manner as it was received. An example of TCP protocol is HyperText Transfer Protocol (HTTP) on port 80 and Terminal Emulation (Telnet) program on port 23.
In UDP protocols, there is no need for prior communication to be set up before data transmission begins. Even though this is faster when compared to TCP, there is no guarantee that packets sent would reach their destination. One popular area where UDP can be used is the deployment of Voice over IP (VoIP) networks.
Examples of UDP protocols are Session Initiation Protocol (SIP), which listens on port 5060, and Real-time Transport Protocol (RTP), which listens on the port range 10000–20000. In a practical voice conversation, SIP is responsible for establishing the session which includes IP address and port information. RTP exchanges the main voice conversation between sender and receiver.
Wireshark — Sniffing network protocols
Wireshark is a network packet analyzer. Even though there are several protocol analysis tools, it is by far the most popular and leading protocol analyzing tool.
In this lab, we will deploy Wireshark to sniff packets from an ongoing voice conversation between two parties and then reconstruct the conversation using captured packets.
Creation and setting up of user accounts
For this lab, we shall setup Trixbox as a VoIP server in VirtualBox. We shall also require at least two softphones — Express Talk and Mizu Phone. Two user accounts with details are created, with details below:
- Account Name: myvoip
- Username: 7070
- Password: 123456
- Account Name: myvoip2
- Username: 8080
- Password: 123456
Figure 1: Proxy server IP being verified from Trixbox terminal
Figure 2: Logging into Trixbox server
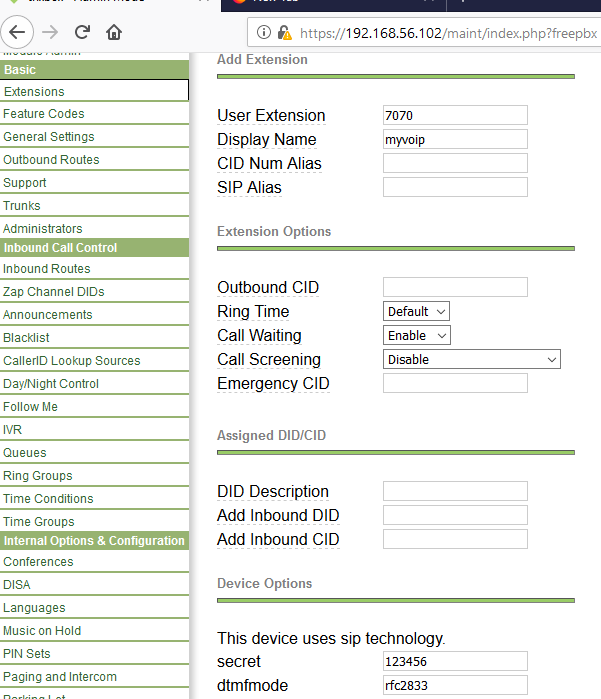
Figure 3: Creating user extension 7070 on Trixbox server
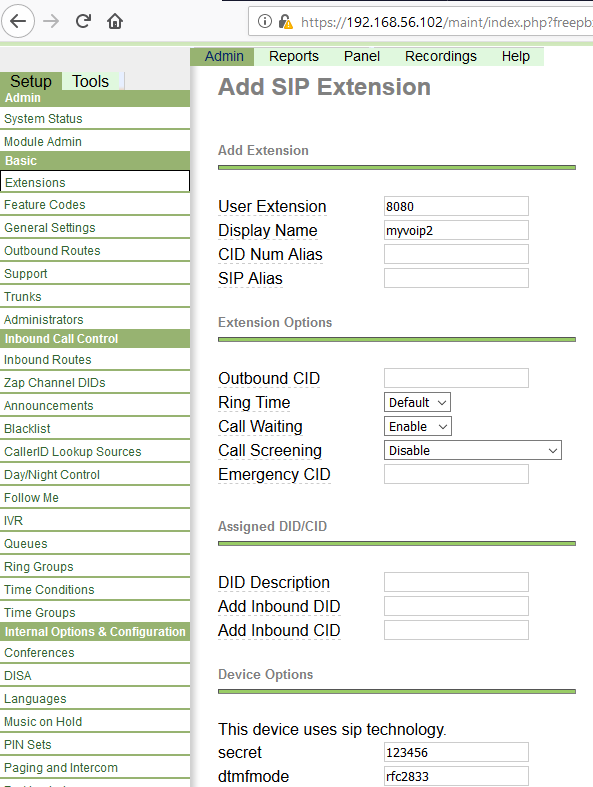
Figure 4: Creating user extension 8080 on Trixbox server
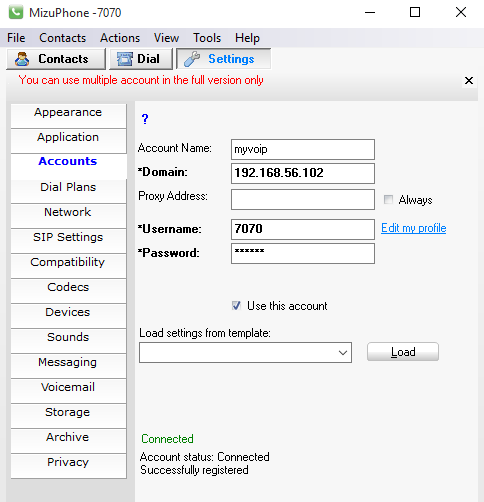
Figure 5: Configuring user extension 7070 on Mizu SoftPhone
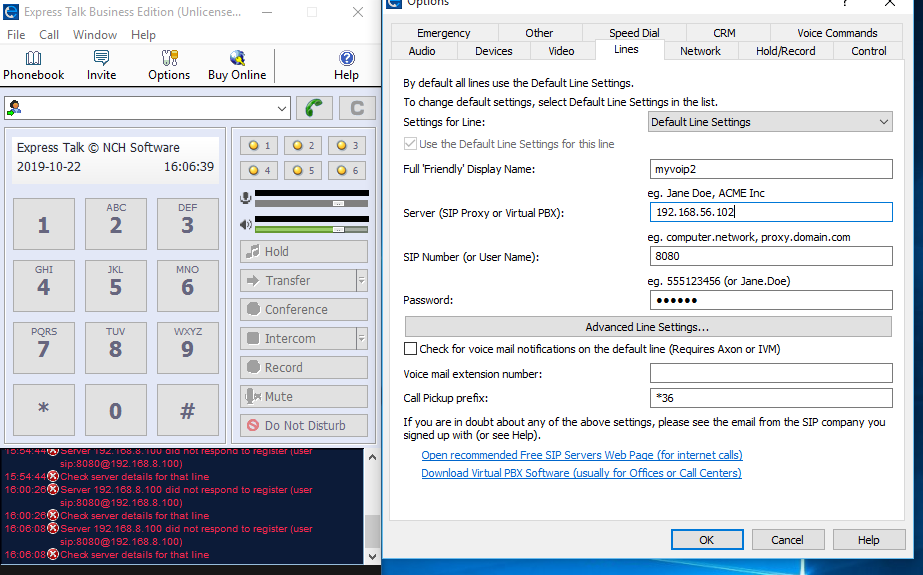
Figure 6: Configuring user extension 8080 on Express Talk Softphone
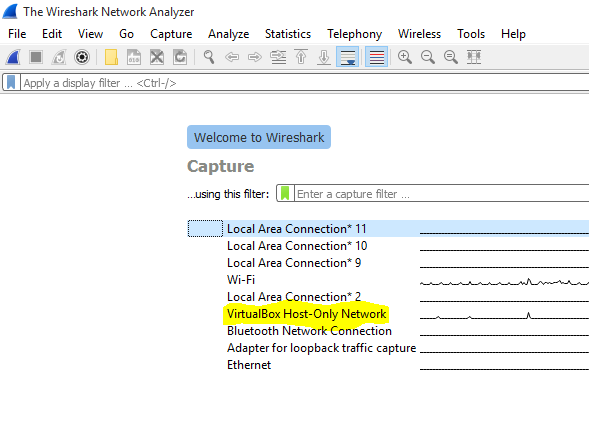
Figure 7: Setting up Wireshark to capture from interface with IP set as proxy server (192.168.56.102)
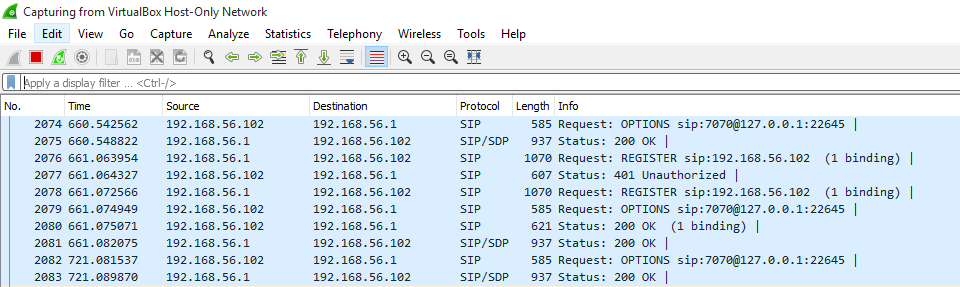
Figure 8: Wireshark application showing SIP registrations from softphones
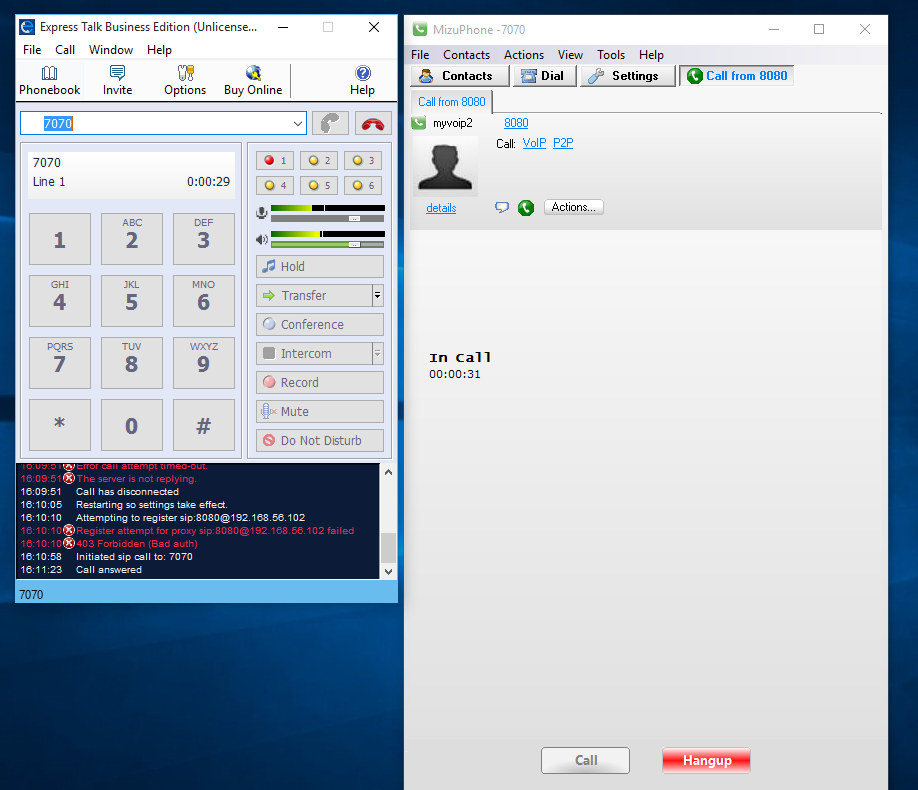
Figure 9: Extension 8080 initiates a call to extension 7070
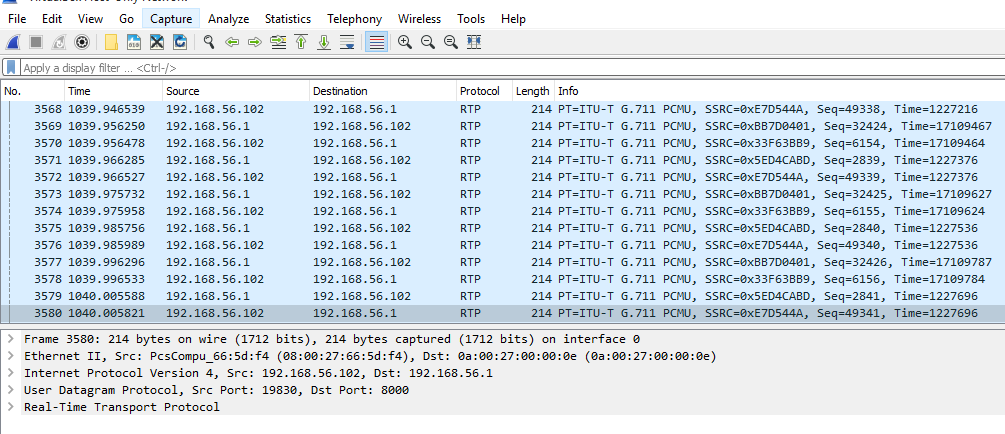
Figure 10: Wireshark application capturing RTP packets from ongoing voice conversation
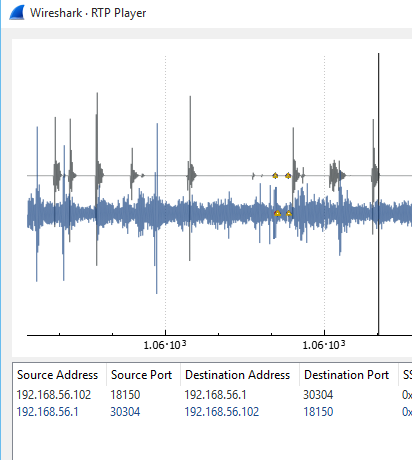
Figure 11. Decoding RTP packets from conversation between extensions 7070 and 8080
Following from figures 1 through to 10:
- User extensions 7070 and 8080 were created on the Trixbox server with IP 192.168.56.102. The extensions were then set up on the SIP softphones Mizu and Express Talk
- Wireshark was launched to monitor SIP packets from the softphones just after they’ve been configured
- Wireshark was set up to capture packets from an ongoing conversation between extension 7070 and 8080
In figure 11, Wireshark is used to decode or recreate the exact conversation between extension 7070 and 8080 from the captured RTP packets. It renders this into a playable audio format.
Conclusion
This article has defined network reverse engineering and explained some basics required by engineers in the field of reverse engineering. We also walked through setting up a VoIP lab where an ongoing audio conversation is captured in the form of packets and then recreated into the original audio conversation.
To prevent attackers or third parties from decrypting or decoding eavesdropped VoIP conversations, Secure Real-time Transport Protocol (or SRTP, an extension of RTP with enhanced security features) should be deployed. When done this way, captured voice conversations may be difficult to decrypt.
Sources
- Wireshark User’s Guide, Wireshark









