Mumblehard Malware
Introduction
In this article, we will learn about a malware known as Mumblehard which is known for targeting Linux and BSD OS. This malware opens a backdoor that gives the full control of the infected machine to cybercriminals.
Mumblehard malware -Components
-
Perl Backdoor
Perl backdoor will request for commands from its Command &Control Server and contains a URL to a file to be downloaded and executed. This backdoor is installed in crontab and has an execution time of every 15 minutes. At each run, every C&C server in the list is queried for a command. This backdoor supports only one command

Become a certified reverse engineer!
Get live, hands-on malware analysis training from anywhere, and become a Certified Reverse Engineering Analyst.0x10: Download from URL and execute
Another important thing to note about this malware is that it disguises itself as httpd by assigning as $0
$0="httpd";
This backdoor makes HTTP Get request to each C&C server in the list and the command is hidden in the PHPSESSID in the response header. This PHPSESSID is hex-coded by the server and in this, it will look like legitimate while doing packer analysis.
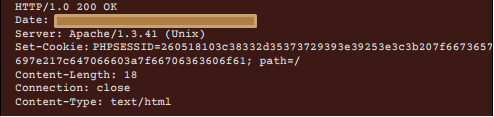
Upon analysis, this appears to be encrypted with same encryption algorithm that is used to obfuscate the whole program earlier. Upon decryption, following are the fields that are present in the PHPSESSIF field:
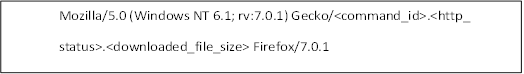
This backdoor uses a hard code user agent and puts the information inside the user agent strings. Below is the format of the user agent being used by Mozilla client:
Below is an example of the backdoor communicating with the C&C server of a successful download and execute command:

-
Spammer Daemon
This spammer daemon will send spam and is written in Perl and packed inside the ELF binary. It has two ways of sending spams which are stated below:
-
Communication with C&C servers
C&C servers runs on port 25 but Mumblehard expects a POST request with binary data as its content. Upon analysis, following are the content of the POST request in binary
- Magic
- Version
- Command
- Pid
- Extra Data Size
- Extra Data
In this, the extra data contain data about how many email were transmitted .The data contains a job ID, none of successful/unsuccessful emails being sent.
The response from the server is HTTP 200 is ok and contains various important fields like job ID, recipients list, message, size of the message etc.
-
Proxy Feature
Another way of sending spam for this is to use the proxy component. It works simply by listening for the inbound connections on TCP port and sends notifications to the C&C server that it is listening on that port. Spammer uses a "Create Connection command" to establish connection with C&C server. It is based on the SOCKS4 protocol and thus uses tunnel for arbitrary traffic through he infected host. Create Connection command fields are as below
- Command
- Port
- IP
-
Indicators of Compromise
Following are the IOCS:
HTTP requests with the following User-Agent pattern

Become a certified reverse engineer!
• Mozilla/5.0 (Windows NT 6.1; rv:7.0.1) Gecko/<1 or more digits>.<1 or more digits>.<1 or more digits> Firefox/7.0.1








