Nmap evade firewall and scripting [updated 2019]
Nmap is the most powerful scanner that is used to perform so many functions including port scanning, service detection, and even vulnerability detection. Nmap from beginner to advanced has covered many basic concepts and commands, and in this second part of this series of articles I will discuss some advanced techniques of Nmap.

What should you learn next?
How to evade a firewall/IDS
Firewalls and IDS (intrusion detection systems) normally play an important role to defend the remote target very well from a security point of view because these hardwares and softwares are capable of blocking the intrusion, but in the case of penetration testing you need to bypass these tools to get the right result otherwise you will be misled. Nmap can scan the firewall and other intrusion detection systems on the remote target computer, as it uses different types of techniques to fight against these softwares and the techniques are dependent on the remote software. There are two types of firewall that might be installed on the target computer:
- Host based firewall (A firewall is running on a single target computer, for example you are running a firewall on your computer)
- Network based firewall (A firewall has been installed and is running to protect the entire network and has been deployed at the node of the network, it might be LAN)
There are two types of IDS/IPS also available that might be installed on the target machine, this is the situation that a penetration tester needs to tackle. There are so many different type of Nmap techniques that can be used in this situation, for example:
TCP ACK scan (-sA)
It is always good to send the ACK packets rather than the SYN packets because if there is any active firewall working on the remote computer then because of the ACK packets the firewall cannot create the log, since firewalls treat ACK packet as the response of the SYN packet. The TCP ACK scan requires the root privileges at the attacker side and it performs very well for the stateless firewall and IDS. As a penetration tester you need to check the response of a firewall; there might be four types of responses:
- Open port (few ports in the case of the firewall)
- Closed port (most ports are closed because of the firewall)
- Filtered (Nmap is not sure whether the port is open or not)
- Unfiltered (Nmap can access the port but is still confused about the open status of the port)
So these are some important responses that you might get during a penetration testing. ACK scan is slightly different from the other types of scanning techniques because it has not been designed to discover the open ports, but it has an ability to determine the filtered and unfiltered responses. Let's compare the two results of an ACK scan.
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 13:30 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00077s latency).
All 1000 scanned ports on 192.168.1.9 are filteredStarting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 13:31 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00020s latency).
All 1000 scanned ports on 192.168.1.9 are unfiltered
So now it is very easy to find out whether the target computer has a firewall enabled or not, since a simple ACK scan means there is a lower chance of detection at the victim side but a high chance for the attacker to discover the firewall. The result of a SYN scan for both the situations are as follows:
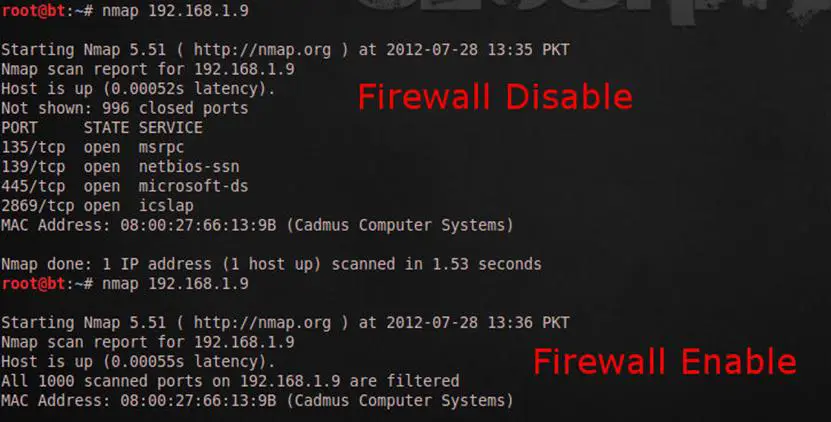
Note: The victim is the Windows computer for all the cases with the three situations.
- Firewall enabled
- Firewall enabled + all ports are closed
- Firewall disabled
TCP Window scan (-sW)
Very similar to the ACK scan with a little difference, the TCP window scan has been designed to differentiate between open and closed ports instead of showing unfiltered. It also requires the root privilege to execute. Let's examine the different responses of a TCP window scan.
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 13:50 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00051s latency).
All 1000 scanned ports on 192.168.1.9 are filteredStarting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 13:51 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00071s latency).
All 1000 scanned ports on 192.168.1.9 are closedThis type of scan does not open any active session with the target computer, so there is no chance that the victim's computer can create a log of the activities. It works on the simple phenomena to send ACK packets and receive a single RST packet in response.
Fragment packets (-f)
It is a very general concept and can be used in so many different situations, for example: if the target machine does not have the capabilities to handle larger packets then the fragmentation technique is useful to evade the firewall. The parameter of this technique is -f, it just split the request into small segments of IP packets called the fragmented IP packets. You can use -f twice -ff if you want to further break the IP headers.
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 14:21 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00056s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:66:13:9B (Cadmus Computer Systems)
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 14:24 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00083s latency).
All 1000 scanned ports on 192.168.1.9 are filtered
MAC Address: 08:00:27:66:13:9B (Cadmus Computer Systems)Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 14:20 PKT
Nmap scan report for 192.168.1.9
Host is up (0.00057s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:66:13:9B (Cadmus Computer Systems)Spoof MAC address
This one is the simpler techniques,you can spoof your MAC (attacker MAC) address., MAC address spoofing creates a very difficult situation for the victim to identify the computer who originated the incoming request. Nmap can select a completely random MAC address for each and every scan based on the vendor name, the other option is to manually specify the MAC address (by doing this an attacker can spoof the address of a computer on the same network). Nmap has the database called nmap-mac-prefixes and
whenever the vendor name is given it looks on the database to find the suitable MAC address.
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 17:18 PKT
Spoofing MAC address 00:00:0C:6D:3F:26 (Cisco Systems)
Nmap scan report for 192.168.1.3
Host is up (0.00036s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
23/tcp closed telnet
80/tcp closed http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:66:13:9B (Cadmus Computer Systems)-
Nmap timing option
Timing option is a very important and an interesting feature of a Nmap, since sometimes you need to make a delay between every request. There are so many reasons for this but the most important reason is stress on the network; sometimes the victim's computer and even a network cannot handle a big request. As a Nmap penetration tester you need to make sure that your scanning should not be treated as a Denial of Service attack (DoS), so the timely response and request are very important aspects in scanning. Nmap has so many features and parameters that can be very helpful to scan a target in a timely manner, the fragmentation technique (-f) as discussed is also a useful technique to split your request into multiple segments. The other important parameters are discussed below:
Delay (--scan_delay)
This is the best parameter that can be used to control the delay between each and every request Since you can control the time between each probe you need to be make sure to use the timing in integer form and do not forget to mention the unit of time:
- ms (millisecond) e.g. 5ms
- s (second) e.g. 5s
- m (minute) e.g. 5m
- h (hour) e.g. 5h
Let's consider an example:
.
.
.
Nmap done: 1 IP address (1 host up) scanned in 0.21 second.
.
.
Nmap done: 1 IP address (1 host up) scanned in 5.31 secondsHost timeout option (--host-timeout)
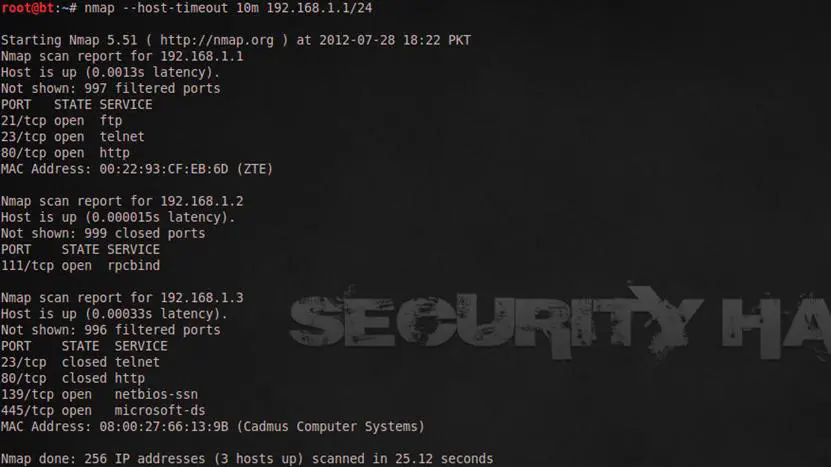
Sometimes a host takes too much time to respond and if you are scanning an entire network then it is very difficult to wait for a single host. There might be so many reasons behind a slow response, for example the network connectivity and the firewall, so if you don't want to waste your time then you can set a time limit.
Nmap Scripting
Nmap scripting is one the best features that Nmap has. Nmap scripts are very useful for the penetration tester because they can save so much time and effort. The Nmap scripting engine has more than 400 scripts at the time of this writing, and you can create your own script and everyone can create a script and submit it to the script engine to help the community of penetration tester.
Nmap scripts can perform so many different functions from vulnerability scanning to exploitation and from malware detection to brute forcing. In this section I will discuss some of the best Nmap scripts and their usage:
smb-check-vulns
This is one of the important scripts that can scan to check the vulnerabilities:
- MS08-067 Windows vulnerability that can be exploited
- Conficker malware on the target machine
- Denial of service vulnerability of Windows 2000
- MS06-025 Windows vulnerability
- MS07-029 Windows vulnerability
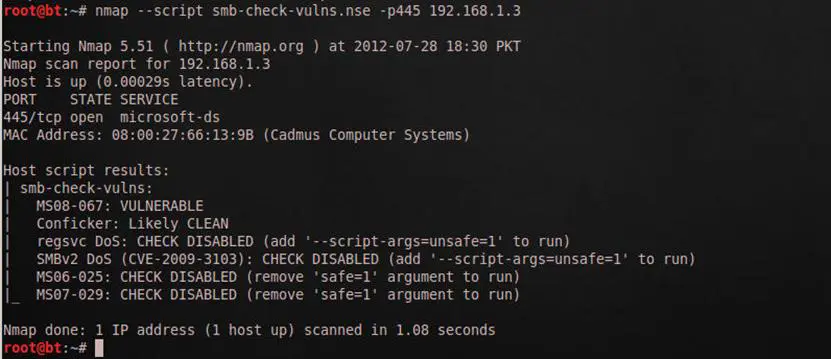
Now it is very easy to find the above vulnerabilities on the target machine, and you can easily exploit it via Metasploit.
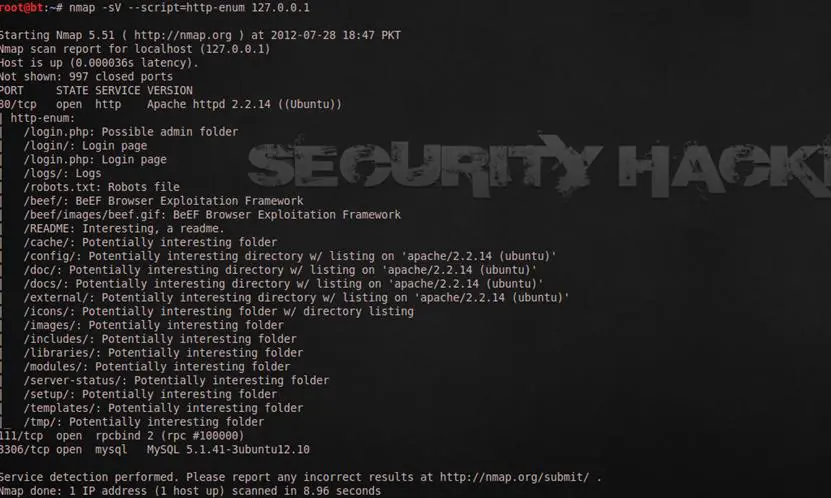
Http-enum
If you want to enumerate on the web server to find the directories of the website then this is the best Nmap script for this purpose. The http-enum script is also used to discover the open ports and to list softwares with their version of each port.
root@bt:~# nmap -sV --script=http-enum 127.0.0.1
Starting Nmap 5.51 ( http://nmap.org ) at 2012-07-28 18:47 PKT
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000036s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.14 ((Ubuntu))
| http-enum:
| /login.php: Possible admin folder
| /login/: Login page
| /login.php: Login page
| /logs/: Logs
samba-vuln-cve-2012-1182
The script to perform the desired scanning against the target machine to find the Samba heap overflow vulnerability CVE-2012-1182.
nmap --script=samba-vuln-cve-2012-1182 -p 139 target
nmap --script=samba-vuln-cve-2012-1182 -p 139 192.168.1.3
smtp-strangeport
So many organizations are running their SMTP server on the non standard port for security reasons. Smtp-strangeport is the script to find out whether the SMTP is running on the standard port or not.
nmap -sV --script=smtp-strangeport target
http-php-version
As the name suggests, this script has been created to get the PHP version from the web server. The software version is very important for a penetration tester to find the respective vulnerability, so this script is very helpful for web application penetration testing.
nmap -sV --script=http-php-version target
The Nmap scripting engine contains so many scripts that you can even find several scripts for a specific softwareor platform. For example: if you want to do penetration testing on a website which is based on WordPress then you can use Nmap scripts for this purpose.
- http-wordpress-plugins
- http-wordpress-enum
- http-wordpress-brute
dns-blacklist
This is the best script in my view to find the blacklisted IP addresses. All you need to do is just provide an IP, then the script checks it for the DNS anti-spam and proxy blacklist.
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-07-28 23:54 PKT
Nmap scan report for 67.213.218.72
Host is up (0.24s latency).
Host script results:
| dns-blacklist:
| PROXY
| dnsbl.tornevall.org - PROXY
| IP marked as "abusive host"
| Proxy is working
|_ Proxy has been scanned
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Conclusion
This article is an effort to cover the most important aspects of Nmap from beginning to advanced so that everyone can learn even without previous knowledge. This is not the end because Nmap has a lot of features, you can do many things by using Nmap. I recommend you to practice with it every day because practice makes a man perfect.










