Analyzing a DDoS Trojan
MD5: 67877403db7f8ce451b72924188443f8
Installer:
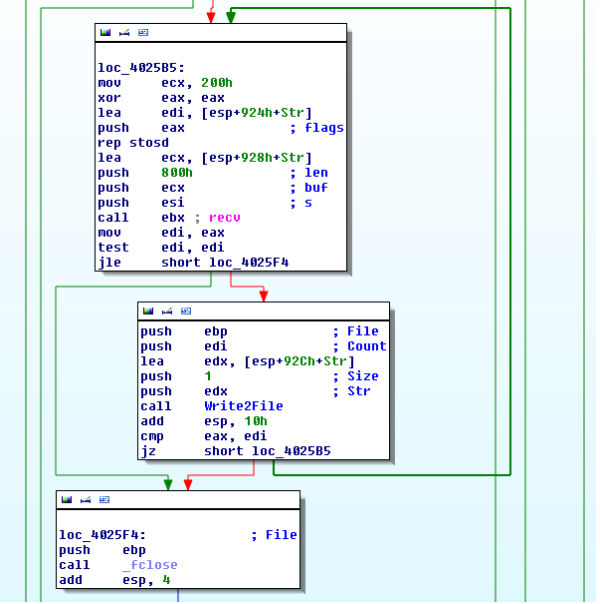
In the main function of the malware, two subroutines are used for checking whether the malware is already installed on the system or not.

Become a certified reverse engineer!
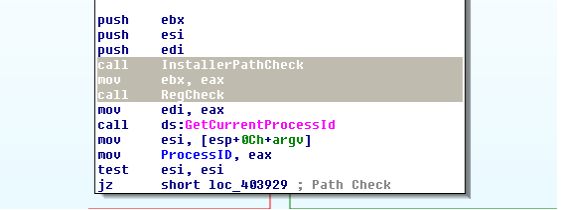
Registry and file paths are checked
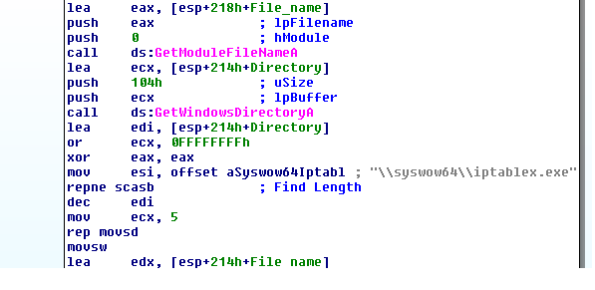
If you look, you will see the file installation is syswow64, which is present in 64-bit systems, so this will fails for all 32-bit Operating Systems.
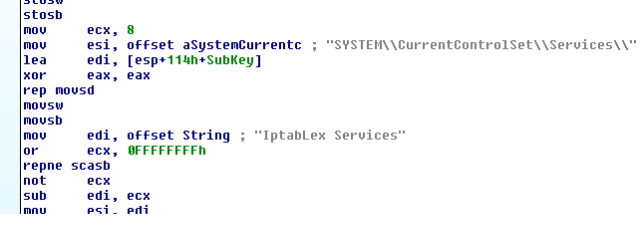
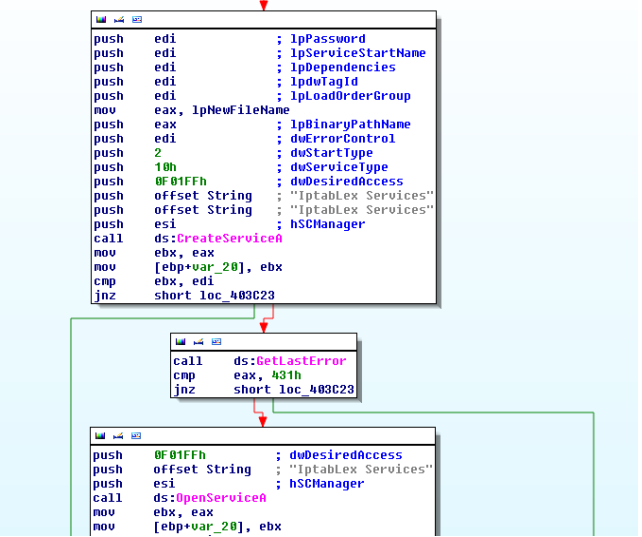
Registry check gives us an indication that this file will be installed as a service with service name as "Iptablex Services"
If both the checks fail at first, it will proceed to check for arguments supplied to the binary
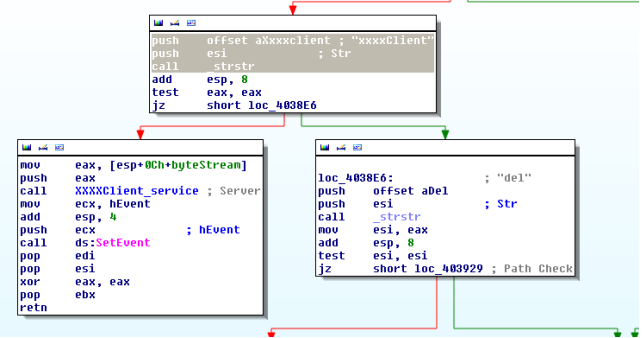
The binary takes two arguments
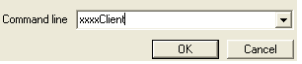
1: xxxxClient
2: del
The "xxxxClient" argument is required when the binary is setup to make C2 communications and all the initialization is done.
The "del" argument is required when the original binary is be deleted
In the first run, most of the checks will fail. After than Binary reaches to the following node
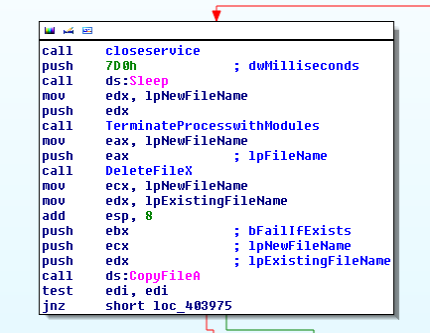
Before the installation routine is called, a call to "TerminateProcessWithModules" is made. This subroutine will enumerate all processes and their loaded dll's if a module with a same name as binary is found it will proceed to terminate the process.
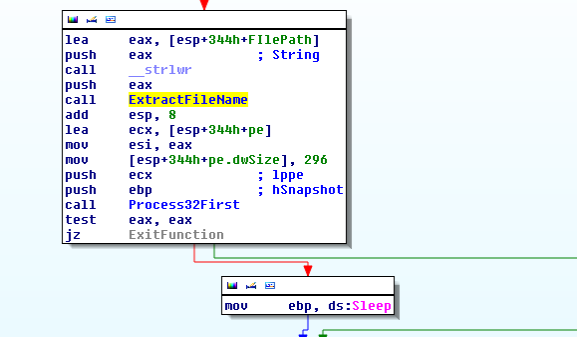
If parent process ID is as same as the current process then the termination process is skipped. This is done because process is started as a child process by the main installation itself. More details will follow.
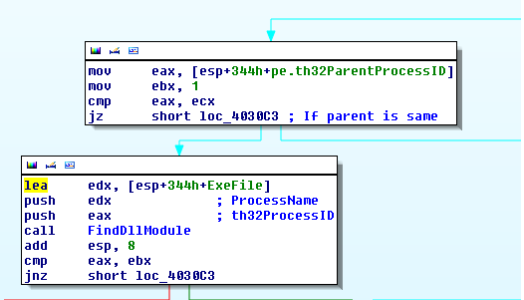
Actually, this subroutine is buggy itself. There is a call to "ConvertUnicodetoAscii "subroutine which takes a string argument from PROCESSENTRY32.szExeFile, which is already an ASCII string. Due to which, it will never be successful in terminating an already running instance of the same malware.
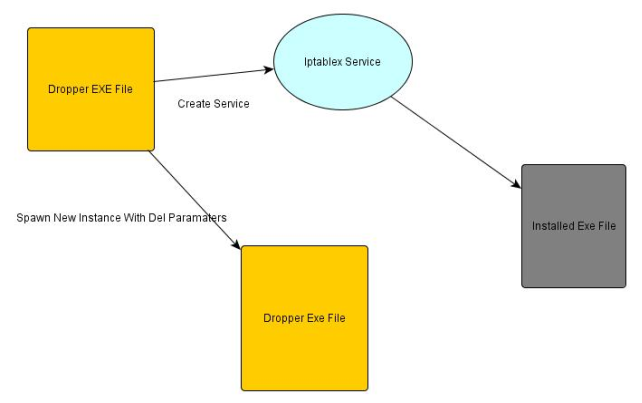
Not only will it further proceed to create and start the service "Iptablex Service" but also it will execute itself again with "del" in parameters
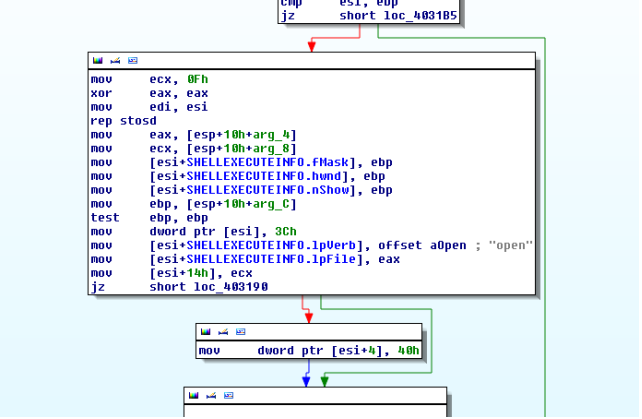
The service starts from ServiceProc subroutine . During the initialization phase two global windows event objects are created i.e "GlobalhbllxxxxServer" and "GlobalhbllxxxxClient".
These events are necessary for the child process to know if initialization phase is over or not.
It will further proceed to launch another instance of the Exe file from the service itself with "xxxClient" as parameter
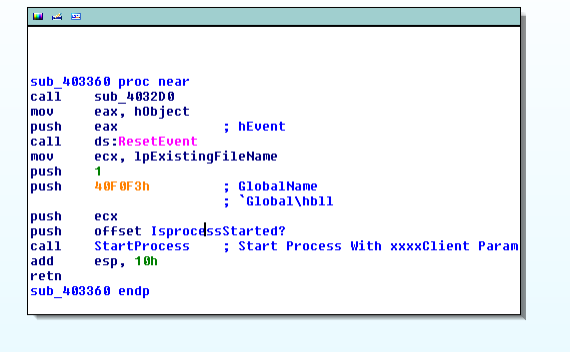
The new instance starts from the following subroutine .
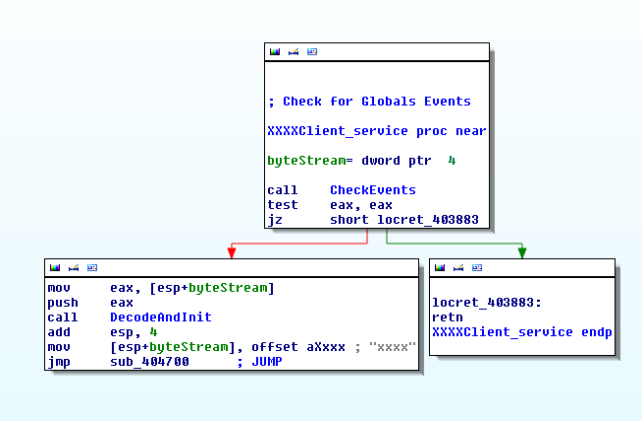
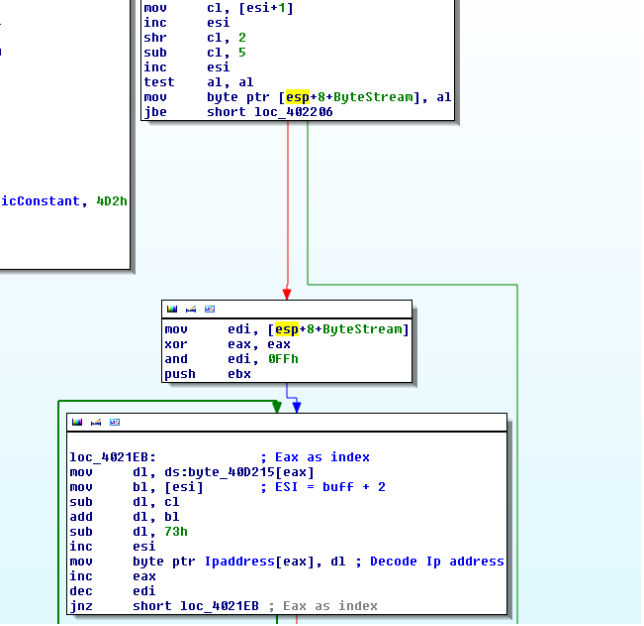
The CheckEvents subroutine checks if global events are set. The c2 parameters (port and IP/DOMAIN) are decoded using the following simple algorithm
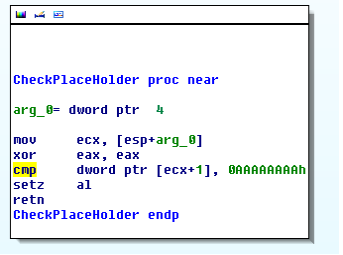
If instead of Ipaddress Domain is present, the domain is checked using a placeholder in the DWORD(EncodedByteStream + 1) as 0xaaaaaaaa
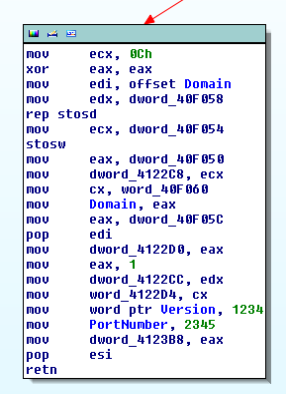
If we bypass that, checking it further reveals the domain used with a constant port number 2345
For skipping, the installation routine and making analysis easy .Following program can be used to keep the Events Alive before starting to debug
#define WIN32_LEAN_AND_MEAN
#include <windows.h>
signed int __cdecl startEvent()
{
HANDLE hObject;
HANDLE hEvent;
hObject = CreateEventA(0, 0, 0, "GlobalhbllxxxxServer");
if ( hObject )
{
if ( GetLastError() != 183 )
{
hEvent = CreateEventA(0, 0, 1, "GlobalhbllxxxxClient");
if ( hEvent )
return 1;
}
CloseHandle(hObject);
}
return 0;
}
int main(int argc, char **argv)
{
startEvent();
while (1)
{
Sleep(3000);
}
}
If we start the binary with "xxxxClient" arguments, we will skip the installation phase and directly jump to c2 communication subroutine
C2 Communication:
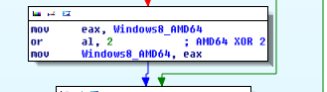
Initially, the initialization packet is transmitted to c2c and it consists of plain text OS related data mostly related to hardware installed. A variable is set in the packet if Windows 2008 server and AMD processor is found. Which shows that these crooks are interested in powerful hardware. This value is set using a xor mask of 4 and 2

After sending an initialization packet, a thread is created for receiving commands from the server. A select time out is set to 30 seconds. If nothing is received within 30 secs then "xy" is sent to the server.
Any request of length greater than or equal to 262 bytes is discarded.
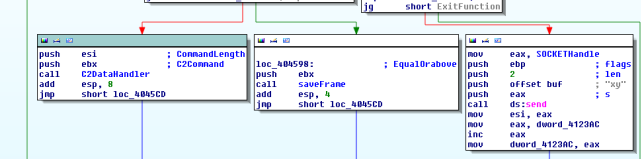
Commands received from c2 are sent to the handler where commands are handled commands like TCP_RAW DDOS flood, Update binary are present.

Become a certified reverse engineer!