Drovorub malware: What it is, how it works and how to prevent it | Malware spotlight
Introduction
Malware is a threat that has increased exponentially in the last few years, with many sophisticated threads impacting citizens, devices, organizations, nation-states and so on. One of the recent threats reported by the FBI and NSA is a new Linux malware developed by Russia’s military hackers, called Drovorub.
According to the FBI and NSA analysis, the malware seems to be associated with the APT28 (Fancy Bear, Sednit), a nickname given to the hackers operating out of the military unity 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main SpecialService Center (GTsSS). This malware has been used to implant backdoors inside compromised networks for persistence, exfiltration and later access.
Drovorub: How it works
Drovorub is a Linux malware kit that takes advantage of the Linux kernel to infect victims. It is equipped with a kernel module rootkit, a file transfer, a port forwarding module and a C2 server that allows total control over the infected device and network.
When this piece of malware is installed on the target, it provides the capability for direct communications to the C2 server controlled by crooks, downloading and uploading target files between C2 and infected devices, port forwarding network traffic to arbitrary hosts and executing commands with root privileges.
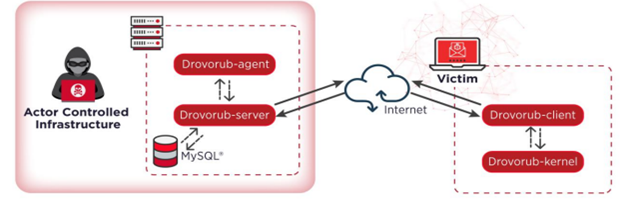
Figure 1: Drovorub high-level diagram with the malware components.
The communication between Drovorub modules is performed using JSON via WebSockets, as seen in Figure 1. The Drovorub-agent, Drovorub-client and Drovorub-server require configuration files and an RSA public key (for the Drovorub-agent and Drovorub-client) or private key (for the Drovorub-server) for communication.
Below are brief descriptions of the Drovorub modules.
Drovorub-server
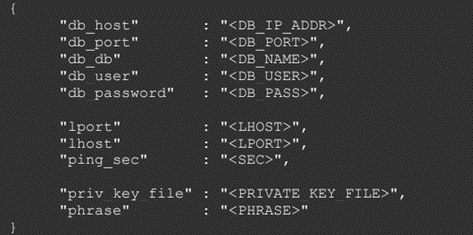
The server is installed and running on the C2 server and is responsible to receive and send messages to the agents installed on the victim’s devices. The Drovorub-server uses a MySQL database to manage the clients (Drovorub-clients and agents). The database stores data used for Drovorub-agent and Drovorub-client registration, authentication and tasking.
Figure 2: Example of the Drovorub-server configuration file.
Drovorub-client
The Drovorub-client component is installed on target devices. This component is capable of uploading and downloading files from C2, port forwarding on the internal network and execute privilege commands due to the rootkit module that provides stealth features to hide the client and the kernel module exploitation hooks.
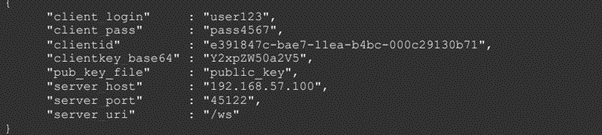
Figure 3: Drovorub-agent configuration file after registration with a Drovorub-server.
Drovorub-kernel module
The Drovorub-kernel module implements the base functionality for hiding itself and various artifacts from user-space, including specified files and directories, network ports, sessions and so on.
When the kernel module is installed and executed, the following activities are performed, namely:
- The Drovorub-kernel module installs all the necessary system call hooks and registers the kernel module by sending a message to the C2 server
- The Drovorub-kernel module hides the Drovorub-client's running processes and the Drovorub client's executable on disk
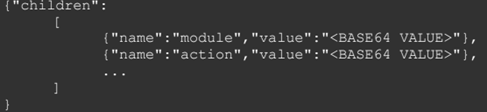
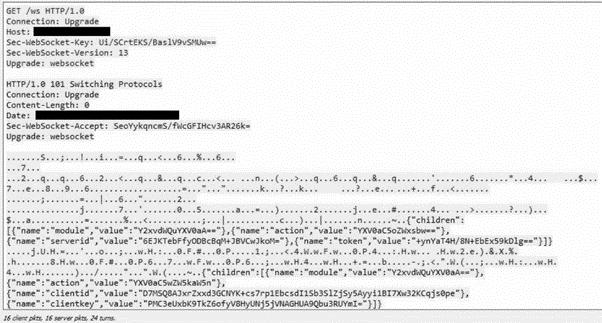
To perform communications with C2, Drovorub uses JSON as the message format for its WebSocket payloads. All the communications have the same structure:
Figure 4: Basic Drovorub JSON payload structure.
Figure 5 below shows the initial WebSocket connection that both Drovorub-client and Drovorub-agent use to connect and authenticate to the Drovorub-server.
Figure 5: Initial WebSocket connection and Drovorub authentication session.
Drovorub-agent
The Drovorub-agent is installed on internet-accessible hosts inside the compromised infrastructure. This agent executable receives commands from its configured Drovorub-server and includes much of the same functionality as the Drovorub-client, except for the remote shell capability.
The Drovorub-agent is not equipped with the kernel module rootkit. The Drovorub-agent is only used to upload and download files from Drovorub-client endpoints and to forward network traffic through port relays.
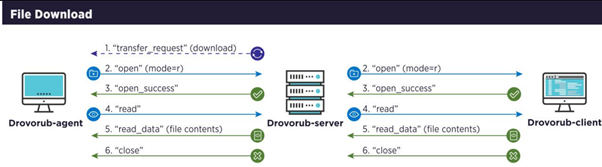
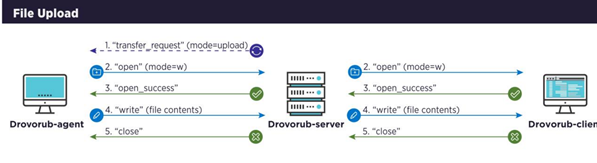
Drovorub-client and agent share some features, such as file download and upload:
Figure 6: File download and upload sequence.
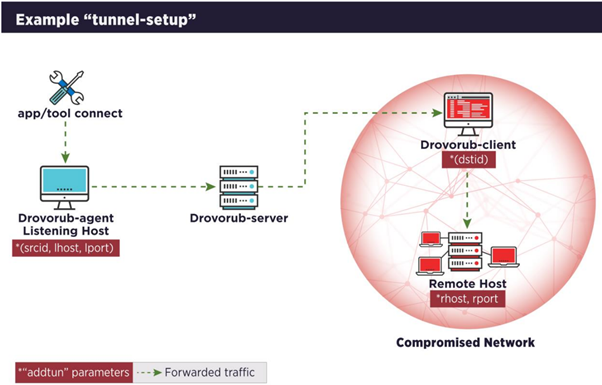
The following diagram illustrates one potential scenario where port tunneling configuration could be used between a Drovorub-agent and a Drovorub-client to relay network traffic to a remote host within the compromised network where the Drovorub-client-infected machine resides.
Figure 7: Example “tunnel” setup.
Through the usage of this panoply of techniques, Drovorub is seen as one of the most emergent threats attacking Linux devices this year. Some prevention measures and mitigations are presented below as a way to respond quickly to incidents this line.
Prevention measures and mitigations
To prevent attacks in-the-wild, organizations should update any Linux system to a version running kernel version 3.7 or later, “in order to take full advantage of kernel signing enforcement,” a security feature that would prevent APT28 hackers from installing Drovorub’s rootkit.
On the other hand, the usage of detection systems such as Network Intrusion Detection Systems (NIDS) like Suricata, Snort, Zeek and host-based agents should be seen as a mandatory measure to block malicious attempts and trigger a notification when abnormal activity is detected. Also, the use of security products in Linux environments is recommended, including antivirus, endpoint detection agents and response. For host-based detection, the NSA provides the following solutions:
- Probing the presence of the Drovorub kernel module via scripting
- Use security products that can detect malware artifacts and the rootkit functionality (Linux Kernel Auditing System)
- Implement live response techniques — searching for specific filenames, paths, hashes and with Yara rules
- Perform memory analysis: The most effective method to find the rootkit
- Make disk image analysis: Malware artifacts are persistent on disk but hidden from regular system binaries and calls by the rootkit
Also, system administrators are advised to perform hardening in its systems to load only modules with a valid digital signature making systems more resilient to malicious kernel attacks via rootkit.
Sources
NSA and FBI Expose Russian Previously Undisclosed Malware “Drovorub” in Cybersecurity Advisory, NSA
Russian GRU 85th GTsSS Deploys Previously Undisclosed Drovorub Malware, NSA
Drovorub “Taking systems to the wood chipper” – What you need to know, The State of Security
FBI and NSA expose new Linux malware Drovorub, used by Russian state hackers, ZDNet