BlindingCan malware: What it is, how it works and how to prevent it | Malware spotlight
Introduction
BlindingCan is a recent malware that has made headlines in the last few months. This malware is used by government-backed hackers from North Korea to perform attacks in the wild around the globe. In this article, we will reveal how this malware has been used, how it operates in-depth and some preventive measures to stop this threat.
The US Federal Bureau of Investigation (FBI) and Cybersecurity and Infrastructure Security Agency (CISA) published a report entitled Malware Analysis Report (AR20-232A) that describes a new piece of malware named BlindingCan. This is a Trojan developed by North Korean hackers from the Lazarus group and with the goal of performing attacks against military defense companies and aerospace sectors. The intention is to steal confidential intelligence and secret information.
BlindingCan: Operation
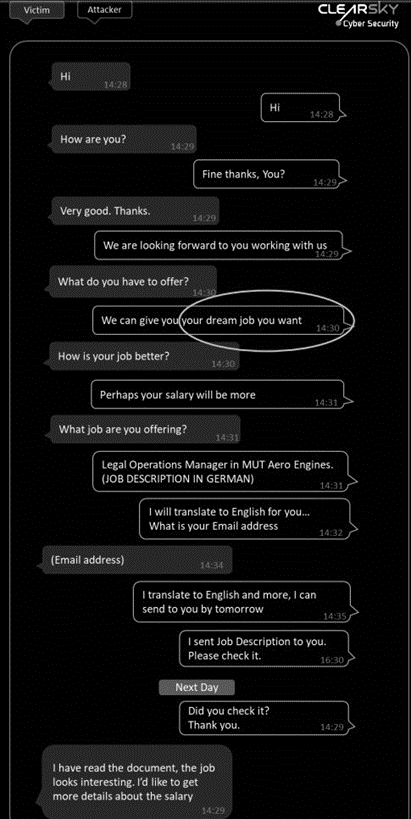
Criminals impersonate recruiters from legitimate companies to lure the victims to open a malicious document — an Office or PDF file that will infect its system. Once criminals gain access to the victim’s device, they perform reconnaissance to gather intelligence surrounding key military and energy technologies. The FBI believes that “threat actors are using malware variants in conjunction with proxy servers to maintain a presence on victim networks and to further network exploitation.” [CLICK IMAGES TO ENLARGE]
Figure 1: Spearphishing message from criminals that lures the victim to open a malicious document sent via email
After opening the Word document, a template injection attack is used to install the malware on the target system. This technique allows the download of an external weaponized Word template containing macros and that can be executed to infect the victim’s device. This evasive attack technique is not new but still very efficient to bypass AVs detection.
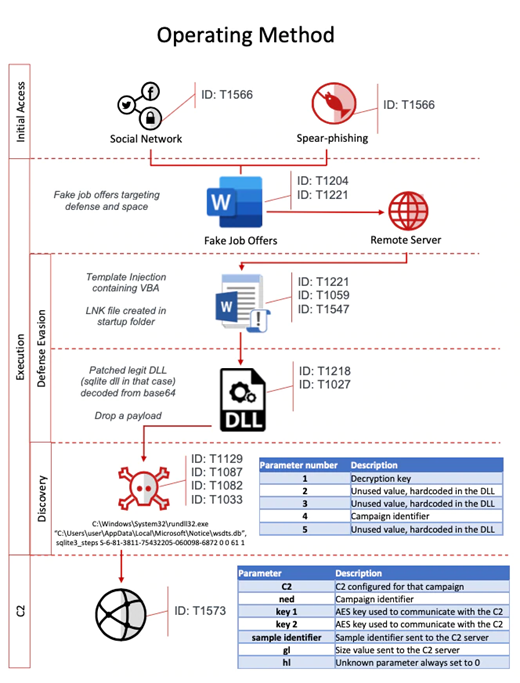
As mentioned, the malicious Word documents contain content related to legitimate job positions. Figure 2 presents the operation workflow of the BlindingCan malware.
Figure 2: BlindingCan operation workflow (McAfee)
The template file is download from a compromised website by crooks, as presented in Figure 3.
Figure 3: External URL with the weaponized Office template (DOTM)
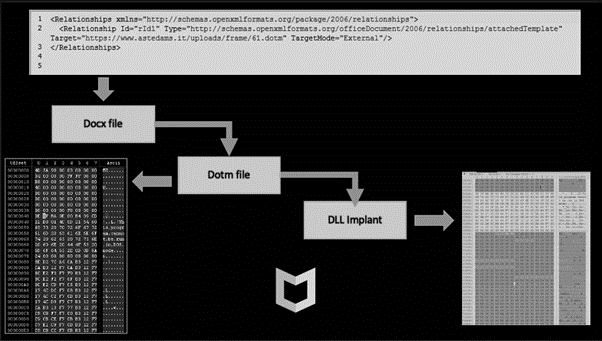
The DOTM (Office template filetype) file is used for loading the next stage, a patched legitimate DLL, onto the victim’s system in order to collect sensitive data and perform lateral movement. The DOTM file (template file) contains a Visual Basic macro to load other malicious DLLs specially prepared for this attack.
Figure 4: BlindingCan workflow — from the Office file download to the DLL implant in the victim’s system
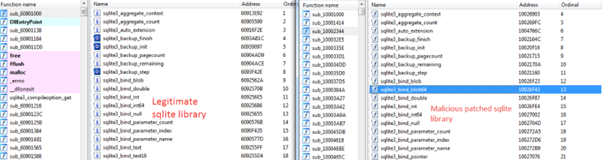
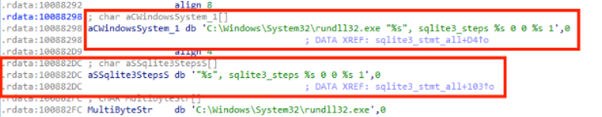
In addition, these DLLs are patched versions of legitimate DLLs such as the SQLite library.
Figure 5: Legitimate library on the left side and the malicious library on the right side
The patched DLL (the malicious one) shares a lot of code with the legitimate DLL, but some calls were added in order to get another DLL from a remote server that is then injected directly into the memory. The injection point can be seen in Figure 6 below, where the DLL injection technique was used via rundll32.exe.
Figure 6: DLL injection technique used by the patched DLL during the BlindingCan infection chain
During its execution, a keylogging and clipboard monitoring component is executed and additional information is extracted from the targeted system. For this, WMI commands are used by crooks. The following command, for example, is used to get the AV products installed on the compromised Windows system:
The malware can also perform several tasks, such as:
- Collect detailed information about all disks installed on the system
- Collect local IP address details
- Get processor information
- Delete itself from infected systems and clean its traces
- Create, initiate and terminate a new process
- Read, write, execute and move files
- Change the current directory for a file or process
- Modify file or directory timestamps
- Operation on processes (create a list, execute, kill)
- Upload/download files
- Obtain disk information
- Obtain a list of services
- Execute arbitrary shell command
During the execution, the malware configuration is stored in one of the following locations:
- Hardcoded in the malware itself
- Stored in a registry entry
- Saved as a file
In case it is saved as a file, it is stored in the same folder where BlindingCan is located. The following directory is used if the configuration is stored in a registry entry:
A configuration file of the BlindingCan malware can be observed in Figure. 7. This piece of information also includes proxy details, as well as C2 server information.
Figure 7: Decoded config from the BlindingCan malware
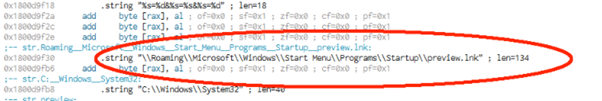
BlindingCan gets persistence by delivering an LNK file into the startup folder, as presented below.
Figure 8: A LNK file is created into the startup folder as a persistence technique
Final thoughts
North Korean government hackers are active threat groups that have targeted the US in recent years, together with Chinese, Iranian and Russian groups. Prevention, as always, is the key to prevent these kinds of attacks.
In this way, it’s important to understand and know the evolution of these attacks over the years in order to apply what we have learned from past incidents. A robust threat response process can then ensure that controls are adaptable to the TTPs and, in this case, create heightened awareness inside the organization.
Finally, a secure web gateway can be seen as a mandatory part of organization security architecture as it can block access to malicious websites. Other measures such as keeping the software and OS updated and having an AV installed and updated are crucial steps that can help us to fight the real challenge called malware.
Sources
Malware Analysis Report (AR20-232A), Cybersecurity & Infrastructure Security Agency
Operation (노스 스타) North Star A Job Offer That’s Too Good to be True?, McAfee
BLINDINGCAN: A New Trojan Strain Abusing Microsoft Attached Document Template, OPSWAT
North Korean hacking group is using BLINDINGCAN malware to attack defence firms, warns CISA, computing.co.uk
The BLINDINGCAN RAT and Malicious North Korean Activity, SentinelOne
BLINDINGCAN - Malware Used by Lazarus, JPCERT/CC Eyes