Bad Rabbit: A New Ransomware Campaign Rapidly Spreading Worldwide
October 24, Bad Rabbit is spreading in the wild
On October 2017, a new massive ransomware campaign rapidly spread across Europe, the malware dubbed Bad Rabbit rapidly infected systems of more than 200 major organizations mostly in Russia, Ukraine, Germany, Japan, and Turkey in a few hours.
The Bad Rabbit ransomware compromised systems at several big Russian media outlets, the Interfax news agency, and Fontanka.ru confirmed the malware hit them.

Become a certified reverse engineer!
According to Kaspersky, the Odessa International Airport has reported on a cyber attack on its information system, but it is still unclear it is the same attack.
"In some of the companies, the work has been completely paralyzed – servers and workstations are encrypted," head of Russian cyber-security firm Group-IB, Ilya Sachkov, told the TASS news agency.
Initially, the US and other Western countries were not hit explicitly by the Bad Rabbit campaign, but according to antivirus firm Avast, the threat has also been detected in the USA.

"Theoretically, if a U.S. organization had infected partners in the targeted regions and were on the same WAN with SMB access, Bad Rabbit could have spread laterally to the computers located in the USA," reported bleepingcomputer.com.
The US-CERT also published a security advisory on the Bad Rabbit campaign, it warned of using unpatched and unsupported software.
"US-CERT has received multiple reports of ransomware infections, known as Bad Rabbit, in many countries around the world. A suspected variant of Petya, Bad Rabbit, is ransomware—malicious software that infects a computer and restricts user access to the infected machine until a ransom is paid to unlock it," reads the alert published by the US-CERT. "US-CERT discourages individuals and organizations from paying the ransom, as this does not guarantee that access will be restored. Using unpatched and unsupported software may increase the risk of proliferation of cybersecurity threats, such as ransomware."
Many experts pointed out that the Bad Rabbit ransomware is Petya-like malware the comparison of the source code with NotPetya revealed the existence of reused pieces of code.
The ransomware demands 0.05 bitcoin ransom (~ $280 at time of the attack) from victims to unlock their systems.
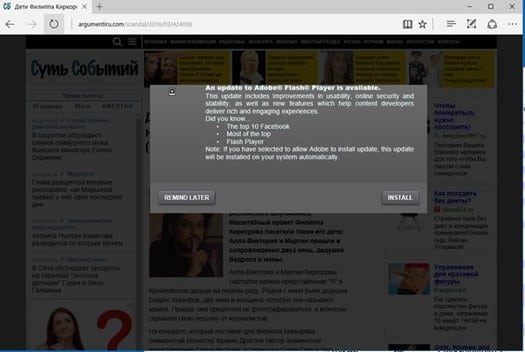
The Dab Rabbit ransomware spread via drive-by download attacks; attackers are using fake Adobe Flash players' installer to trick victims into installing the malware.
Figure 1 - Fake Adobe Flash players installer in Bad Rabbit attack
"On October 24th we observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here's what a ransom message looks like for the unlucky victims," reported Kaspersky Lab.

Figure 2 - Bad Rabbit screen
"No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We have detected a number of compromised websites, all of which were news or media websites," continues the analysis published by Kaspersky Lab.
The malware researchers from the security firm ESET who early analyzed the malicious code tracked is as 'Win32/Diskcoder.D'. According to ESET experts, the malware is a new variant of Petya ransomware. It relies on the open-source encryption software DiskCryptor; it uses AES-128-CBC for the encryption and keys are generated using CryptGenRandom and then protected by hardcoded RSA 2048 public key.
The researchers discovered that the new ransomware does not use the EternalBlue exploit. First reports revealed the malicious code first scans the target network for open SMB shares, tries to access them using the hardcoded list of credentials to drop the malicious code, then uses the Mimikatz tool to extract credentials from the target.
"Win32/Diskcoder.D can spread via SMB. As opposed to some public claims, it does not use the EthernalBlue vulnerability like the Win32/Diskcoder.C (Not-Petya) outbreak. First, it scans the internal network for open SMB shares," reads the analysis published by ESET.
"Mimikatz is launched on the compromised computer to harvest credentials. A hardcoded list username and password is also present."
New precious details emerged from the analysis of malware researchers at Cisco Talos and F-Secure who respectively discovered and confirmed the presence an NSA exploit in the Bad Rabbit ransomware.
"Despite initial reports, we currently have no evidence that the EternalBlue exploit is being leveraged. However, we identified the usage of the EternalRomance exploit to propagate in the network. This exploit takes advantage of a vulnerability described in the Microsoft MS17-010 security bulletin. The vulnerability was also exploited during the Nyetya campaign," reads the analysis published by the Talos team.
Researchers from ESET reported that the payment website is hosted on the Tor network, the ransom note provided instructions to make the payment while displaying a countdown of 40 hours before the price of decryption increase.

Figure 3 - Bad Rabbit countdown
Bad Rabbit Preliminary Analysis
The colleagues at the CSE Cybsec ZLab malware lab have conducted a preliminary analysis of the Bad Rabbit ransomware discovering some interesting aspects of the attack.
The team released a preliminary pre-announcing a complete analysis that they will release in the next days, but we believe our findings can be useful for the security community.
This malware calls back to the notorious NotPetya primarily for two characteristics:
- The behavior after the reboot with a particular ransom note (Figure 1)
- The spreading capability through lateral movements that rely on the SMB protocol.
Comparing NotPetya with Bad Rabbit, the malware researchers noticed that the latter has more sophisticated behavior. Malware authors likely reused some pieces of NotPetya code increasing the complexity of the code itself and fixing coding error that transforms NotPetya from a ransomware to wiper. The Bad Rabbit leverages the open source library DiskCryptor to encrypt the user files.
The ransomware propagates through drive-by download attacks; attackers infected many sites in Russia, Bulgaria, and Turkey. Bad Rabbit hackers deployed on the compromised websites a JavaScript that redirects visitors to 1dnscontrol[.]com. At the time of the analysis, the site, which was hosting the malicious file, is no longer reachable. The script was used to download the ransomware using a POST request to the static IP address (185.149.120[.]3).
The ransomware appears as an Adobe Flash update, in reality, it is a dropper containing some payloads.
When the dropper executes itself, it first checks the existence of the file "C:Windowscscc.dat." This is the library used by the malware to encrypt the user files. The ransomware interprets the presence of the file as an indicator of compromise; this means that the host has been already infected and for this reason, the attack chain is halted. We can conclude that the file cscc.dat acts a sort of killswitch for the malware.
When the infection is ready to go, the dropper file extracts some files:
- "C:Windowsinfpub.dat"
- "C:Windowscscc.dat"
- "C:Windowsdispci.exe"
- "C:WindowsEC95.tmp"
The researchers discovered that "infpub.dat" is used by the author as the "controller" of Bad Rabbit; it controls every action of the dreaded ransomware. Once the "infpub.dat" is loaded in memory, it deletes itself from the disk remaining only in memory, making hard the detection as many other fileless malware.
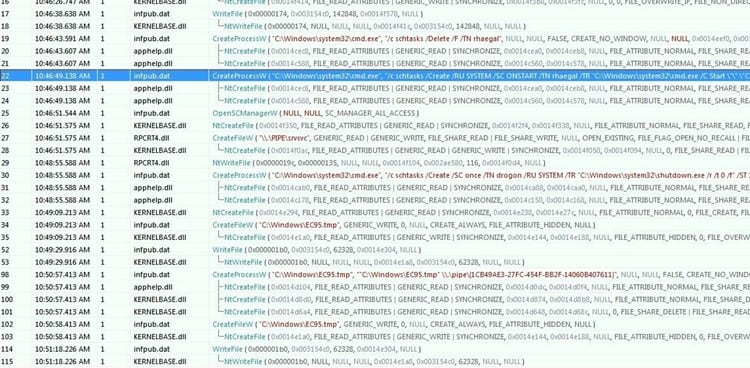
Figure 4 - Some actions of "infpub.dat"
Figure 2 shows the process "infpub.dat" performs several actions, including the reboot of the machine and the execution of "dispci.exe" executable at the startup.


Figure 5 - Figure 5 - Reboot scheduling
The "infpub.dat" is also tasked of the propagation in the network with a particular SMB tool to execute on the other machines in the subnetwork. It launches a modified version of the "Mimikatz" tool to harvest the password stored on the victim's host and reuse it to gain access to other machines.
The malware scans the target network for open SMB shares, tries to access them using the hardcoded list of credentials to drop the malicious code, then uses the Mimikatz tool to extract credentials from the target.
Another difference between NotPetya and Bad Rabbit is that the latter enforces its propagation capability brute forcing with its own wordlist.
After the scheduled reboot, the scheduled process "dispci.exe" overwrites the original MBR with its own version.
The following chart shows the behavior of the malware observed by the malware experts at CSE ZLab team:

Figure 6 - Bad Rabbit's control flow
Conclusion
Further reflections on the Bad Rabbit ransomware
While Petya and NotPetya implements a Two-stage attack, the Bad Rabbit has three stages.
The Bad Rabbit attack vector requested more effort respect the Petya/NotPetya ones; threat actors compromised dozens of websites to deploy the malicious JavaScript.
Most of the compromised websites belong to restaurants, hotels and "house rental" services.
Who is behind the attack? What is the real attackers' motivation?
In this phase is not possible to attribute the attack to a specific threat actor. It is interesting to note that the malware does not explicitly implement a wiper behavior, suggesting the operators are financially motivated. However, The Onion website used for the payment is no longer available; this implies that victims cannot pay the ransom to decrypt the file.
This behavior could be intentional and used by attackers to hide as a distraction tactic.
How to protect yourself?
Security experts are still analyzing the Bad Rabbit ransomware; meantime, malware researchers from Kaspersky are suggesting disabling WMI service to prevent the malware from spreading over the target network and to block the execution of files c:windowsinfpub.dat and c:Windowscscc.dat.
CSE experts also pointed out that c:Windowscscc.dat file could be considered a Killswitch for Bad Rabbit; its presence halts the infection process.
To protect your system against this threat
- Create a couple of files C:Windowsinfpub.dat & C:Windowscscc.dat.
- Remove all permissions to both files. When doing this, remove the inheritance, so the files do not inherit the perms of the C:Windows folder.
As usual, stay vigilant when opening unsolicited mail containing documents or clicking on embedded links.
References
http://securityaffairs.co/wordpress/64713/malware/bad-rabbit-ransomware.html
https://www.kaspersky.com/blog/bad-rabbit-ransomware/19887/
https://www.welivesecurity.com/2017/10/24/bad-rabbit-not-petya-back/
https://www.kaspersky.com/blog/bad-rabbit-ransomware/19887/
http://securityaffairs.co/wordpress/64741/malware/preliminary-analysis-bad-rabbit.html
http://securityaffairs.co/wordpress/63081/malware/zlab-malware-analysis-report-notpetya.html
https://www.us-cert.gov/ncas/current-activity/2017/10/24/Multiple-Ransomware-Infections-Reported
http://blog.talosintelligence.com/2017/10/bad-rabbit.html
https://labsblog.f-secure.com/2017/10/26/following-the-bad-rabbit/