Malware in dark web
The Dark Web plays a crucial role in the criminal underground especially for the communities of malware developers; the principal darknets are privileged environments for malware authors and botmasters.
The numerous black marketplaces are excellent points of aggregation for malware developers and crooks that intend to pay for malicious code and command and control infrastructures.

Become a certified reverse engineer!
The use of dark nets represents a design choice for malware developers that use them to hide the command and control servers.
Just three years ago I made a rapid analysis to determine the number of malicious codes that were exploiting both the Tor network and the I2P dark net to hide their command and control servers. The results were surprising, the number of malware that were using darknet was limited, with a prevalence of Tor-based malicious code.

Figure 1 - Malware using C&C in the Dark Web (Security Affairs 2015)
In just three years the situation has completely changed, almost any ransomware today relies on hidden services in the Tor network for the payment infrastructure. Many types of malware are directly controlled by servers hosted on both Tor and I2P, and it is quite easy to find Ransom-as-a-Service (RaaS) in the darknets.
Below just a few examples of malware that were discovered in the last 12 months leveraging darknets for their operations:
- 2017 - MACSPY – Remote Access Trojan as a service on Dark web
- 2017 – MacRansom is the first Mac ransomware offered as a RaaS Service.
- 2017 – Karmen Ransomware RaaS
- 2017 –Ransomware-as-a-Service dubbed Shifr RaaS that allows creating ransomware compiling 3 form fields.

Figure 2 - Shifr RaaS Control Panel
Hiding command and control infrastructure in the dark web
Malware authors use to hide C&C servers in the darknet to make botnet resilient against operations run by law enforcement and security firms. The use of anonymizing networks is quite common, but it has pro and cons, let's see in detail which are advantages and problems.
Tor-Botnet
During the Defcon Conference in 2010, the security engineer Dennis Brown made an interesting speech on Tor-based botnets; he explained which are pro and cons for hiding C&C servers in the Tor Network. The principal advantages of Tor-based botnets are:
- Availability of Authenticated Hidden Services.
- Availability Private Tor Networks
- Possibility of Exit Node Flooding
Security researchers use traffic analysis to detect botnet activities and to localize the C&C servers; typically they do this by using Intrusion Detection Systems and network analyzers. Once uncovered a botnet, the security researchers and law enforcement have different options to eradicate it:
- Obscuration of the IP addresses assigned to the C&C server
- Cleaning of C&C servers and of the infected hosts
- Domain name revoke
- Hosting provider de-peered
The Botnet traffic is routed to the C&C server through the Tor network that encrypts it making hard its analysis.
Brown proposed the following two botnet models that exploit the Tor network:
- "Tor2Web proxy-based model."
- "Proxy-aware Malware over Tor network."
"Tor2Web proxy-based model."
The routing mechanism relies on the Tor2Web proxy to redirect. onion web traffic. The bot connects to the hidden service passing through the Tor2Web proxy pointing to an onion address that identifies the C&C server that remains hidden. The main problem related to this approach is that it is easy to filter Tor2Web traffic, the model also suffers a significant latency due to the Tor network that could make unresponsive the botnet.
"Proxy-aware Malware over Tor network."
Bots implementing this approach run the Tor client on the infected hosts. Bots need to support the SOCKS5 protocol to reach. onion addresses through the Tor network once loaded a Tor client on the victims' systems.
This second approach is more secure because traffic is not routed through a proxy and it is entirely within the Tor network due to the direct connection between bots and C&C servers.
This approach is more complicated from a Bot perspective due to the complexity of managing SOCKS5 interface and in botnet synchronization. This kind of botnet could be easily detected by the presence of the Tor traffic on a network.
Strengths and weaknesses of Tor Botnets
The main points of strengths for implementing a botnet based on Tor are:
- Botnet traffic masquerading as legitimate Tor traffic
- Encryption prevents most Intrusion Detection Systems from finding botnet traffic
- The command and control servers (C&C) are hard to localize
- Hidden Services provide a Tor-specific. onion pseudo top-level domain, which is not exposed to possible sinkholing.
- The operator can easily move around the C&C servers just by re-using the generated private key for the Hidden Service.
The main weaknesses are:
- Complexity botnet management
- Risk of botnet fragmentation
- Latency in the communication
The Mevade Botnet - A case study
The Mevade malware (a.k.a Sefnit, LazyAlienBiker) is one of the biggest Tor-based botnets in the history, in September 2013 it caused a spike in the number Tor users that reached 5 million.

Figure 3 - Tor Metrics Mevade Spike Tor Users
Authors of the Mevade bot were Russians; they used the botnet to install adware and toolbars on infected systems, mine Bitcoin and steal sensitive information from the victims' machines. Experts at TrendMicro revealed that the Mavade bot also implemented backdoor features and the ability to communicate over SSH to remote hosts.
Malware in the dark web
In the Tor network it is easy to find hidden services proposing malware and related services to the visitors, below a short list of onion sites that I have visited searching for malware in the last hours:
Let's start with the Berlusconi Market which has an impressive listing of malware, it includes botnets, exploits, exploit kits and security software.
Surfing the market, we can find any kind of malware, from mobile RAT like DroidJack to banking trojan like GozNym. While the android RaT goes for a few dollars, the full version of GozNym botnet that includes the installation on user's bulletproof servers and the code goes for 1500 Euro.
Sellers also offer services for set up a botnet or to power a DDoS attack that can bypass protection services (i.e., Incapsula, CloudFlare, Sucuri).
Several vendors offer very cheap Keyloggers (price between 1 and 5 Euro) and DDoS scripts that also works against. onion sites.
The offer also includes various software to hack mobile devices, for example, the super Bluetooth Hack goes for less than 3 Euros, it allows you to "hack" into another phone so that you can control and access information such as call history, text messages, ringtones, and more.
Let's continue our tour visiting The Dream Market marketplace; it is organized in several categories, some of them include goods that could be interesting for us.
Searching for the term Trojan, it is possible to find many sellers offering malicious code, from banking Trojan to ransomware.
Android RAT and info stealer are very cheap; it is possible to buy them for less than 5 dollars. Digging the black marketplace, we can find other malware, like the SMSBot Android bot and BetaBot, both available for less than ten dollars.
Of course, it is also possible to pay for ransomware, the quality of the code offered on the market is not so good, but this is normal for generic marketplaces.

Figure 4 - The Dream Market - Searching for Ransomware
Another black marketplace that has an interesting malware offer is the "Wall ST Market," it includes specific sections where to find malicious codes, botnets, exploit kits.
Wannabe crooks can buy the ATM Cutlet Maker malware for around $3500; it was first spotted in October 2017 by researchers at Kaspersky Lab that noticed a forum post advertising the malicious code.
A silent Monero Miner Builder could be paid 300 Euro while a Jigsaw Ransomware is available for 120 Euro. Android spyware is very cheap; the DroidJack Android RAT is available for just one dollar.
Figure 5 - Wall ST Market black marketplace
On the Tor Network, it is also possible to find entire repositories of malware, one of them is DarKoder. Such kind of repositories are well organized and includes almost any kind of malware and component for malware development. Of course, the offer is for more skilled professionals that once obtained the malicious code can customize the installation and deliver them.

Figure 6 - Darkoder Repository
The repository is organized into several categories that include:
- Botnets
- Crypters
- DOSer
- Keyloggers
- Miner
- Old school malware
- Others type of malware
- RAT
- SE malware
Exploring the RAT folder, we can find popular malware such as DarkCometRAT5, the ProtonRAT, and PurpleRat.
The botnet folder includes several items, such as Banking botnets, DDOS botnets, and Logger Botnets.
Searching for Ransomware-As-A-Service, I have found RaaSberry, a set of customized ransomware packages that are ready to distribute. The packages are pre-compiled with a Bitcoin address provided by the users. Like any other RaaS, the RaaSberry also provide a Command and Control (C&C) Center to manage your victims and view individual AES keys.
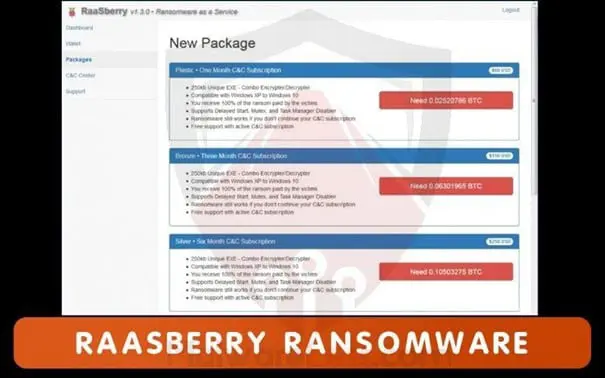
Figure 7 - RaaSberry Ransomware-as-aService
Conclusion
Security experts have highlighted the deep differences between the various black markets, crooks in each geographic area specialize their offer. Brazilian crime communities, for example, are more focused on banking Trojan meanwhile Chinese hacking communities are focused on mobile malware.
The prices for malware are very different for specific geographic areas.
Looking at the price list collected by security firms, we can see that specific products in some markets tend to be more expensive than in other regions.
This is the case of Keyloggers in the Middle Eastern and North African forums that are offered on average goes for $19, much more expensive than elsewhere. In the North American underground, for example, it is possible to buy them for between $1 and $4.
Figure 8 - The Middle Eastern and North African Underground (Trend Micro Report)
The above differences demonstrate the intense activity of malware communities in different regions; their evolutions are often related to the specific habits of potential victims in the area instead of a global trend.
Sources
- Maersk Notpetya Losses
- FedEx 300 million notpetya attack
- Largest bitcoin exchange
- North African cybercrime underground
- Bithumb hacked
- Ethereium currency hack
- Coindash cyber heist
- Veritaseum cyber heist ethereum
- G7 declaration responsible states behavior cyberspace
- IoT devices DDoS attacks
- The middle eastern and north African underground where culture and cybercrime meet









