MalLocker Android ransomware: What it is, how it works and how to prevent it | Malware spotlight
Introduction
Malware is persistent presence in our life. In the past few months, several pieces of different malware families were identified as affecting mobile devices. This is, in fact, a new landscape from the viewpoint of criminals. Many of those criminals are directing their effort at the mobile surface, a daily object that stores sensitive user information.
Within this context, a new sophisticated Android ransomware with novel techniques was identified by Microsoft: MalLocker. This is one of the latest pieces of ransomware observed in the wild and it is attacking Android users’ devices around the globe.

Become a certified reverse engineer!
How MalLocker is distributed in the wild
As observed in other kinds of mobile malware families, MalLocker is being shared on random and compromised websites by crooks. It is also circulating on several online forums, using social engineering schemas to disseminate the threat — including masquerading as popular apps, cracked games and video players.
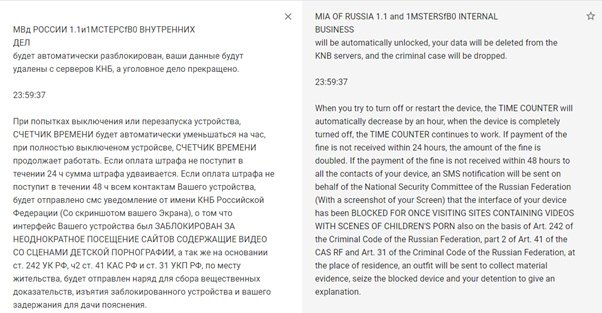
MalLocker doesn’t block access to files and encrypt them after installing on the victim’s device. Instead, it shows an overlay screen with the ransom note, using never-before-seen techniques that make use of certain Android features to freeze the device. After that, a ransom note that contains the instructions to pay the ransom is presented and automatically resized and cropped to fit it without distortion (Figure 1).
Figure 1: MalLocker overlay window with the ransom note and countdown
MalLocker obfuscation layer
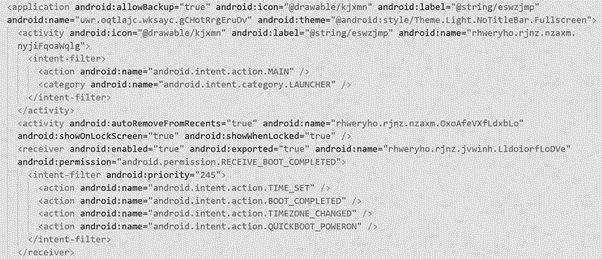
In order to bypass security software, the malware is obfuscated. A clear signal of this activity is observed in the manifest file, due to the absence of code that defines the malware classes.
Figure 2: Suspicious manifest file with the absence of code
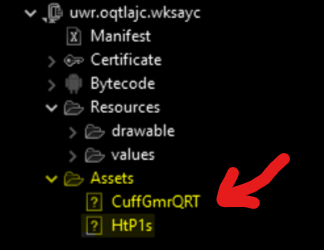
In detail, the class.dex file has two classes inside that are not declared in the manifest file, confirming the suspicious activity. Like other malwares, it stores the malicious binary files encrypted and obfuscated inside the Assets folder.
Figure 3: Encrypted executable code in the Assets folder
After the first execution, the class.dex file is decrypted and the payload is loaded into the memory, starting the infection chain.
Figure 4: Asset file before and after decryption
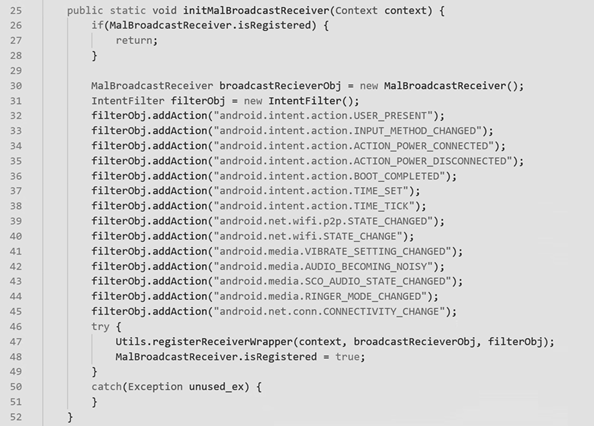
According to Microsoft, “the malware saves this configuration to the shared preferences of the app data, and then it sets up all the Broadcast Receivers. This action registers code components to get notified when certain system events happen. This is done in the function initComponents”.
Figure 5: Starting BroadcastReceiver against system events
Digging into the MalLocker details
Instead of encrypting the system files, the malware uses a dual mechanism to show its ransom note and block the screen.
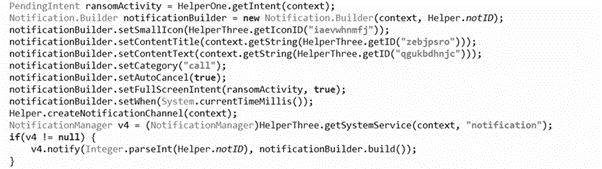
MalLocker ransomware takes advantage of the call notification function available on Android devices. The malware abuses the call notification that activates for incoming calls to show details about the caller and uses it to show an overlay window that covers the entire area of the screen with the ransom note message.
Figure 6: The notification with full intent and set as “call’ category
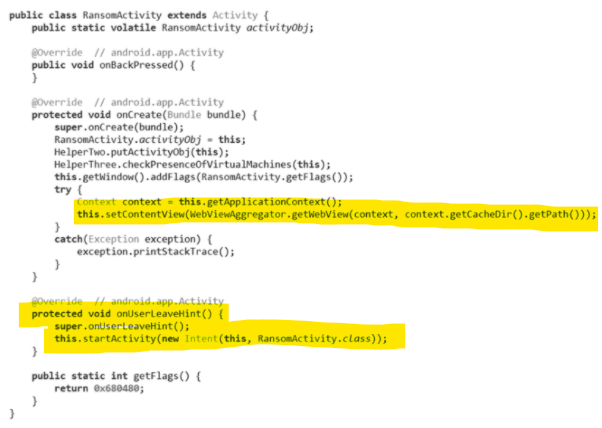
On the other hand, the ransomware uses the onUserLeaveHint() functions (highlighted below) every time the user switches an application into the background and takes advantage of this technique to launch and draw a new overlay window, automatically resized and cropped and presenting the ransom note (Figure 7).
Figure 7: The malware overriding on UserLeaveHint call
With these new techniques and tactics in place, criminals can take advantage of these new improvements to target a new surface in relation to conventional malware.

Become a certified reverse engineer!
Final thoughts
This is a shift in the mobile malware landscape, where fresh techniques explored in the wild by criminals were observed. MalLocker is a new ransomware variant and built to evade protections, registering a low detection rate against security solutions.
Notice that MalLocker’s machine-learning module indicates continuous evolution of this Android ransomware family, researchers said.
“This ransomware is the latest variant of a malware family that has undergone several stages of evolution,” researchers said. “We expect it to churn out new variants with even more sophisticated techniques. In fact, recent variants contain code forked from an open-source machine-learning module used by developers to automatically resize and crop images based on screen size, a valuable function given the variety of Android devices.”
“This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow,” Microsoft added.
Within this context, the precautions to be taken to avoid potential infections are those already known, including:
- Avoid the download of apps from unofficial Play Stores
- Before installing a new application, read the requested permission carefully
- Beware of fake apps; and
- Always update the Android operating system.
Sources
Sophisticated new Android malware marks the latest evolution of mobile ransomware, Microsoft