SQL Injection Through SQLMap Burp Plugin
Hai folks,
This article gives you an overview of SQLMAP, an SQL injection tool used for detecting and exploiting the SQLI.
What is SQLI?
SQL Injection is a web based attack used by the hackers to steal the sensitive information from the organizations through web applications. It is one of the most common application layer attack used today. This is a kind of an attack that takes an advantage of improper coding of the web applications that allow the hackers to exploit the vulnerability by injecting SQL commands into the prior web application.

What should you learn next?
Underneath fact for the SQL Injection is because of the fields available for the user input in the web application allows SQL statements to pass through and interacts or queries the database directly.
For Example, Let us consider a web application that implements forms-based login mechanism to store the user credentials and perform a simple sql query to validate each login attempt. Here is a typical example.
select * from users where username='admin' and password='admin123';
If the attacker knows the username of the application administrator is admin, he can login as admin without supplying any password.
admin'--
The query in the back-end looks like
Select * from users where username='admin'--' and password='xxx';
Note the comment sequence (--) causes the followed query to be ignored, so query executed is equivalent to:
Select * from users where username='admin';
So password check is bypassed.
What is SQLMAP?
SQLMAP is an open source penetration testing tool that helps in automating the process of detecting and exploiting SQL injection vulnerabilities and taking full access over the database servers. SQLMAP comes with powerful detecting engine, and many niche features for the penetration tester and wide range of switches lasting from database fingerprinting, data fetching from the database, accessing the underlying file system and executing the commands on Operating System via Out-of-band Connections.
Since SQLMAP is developed in python it is a portable application, meaning that it will work in any operating system that supports python.
What is SQLMAP burp plug-in?
When we audit a web application, we normally configure an intermediate proxy to have more control over the request and response parameters.
SQLMAP plug-in is an add-on feature that we can configure to the burp through which we can redirect a URL or a request directly to the SQLMAP with a single mouse click
How to download the plug-in:
You can download the zip file from the following URL:
http://code.google.com/p/gason/downloads/list
Unzip the file and keep it in the same folder where burp proxy is located.
Then execute the following command to run the burp with plug-in
LINUX:
Java –classpath burpplugins.jar:"burpsuite_v1.4.0.1.jar" burp.StartBurp
Windows:
Java –classpath burpsuite_v1.4.0.1.jar;burpplugins.jar burp.StartBurp
Replace the burpsutie with the appropriate version that you are using. In my case I am using burpsuite_v1.4.0.1.jar
You need to download the SQLMAP as you need to give the executable to the plug-in
Setting up SQLMAP:
On Windows:
- Download and Install python 2.7*(http://www.python.org/getit/) official website for downloading python
- Download sqlmap(https://github.com/sqlmapproject/sqlmap)
- Unzip the name.zip file to sqlmap directory.
On Debian or Ubuntu
- Sudo apt-get install python-tk python2.7
- git clone git://github.com/sqlmapproject/sqlmap.git
- cd sqlmap
- wget http://gui-for-sqlmap.googlecode.com/files/sqm-60712.zip
- unzip sqm-60712.zip
Setting up the environment:
- If you are using OWASP broken web application, then simply access one of the vulnerable site from your local browser where you are running SQLMAP
- If you don't use OWASP broken web application, then you need to set up a virtual machine that has a web server to host the vulnerable web application.
- Configure another VM with ubuntu where the attacker runs SQLMAP
Configuring the Proxy:
- If you are using Mozilla Firefox, then go to Edit > Preferences > Advanced > Network > settings and select "Manual Proxy Configuration" by enabling the radio button. Run the HTTP proxy with local-host and the port in which the proxy is running
- If you are using Chrome, then go-to settings > Show Advanced Options > Network > Change proxy Settings > Connections > Lan settings.
How to use the plug-in:
Once you load the plug-in, then it is very easy to make use of it. Run the burp proxy with loaded plug-in. In the "site map" tab under the "target" you can see the particular domain that you are trying to test for SQLI and all the crawled pages related to the domain.
On the right side click on the URL that you want to test, you can see the request parameters of the URL in the bottom panel. Right click on the request parameters and you can see the option "Send to sqlmap" as shown in the figure (I).
[caption id="" align="alignnone" width="601"] Figure (i)[/caption]
Figure (i)[/caption]
Then you can see a new window (SQLMap wrapper) that will allow you to configure sqlmap. Below Image gives you a clear view of the wrapper. Let's observe figure (ii),
[caption id="" align="alignnone" width="589"] Figure (II)[/caption]
Figure (II)[/caption]
Now let us have an over view of configuration features of the wrapper. In the "Target" textbox specify the URL that you are willing to test. (Normally it will be filled by default as you have sent the request parameters previously, if needed you can change the URL).
Specify the method on which the domain is accessible (GET/POST). In the "Bin-path" give sqlmap executable.
If you are aware of the DBMS of the web application, specify the database by selecting one of the options listed in the dropdown list. By default "auto" is selected which means that the SQLMAP wrapper tries with all the databases listed in the dropdown list to find out the database used by the application.
You can enumerate the database users, passwords, roles, privileges, databases etc by selecting the appropriate option from the Action dropdown list. By default it is set to "auto" which means it will try to enumerate all the options listed in the dropdown list in the sequential order.
If you are aware of the databases, users, tables, or columns, you can enumerate it by simply specifying it in the Database options.
Tampers are a kind of special characters or symbols that you are willing to insert into the query while pen-testing the application.
Once we configure the SQLMAP click on the "RUN", this will open a new tab with execution of the program with the configuration that you have given to the wrapper or the SQLMAP. We can make any number of simultaneous execution tabs with difference instances.
Below image shows the output tab. Let's observe figure (III),
[caption id="" align="alignnone" width="600"] Figure (III)[/caption]
Figure (III)[/caption]
Bored with theory, now let us see an example, the below URL is a vulnerable site for practicing the SQLI. You can also find the SQLI practice URL's by goggling.
http://192.168.2.3/news-and-events.php?id=22
Id parameter in the above URL is vulnerable to SQLI; let us find it out through our SQLMAP wrapper (Burp suite plug-in).
Open the URL in the browser for which the proxy has been configured. In the proxy (burp) go to the "site map" and click on the URL and send it to the sqlmap by right clicking on the response parameters of the website, as I mentioned previously. Figure (IV) shows you the wrapper opened for the above mentioned URL.
[caption id="" align="alignnone" width="544"]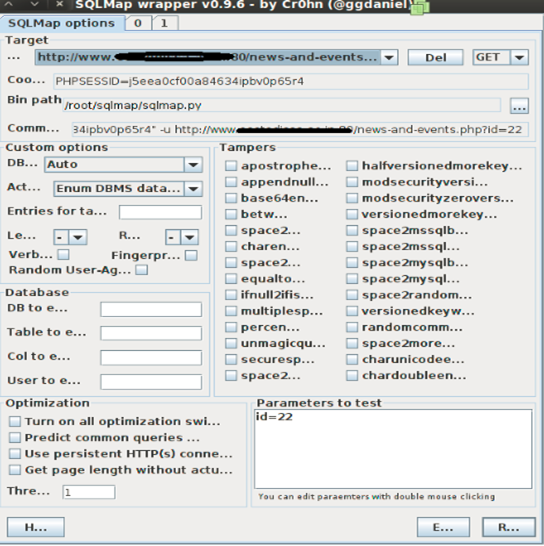 Figure (IV)[/caption]
Figure (IV)[/caption]
The target specifies the URL we are testing, cookie specifies the cookie or session id. Wrapper automatically identifies the positions in the URL where SQLI can be injected and specifies list of the parameters in "Parameters to test" text area (in our case we have only one possibility for injection which is "id" parameter).
In this example I have configured the SQLMAP wrapper to enumerate the list of databases that are configured in the backend database.
[caption id="" align="alignnone" width="518"] Figure (V)[/caption]
Figure (V)[/caption]
Figure (V) shows you the output tab which intend displays you how the plug-in tried to exploit the SQLI vulnerability in different ways
We can see that initially the wrapper tried to exploit the vulnerability by using "Boolean-based blind SQLI" by using AND operator. The payload shows how the tool tried to exploit the vulnerability. Here we can see the payload: id=22 AND 4626=4626, which is equivalent to the following URL:
http://www.eastodissa.ac.IN/news-and-events.php?id=22 AND 4626=4626
As the URL is always true, the above URL returns the same page as of the original URL.
In the second trail it tried "error-based SQLI". Later by using UNION operator
[caption id="" align="alignnone" width="534"] Figure (VI)[/caption]
Figure (VI)[/caption]
From the figure (VI) we can observe more server details like web server, Operating System, back-end DBMS.
" Information_schema" and "nilakantatrust" are the two databases that are used by the web application.
Now let us try to enumerate all the tables and the columns of the tables from the above databases. To do so configure the SQLMAP wrapper Action field with the option "Enumerate database tables and columns". Figure (VII) shows you the same.
[caption id="" align="alignnone" width="532"] Figure (VII)[/caption]
Figure (VII)[/caption]
Figure (VIII) shows us the tables of the database "nilakantatrust"
[caption id="" align="alignnone" width="485"] Figure (VIII)[/caption]
Figure (VIII)[/caption]
Let us see the columns of these tables. Figure (IX) shows the columns and their data types of two tables "est_notice" and "est_news" of nilakantatrust database.
[caption id="" align="alignnone" width="534"] Figure (IX)[/caption]
Figure (IX)[/caption]
We can also dump complete database by selecting the option "dump dbms databases". And also store complete data into a file by using the option "save to file" in the output tab.
[caption id="" align="alignnone" width="501"] Figure (X)[/caption]
Figure (X)[/caption]
Figure (X) shows the dumped data of the table "est_admin" from "nilakantatrust" database and storing it into a file.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Conclusion:
SQLMAP is a powerful tool which is used to automate the process of detecting and exploiting the SQLI.










