Detection and prevention of DNS anomalies
Malware and Botnets have been a threat to systems and networks for several years. The usual methods of detecting a virus with a local virus scanner or their spreading with intrusion detection system (IDS) will not mitigate the complete threat. The characteristics of traffic could be used to detect different threats. Most Internet communication starts with one or more Domain Name System (DNS) lookups.
DNS (Domain Name System)
The DNS delegates the responsibility of conveying domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. The mapping is done by hostname, IP address, text records, mail exchange information, nameserver information and key information. DNS is composed of a hierarchical domain name space that contains a tree-like data structure of linked domain names (nodes).

Become a certified reverse engineer!
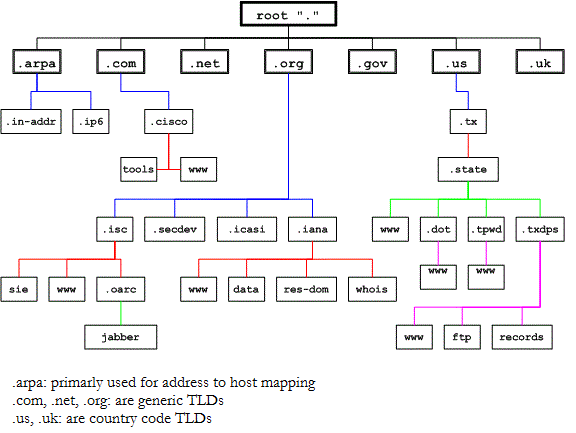
To understand the functionality of DNS, we must understand some basic terminologies first:
Resolver: A DNS client that sends DNS messages to obtain information about the requested domain name space.
Recursion: The action is taken when a DNS server is asked to query on behalf of a DNS resolver.
Authoritative Server: A DNS server that responds to query messages with information stored in Resource Records for a domain namespace stored on the server.
Recursive Resolver: A DNS server that recursively queries for the information asked in the DNS query.
Fully Qualified Domain Name (FQDN): A Fully Qualified Domain Name is the absolute name of a device within the distributed DNS database.
RR: A Resource Record is a format used in DNS messages that is composed of the following fields: NAME, TYPE, CLASS, TTL, RDLENGTH, and RDATA.
Zone: A database that contains information about the domain name space stored on an authoritative server.
How DNS Works
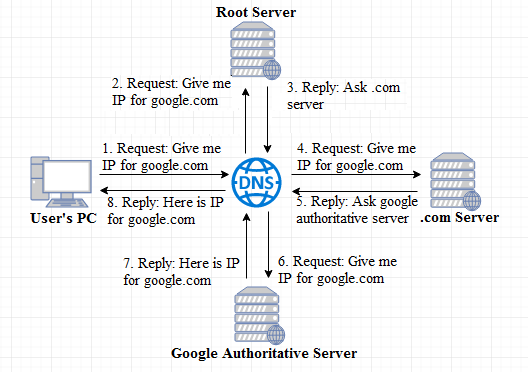
The primary function that a DNS perform is the translation of hostnames to IP addresses or IP addresses to hostnames. This could be a client application such as a web browser or an email client or any DNS application sending a DNS query to a DNS server requesting the information defined in a Resource Record (RR). The process of translating the request is comprised of several steps:
- The DNS resolver sends a query message to the recursive resolver asking for the address of www.ehacking.net/.
- The DNS recursor sends a query message to the root name servers looking for the .net domain name space.
- The root name servers send a DNS referral response message to the DNS recursor informing it to ask the Top Level Domain (TLD) name servers for the .net domain name space.
- The DNS recursor sends a query message to the TLD name servers looking for the .ehacking.net domain name space.
- The TLD name servers send a DNS referral response message to the DNS recursor informing it to ask the .ehacking.net name servers, name server 1 .ehacking.net or name server 2 .ehacking.net, about this domain name space.
- The DNS recursor sends a query to name server1 .ehacking.net or name server2 .ehacking.net asking for www.ehacking.net.
- The .ehacking.net name servers, name server 1.ehacking.net or name server 2.ehacking.net, send an authoritative DNS query response message to the DNS recursor with the A (address) RR information for www.ehacking.net.
- The DNS recursor sends a DNS query response message to the DNS resolver with the A (address) RR information for www.ehacking.net.
DNS anamoly detection
There are worms and malicious programs to generate DNS packets that violate the format of a valid DNS header. This can be detected at the network level as well as in a well-formatted host based script that has the capability to parse the packets and decode DNS traffic for validations. Once we have the anomalies detected, we can look into the action items for the source IP addresses. For the detection of DNS anomalies, there are two groups. The first group of method analyzes the packets for DNS anomalies in the data they contain; these detection methods can be performed in real time as packets arrive. The second group of method performs statistical analysis on a large set of data. This allows us to detect anomalies in the volumes of queries or the query responses over time.
Blacklisting
In general, a blacklist is used to deny access to certain hosts because they are known to be malicious. The blacklist can be generated by combining different popular blacklists to check the query against. The blacklist checking mechanism based on the principle: if it's on the list, it is malicious. This method will probably identify mostly human trigger anomalous DNS traffic.
The biggest flaw in the blacklisting method is that the list can contain thousands of entries, which seems to be a lot. There may be many domains that don't exist anymore or multiple IP addresses assigned to a single domain.
Tunnel DNS detection
Since DNS data is often poorly monitored and frequently allowed to pass through the firewall, it is an ideal candidate for a covert channel. DNS packets can be used to create a hidden data channel (covert channel). There are seemingly numbers of ways to hide data in legitimate DNS packets.
The detection of a covert channel is based on analysis of packet characteristics. There are a few characteristics that can distinguish packets used in the covert channel. If the channel is used to transport reasonable amounts of data, the length of the query or the size of the response record can easily be checked. The average length of the one million most used domains is ten characters, where the average query length of a DNS tunnel used to copy a random file is well over 30 characters. If this method is used in combination with timing analysis, a high volume stream of large DNS packets can be identified.
Fast flux detection
Fast-flux is a technique used by cyber-criminals to hide critical hosts behind a changing set of compromised hosts. A modified DNS server is used that will return a different set of IP addresses for a given domain over time and relay for instance HTTP traffic to the server hosting malicious site.
The fast flux hosting service can be easily detected. There are three things that should be noticed. The first obvious notion is the number of records. The domain resolves to ten "A" type of records that is a lot for most websites. The second notion would be the IP addresses, and the third is abnormally low Time-To-Live (TTL) of the records. It has been set to 300 seconds or five minutes. This allows the fast-flux service provider to switch hosts very frequently, to mitigate the fact that bots are normal clients which are not reliable as service providers.
Character frequency
The character frequency analysis method is a very promising method for detecting generated data where a natural language would be expected. It is used in cryptography for detecting language characteristics in a cipher text. This method was initially investigated for reliable covert channel detection, but it can detect more anomalous data.
An attacker can compress and encrypt the data to optimize the bandwidth and hide the data. If the language of the adversary can be predicted, the characteristics of the language can be compared to the domain name and an assumption can be made if the domain name is generated by the system or chosen by the attacker.
Implementation flaws used for attacks
It is a DNS server that allows DNS clients that are not part of its administrative domain to use that server for performing recursive name resolution. The primary task of the open resolver is to provide responses to queries from anyone asking a question.
The malicious activities made DNS open resolver vulnerable to attacks like
DNS Cache Poisoning: It occurs when an attacker sends false and usually spoofed RR information to open resolver that is further stored in the DNS cache for the lifetime TTL (Time-To-Live).
DNS Amplification and Reflection Attacks: It uses DNS open resolver to increase the volume of attack and hide the true source of the attack. This results in DOS and DDOS attacks.
Resource Utilization Attack: This attack tries to consume all available resources to impact operations of the open resolver negatively.
Prevention
The following configurations can be applied to the DNS Server service to prevent the server from acting as an open resolver.
Open a Command Prompt and at the Command Prompt, issue the following command:
DnsCmd ServerName
/Config
/NoRecursion {1|0}
DnsCmd: This is the name of the tool used from the CLI to perform administrative tasks for the DNS Server service.
/Config: Specifies that the argument for the DnsCmd command applies to the configuration of the DNS Server service.
/NoRecursion: Specifies that an argument of 1 or 0 will follow to disable or enable recursion for the DNS Server service.
{1|0}: This is the name of the tool used from the CLI to perform administrative tasks for the DNS Server service.
Abusing TTL Records
The Time-To-Live (TTL) field used to inform the resolver how long the RR may be cached until the resolver needs to send a DNS query again. This field can be used maliciously by setting the value for an RR to a short or long TTL value.
Short TTL: The hostname to IP address mapping for devices in the requested domain name space will rapidly change.
Long TTL: it can distribute the RRs for the malicious host to many resolver clients, thus allowing use for malicious activities.
Prevention: To prevent a DNS server from storing RR Time-To-Live information in the cache of the resolver, following configuration can be used:
Maximum cache length for RRs
// The 'max-cache-ttl' configurations option allows the
// operator to define the amount of time the DNS server
// will store RR information in the resolver cache.
//
// Note: Operators should test any non-default changes
// prior to deploying to production environments.
options {
max-cache-ttl <number>;
};
Maximum cache size
// The 'max-cache-size' configurations option allows the
// operator to define the amount memory a DNS server will
// use for storing RR information in the resolver cache.
// When data stored in cache has reached the configured
// memory limit, BIND will purge RR information from the
// cache to store new RR information.
//
// Note: If this options configuration is set to a low
// value, it may cause the DNS server to issue queries
// more often since entries stored in the cache will be
// purged quicker. This is dependent on the amount of
// queries the DNS server processes.
//
// Note: Operators should test any non-default changes prior
// to deploying to production environments.
options {
max-cache-size <number>;
};
Spoofing prevention
Several techniques can be used to prevent and limit spoofing:
IP source guard:
In the IP Source Guard, the DHCP inspects traffic within a VLAN to understand which IP addresses have been assigned to which network devices on which physical switch port. The information is then stored in a DHCP snooping binding table; IP source guard can leverage it to filter IP packets received by a network device. If a packet is received with a source address that does not match the DHCP snooping binding table, the packet is dropped.
Access control list:
Access control lists (ACLs) can provide static anti-spoofing protection against unused and unreliable address space. These anti-spoofing ACL are applied to network traffic receiving boundaries as a component.
Spoofing can be minimized in traffic originating from the local network by applying ACLs that use Access Control Entries (ACEs) which limit the traffic to only valid local addresses.

Become a certified reverse engineer!
Indicators for DNS anomaly
- Increase in number of DNS packets
- Decrease in cache hit ratio
- Increase in average DNS queries of individual source IP addresses
- Increase in number of recursive queries
- Increase in number of source IP addresses within a limited time slot
- Decrease in ratio of resolved queries
There are many companies working hard to overcome DNS anomalies and the threats associated with it. They are rapidly introducing new promising configurations, but there are some protocol and other flaws that make DNS vulnerable. We should consider some counter moves when DNS anomaly is encountered so that any loss can be prevented on time.








