Hacking communities in the deep web [updated 2021]
The role of hackers has changed over the years, in the past these professionals were viewed as dangerous criminals that needed to be kept at arm's length; meanwhile today they are highly sought from private companies, intelligence agencies and by criminal gangs.
"An increasingly large number of modern business operations rely on an understanding of the risks associated with software that can easily be made vulnerable to hacking." Reported in a post I published on the Fox News site on the role of hackers.
Hacking services are among the most attractive commodities in the underground market, it is possible to hire a hacker to request a "realistic" penetration test, or to pay to take over a Gmail or Facebook account for cyber espionage purpose.

What should you learn next?
How much does it cost to hire a hacker? How to do it and what is the price for their services?
Recently, journalists at Business Insider have published a post that described the prices for principal hacking services that it is possible to acquire online. According the Business Insider an individual that wants to hack someone's Gmail account will have to pay about $90.
"Hacking a Gmail address can come in handy if you lose your account password, manage other people's business accounts or simply want to improve your computer skills." states the post. "'If you want to crack Gmail passwords, you can hack Gmail with browser settings, phishing and keylogging software and special scripts"'
Hackers, for example, could be hired to hack into a social media account, the cost to hack into someone's Facebook account is $350, or simply to increase the rank of a company on a social network.
The investigation conducted by the journalists revealed that a hacker can steal someone's Hilton HHonor points for $15 or to compromise a NetFlix account just for $1.25.
Other common commodities in the hacking underground are the hacking courses that goes for $20 and hit-and-run attacks, such as a DDoS or a website defacement.
"Website hack or DDoS. Paying well." is the message of a hacker that promises to hack a WordPress-built website down for "2k euro."
There are various ways to buy hacking services and probably the most interesting place where it is possible to meet members of the principal hacking communities is the Deep Web … let's explore it!
Diving in the hacking communities
The number of Hacking communities in the Deep Web is very high as reported by several investigations published by security firms and cyber-experts, hackforum, Trojanforge, Mazafaka, dark0de and the recent TheRealDeal are just a few samples.
The majority of the hacking communities are closed to the public and one must request an invitation to join the discussions. In many cases, these groups specialize their activities on specific topics and practices (e.g. Social media hacking, data theft, malware and exploits and hit-and-run attacks (i.e. DDoS, Web site hacking).
Among the communities accessible only by invitation there are several hackforums, an example is the popular Trojanforge, which specializes in malware and code reversing.
Let's start our tour on the Deep Web from the results of a study conducted by the experts at Dell Secure Works Counter Threat Unit (CTU) to see what is changing from the publishing of the report and which are the dynamics and trends behind the hacking communities in the underground. In 2013, experts at Dell Secure Works Counter Threat Unit (CTU) published a very interesting report titled "The Underground Hacking Economy is Alive and Well." which investigated the online marketplace for stolen data and hacking services. The study listed the goods sold in the black markets and related costs. One year later, the same team of researchers at Dell SecureWorks released an update to the study of black hat markets, titled "Underground Hacker Markets", which reports a number of noteworthy trends.
The researchers observed a growing interest in the personal data, in particular in any kind of documentation that could be used as a second form of authentication, including passports, driver's licenses, Social Security numbers, and even utility bills.
"The markets are booming with counterfeit documents to further enable fraud, including new identity kits, passports, utility bills, social security cards and driver's licenses." states the report.
Another distinguishing element of the evolution of the underground marketplaces in the last year is the offer of Hacker Tutorials, as we have seen this kind of product still represents an element of attraction in the hacking community.
Training tutorials provide instruction to criminals and hackers that want to enter into the business of stolen credit card data, information on running exploit kits, guides for the organization of spam and phishing campaigns, and tutorials on how to organize hit-and-run DDoS attacks.
"These tutorials not only explain what a Crypter, Remote Access Trojan (RAT) and exploit kit is but also how they are used, which are the most popular, and what hackers should pay for these hacker tools," the report said.
Other tutorials offered in the hacking communities include instruction to hack ATM and to manage a network of money mules, which are the principal actors for the cash out process of every illegal activity.
Figure 1 - Hacking Tutorial - Dell Secure Works Counter Threat Unit (CTU) Report
The results of the investigation conducted by the experts at Dell confirm the findings of another interesting report published by TrendMicro on the activities in the Brazilian underground, which is characterized by the availability of a significant number of similar products and services. Hacking communities are very active in selling stolen credit cards, differentiating their offer to reach a wider audience and provide tailored services at higher prices.
"It is apparent that the underground hackers are monetizing every piece of data they can steal or buy and are continually adding services so other scammers can successfully carry out online and in-person fraud," states the report.
In the following table that I have found on Twitter are listed the services and the products with related prices expressed in both Bitcoin and Euro.
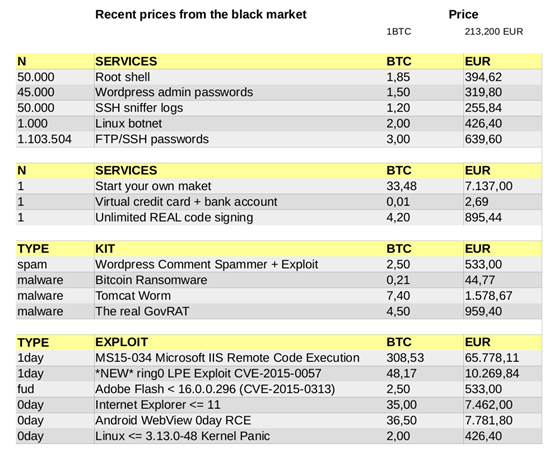
Figure 2 - Listing and average prices for black markets
Hiring hackers in Tor network
I anticipate you that I'm quite diffident of the amazing number of offers from alleged hackers that advertise their services on various hacking forums in the underground. The experts that you will find in many hacking communities could help you to run a penetration test on your website or can exploit known flaws in vulnerable websites that you intent to compromise.
Let's start our tour from the "Rent-A-Hacker" website; it seems managed by a single hacker that presents himself with the following statement:
"Experienced hacker offering his services! (Illegal) Hacking and social engineering is my business since i was 16 years old, never had a real job so i had the time to get really good at hacking and i made a good amount of money last +-20 years.
I have worked for other people before, now im also offering my services for everyone with enough cash here.
The Onion URL for its website are:
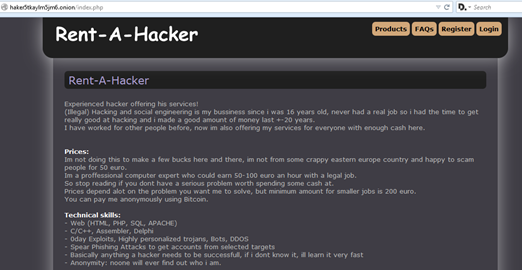
Figure 3 - Rent-A-Hacker Tor website
The hacker explains that he is a professional hacker specialized in illegal hacking services that he offer to "destroy some business or a persons' life."
Reading his description it seems to be specialized in the hacking of websites and probably he manages a botnet that it offers for DDoS attacks.
The hacker explains also that he is able to run espionage campaign and tracking of pedos online. Among the services he offers, there is also the gathering for private information of any individual, anyway every tack could be committed by paying an hourly rate that is about 100 dollars, of course prices depend on many factors, including the complexity of the task assigned to the expert.
Of course, the payments are anonymous and made through Bitcoin virtual currency.
Surfing on Tor network, I have found several black markets and forum offering hacking services, "Hacker for hire" (http://hacker4hhjvre2qj.onion/) is one of them.
The website offer wide range of service, from cyber frauds to hacking services. It is curious to note that operator of the website also offer both offensive and defensive services, specific services in fact are tailored for victims of the cybercrime.
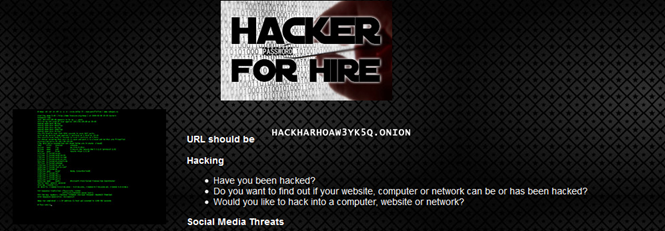
Figure 4 - Hacker for hire
Hacking
Web Server security Audit USD 150 (0,62 BTC at the time I'm writing)
Social media account take-over
Social media (FB, Twitter, etc.) – account hacking USD 50 (0,21 BTC at the time I'm writing)
Spyware and Device Tracking
Spyware development USD 180 (0,74 BTC at the time I'm writing)
Device Tracking USD 60 (0,25 BTC at the time I'm writing)
Intelligence and Investigation
Intelligent report – locate people USD 140 (0,58 BTC at the time I'm writing)
Intelligent report – background checks USD 120 (0,49 BTC at the time I'm writing)
Fraud Track – Find your Scammer USD 120 (0,49 BTC at the time I'm writing)
Cyber extortion To be agreed prior contact
Another website that offers many illegal products is the "Hell"
(http://hell2bjhfxm77htq.onion).
Figure 5 - The Hell Hacking Forum
The web portal hosts several sections related to hacking tools, tutorials and of course, it is populated by hackers that offer their services. In the section "Jobs" there are various offers for hacking services, I contacted some of the alleged hackers negotiating the following prices for some specific tasks.
Product Price
Hacking
Hacking web server (vps or hosting) USD 250 (1,04 BTC at the time I'm writing)
Hacking personal computer USD 200 (0,83 BTC at the time I'm writing)
Hacking Social Media Account (Facebook, Twitter) USD 300 (1,25 BTC at the time I'm writing)
Gmail Account Take over USD 300 (1,25 BTC at the time I'm writing)
Security Audit
Web Server security Audit USD 400 (1,66 BTC at the time I'm writing)
Malware
Remote Access Trojan USD 150 - 400 (0,62 – 1,66 BTC at the time I'm writing)
Banking Malware Customization (Zeus source code) USD 900 (3,75 BTC at the time I'm writing)
DDoS attack
Rent a botnet for DDoS attack (24 hours) USD 150 - 500 (2,08 – 1,66 BTC at the time I'm writing)
In the Tor network, several hackers offering their services using their own websites, black markets represent the privileged choice to get in touch with a hacker and hire him. The principal benefits to hire a hacker on a black marketplace are:
- Possibility to verify the reputation of the hacker and its abilities.
- Availability of escrow services that protect both buyers and sellers.
For this reason, I decided to explore some of the most popular black markets searching for hackers to hire. I started my short tour from the TheRealDeal black market (http://trdealmgn4uvm42g.onion) that was recently emerged in the underground community to provide both sellers and buyers a privileged environment for the commercialization of exploit kits and hacking services.
Figure 6 - TheRealDeal Marketplace
I have found among the hackers that propose their services the possibility to pay for a DDoS attack or for the customization of a malware, also on TheRealDeal market it is possible to pay for tutorials of different kind.
Below a table that outlines the offers I received from the hackers I contacted, or that published their offers on the marketplace.
Product Price
DDoS attack
24 Hours DDoS Service USD 480.61 (2 BTC at the time I'm writing)
Services
Market set up USD 7957.80 (33,11 BTC at the time I'm writing)
Malware
Anonymous RAT setup for dummies USD 1,2 (0,005 BTC at the time I'm writing)
The real GovRAT - source code + Instructions on setup and compile + 1 digital certificate for code signing to sign your files USD 1081.38 (4,5 BTC at the time I'm writing)
RAT set up service and deployment on bullet proof hosting USD 1201.53 (5 BTC at the time I'm writing)
Android RAT + Tutorial USD 1,2 (0,005 BTC at the time I'm writing)
Hacking
Hacking web server USD 500 (2,08 BTC at the time I'm writing)
Hacking Social Media Account (Facebook, Twitter) USD 200 (0,83 BTC at the time I'm writing)
Tutorial
Hacking Tutorial, Cash out tutorial, Carding tutorial etc. USD 2,40 - 72,09 (0,01 – 0,3 BTC at the time I'm writing)
Another popular black market is Nucleus (http://nfc2s3fsbjh22hzz.onion, http://ifa3gxnvs6gj7ooa.onion/ but at least another 2 mirrors are up to serve visitors), this marketplace is more focused on products (i.e. malware, stolen card data, etc.) than service. I tried to contact some sellers and only one of them offered me hacking services to hack a server or to compromise a specific user stealing his data with targeted attack. In the following table are resumed some of the products/services available on Nucleus marketplace.
Product Price
Hacking
Hacking Tool: Spying a Computer USD 500 (2,08 BTC at the time I'm writing)
Hacking a web server USD 1000 (4,16 BTC at the time I'm writing)
Targeted attack on a specific user USD 2000 (8,32 BTC at the time I'm writing)
Software protection cracking - Reverse engineering USD 10 (0,04 BTC at the time I'm writing)
Penetration Testing USD 100 – 250 per hour (0,4 - 1,04 BTC at the time I'm writing)
Custom Facebook Hack USD 250 (1,04 BTC at the time I'm writing)
Tutorial
How to make a Botnet USD 22,11 (0,09 BTC at the time I'm writing)
How to set up a RAT USD 0,11 (0,00004BTC at the time I'm writing)

The opinion of an expert – Paolo Stagno
In order to give you an illustrious opinion about the hacking in the Deep Web, I decided to involve a valuable colleague, Paolo Stagno, aka VoidSec, which is a Cyber Security Analyst specialized in Underground Intelligence. Paolo is attending as speaker at various international conferences, including DEFCON, BlackHat, and Droidcon, and he is the leader and founder of VoidSec.com, a meeting place where hackers can share experience and ideas.
Below my questions for Paolo regarding deep web and hacking communities:
What can we find in the in the deep web?
The Deep web is a "hidden reality" where is possible to find every kind of illegal products and services. Black markets are the places in the Deep Web were sellers offers their illegal goods and services, including drugs, weapons, counterfeit, stolen merchandise, credit cards, access to bank accounts, fake identities and related documents, various accounts, trafficking in persons, organs, hacking services and also hitmen.
The hacking market inside the deep web is flourishing thanks to the anonymity offered by the communications protocols implemented in this part of the web. The newest trend observed by security experts is the model of sale known as hacking as a service. The addition of a technical support to the hacking tools (i.e. Friendly interfaces, email and IRC) lowers the level of difficulty for their usage, ransomware kits, for example, are offered according this model example allowing anyone to commit crimes just for 50 €.
Most common services available in the hacking underground are:
- Hire an hacker
- Botnet
- exploit kit
- 0day
- Crypter
- DDoS
- Doxing
- Spam
- Malware
- Money laundering services
For renting a botnet, usually used to run spam or for DDoS campaign, users pay a price from 2-5$ / month (with a limitation on the number of attack sessions and their duration) up to $ 100-200 every day for more complex attacks.
Exploit kits are still sold in their entirety (including source code), but they still have exorbitant prices ($ 20-30k), for this reason, users rent them for the limited periods ($ 500 / month). A similar approach is the same goes for 0-day exploits that can cost up to hundreds of thousands of euro (MS-15-034).
Which are the principal players of the hacking on the deep web?
In deepweb, there are several hacking communities that are accessible via both anonymizing protocols or via Clearnet. Many of them are accessible only by invitation resulting exclusive, usually they are focused on specific topics (i.e. trojanforge: malware and reversing), but there are also generic communities (hackforum) in which members address various issues related to the world of hacking except carding, frauds or "financial" crimes.
In the Darknets, there are many forums and chat dedicated to activities of black hacking, but the sale of products and services is arranged through black marketplaces to reach a wide audience. The major players in the hacking landscape in the deep web are:
- Agora (TOR)
- silkroadreloaded (I2P - potentially dying due to the transfer from TOR I2P resulting in reduction of total consumption)
- TheRealDeal (TOR) past the spotlight recently due to the possibility of buying 0day exploits
- DreamMarket (TOR)
- MRNiceGuy (TOR, clone of the original)
- Outlaw (TOR)
- MajesticGarden (TOR)
Among the blackmarket in Clearnet find
- Rescator
- Lampeduza
What are the risks for buyers?
The black markets hosted in the Darknet increase the safety of both sellers and buyers, making hard to track them by law enforcement. In any case, there is the concrete risk that users fall victim of a website used as honeypot by the law enforcement.
Another risk for buyers is that law enforcement can intercept the shipment of real and illegal products (i.e. Drugs or weapons).
How is the payment, what guarantees the buyer?
Trust is one of the major problems of the hacking communities, in the black markets, exactly like in any other market, the operators have been implemented a reputation mechanism based on the buyers' feedbacks. Some black markets implement escrow mechanisms based on BTC MultiSignature in order to protect both sellers and buyers.
The Payment is generally made by exploiting virtual currency schema such as Bitcoin and Litecoin, rarely operators allow PayPal, Western Union and other payment systems.
What activities conduct VoidSec in deep web?
VoidSec runs an intense activity of Underground Intelligence by performing research and prevention of threats, primarily by monitoring the main marketplaces and hacking communities. We analyze the latest trends, products and services offered in the DeepWeb.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Conclusion
As we have seen it not so difficult to hire a hacker in the numerous black markets available on the Deep Web, especially when someone needs simple tasks. The situation is quite different when you search for a professional hacking team to hire; these groups usually use different channels to communicate with a restricted number of clients. Another consideration to make is that the majority of services offered through several hidden services are scams and in many cases, the hackers are not able to complete their tasks.
For this reason, users that intend to hire a hacker usually refer black markets due to the reputation mechanisms they implements.
Another reflection to make is that the prices for various hacking services are quite similar among the different forums or hacking communities, this can allow us to monitor the evolution and trends in the hacking underground. Price variations, for example, could be caused by to the sudden availability of a product in the criminal ecosystem. The availability of a large amount of data related to a data breach could cause a decrease for the price of a single record and sustain the offer hacker against clients of organizations affected.
This information is extremely valuable for law enforcement and for those who constantly monitor criminal groups and their operations.
Stay tuned …
If you an interested in a career of ethical hacking, consider enrolling in an Infosec hacking course!
Interested in learning more? Check out these articles
How Much Does it Cost to Become a Penetration Tester?
How to Advance In Your Career as a Penetration Tester
Sources
http://securityaffairs.co/wordpress/36709/cyber-crime/hiring-hackers-how-much-is-it.html
http://www.foxnews.com/tech/2015/01/15/modern-hacker-takes-on-new-role/
http://securityaffairs.co/wordpress/31301/cyber-crime/underground-hacking-markets.html
http://www.secureworks.com/resources/blog/the-underground-hacking-economy-is-alive-and-well/
http://www.secureworks.com/assets/pdf-store/white-papers/wp-underground-hacking-report.pdf
http://securityaffairs.co/wordpress/30350/cyber-crime/brazilian-underground-cyber-market.html











