Lazarus’s VHD ransomware: What it is, how it works and how to prevent it | Malware spotlight
Introduction
Data encryption malware is one of the most popular malware families in recent years and targets mass volumes of users and companies around the world. In this article, we will take a deep dive into a new VHD ransomware distributed in the wild by the Lazarus group — the criminals behind the WannaCry incident in 2017.
The VHD ransomware is one of the most dangerous threats today. This is because it tries to change system settings, disable some programs and functions of the target operating systems and demands payment in cryptocurrency via a ransom note dropped during the ransomware execution. The Lazarus group have been using this ransomware, which uses methods typical of APT attacks but specialized in financial cybercrime.
The activity of the Lazarus Group surged in 2014 and 2015, where custom-tailored malware was used in its cyberattacks. The group has been linked to several major cyberattacks, including the 2014 Sony Pictures hack, several SWIFT banking attacks since 2016 and the WannaCry ransomware infection in May 2017.
Lazarus’s VHD ransomware
Researchers from Kaspersky detailed a new VHD ransomware used by the group between March and May 2020. The analyzed samples have been deployed over the network of the target enterprises, brute-forcing the SMB service on every discovered machine and using the MATA malware framework documented by Kaspersky here and also used by the Lazarus group.
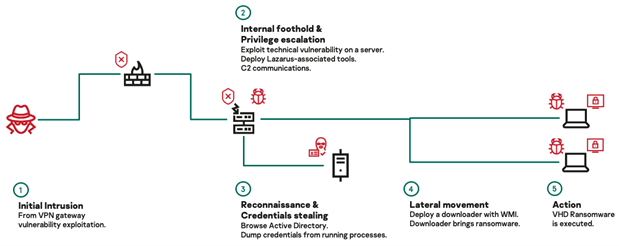
Initially, criminals gain access to the target infrastructures via widespread botnet infections such as Emotet and Trickbot families or by exploiting vulnerable VPN gateways. When criminals have a good understanding of the target’s finances and IT processes and network, they escalated their privileges on the compromised systems and installed a backdoor that is part of the MATA malware framework. The criminals leverage the backdoor to control the Active Directory server and use it to deliver VHD ransomware to all systems in the target network within 10 hours using the help of a Python-based loader.
After finishing the infection chain with the ransomware deploy, criminals enter in a new phase: the negotiation.
Figure 1: High-level diagram of the Hakuna MATA and VHD ransomware.
Diving into the details
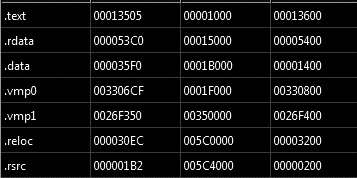
VHD is a standard ransomware tool that spreads through the drives connected to the target device, encrypts all the files and deletes all System Volume Information folders that prevent the impacted system could be restored. The ransomware binary is protected with VMProtect packer in order to prevent its analysis. The binary sections vmp0, vmp1 are the first signal of this packer.
Figure 2: Binary sections (vmp0 and vmp1 — VMProtect packer).
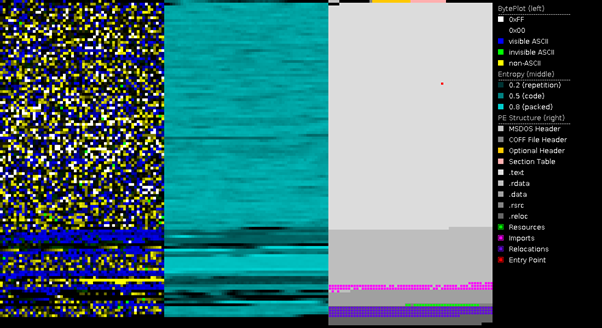
As observed in the PorEx diagram below, some parts of the binary were obfuscated, such as the malware config, ransom note details and so on.
Figure 3: PortEx diagram — VHD ransomware.
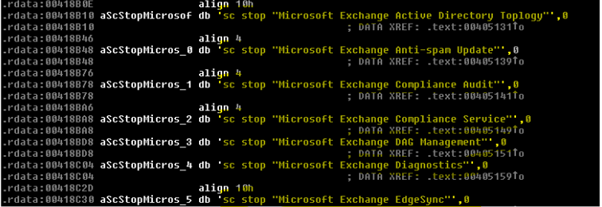
One interesting detail this threat is related to some services that are suspended to preserve important files from modification such as Microsoft Exchange and SQL server. Next, the services suspended during the ransomware operation are presented.
Figure 4: Services stoped during the ransomware execution.
Here’s a complete list of stoped services during VHD ransomware execution:
sc stop "Microsoft Exchange Active Directory Toplogy"
sc stop "Microsoft Exchange Compliance Audit"
sc stop "Microsoft Exchange Compliance Service"
sc stop "Microsoft Exchange DAG Management"
sc stop "Microsoft Exchange Diagnostics"
sc stop "Microsoft Exchange EdgeSync"
sc stop "Microsoft Exchange Frontend Transport"
sc stop "Microsoft Exchange Health Manager"
sc stop "Microsoft Exchange IMAP4"
sc stop "Microsoft Exchange Health Manager Recovery"
sc stop "Microsoft Exchange Information Store"
sc stop "Microsoft Exchange IMAP4 Backend"
sc stop "Microsoft Exchange Mailbox Assistants"
sc stop "Microsoft Exchange Mailbox Transport Delivery"
sc stop "Microsoft Exchange POP3"
sc stop "Microsoft Exchange POP3 Backend"
sc stop "SQL Server Agent (TESTINSTANCE)"
sc stop "SQL Server (TESTINSTANCE)"Some important Windows calls are also executed during the malware operation. Some of them are described in a brief way below to a better understanding of how the malware works.
Calls loaded from kernel32.dll
Call loaded from shell32.dll
Call loaded from user32.dll
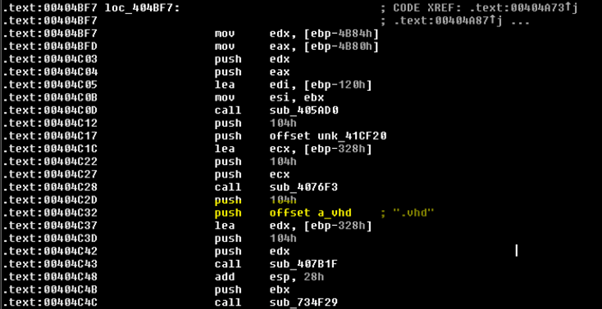
Every time a file is encrypted, it is renamed. The extension “.vhd” is appended to the end of the file name.
Figure 5: Ransomware extension (.vhd) is appended to the file name whenever a file is encrypted.
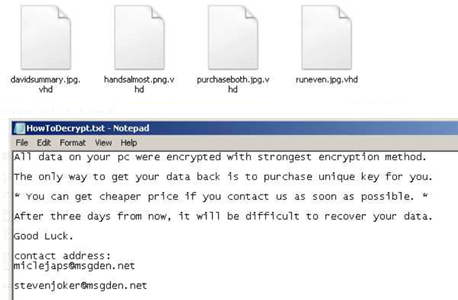
The ransom note is also dropped into the desktop folder “HowToDecrypt.txt” with the instructions for paying the ransom and recovering the damaged files.
Figure 6: Damage files and ransom note dropped into the desktop folder.
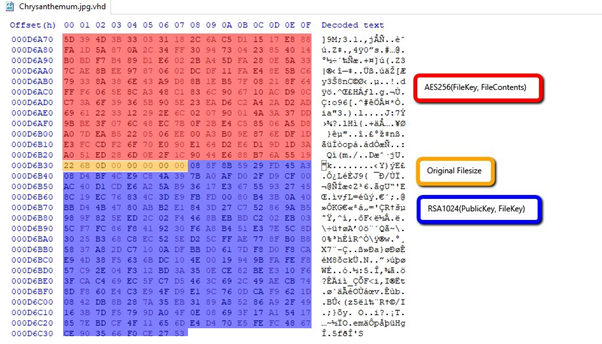
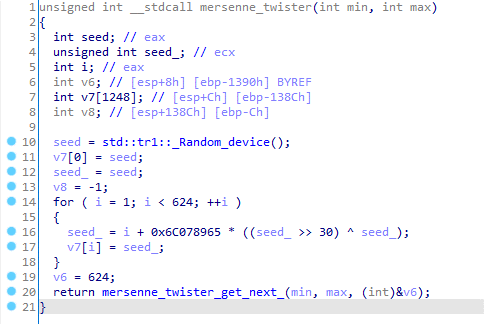
The ransomware is written in C++ and the files are encrypted with a combination of AES-256 in ECB mode and RSA-2048. The ransomware uses Mersenne Twister as a source of randomness, but unfortunately for the victims, the RNG is reseeded every time new data is consumed. The combination of ECB and AES is not semantically secure, which means the patterns of the original clear data are preserved upon encryption.
VHD implements a mechanism to resume operations if the encryption process is interrupted. For instance, for files larger than 16MB, the ransomware stores the current cryptographic materials on the hard drive, in cleartext. This information is not deleted securely afterwards, which implies there may be a chance to recover some of the damaged files.
Figure 7: Details about cryptographic algorithms and Mersenne Twister block with the RNG seed.
A strategy often used by malware developers is the usage of mutex entries to prevent further infections when a target device has already been infected. VHD ransomware creates during its execution the mutex “AEEAEE SET”, as observed below.
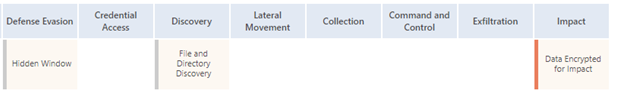
The malware’s plan is not very complex, as presented by the MITRE ATT&CK matrix below. Ony some functions to hide its presence and calls to scan the target device and drives and also to access the system files are used by the malicious binary.
MITRE ATT&CK™ Matrix

Become a certified reverse engineer!
Preventing against ransomware incidents
There is not a perfect formula to fight ransomware incidents, but some measures can be enumerated to prevent some situations:
- Provide social engineering training and explain to employees how following simple rules helps to avoid ransomware incidents.
- Ensure that software, applications and systems are up to date.
- Use endpoint protection solutions to prevent malicious infections.
- Use vulnerability management and monitoring systems to identify potential unpatched flaws and to detect incidents in real time.
- Use canary files to detect ransomware early.
- Perform cybersecurity audits and mitigate any weaknesses discovered in order to prevent attacks in the wild, both from the external and internal perspective.
Sources
Lazarus on the hunt for big game, Kaspersky