How to use Radare2 for reverse engineering
This article defines reverse-engineering as it is used in the analysis of software. We will explain in detail how to use radare2 for reverse engineering.
It exposes techniques that can benefit self-starters, security analysts, engineers, software auditors and hobbyists who want to improve their understanding of low-level aspects of a piece of software. It offers a system approach to understanding reverse-engineering and real-world examples.

Become a certified reverse engineer!
What is reverse-engineering?
Reverse-engineering is the creative process of analyzing software and understanding it without having access to the source code. It is the process by which software is deconstructed in a way that reveals its innermost details such as its structure, function and operation.
Reverse-engineering is one of the core skills required in the software security industry. Most attacks, which are usually launched in the form of malicious software, should be reversed and analyzed. After a malware attack is launched within a system, the key requirements are to clean the system and nodes and protect them from being compromised.
It is the work of a software analyst to determine how the malicious software installed itself within the system and develop steps for uninstalling the software. Reverse-engineering is used in malware analysis to understand what that piece of code is doing and to create a detection process to prevent it from re-infecting the system again.
What is radare2?
Radare2 is an open-source framework that can perform disassembly, debugging, analysis, comparing data and manipulation of binary files. This framework works on Windows, Linux and many other platforms and architectures. The Windows installer can be downloaded from GitHub.
Radare2 utilities
Radare2 comes with a few other important tools. These tools are command-line utilities which can be used together or independently. This article will discuss four key utilities that are shipped with radare2.
rax2
rax2 comes in handy when there is a need to make base conversions between hexadecimal representations, floating point values, hex-pair strings to ASCII, binary, octal, integer and so on.
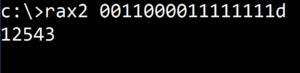
Figure 1. Using rax2 to convert binary 0011000011111111d to integer 12543
rasm2
rasm2 is an assembler and disassembler for several architectures, including Intel x86.
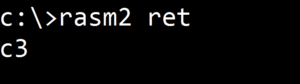
Figure 2. Converting the Assembly Language Code for return (ret) into machine code
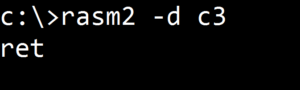
Figure 3. rasm2 converts machine code c3 into Assembly language
rabin2
rabin2 provides key information about executable binaries. It is mostly known as a binary program info extractor. As shown in Figure 4, we see that the executable binary under observation will run on x86 architecture and has a bin type in the Portable Executable (PE) format. We also see that this binary was coded using C++.
There is additional information on whether the least-significant (little-endian) or most significant value (big-endian) in the sequence is stored first at the lower storage address.
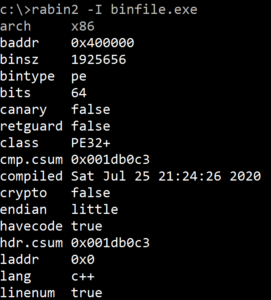
Figure 4. rabin2 utility extracts information from an executable binary
radare2
This is the main library and framework tool, which uses the core of the hexadecimal editor and debugger. This is the utility that can be used for reversing software.
How to reverse-engineer an executable binary
This section will describe how to reverse an executable binary. When this standard program requests a user to input the secret password for logging on to a system, it compares the input password with a static string then prints a statement each for the correct code and wrong codes. The aim here is to illustrate the functionality of radare2.
To begin with reversing, we launch radare2 and load a binary file named binfile.exe.
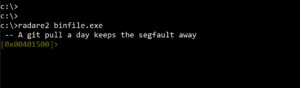
Figure 6. Loading executable binary into radare
We can analyze the binary using the aa command. The aa command analyzes all flags starting with symbols, functions and the program’s starting point.
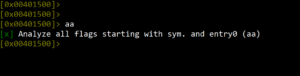
Figure 7. How to initiate analysis of binary loaded into radare2
During binary analysis, we can jump to any section within the binary code. The “s” command in radare2 is used to “search” for data within the code. As shown in Figure 8, it is used to search for the key “password” within the code. Note that the address changes from the entry point 0x00401500 to the address where the key is found: 0x00488019. Running the command s entry0 at any time will return us to the starting address 0x00401500 shown in Figure 10.
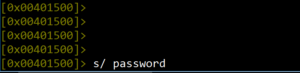
Figure 8. Seeking keywords within a binary code
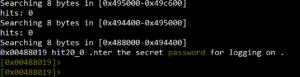
Figure 9. Keyword found at address 0x140008b14
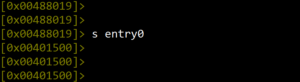
Figure 10. Returning to the entry point
To continue code analysis, we can switch to visual mode with the code “V”. This presents the hex view of the visual mode shown in Figure 12.

Figure 11. Switching to visual mode for code analysis
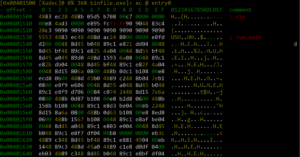
Figure 12. Hex editor in radare2
Since the results from the hex editor is not actually what we need to see, we can change the view using the command p and the down arrow key until we get to the address range 0x00401563 to 0x004015bb. In this address range, we see key information, password radare2 which is never available to the User during execution of the program.
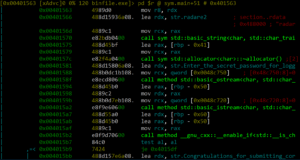
Figure 13. Viewing hidden codes in binary files using radare2
Instead of loading an executable directly into radare2, we could also run it with the switch -d which loads the binary file in debug mode.
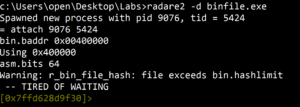
Figure 14. Launching radare2 with the -d option
While in debug mode, the executable file can be launched with the command dc.
![]()
Figure 15. Launching binary file whilst in debug mode
Figure 16. Checking register state in debug mode
Conclusion
This article has defined radare2 as an example of a tool which can be used to deconstruct a software and reveal its innermost details even if the source code is not available. We also provided practical steps on how to deconstruct an executable.

Become a certified reverse engineer!
Sources
- Bruce Dang, Alexandre Gazet, Elias Bachaalany, Sébastien Josse, “Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation,” Wiley, 2014








