Ethical hacking: SNMP recon
In this article, we will discuss the various methods of ethical hacking one could take to perform reconnaissance on the SNMP protocol. As you may know, SNMP reveals too much information about targets that might result in attackers compromising a target network. Today, we’ll explore the available tools that one can use to query information on targets.

FREE role-guided training plans
Overview of SNMP
There are numerous protocols available today, and SNMP is one of the least understood. SNMP allows us to manage computers and network devices.
SNMP is stateless and is datagram-oriented. It allows one to manage computers within the network. The managed computers will have an agent that communicates with the manager computer. These agents will send information to the manager, which will be stored in a database known as the Management Information Base (MIB), which is a hierarchical organization of the information collected on every SNMP device within the network.
This juicy information is invaluable for hackers that are going for SNMP information within the network. Hackers are able to target this database for information on hosts on the network, such as:
- Users: This can be able to describe the number of user accounts and their names. User groups and account creation information can also be obtained using SNMP
- Software installed: The installed software list can be easily obtained from the target machine easily using SNMP. This can be extremely valuable when determining the versions of installed software for a more targeted attack
- Open ports: Hackers can be able to determine open ports with more stealth by querying SNMP information rather than conducting an active scan that might give them away to system admins and others
SNMP communication takes place with Protocol Data Units (PDUs), of which there are several different types. These include:
- GetRequest: This PDU is sent by the SNMP manager to retrieve one or more requested MIB variables specified in the PDU
- SetRequest: This PDU is sent by the SNMP manager to set one or more MIB variables specified in the PDU with the value specified in the PDU
- GetNextRequest: This PDU is sent by the SNMP manager to retrieve the next MIB variable that is specified in the PDU. You can have multiple requests in the PDU. This PDU is primarily used by the SNMP manager to walk through the SNMP agent MIB
- Trap: This is an unsolicited message sent by the SNMP agent to notify the SNMP manager about a significant event that occurred in the agent
There are a few more PDUs that exist that are beyond the scope of this article, such as GetBulkRequest, Response and InformRequest.
SNMP versions
There are mainly three versions of SNMP in use today. Their difference is in their implementation and security via the community string. The community string is like a password, where authenticating to the manager is through a “private” community string.
The following are the different SNMP versions:
- SNMPv1: This version of SNMP is extremely poor at security, since it uses cleartext authentication. The community string here is by default set to “public”
- SNMPv2: This version of SNMP improved from v1 in terms of performance and security. However, it was not reverse-compatible with v1, hence not widely adopted
- SNMPv3: This version of SNMP improved greatly in terms of security and performance from v1 and v2. It introduced integrity checks and encryption. It is, however, still not widely implemented in many organizations
Using the “public” community string, is possible to query the MIB for information of particular hosts within the network. We can also use the “private” community string to make configuration changes to systems on the network.
Attacking SNMP
One of the common SNMP querying tools that comes within Kali Linux is snmp-check. This tool allows us to collect much information from a target, as discussed above, and much more. Metasploit also comes loaded with a list of default MIBs in its database. It uses them to query the device for more information depending on what level of access is obtained.
To launch snmp-check, open the Kali Linux terminal and type “snmp-check”. You will receive a screen similar to the following:
Once open, we get a basic usage manual that shows us how to use the tool.
We will now query some information from our target host. This information is queried from the MIB of the target host. It is important to note that this will only work for SNMPv1 and SNMPv2, not SNMPv3.
Obtaining information from a target
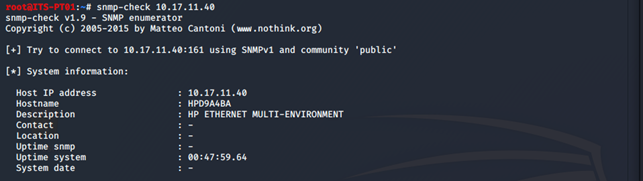
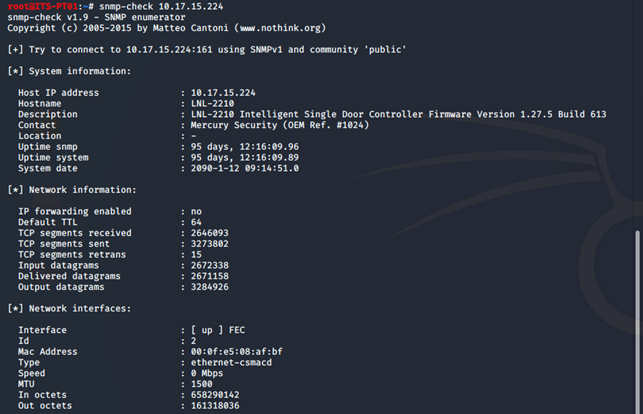
Now let’s take a look at how we can be able to collect juicy information from a target within our network. We decided to use our target printer within our local network to query for accessible information. The screenshot below shows what we were able to get after passing an snmp-check of our printer’s IP address.
snmp-check is able to expose the system information of the affected printer. The amount of information that we are able to access will depend on the MIB records available and type of device being accessed.
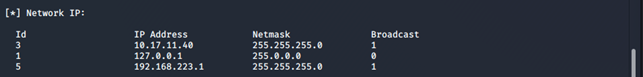
We can also see below that we are able to read network information:
The screenshot above shows network statistics of the target. We can also view network IP information, as shown below:
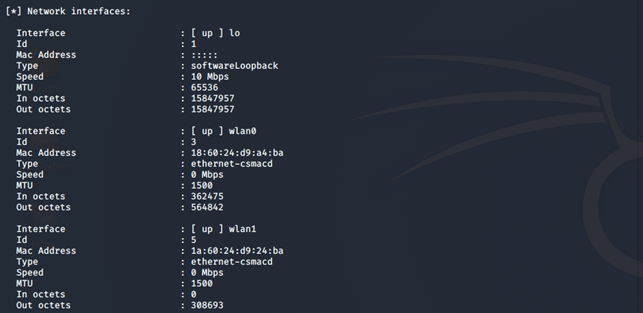
We are also able to view network interface information:
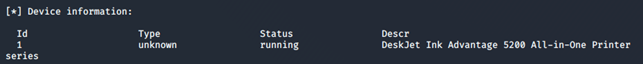
The tool also allows us to view device information:
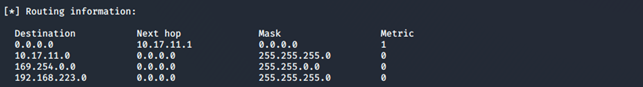
As we can see above, we are able to pinpoint the exact series of printer that is in use and its current status. We can also view network routing information, as shown in the following screenshot:
The information accessed above can vary quite a lot. We accessed a door-unlocking device and received almost similar results. This is shown below:
Some of the other information that we can receive from other hosts include routing information, TCP connections and listening ports.
Let’s now briefly discuss how we can prevent SNMP-based attacks.
Defending against SNMP-based attacks
In order to prevent SNMP-based attacks, we need to ensure that devices that have SNMP enabled but do not require it must get it disabled. SNMP must also be blocked at the network perimeter if it is not required within the network.
In addition, the default SNMP community read string must be changed from public and the default community write string from private. These must be changed to different longer and more difficult-to-guess strings.
One final step is to upgrade to SNMP v3, which is much more secure than v1 and v2.
If SNMP is allowed to remain open, hackers are able to obtain information such as ARP table network information, usernames and open TCP ports that can allow them to attack the system further.
Conclusion
The SNMP protocol can be quite beneficial to hackers who know the tools to use and the information to collect within the network. Knowing the right tools and approach can save you some good time in your reconnaissance. In addition, we looked at snmp-check and a few commands that can be very beneficial during a hacking exercise.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Sources
- Network Basics for Hackers: Simple Network Management Protocol (SNMP) Theory, Reconnaissance and Exp, Hackers-Arise
- Protocol data units (PDUs), IBM
- SNMP Attacks and Security, Mauno Pihelgas
- How to Find and Create SNMP Community Strings in Windows and Linux, Comparitech
- Lock IT Down: Don't allow SNMP to compromise network security, TechRepublic